Added a second WAN, no way to get forwarfing NAT working on the 2nd
-
@Bob-Dig Yes, each WAN has it's own nic and is connected to Internet through its connections (1 is radio, the second fiber).
-
@Bob-Dig There is no NAT Reflection, I do all the tests from outside. From inside, all computers have Internet. To access websites, I use internal dns configd con local IPs.
But the problem I have is from outside. -
@vincentvije
Do the packets even arrive on WAN2 of pfSense?
Enable the logging of the filter rule and see if you get hits.Where did you define the rule for allowing incoming traffic? On the WAN2 interface, on an interface group or a floating rule?
-
@viragomann Thanks a lot. Yes they arrive, I connected directly on a switch in the WAN2 side. I can ping Internet and the ISP router 80.17.182.97/28, other devices (we have several public IP) like 80.17.182.99/28, but not the pfSense WAN2 IP 80.17.182.98/28.
For the rules, I, think I've the same as with old WAN connection.!
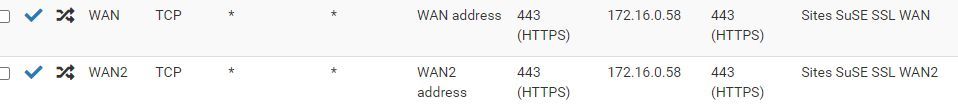
Firewall NAT :
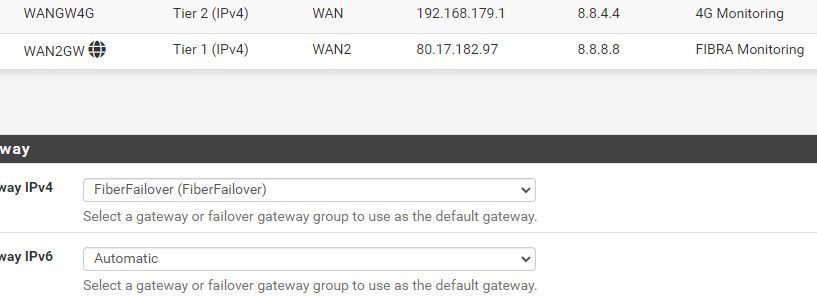
Screenshot - 9_4_2024 , 5_18_58 PM.jpgSystem / Routing / Gateways :
System Routing :
Thanks a lot. I hope you've some idea.
-
@vincentvije said in Added a second WAN, no way to get forwarfing NAT working on the 2nd:
Yes they arrive, I connected directly on a switch in the WAN2 side.
Do you have an IP in the WAN2 subnet? A public one?
I can ping Internet and the ISP router 80.17.182.97/28, other devices (we have several public IP) like 80.17.182.99/28, but not the pfSense WAN2 IP 80.17.182.98/28.
This presumes, that there is a rule on WAN2, which allow ICMP echo requests.
The outbound NAT comes only in play for outbound traffic. It doesn't matter for inbound.
So even if WAN2 is the default route, you cannot access the server behind pfSense from outside?
-
@viragomann Exactly.
But I then doesn't find where are inbound rules.
Every place I checked had the same kind of config for WAN and WAN2.
WAN answer ping and forward to swebserver, but WAN2 not...In firewall / Rules / WAN :
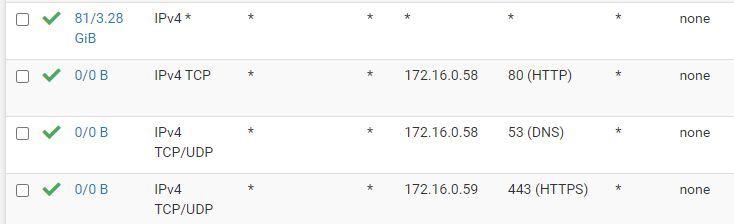
And WAN2 :
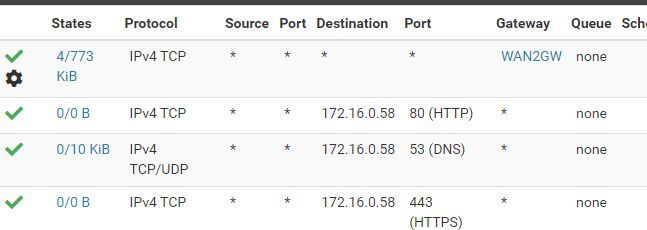
-
@vincentvije
Remove this one:
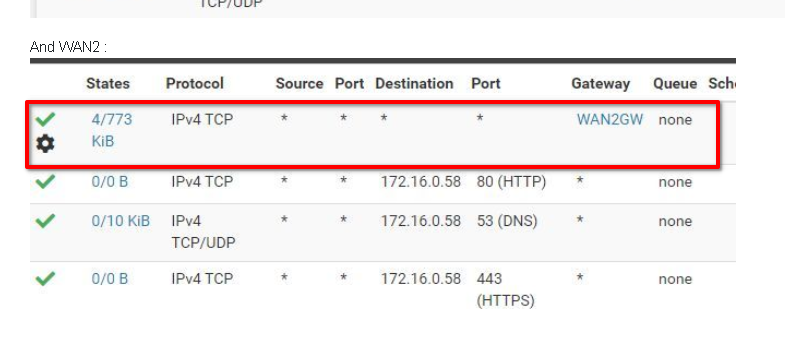
Or at least remove the gateway. This will not work at all.
