Ping monitoring
-
I am trying to setup something on pfsense that will ping a local client and then send an email alert whenever it is down.
Currently running telegraf and ntopng and sending to influx databases for some grafana dashboards but can't seem to find something you would think is so simple.
I did notice the following option in the telegraf plugin,
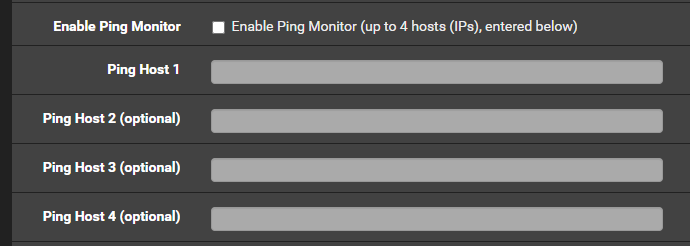
But I can't seem to find where it puts it in the database and would really just like for pfsense to email me whenever this ip doesn't respond to ping.
Also thought this would be somewhere in ntopng but can't seem to find it there either.
-
I was able to find this solution on my own using ntopng.
Enabling alerts and then using the active monitoring section to setup a continuous ping measurement to my local host worked flawlessly.
One thing to note is you do have to make sure and enter your smtp host with smtps:// or else it won't be able to send the emails.
-
@bigjohns97 said in Ping monitoring:
One thing to note is you do have to make sure and enter your smtp host with smtps:// or else it won't be able to send the emails.
Aka port 465. If your mail host (mail server) needs you to do so. Like, for example, gmail.
Other, using submission, using port 587, don't need that. -
@Gertjan While gmail is supposed to support both ports I tried both and neither would work until I used the smtps prefix.
Was able to find this in a github support thread it wasn't in any documentation.
-
You make me doubt now.
Are you talking about the pfSense Nortifications ( System > Advanced > Notifications )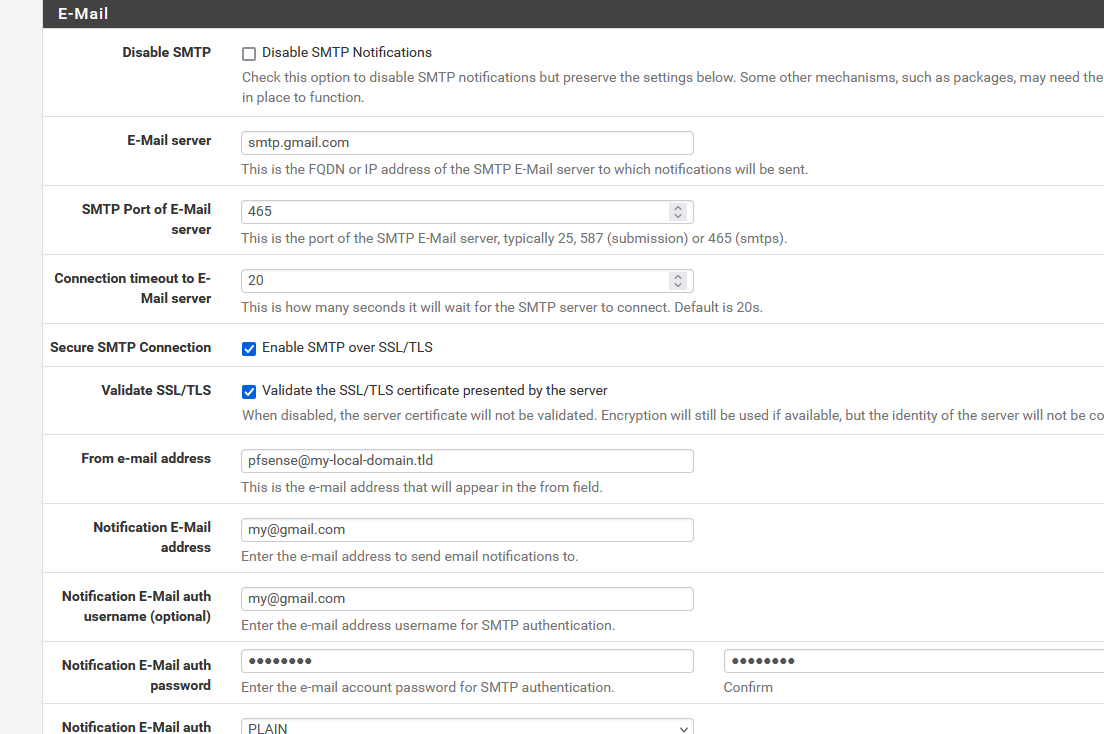
-
@Gertjan No I meant you had to do this in ntopng, in pfsense the above config you have would work.
