Allow access from Europe
-
@chudak I do it slightly different I do a Geo block on a bunch of countries and allow IPsec from everywhere else.
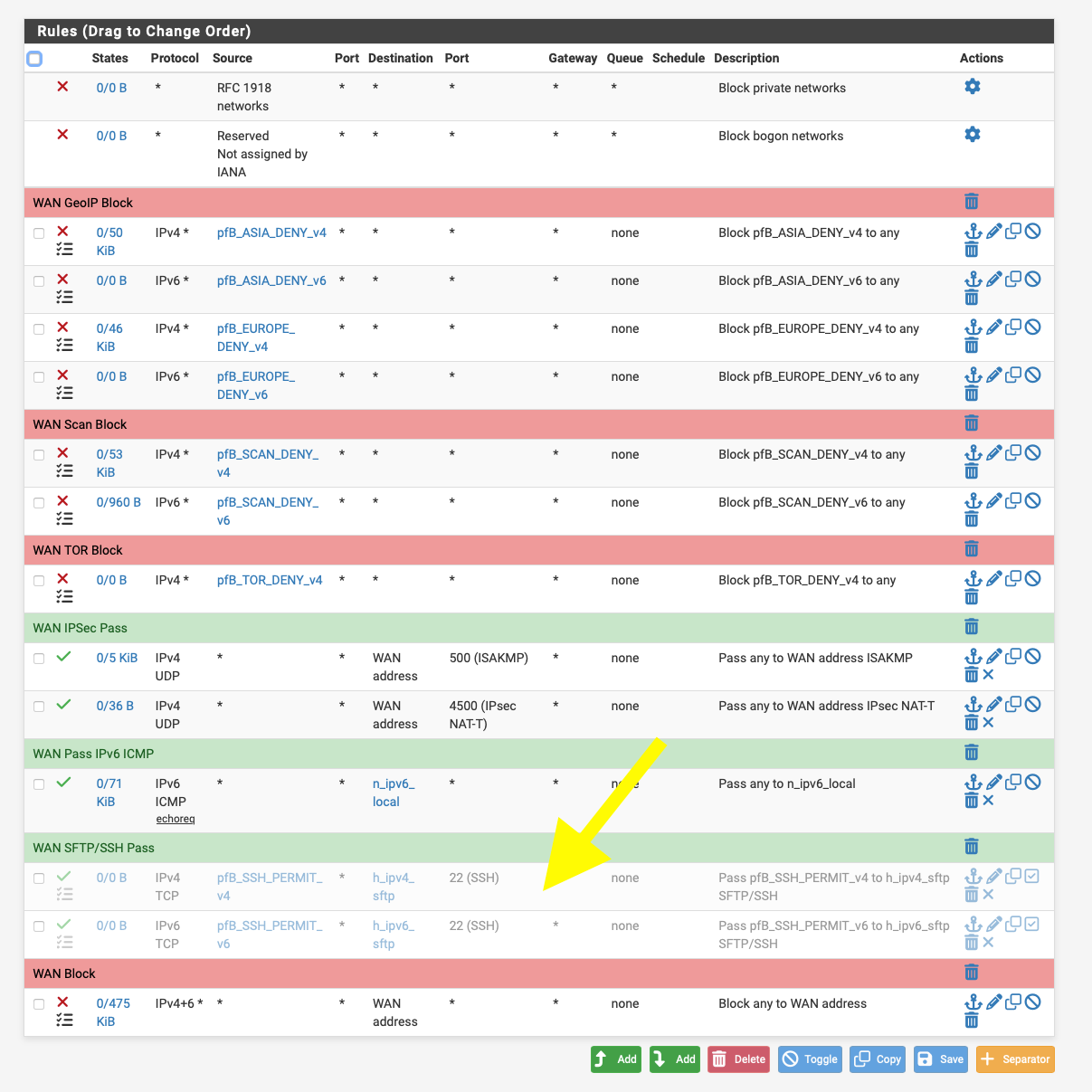
But if you wanted to enable certain countries you'd use something like my disabled ssh / sftp rule.
