Squid V6.10
-
@Patch mine is directly from pfSense official freeBSD repo. I could never install the other version because I have an ARM processor
-
@JonathanLee I built my own setup, using Community Edition.
It won't let me pick anything other than "Current Stable Release (2.7.2)" in System/Update/Update System > Branch.@Patch I don't have those in the "Available Packages" list.
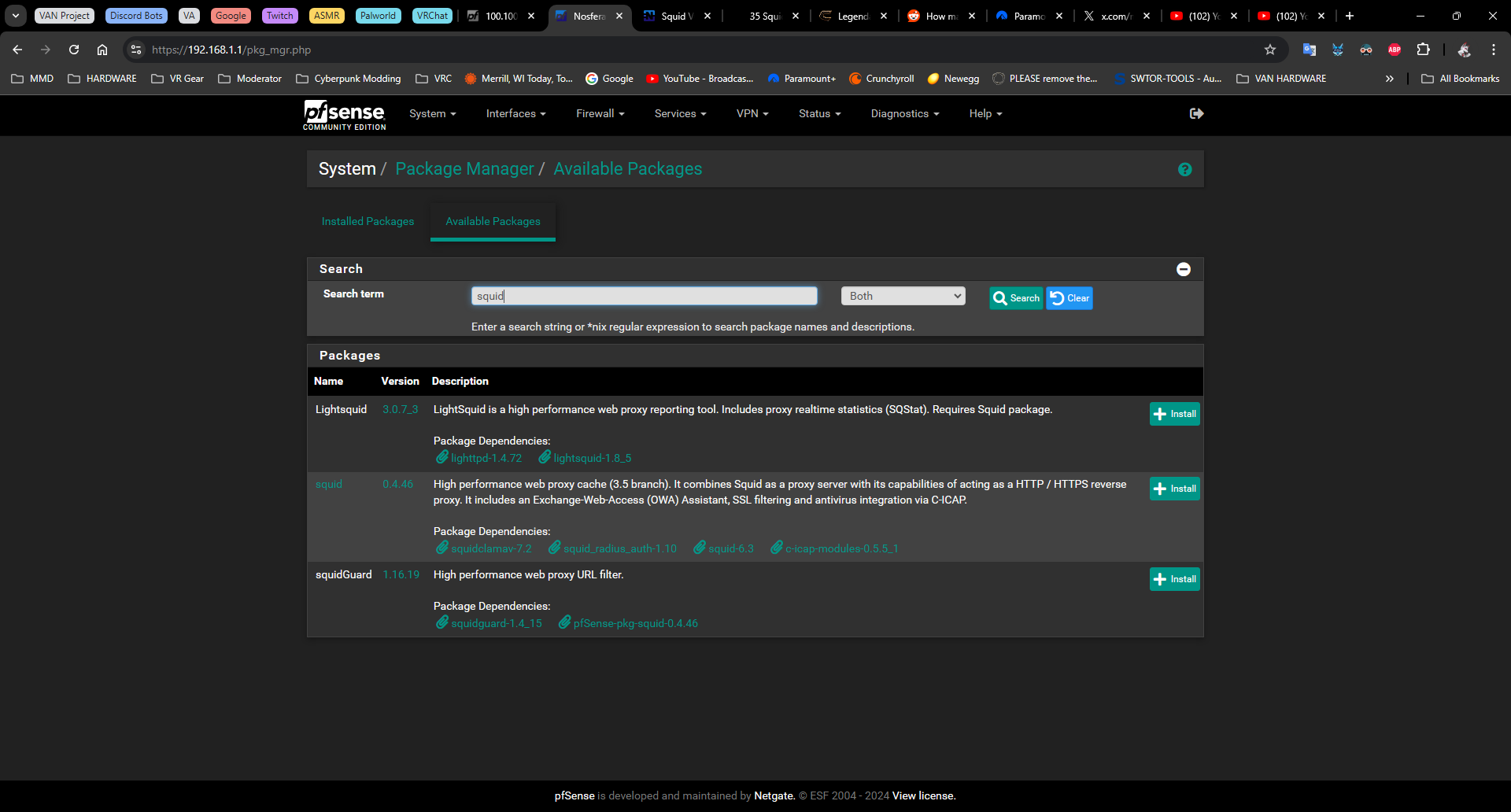
-
@Nafryti did you run the fetch command in the post I linked above first.
