Allowing random IP/PORT into LAN
-
I can not connect a video conference software because of the randomization. I have watched the logs and the ports are random, and the destination IP is random.
Is there a way to connect in this situation.
-
@wwdot_computers You are hosting a video conference server on your LAN and need to connect to it from somewhere on the Internet? Normally one would use NAT to forward the desired ports. Though, I would limit that connection as much as possible to avoid the entire Internet connecting to it.
uPnP is common in gaming, where the game software tells the router which ports to open while the game is running. uPnP can be enabled on pfSense.
-
@SteveITS Thank you for your response. We do not host the software. It is a video meeting that we receive a link for and sign in to the interface. Everything seems to connect ok except the main meeting window.
I did talk to tech support for about 2 hours yesterday trying to figure out what was going on.
If it helps, I ultimately used a VPN, and it connected to the software without an issue.
I do not want to have the VPN on all the time.uPNP did not work when I turned it on. That may be because I am not too sure how to use that part of the firewall. As I am getting better at the operation of the firewall, there is still a lot that is lacking.
-
@wwdot_computers UPnp would have nothing to do with connecting to some service hosted on the internet.. Nor would you need to do any port forwarding..
Unless you were blocking outbound connection, the default in pfsense is any any - you should be able to connect to anything you can resolve an IP to or any IP directly.
Are you blocking anything in pfsense? IPS, pfblocker? any other rules that would block IP ranges or ports, etc.?
So where exactly did you setup the vpn? On the client? Or pfsense?
-
@johnpoz I have a deny all rule at the very bottom of my LAN rules. If I disable it, then everything works fine. I set the firewall up as a security device. I do not want things calling back home if for some reason I was infected.
The VPN is on the client.
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
I have a deny all rule at the very bottom of my LAN rules. If I disable it, then everything works fine.
So your LAN rules probably don't allow, what your application needs.
We don't know the app, so we cannot tell you, which port or protocol to open to succeed.
-
It is a web app. I click a link on an email from Veterans Affairs. When watching the firewall log, there is a random IP and random Port that are generated when trying to connect.
Not sure if it matters, but I am also having trouble with my Datto Backup. It is offline until I VPN out.
-
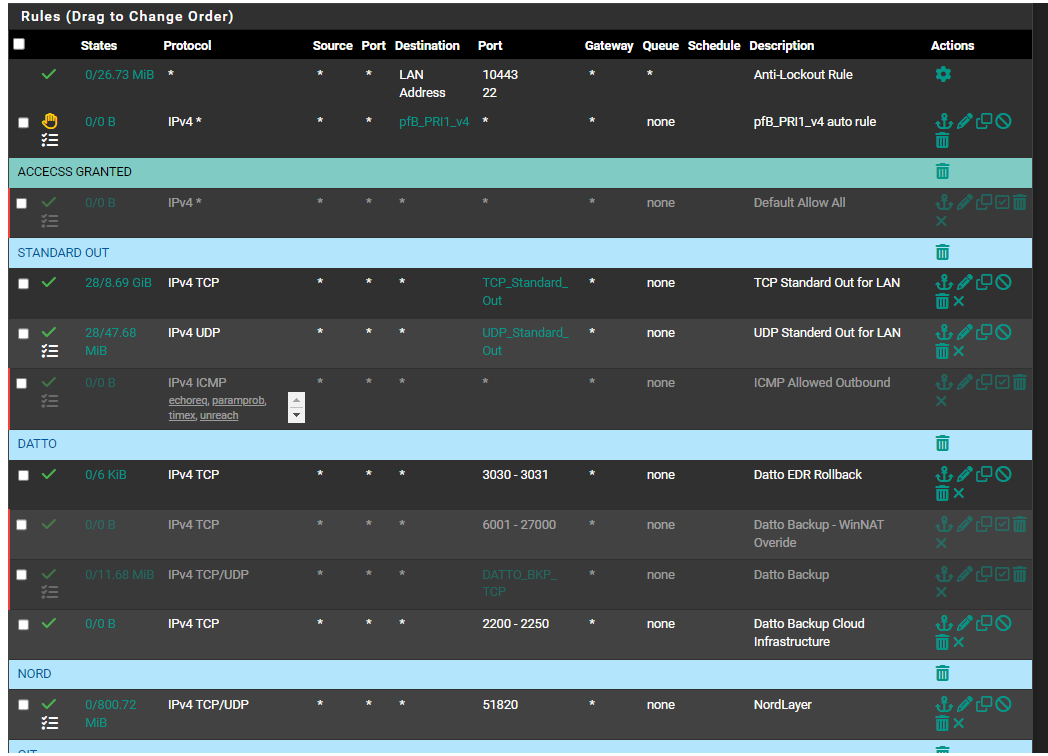
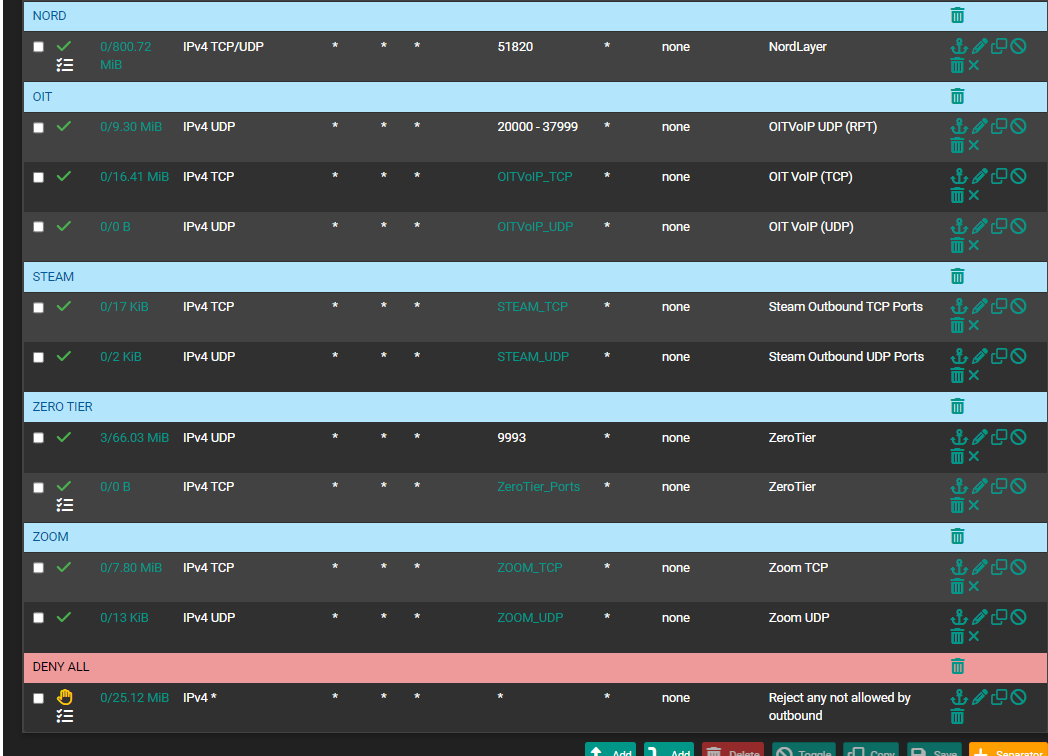
@wwdot_computers post a screenshot of your LAN rules.