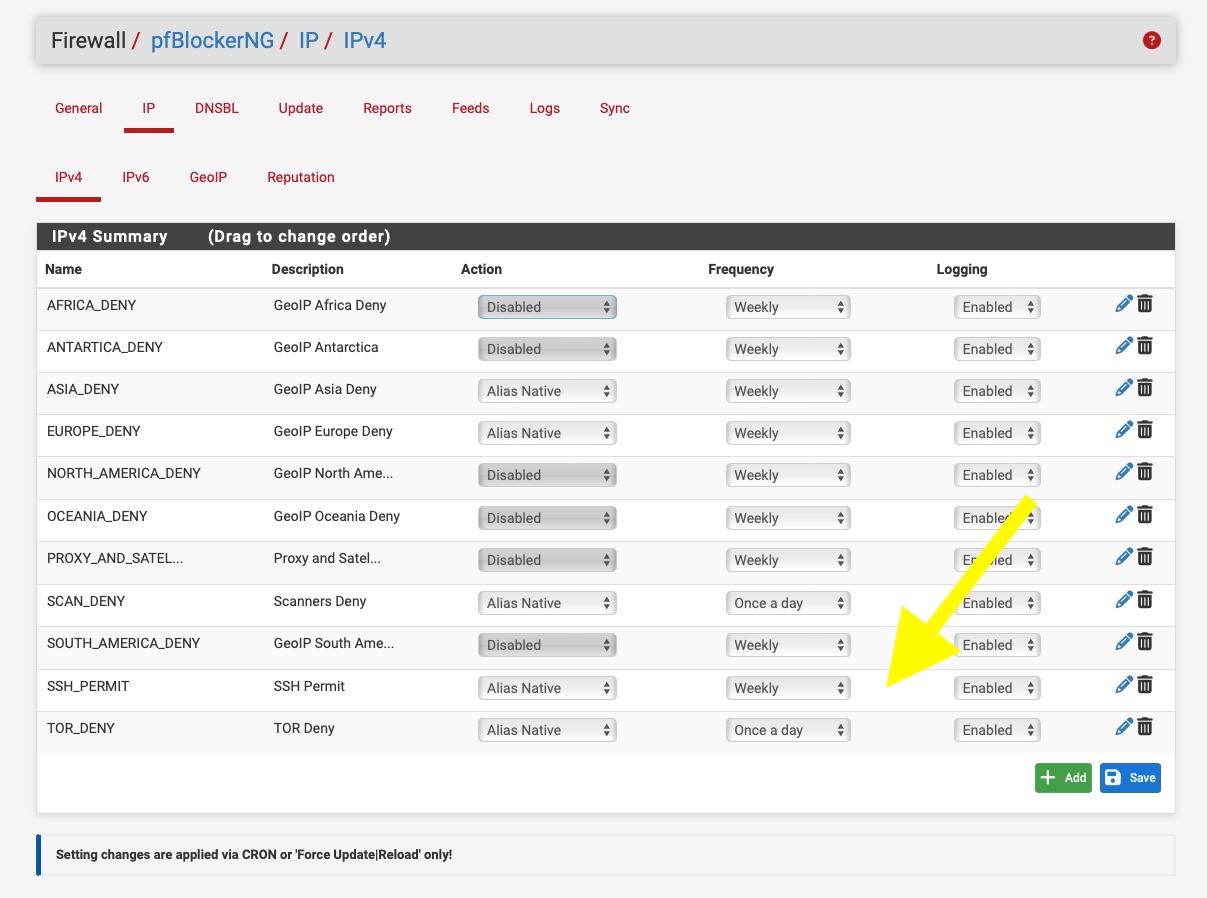
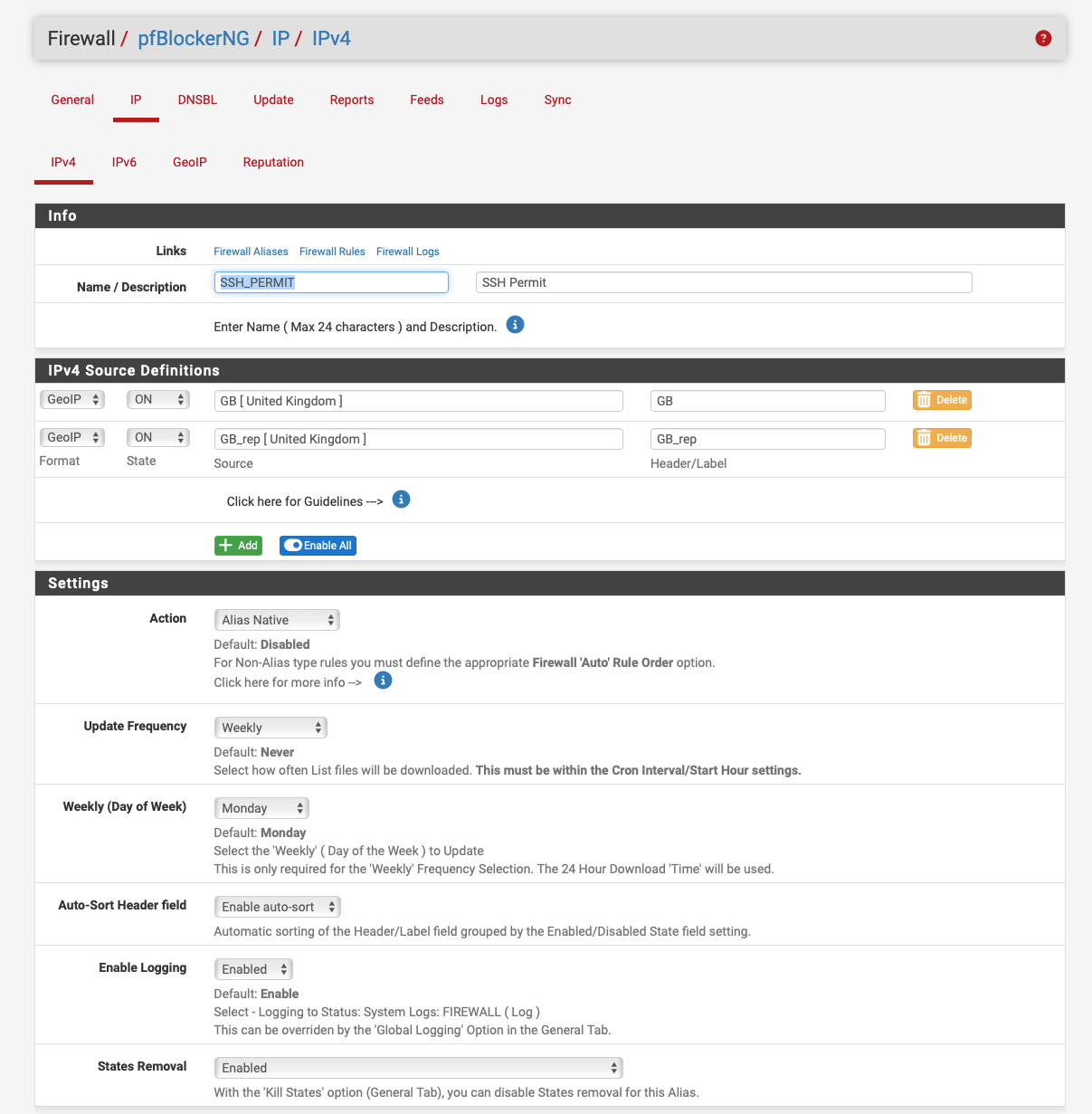
You just need to enable the country pre visit and hope the country is in the alias.
Is your issue the rule order in pfBlocker?
-
One option is to setup a dyndns account and always allow access from that. Then you can always update it from where ever you are and connect from there as a fallback option. Though you may have to wait for it to update at the pfSense end.
-
I think my issue is pBlockerNG
Thx it's very interesting.
I need to allow OpenVPN only.
I suspect TaleScale does not care.And do you test?
-
@stephenw10 said in Allow access from Europe:
One option is to setup a dyndns account and always allow access from that. Then you can always update it from where ever you are and connect from there as a fallback option. Though you may have to wait for it to update at the pfSense end.