-
@Patch OH... ok, I'll give that a shot on Skunkworks and if all goes well I'll deploy it on the primary.
-
UPDATE 08/29/24:
My HyperV instance of pfSense nicknamed "Skunkworks" has stopped connecting to the internet and I have no idea why, for all intents and purposes, there should be a completely unobstructed pathway from the Modem to the VM, and yet, it just can't see the netgate update server anymore. I haven't messed with any settings since my last post and was finally going to buckle down and give this a shot and it decided it had enough of me. I'm grateful the Primary isn't screwed up any, going without internet is entirely unacceptable. Seeing how the network usage is far more than any OTC box router can handle, but not quite Enterprise grade, I'll touch back on this with a fresh installation of Skunkworks, and well after my anxiety settles down.@Patch said in Squid V6.10:
@Nafryti did you run the fetch command in the post I linked above first.
I'm assuming you either did that in the terminal access or using the Package that allows you to enter commands from the WebUI? I suppose Telnet is an option too, but that'd be at the outer extents of my ability level. Last time I tinkered with Telnet was to reprogram an old Dell Managed Switch I was playing around with, and that took some nightmarish re-wiring of a serial COM cable, still have the cable too.
-
@Nafryti said in Squid V6.10:
I'm assuming you either did that in the terminal access or using the Package that allows you to enter commands from the WebUI?
Any of
- HyperV terminal
- pfsense -> Diagnostics -> Command prompt -> command
- ssh terminal
-
@JonathanLee aren't you running the non-pfsense maintained version from @lg1980
https://forum.netgate.com/topic/186331/new-squid-6-7-and-clamav-1-3-0/7
-
@FoolCoconut No. I have an Advanced ARM processor. You remember Cirix processors?
-
Dang, the updated one fixed all the security issues but the GUI has some small issues
-
Well, I have a lot to do and sort out sometime soon, and I've been procrastinating for far too long. I still have not been able to get a new Skunkworks loaded yet, I've got to reorganize components, and then I'll be able to finally start testing again.
My wish for 6.10 to finally be reevaluated by NG hasn't changed, I haven't looked, but I know from experience how stubborn some devs can be over things.
There was and imho still is a demand for such a caching service, not everyone has a completely separate machine to cache downloads to, but when you DIY a router, with a 1TB HDD and run the OS on the RAM, then you honestly have the freedom to setup something like that, but only if there isn't any complacency.
-
Now that the Vulnerabilities are fixed Upstream, I see no reason why this Package is still deprecated. I would love to deploy it for my Customers but can't reasonably do so :(
-
@ICS_DOS Outside of the vulns found and/or fixed there is still the fact that there is no maintainer for Squid for pfsense. There is a lot wrong with the package and unless someone steps up and volunteers their time to fix all the glaring problems i see no reason why netgate would still have this package in the repo.
-
This post is deleted! -
@michmoor said in Squid V6.10:
"still the fact that there is no maintainer for Squid for pfsense."
That's not true at all, there is someone from NG (at least that's my understanding of the name: "marcos-ng") updating the repo.
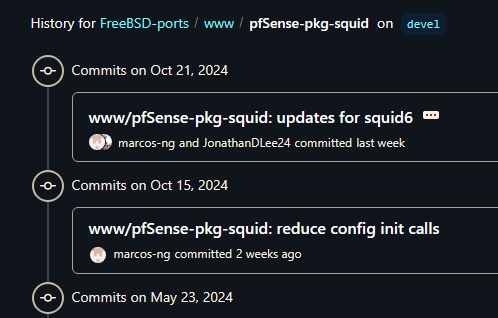
@michmoor what problems, if you don't mind my asking?
-
I do not think that he still uses this package anymore for a while. I would search out others for help.
-
@Nafryti Yes there were commits done but that does not mean there are maintainers. I repeat there are no volunteers maintaining this package on pfsense.
