FW rules for subnet-only traffic?
-
I recently struggled with an issue where a device (a network switch) on subnet 192.168.44.0/24 @ 192.168.44.76 could not communicate with the gateway (pfSense) @ 192.168.44.1.
After much frustration we ended up checking the firewall logs and saw that the "Default deny" rule was blocking this traffic from 192.168.44.76 <=> 192.168.44.1. This does not make sense to me because my understanding of how a firewall works is that FW rules only affect routed traffic (when trying to enter/exit the subnet) and that all traffic within the same subnet always is unaffected by firewall rules because it is essentialy switched (not routed) and so never traverses the firewall. Is this not true?
Adding this rule to allow traffic within the subnet solved my problem
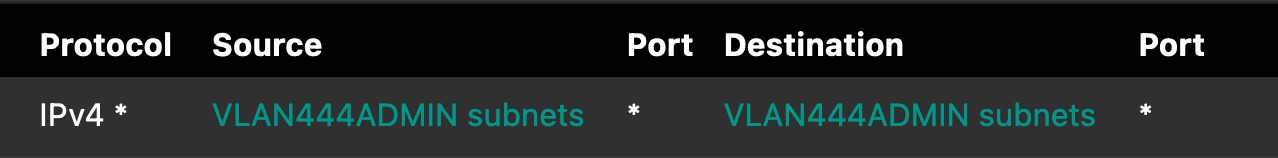
... but I don't understand why I had to add this rule. Is my understanding of when traffic is processed by the firewall incorrect? Or is this some odd edge case that is just a quirk? -
@aaronssh
No, the firewall rules can be considered as doormen on the interfaces, checking which packets are allowed to pass.So if you want to access pfSense itself from any connected device you need a proper rule on the incoming interface. Otherwise it is blocked.
Packets to any other destination than pfSense, however, don't enter an interface and hence do not require a pass rule.
-
@viragomann Thank you for that explanation. I get what you are saying but it conflicts with the following:
Visually I imagine a building where each room is a subnet and each door is an interface. Since all traffic on the same subnet never leaves the room, the door never needs to be opened. (Actually that is how it was explained to me on this forum 10 years ago.)
So I imagine traffic approaching the door (the interface) and not needing to exit the room, so the traffic can continue to flow. So it sounds like this analogy isn't fully accurate to the actual behavior. Just curious, do you have a better analogy that helps one understand this specific quirk a little better?
-
@aaronssh Actually, now that I think about it, if I change "doormen" to "bouncers" and visualize two men (the FW rules) standing in front of the door inside of each room, then it does make sense how they might block both anything exiting the room and anything trying to touch the door, even if the door is never opened. That analogy works for me. Thank you so much for the reply!
-
@aaronssh said in FW rules for subnet-only traffic?:
Visually I imagine a building where each room is a subnet and each door is an interface. Since all traffic on the same subnet never leaves the room, the door never needs to be opened. (Actually that is how it was explained to me on this forum 10 years ago.)
The subnet is not the whole network.There are also devices connected to it. One of them is pfSense.
Consider pfSense as a room. The doors are the interfaces. Behind each, there is another room. This is the subnet. Each door in this room (subnet) is an interface of a device, which is connected to it.
-
Mmm, pfSense doesn't see traffic between hosts inside the same subnet but it does when one of those hosts is itself. It can, and will, filter any traffic it sees.
The same would be true if you have a firewall running on any other host in the subnet. So if you have bunch of Windows machines if one of them thinks it's running in a public network it too will block traffic from other hosts in the same subnet. The Windows firewall normally allows it because it sees the network as private but it can.
-
@aaronssh said in FW rules for subnet-only traffic?:
Adding this rule to allow traffic within the subnet solved my problem
This rule does work but is suboptimal. "More correct" would be to change the second _net to _address.