I don't get it.
Can you elaborate?I have DDNS names already setup
-
Install the dyndns client on your laptop, for example. Then run the update from where ever you are. Have a rule that passes traffic from that above the pfBlocker block rules.
-
@stephenw10 said in Allow access from Europe:
Install the dyndns client on your laptop, for example. Then run the update from where ever you are. Have a rule that passes traffic from that above the pfBlocker block rules.
I see
Wonder if I can do this trick using the same DDNS name on different machines: iPhone, iPad etc?
What I am not clear is - why do you think that the FW rules will win over pfBlockerNG block, if used from overseas.
-
@chudak said in Allow access from Europe:
why do you think that the FW rules will win over pfBlockerNG block, if used from overseas.
You have to put them above the pfBlocker rules as I said. Otherwise pfBlocker will obviously block that traffic first.
@chudak said in Allow access from Europe:
Wonder if I can do this trick using the same DDNS name on different machines: iPhone, iPad etc?
If they are all behind the same public IP address then sure. And you'd only need to run the client on one of them.
-
@stephenw10 said in Allow access from Europe:
@chudak said in Allow access from Europe:
You have to put them above the pfBlocker rules as I said. Otherwise pfBlocker will obviously block that traffic first.
Of cause, I forgot about the order of the rules!
@chudak said in Allow access from Europe:
Wonder if I can do this trick using the same DDNS name on different machines: iPhone, iPad etc?
If they are all behind the same public IP address then sure. And you'd only need to run the client on one of them.
Col, so I will use it on iPhone iPad all I need is to find a good DDNS iOS client.
Any clues how to test it from the US?
-
@chudak my rule is for enabling ssh from the UK where I'm based so its easy to test, I just switch the two rules on when required, otherwise they are off.
-
@chudak said in Allow access from Europe:
Any clues how to test it from the US?
You could sign up to a VPN provider create a connection to Germany, policy route a subnet hanging via the German VPN connection and then try and run your VPN connection to home over it.
-
@chudak said in Allow access from Europe:
Any clues how to test it from the US?
Just run it from somewhere in the US and then try to connect. You will see states and traffic on your pass rule if it's being used. It will only be used if the dyndns is being correctly updated and resolved.
-
@stephenw10 said in Allow access from Europe:
Install the dyndns client on your laptop, for example. Then run the update from where ever you are. Have a rule that passes traffic from that above the pfBlocker block rules.
Regarding the FW rule.
I added an alias and a new rule before pfBlockerNG in the floating section.
So far I see no traffic
-
Yes just use the hostname in an alias. By default pfSense resolves it every 300s. You can reduce that if required in Sys > Adv > Firewall but you probably don't need to. The TTL is often higher than that anyway.
-
@stephenw10
Did you actually do this kind of set up?So far I don't see it's working.
Here is what I have
added DDNS "full_access"
added alias "full_access"
added a rule on WAN interface to all protocols any destination
placed the rule in the Floating above pfB rulesAt this point, I assume I can access all my network resources from any network from my iPhone as long as DDNS "full_access" is my iPhone IP address
And it does not work so far :(
-
Check that the rule is still at the top of the list. pfBlocker can re-create it's rules at the top of the list depending on how you have it set.
Check the floating rule is set to quick.
Make sure pfSense can resolve 'full_access' to the correct IP address.
-
@stephenw10 said in Allow access from Europe:
Check that the rule is still at the top of the list. pfBlocker can re-create it's rules at the top of the list depending on how you have it set.
Check the floating rule is set to quick.
Make sure pfSense can resolve 'full_access' to the correct IP address.
I can't make it work :( and pfB keeps moving all rules on top
But found a good site to test global ping when playing with pfB
https://www.jsdelivr.com/globalping -
Yes pfBlocker puts it's rules at the top by default. You need to change the rule handling to allow custom rules above it.
Or you can use a pass rule for the dyndns name in pfBlocker so it gets added at the top anyway.
Is pfSense resolving the host correctly?