-
@viragomann But I can't remove the gateway, it's the one we use for LAN computers to go to Internet :
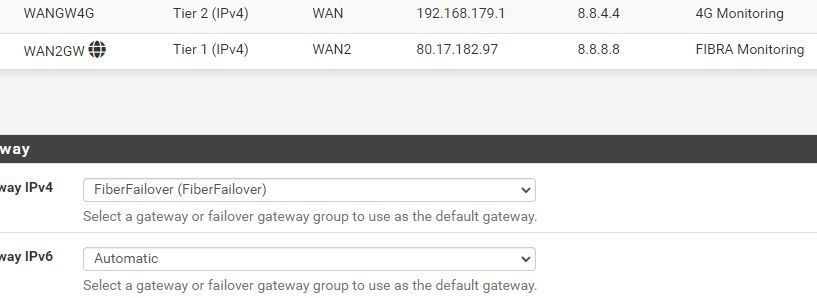
?
-
@vincentvije
I meant, the gateway from the pass rule. -
@viragomann Thanks so much, you did it !
But this rule was added automatically by pfSense, why ?And why do I keep it with WAN and not WAN2 ?
WAN is forwarding well with it, but WAN2 not, I don't understand.For the moment, forwarding work with WAN2, but pinging WAN2 not.
-
@viragomann What I mean is I've the same rule for WAN and for WAN2, why removing from just WAN2, and whay did pfSense added it ?
And the ping problem is not solved ? -
@vincentvije said in Added a second WAN, no way to get forwarfing NAT working on the 2nd:
But this rule was added automatically by pfSense, why ?
 Never had this issue.
Never had this issue.
And I cannot think of any sense, where pfSense is adding a policy routing rule automatically.And why do I keep it with WAN and not WAN2 ?
WAN is forwarding well with it, but WAN2 not, I don't understand.Strange thing: your screenshots above show on WAN port 443 is allowed to .59, but on WAN2 port 443 is allowed to .58.
For the moment, forwarding work with WAN2, but pinging WAN2 not.
Do you have a rule in place to permit it now?
Did you remove the policy routing rule entirely or only the gateway setting. -
@vincentvije said in Added a second WAN, no way to get forwarfing NAT working on the 2nd:
What I mean is I've the same rule for WAN and for WAN2, why removing from just WAN2
A policy routing rule on a WAN interface is useless in almost all cases.
-
@viragomann About 59 and 58, it's because they are different webservers, I miss to send you with same webservers but it's fin.
I don't know where and how adding ping rule ? There's no port. How to do it ?About the routing rule, maybe I should remove this from WAN : ?

-
@vincentvije
This rule allows any access, any protocol, from anywhere to anywhere on this interface.
So this includes also pinging to the interface IP. Hence I'd expect, that pfSense is responding.However, you can also forward pings. In this case it's on the destination device to respond.
For an allow-ping rule, there is no port needed. Just select ICMP protocol, you can limit the rule to "echo request" for instance, and set a source and destination if you want.
-
@viragomann Thanks a lot Viragomann, so I should make the same rule on the other interface WAN2 and it then should answer the pings as WAN do ?
With all your answers, I will take time to understand better how pfSense works.
-
@vincentvije said in Added a second WAN, no way to get forwarfing NAT working on the 2nd:
so I should make the same rule on the other interface WAN2 and it then should answer the pings as WAN do ?
Yes, if you want to allow pings.
Your allow-any rule on WAN2 only allows TCP. This doesn't allow pings, which is ICMP. -
@viragomann Thanks to your explanations, I understood and cleaned all pfSense rules and configs!
Thanks you so much Viragomann !