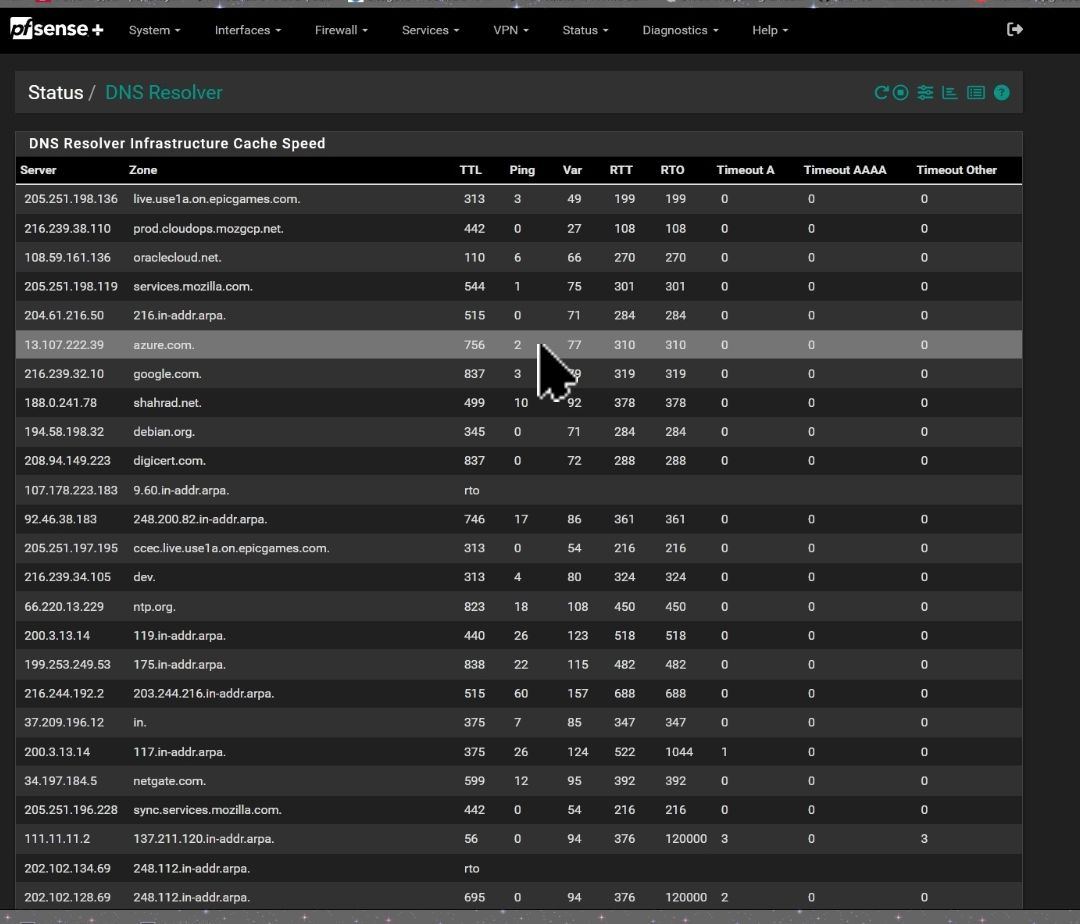
external names (amazonaws.com) resolution when enable DNSforwarder or DNS resolver.
-
hello,
Today I realized that I'm getting issues to resolve aws names like:
"78883e02f46a329474aeb6e83a544834.gr7.eu-central-1.eks.amazonaws.com"
using the pfsense diag_dns.php webpage.
if I disabled both dns forwarder and dns resovler it can lookup the ip address,
however
as soon as I enable any of them it includes de 127.0.0.1 query server and gets host not resolved.Any idea on what setup I'm doing wrongly?
-
@guybrush2k4 said in external names (amazonaws.com) resolution when enable DNSforwarder or DNS resolver.:
if I disabled both dns forwarder and dns resovler it can lookup the ip address,
root@ns311465:~# dig 78883e02f46a329474aeb6e83a544834.gr7.eu-central-1.eks.amazonaws.com +short 10.148.181.246 10.148.181.157and these two are non routable IPs aka rfc1918.
So, useless on a classic router WAN interface, as you and route to it.Don't take my word for it, use the unbound manual instead, but unbound (and the ancient forwarder dnsmasq) will exclude this kind of DNS answers. These is probably a unbound (custom ?) option to override this.
-
@Gertjan
Thanks for your replay, it was really verry usefull.
I did not even thought about what ip address was behind that name.
I understand now after a couple of youtube videos that dns resolver = unbound and dns forwarder= dnsmasq.
and I switched to dns resolver.anyway I still need some how this to be resolved.
I enable debug info. and as you mention looks like unbound is bloquing that answer.
I hope you can see in the picure the query is sanitized.
