Need Help with NAT reflection
-
@viragomann
What do you mean, how did I configure the gateway group?
I changed from my previous ISP to the new one and set it as Tier 1 and the additional ISP I have is set as Tier 2 the Trigger Level is set to "Packet Loss or High Latency"The default Gateway is set to the Gateway group I configured
In all the first rules on all interfaces (the rules that give an internet network to the interface) a default is set.
Currently, both ISPs are active. -
@Itay1787
I'm wondering, where NAT reflection comes into play here. Without a NAT rule, there would be no NAT reflection at all. And apart from the one on the VPN interface, and this would only have any affect if you map the requested host name to the VPN clients IP.Anyway I think, this could only work with a masquerading rule (outbound NAT, S-NAT).
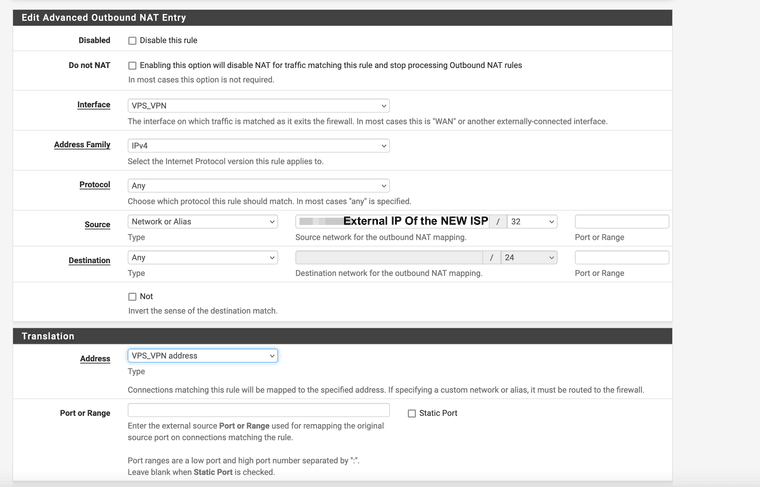
I'd add the rule to the VPN interface of the VPS. You can limit it to the source of your public IPs. This way, you will see the real source IP if the access is coming from any other address. -
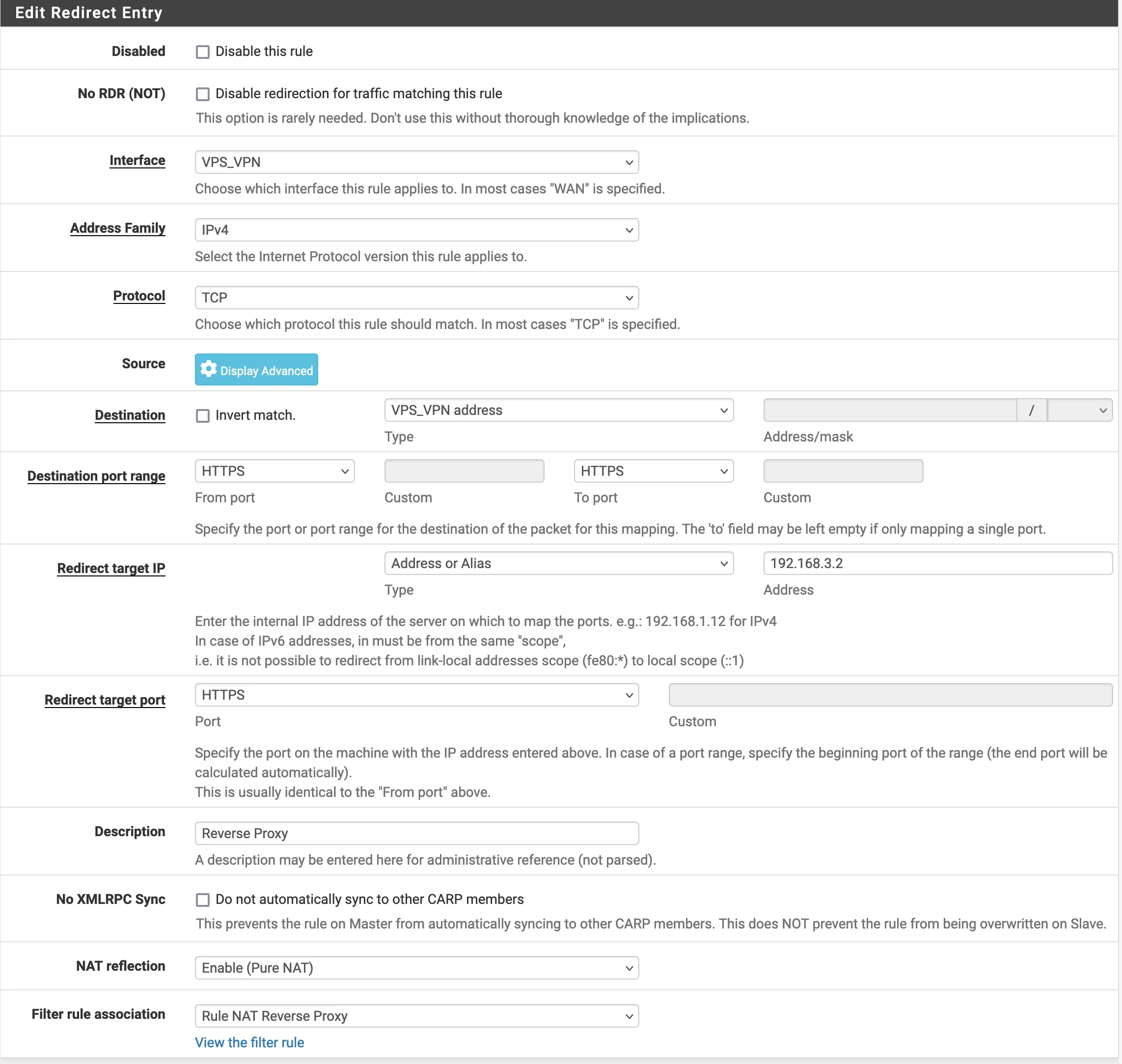
@viragomann hey, I tried to add this rule but it doesn't work. Did I do it correctly?
-
@Itay1787
If this is on the VPS site and the alias in the source includes both of your public IP, then yes, I'd expect it to work.It should translate the source address in packets to the server VPN address on matching traffic.
You can verify this with packet capture.If it doesn't work ensure the the request packet is routed out on WAN properly.
-
@viragomann No, This is my Location the VPS is Debian Server the run OpenVPN server with iptable rule to do 1:1 on the NAT VPN.
The thing that I don't understand is why it works without any rules (except the port forward) on my previous ISPs and now it doesn't works with the new one
-
@Itay1787 said in Need Help with NAT reflection:
No, This is my Location the VPS is Debian Server the run OpenVPN server with iptable rule to do 1:1 on the NAT VPN.
Maybe it also works if you do it on your site, but then you have to change the interface to that one, which is facing to the destination server of the port forwarding (e.g. LAN) and the translation to the respective interface address, but not sure.
The thing that I don't understand is why it works without any rules (except the port forward) on my previous ISPs and now it doesn't works with the new one
Possibly you have other NAT rule with reflection or your ISP router did reflection.
