Virtual PFsense behind physical router
-
Greetings. I believe that's NAT problem, but maybe someone will advise me what exactly it is, because I do not understand what exactly wrong.
I have a need in such network, i.e. virtual PFsense behind physical router. The scheme is below (yes, that is network of my homelab)
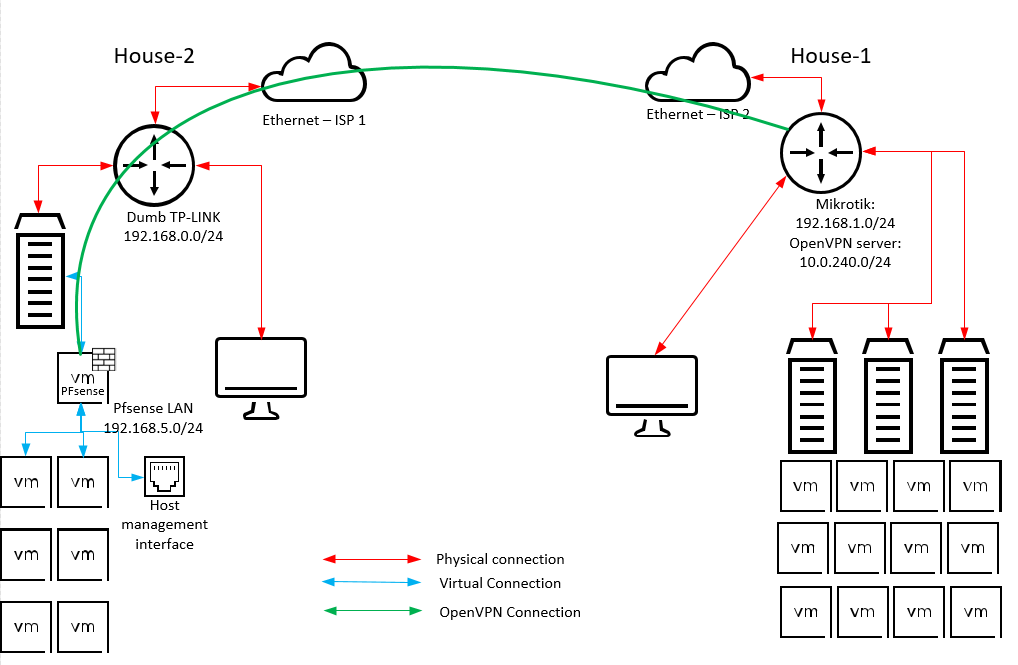
The routing in House-1 is fine, i.e. LAN and OpenVPN network are routed between each other.
The virtual PFsense have IP:- 192.168.5.1 for Pfsense LAN
- 192.168.0.2 for PFsense WAN with gateway on 192.168.0.1
- 10.0.240.2 for PFsense OpenVPN (client)
Host management interface is 192.168.5.2 and I have NATted it over 443 port for OpenVPN and it works.
Now the problem 1.
The LAN clients can't get access to the internet. Even if I disable VPN and return their Gateway to default.Now the problem 2.
Separate issue from problem 1.
The virtual PFsense LAN doesn't have access to ether OpenVPN network or to the ethernet. Only to House-2 LAN segment. And I wanna to have all VMs behind PFsense to go via OpenVPN. I can ping House-1 IPs from PFsense console. But can't from LAN clients of PFsense
I.e. I need to force LAN clients of Virtual PFsense to OpenVPN tunnel.