I will need to figure out if it is posible wo white list some options and how safe it would be.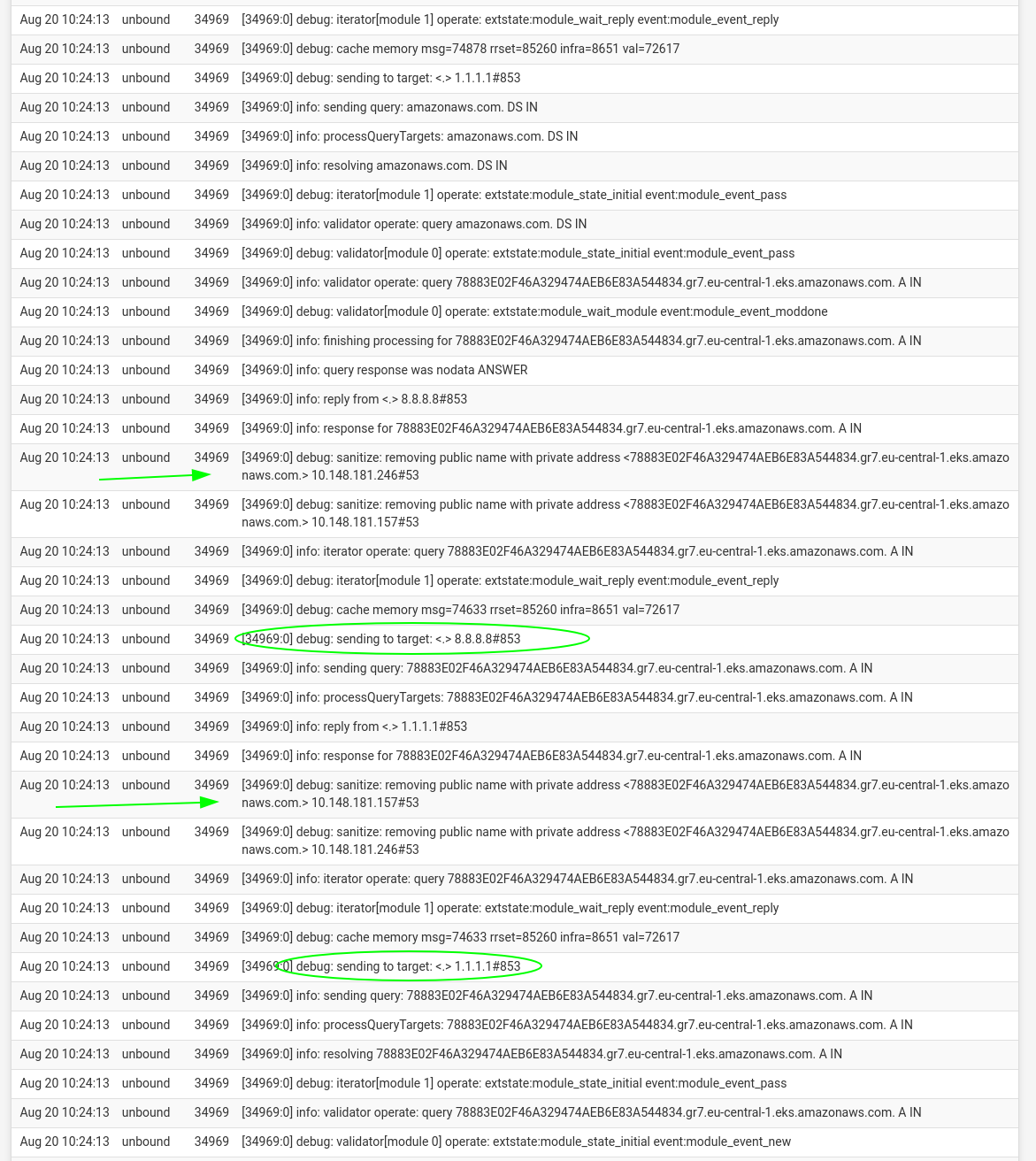
But anyway, Thanks for your answer it was really helpfull
-
@guybrush2k4
I complete my previous message as a quick google search gave me the answer:
https://blog.jenningsga.com/pfsense-dns-resolver-and-private-domains/
I need to add this. to the custom options:
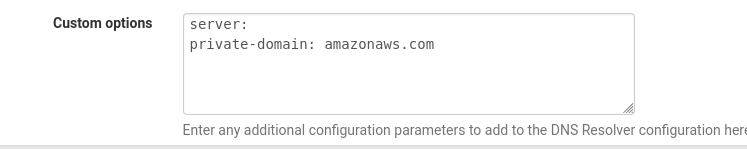
So that now it allows weird things from amazonaws.com.
