DNS Resolver Enable SSL/TLS Service - automatic interface response routing behavior
-
Hi
I am setting up a pfSense to accept DoT (DNS over TLS) queries on port 853 and to do that you enable it here:
Services --> DNS Resolver --> General Settings --> Enable SSL/TLS Service
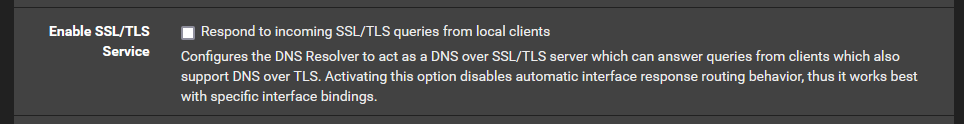
On the description it has the following message:
Activating this option disables automatic interface response routing behavior, thus it works best with specific interface bindings.
I have read the help files but cannot find anywhere what this means and what will change. Can someone give me a simple explanation as what this means and if there is anything I should do?
Thanks
-
That works for me


 :
:Use the default :
Then, when Saved and Applied, fact check :
[24.03-RELEASE][root@pfSense.bhf.tld]/root: sockstat | grep '853' unbound unbound 563 7 udp6 *:853 *:* unbound unbound 563 8 tcp6 *:853 *:* unbound unbound 563 9 udp4 *:853 *:* unbound unbound 563 10 tcp4 *:853 *:*this says : unbound listens on All interfaces, using TCP and UDP, on port 853.
Yeah; strange, UDP and TLS .... that new to me, but why not ^^Responds to incoming SSL/TLS queries from local clients" only f you don't trust your own 'LAN' networks, for example : you use Wifi stuff and you think some one has broken into your Wifi ....
If this is not the case, don't bother yourself with it. -
@Gertjan I have no idea what you are on about, perhaps lost in translation

What does the below statement mean, I understand the other settings:
Activating this option disables automatic interface response routing behaviour, thus it works best with specific interface bindings.
-
@shoulders said in DNS Resolver Enable SSL/TLS Service - automatic interface response routing behavior:
Activating this option disables automatic interface response routing behaviour, thus it works best with specific interface bindings.
Some one was asking that question a while ago :
The answer was :
The warning there is about unbound's behavior when bound to multiple interfaces, especially bound to all. With that box active, it responds back to the client from the closest interface routing-wise for UDP. With it inactive, unbound is smart enough to always reply back to the client from the address to which the original query was sent. That behavior doesn't matter for most. Primarily things like DNS over IPsec tunnels are affected.
Don't try to translate this

-
@Gertjan thanks, really helpful. Still I don't know why Netgate have not fixed this. Enabling DoT should just be that and not affect anything else.