I have read
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-route-internet-traffic.html#assign-openvpn-interfaces
But that didn't helpBelow is my firewall rules
WAN:
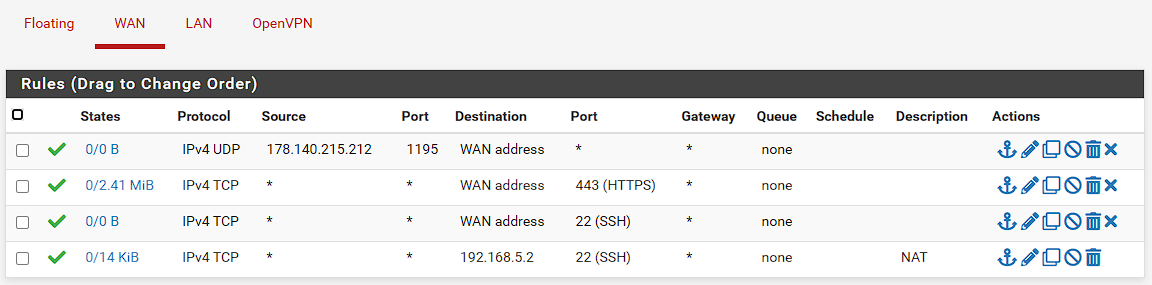
LAN:
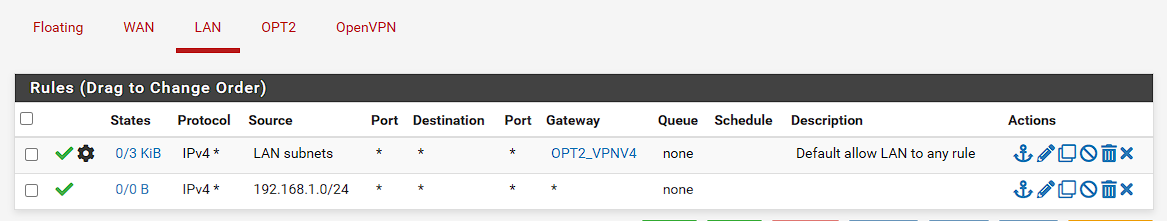
OPT2:
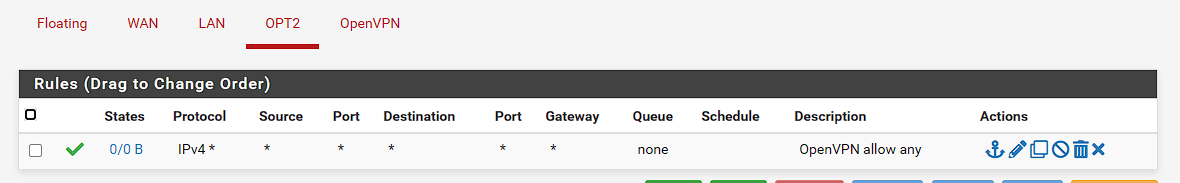
OpenVPN:
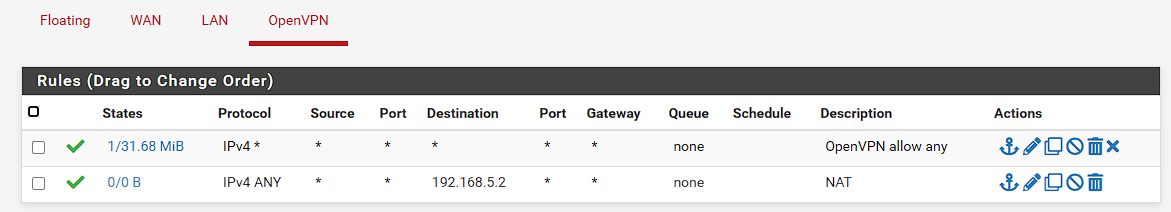
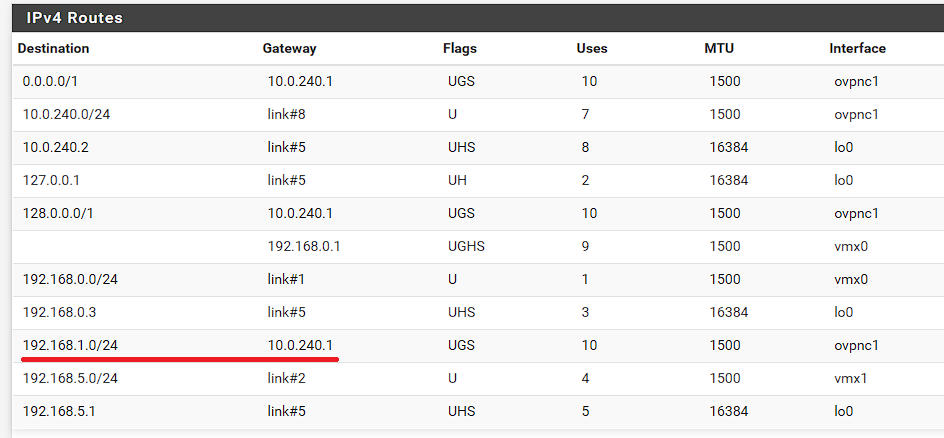
And routes, I have added 192.168.1.0/24 to the Remote IPs:
-
Problem 2 fixed by adding route to 192.168.5.0/24 on Mikrotik side