As mentioned above, I would use any other source, which is connected to the interface, to verify the routing. Routing traffic out to the internet and back in on another interface is a hack to me.
-
@viragomann said in Need Help with NAT reflection:
Possibly you have other NAT rule with reflection or your ISP router did reflection.
This is the weird thing, The ISP's connection was connected directly to pfsense so there was no other router present.
I know there are other ways to do what I want. But I want it to work. I feel like something is broken that it's not working.And I have no idea what rule to put in NAT.
I tried everything as I said.
any in Destination and any in Source didn't help... -
@viragomann Could it be that PPPoE has something to do with it?
It's just that the new ISP uses itI also checked if the pfsense connects to the VPN through the other ISP and not the same ISP I connected through.
not working
I checked every possible NAT rule
does not help
The conclusion I came to:
As long as the client device tries to go to the public host names NOT through the new ISP it works (If I connect through a VPN the client - then I work, if I do policy routing - switching the gateway via pfsense to the client device that I will connect to the internet via the other ISP then it WORKING. )
Then I thought maybe the ISP blocks NAT reflection because maybe it detects it somehow...
But if I forward the ports through the new ISP directly
and activate NAT reflection it works too.... something very strangeI'm out of ideas as to how to fix it...
-
@Itay1787
As I said, it's not fully clear to me, how this has worked before. Without knowing all your rules, that's hard to say.A suspicion is still an asymmetric routing issue. To rule this out, enable the logging of the default deny rule, try to access your server, than check the firewall log for related blocks.
-
@viragomann Hi, I have new information.
After some tests
that I install pfsense on a VM to check if I connect to PPPoE through it and then do "CG-NAT" to the main pfsense to see if it will work.
And it works!!!!!! The only thing I changed in the main pfsense is in the gateway group that the interface from the virtual pfsense will be the main one and all traffic will go through it!What it looks like is as long as the external IP address of the client trying to access is the same external address that is visible in pfsense then it just won't work.
Now I have no idea what rule and where I should put it to solve this problem. I have never encountered this problem in my life.
So I don't even know what to call it to google it