For example here is the config in ntopng.
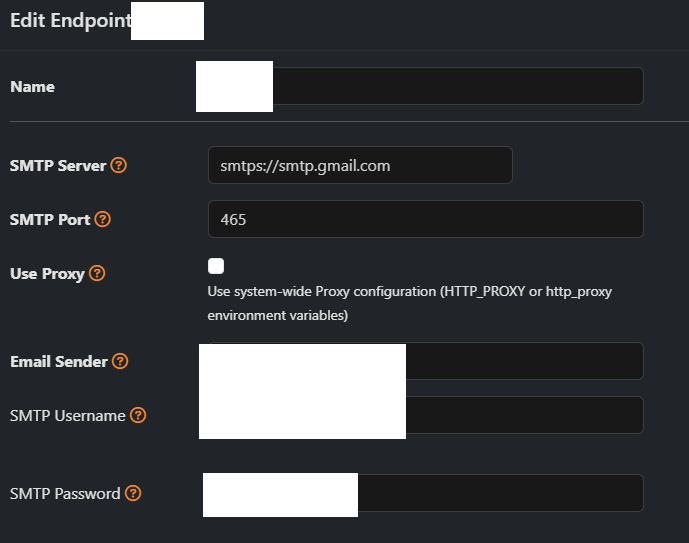
I spent a lot of time troubleshooting why just putting smtp.gmail.com wouldn't work, you had to put the prefix of smtps:// in front or it would error out. I guess I figured it would see the port 465 and know it needed to be secure.
I was posting in case anyone else tried this because I couldn't find the prefix requirement anywhere on the ntopng docs.
-
@bigjohns97 Be aware that NtopNG does use a fair bit of ressources and does a substantial amount of diskwrites/sec in the default setup because it will start monitoring all traffic on a interface. If you only use it for ping monitoring you should probably disable the monitoring of interface traffic - to prevent it wearing your SSD/eMMC out and to conserve CPU ressources.
-
@keyser I appreciate the heads up but I was already running ntopng for traffic DPI grafana dashboard shown below
https://github.com/lephisto/pfsense-analytics
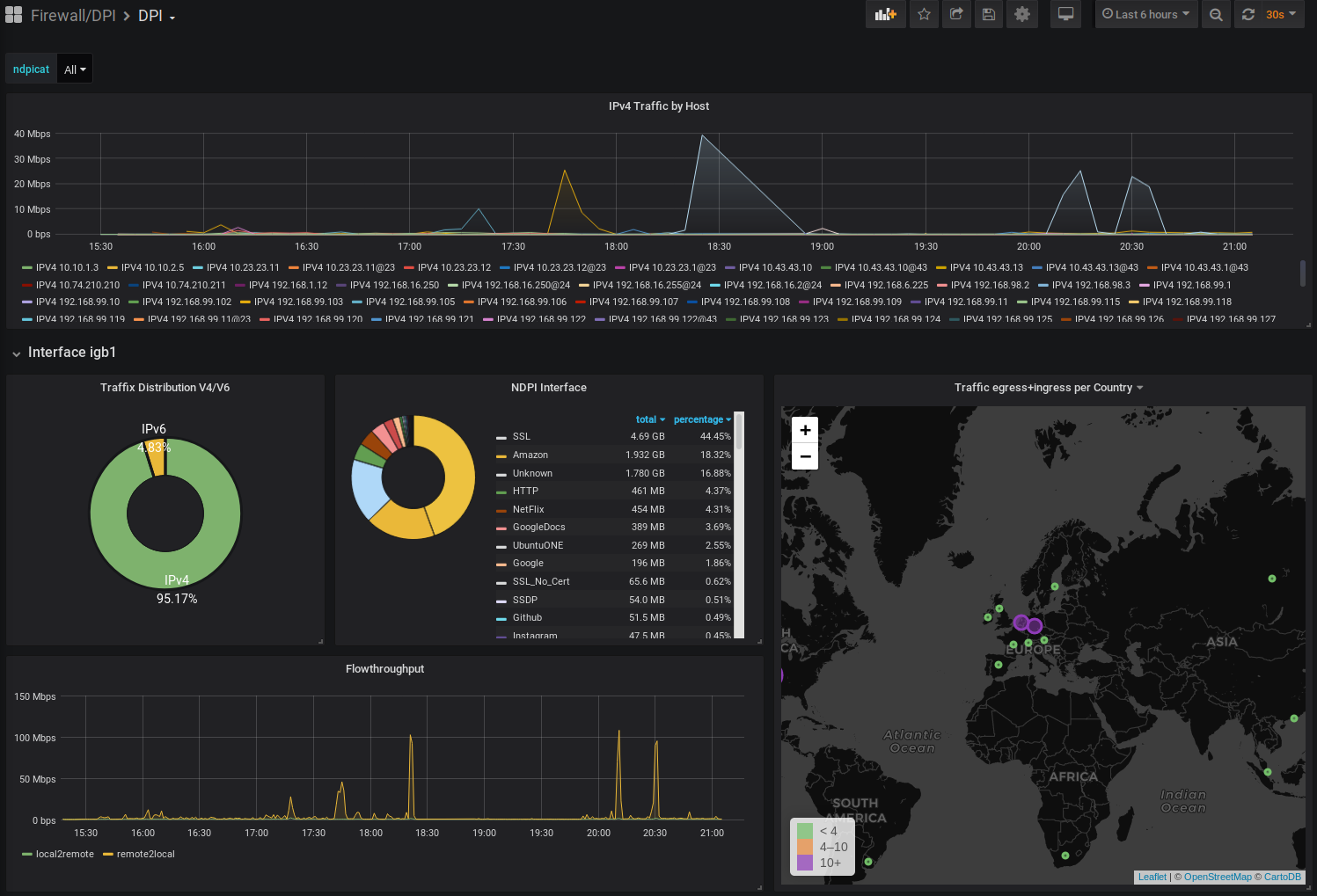
I have also turned off all of the local stuff possible while just leaving the timeseries required for the DPI stuff above that is hosted on another system on the LAN.
-
@bigjohns97 what version of pfsense do you have this running on. The comments on the GIT page have some not able to get it working on 2.6.
There are other issues with the docker stack as well. Just worried you may be running out of date and insecure software to get this data. -
@michmoor 24.03 the latest release
-
@bigjohns97 if you got it working it would help others if you posted how on git. There seems to be a fair amount of people struggling—just a suggestion.
-