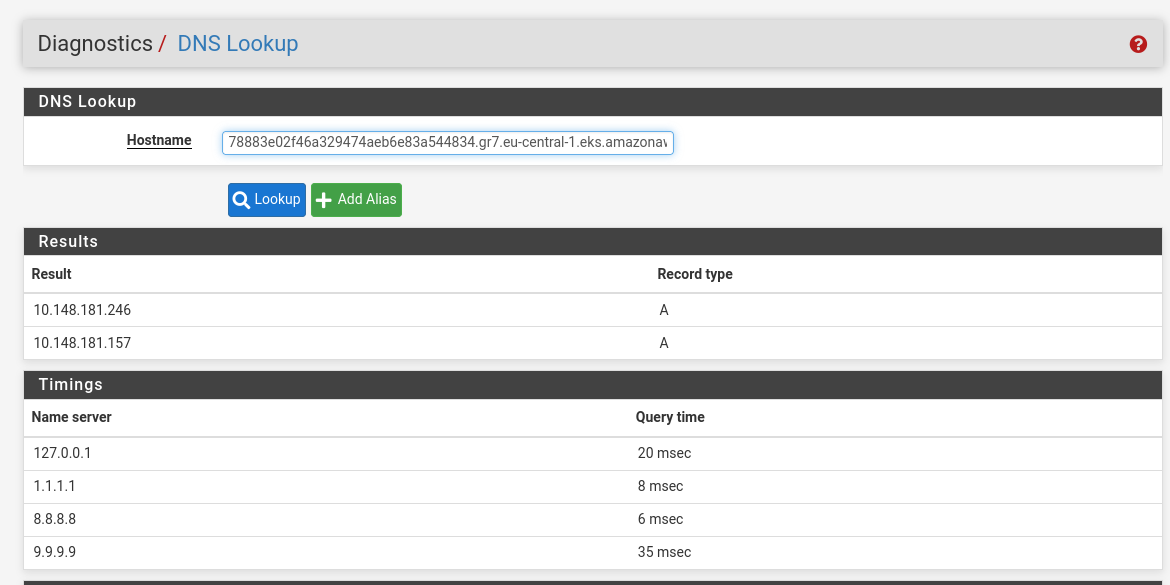
Thanks every one for your help. -
Ditch these :
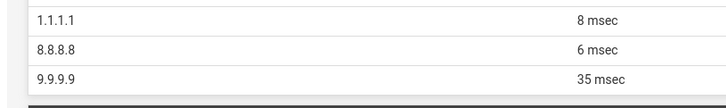
as the resolver doesn't need them.
A resolver doesn't need another resolver.
That is, if 1.1.1.1 8.8.8.8 9.9.9.9 pay your for your DNS traffic, then it's ok you send them your info. -
@Gertjan
uhmm really?
can you elaborate a little bit more? I though it was good practice kind of use those clodflare, google, quad9 servers as dns servers.
to whom is querying unbound if you do not have dns in the general settings? -
@guybrush2k4 said in external names (amazonaws.com) resolution when enable DNSforwarder or DNS resolver.:
uhmm really?
Because you said so :
@guybrush2k4 said in external names (amazonaws.com) resolution when enable DNSforwarder or DNS resolver.:
I understand now after a couple of youtube videos that dns resolver = unbound and dns forwarder= dnsmasq.
and I switched to dns resolver.So I presumed you saw the light. Not entirely, then.
Let this sink in :
A resolver needs nothing (from you, me or Netgate) to work.The : "you need 1.1.1.1 8.8.8.8 9.9.9.9 has been thrown in your head because they; the 1.1.1.1 8.8.8.8 9.9.9.9, invested millions ( in $ or €) if not more so that you have that impression".
It's the other way around, 1.1.1.1 8.8.8.8 9.9.9.9 need YOU because they need your DNS as it is worth .... well... many factors more as the millions they've invested.And yes, in the past, when bandwidth was very expensive and slow, YOUR ISP gave you their DNS, so you had a short and fast path to a/their DNS (a resolver) so your ISP uplink (the so called POP's) where less charged with huge quantities of always identical DNS traffic from their clients.
That's over now, we all have xxx Mbits/ sec and a POP link cost less as a 'Happy meal' (per day ..).See this one : How DNS Works - Computerphile
( and if you have some time left, see all their video's, they are pure gold )Can you tell me who told you that you need 1.1.1.1 8.8.8.8 9.9.9.9 ?
-
If you can not resolve then sure you would need to forward - but to be honest forwarding to 3 different ones is not good practice. For starters quad9 is a filtering dns, while google says they don't..
Unless the different services filter exactly the same stuff, its not a good idea to have them all listed. Because don't really know which one will get asked at any given time. So filtering might work on one, but if you ask a different one it might not be, etc.
While generally if you are not setting up the filtering and they only filter bad stuff is not too bad, but if one of those was like opendns or something that you set like categories to filter, like p0rn, gambling, etc. and one of your other ns doesn't filter those - then your won't work 100% of the time.
Even if they just filter bad stuff if not the same - you might be run into an issue where something doesn't resolve at times, but at other times it does which could be confusing to what is going on, etc. And lead you down a rabbit hole figuring out why..
If your going to forward, I would pick one of the services and use them.. These services have very reliable anycast networks setup to make sure that dns works.. The odds of one going out is pretty slim, and they serve up dns to most of the planet.. They rarely ever go out.. There is little point to using all of them.
If what your concerned with is that your dns always works - then resolving is better anyway. Since why sure some specific domain might go down, if you can not talk to their authoritative ns. Dns as a whole is not going to fail, if the roots go down, or the gtld servers do then dns would be out for the whole planet anyway.. Since where you forward, resolve at somepoint as well.
-
@guybrush2k4
Long story short
And then you see