Read the redmine notes regarding those Git commits. Its clearly stated by the engineer who pushed the PR that Squid is going away.One of the biggest issues is that transparent mode is useless and broken. That alone makes the package unusable for most.
https://redmine.pfsense.org/issues/14390There are those in the forum who still use the package daily like @JonathanLee who is very active with it and probably is a good resource for all things Squid on pfsense.
-
Squid itself has been updated with many of the fixes per this email.
Just got an update on Squid working on bug fixes. Looks like 7 is the version that mitigates most of all of them.
"The Squid Project apologizes for being late in responding to the
publication of 55 vulnerabilities disclosed by Joshua Rogers of Opera Software
at https://megamansec.github.io/Squid-Security-Audit/We thank Joshua for discovering these bugs and sharing their details with us.
The surprise publication caught us off guard, but Squid
developers had worked on addressing some of the disclosed vulnerabilities
since before that publication. This message summarizes Squid's status on
October 9th, 2024.As of Squid v6.8, the vast majority of high-impact vulnerabilities have been
addressed. The following disclosed vulnerabilities are still present:Vulnerability “strlen(NULL) Crash Using Digest Authentication”
This vulnerability is still present in Squid v6.11. A fix is expected in Squid
v6.12, due any day now.
Digest authentication is disabled by default; the current workaround is
to avoid Digest authentication.To verify whether your Squid configuration is vulnerable, check whether it
contains "auth_param” directive. Configurations with auth_param directives
mentioning "digest" scheme may be vulnerable.pipeline_prefetch (HTTP pipelining of client-to-Squid requests)
All reported pipelining-related vulnerabilities may still be present in Squid
v6. Pipelining code will probably be removed in master branch and become
unavailable in Squid v7. Pipelining is disabled by default.If you do not need pipelining (or do not know for sure that you need it), do
not enable that performance optimization.To verify whether your Squid configuration is vulnerable, check whether it
contains a pipeline_prefetch directive. Configurations containing a
pipeline_prefetch directive set to a positive value may be vulnerable.ESI (Edge Side Includes)
Most reported ESI-related vulnerabilities are still present in Squid v6. ESI
code has been removed in the master branch and will not be available
in Squid v7.
ESI is disabled in the default build starting with Squid v6.10. In earlier
versions, ESI code is enabled by default, but the risk is moderate because
exploiting this family of vulnerabilities requires Squid to be
configured as a reverse proxy for a malicious origin server.If you do not need ESI (or do not know whether you need it), disable it with
--disable-esi (default for Squid v6.10 and later).To verify whether your Squid build is vulnerable, run squid -v. Squid v6.9
and earlier versions may be vulnerable unless the output contains
--disable-esi. Squid v6.10 and later versions may be vulnerable if the
output contains --enable-esi.Squid v5
Some fixes were backported to Squid v5, but we lack the resources necessary to
support that old version. Folks running Squid v5 and earlier versions should
either upgrade to the latest v6 release or rely on their
integrator/distributor for support.--
Francesco Chemolli
Squid Software Foundationsquid-users mailing list
squid-users@lists.squid-cache.org
https://lists.squid-cache.org/listinfo/squid-users"Version 7 is where most almost all of the issues are resolved with. Again some changes were made that would require a Netgate php-software used to configure Squid to Squid software convergence test and tune up. I love Squid it is like a swiss army knife.
-
@JonathanLee I see all these updates, all this work going on for Squid, and everyone saying it's either "useless" or "still full of vulnerabilities" what is going on here?
Is there some kind of secret here? What's up, I get that months ago it was exposed for vulnerabilities and then what happened? did these people just pull the wool over their eyes and say "oh well, it'll never be fixed." and no matter what Squid Devs do it's all in vain due to the lack of vision?
If not with Squid, then what can I use to Download Cache Steam downloads?
-
@Nafryti we can hope they fix it. I do know Opensense has updated Squid and continues to support it last time I checked. So I do hope pfSense continues to support it. We know the vulnerabilities are fixed now so that should not be an issue anymore. I know it was still listed on the snapshots last time I checked. The php code does need some software convergence with the status pages etc now that vulnerabilities are mitigated.
Yes I hope it is updated soon. I am thankful it is still listed
-
@JonathanLee Curious. Does OPNsense Squid have the same problem with transparent proxy as pfsense or have the devs over there fixed it?