-
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
there is a random IP and random Port that are generated when trying to connect.
Well that is not going to work very well when you don't allow what port they are going to use..
Not sure how you think there is something that can magically fix this in a firewall.. Have the owners of where your trying to connect to give you an IP range or ASN that they will be hosting off of, and what possible ports that might be used.. I doubt its all 65k of them.. And they are hosting off something so while it might be a large CDN or something - its not going to be all of the internet
-
@wwdot_computers So, your "_standard_out" aliases or another rule needs to allow the port used. If you don't know the port you can enable that "default allow all" rule up top to allow all outbound.
Edit: or allow the service's IP(s) as John described, using any port.
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
I do not want things calling
Good luck with this approach.
-
@Bob-Dig yeah not really fan of that sort of blocking to be honest either.. If something bad was going to be calling home - they would be doing it over known used ports anyway - most likely 443 these days now that anyone can get a ssl cert for any domain they have control over in like 30 seconds ;)
If you run bad code and it wants to talk outbound your too late if you ask me.. Hey I log outbound traffic from my iot stuff for example - and I do take a look at now and then to see if anything fishy is going on..
Blocking via dns is much easier to stop from going to place you don't want users going to to be honest. Or blocking known bad IP ranges, sure ok.. But then again most bad stuff prob just going to spin up an instance in some CDN or hosting platform anyway. But trying to run a allow only specific your going to be doing that a lot ;) Its a lot of work..
What I find odd is called support, why wouldn't they just have given you the IP (range or ASN) and port(s) when you called them and said you were having issues?
-
Thank you all for responding. I do use a DNS filter for my clients. I kind of figured that there was not going to be a way to dynamically open ports. I was on the phone with support for a while last night. While the guy had some good knowledge of firewalls and networking, I had already tried all of his suggestions. All I wanted to know was the port and IP ranges. He pinged his colleague and had zero luck finding out that information.
I will continue to use my VPN for the video calls.
However, that does not fix my issue regarding the Datto Backup. I have added the ports that need to be open into an alias, as I sure you can see, both the TCP and UDP. There is one port that they are saying needs inbound access:
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)How do I open that up? Like I said, new to pfSense and the like. I have tried creating a WAN rule, I must not have had things correct because the agent still would not connect. I tried NAT, and must have the same issue as the agent just would not connect. However, like the video call, the agent connects fine when on VPN.
-
@wwdot_computers Datto would be on your network so is not related to pfSense, because traffic between PCs on the same interface doesn't go through the gateway. They mean, open that port in the Windows firewall.
-
@wwdot_computers if you want port 25568 that hits you public facing interface (wan) to get forward to some inside machine say 192.168.1.100 that would just be a port forward.
That and then the associated firewall rule that the port forward can auto create for you.. Just need to make sure the rule is in the correct place on your wan so some other rule you might have placed there doesn't block the traffic your trying to allow.
edit: if this is machine A talking to B that are on the same network - as @SteveITS mentions pfsense has nothing to do with that traffic.
-
-
@wwdot_computers but that is outbound traffic - you would have to adjust your rules to allow for the traffic.. So you see that blocked.. By default default deny is logged.. So if your rules do not allow these to talk to something in the cloud, ie the internet then one of your rules is not allowing it.
Did you inherit this set of rules? I would assume someone that created all those would understand how to allow something else..
You say this is inbound
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)I find it highly unlikely that some service you backup to in the cloud would need unsolicited inbound traffic from the internet to some machine behind pfsense.. But that would be a port forward.
-
@SteveITS
It was a joint effort? Under guidence I created the rules. However the person that helped is no longer able to do so. Long story.Would you suggest going back through the rules and starting over?
So the inbound connection:
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)Is really outbound? How does that track? It seems that they are requesting an inbound connection?
-
@wwdot_computers see my edit.. I have never heard of some backup service to the cloud that would require you to open a port from the internet to your server your backing up - that makes no sense at all.
Unless you have turned off default deny logging that is logged, and your last reject rule is set to log - so if pfsense blocked something from it would be logged