@michmoor I would be happy to, share what you found and I will help best I can.
I found this solution on git under the ntopng project
https://github.com/ntop/ntopng/issues/8174
-
@bigjohns97 said in Ping monitoring:
I was able to find this solution on my own using ntopng.
Enabling alerts and then using the active monitoring section to setup a continuous ping measurement to my local host worked flawlessly.
FWIW, I strongly recommend reading through the code before considering use of ntopng active monitoring, most especially on a firewall. It does things you might not expect or want, such as ssh probes.
-
@dennypage Are you talking about the built in behavioral checks, because I disable all of those.
-
@bigjohns97 said in Ping monitoring:
@dennypage Are you talking about the built in behavioral checks, because I disable all of those.
The ssh probes are from the os fingerprinting system and cannot be separately disabled.
Enabling active mode gives ntopng license to do things that have no business being on a firewall. I actually would have disabled it in the package if there were a command line option to do so.
-
@dennypage Help me understand what the risks are here, to me this is nothing more than what an nmap scan would do.
-
@bigjohns97 said in Ping monitoring:
Help me understand what the risks are here, to me this is nothing more than what an nmap scan would do.
Ntopng is an autonomous agent, whereas nmap is not. Consider that. You should look at the ntopng code and decide for your self. The best I can tell you is that I have, and I recommend against enabling it.
FWIW, you may have different views on network security that I do.