freeradius3 seemed to use old certificate expiration date
-
I use freeradius3 0.15.10_1 on 2.7.2 CE. I use it for WiFi WPA2-Enterprise with EAP-PEAP. I obtain certificates from Letsencrypt. Everything was working for many months (and years before I moved RADIUS and certificate management from Synology).
This morning I woke up to my devices disconnected from WiFi. pfSense logs had "Login incorrect (eap_peap: (TLS) Alert read:fatal:certificate expired)". First I thought, oh, no, ACME didn't renew the Letsencrypt certificate. But no, the certificate expiration was on 25 Nov 2024 and it was renewed on 27 Aug 2024. I checked everything, I restarted the radiusd service. I even renewed the certificate "just in case" this restarted radiusd again, I checked. I reentered the login info on one of my Android phones, still authentication problem on the phone and "Login incorrect (eap_peap: (TLS) Alert read:fatal:certificate expired)" in the pfSense log.
I started to wonder maybe it's some other certificate that expired. Maybe it was on the client devices. I googled and didn't find anything relevant. By the way the intermediate CA for the certificate was R10 but in the end it didn't matter.
I started trying random things. I changed the SSL Server Certificate in the RADIUS EAP settings to the one for a different domain. I changed the domain name in the WiFi settings on the phone and it connected. I didn't see any difference between those certificates besides the domain names obviously.
So, I changed the certificate in the RADIUS settings back to the original one, made the change on the phone and it connected! So did my other devices that were disconnected. In the end, I didn't make any changes.
I tried to analyze what happened and figured that tonight was the date that the old Letsencrypt certificate was supposed to expire. Their certificates expire after 90 days but they are renewed after 60 days. My certificate was renewed on 27 Aug 2024, roughly 30 days before today. So, today was the expiration date of the preceding certificate that was no longer in the system, and it was replaced a month ago.
Somehow, somewhere RADIUS remembered the expiration date of the old certificate or maybe it even used the old certificate but it wasn't in the System/Certificates/Certificates.
I rebooted pfSense 5 days ago. So, I don't understand how all this could happen. It never happened before. Any ideas? I'd like to prevent this from happening again.
-
I'm not using "WiFi WPA2-Enterprise with EAP-PEAP" at all, but I do use FreeRadius.
It is possible to LE certicates, by would you (make live harder) ?
You only need to answer one question : do you trust yourself ?
If yes, then :
(if no ... sorry, can't help you ^^)These two :
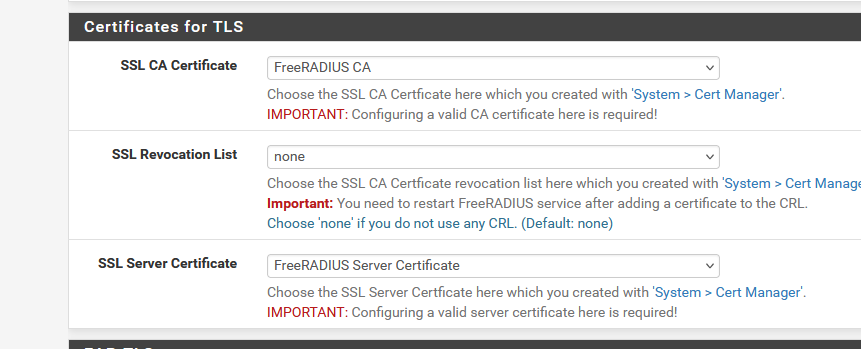
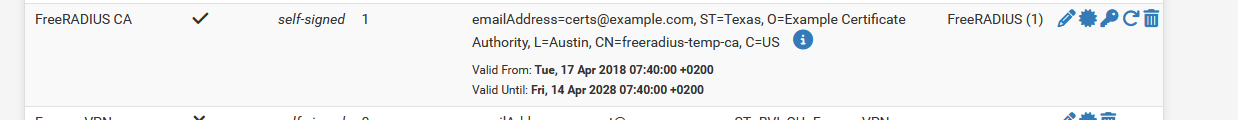
are here : The CA is under CA :
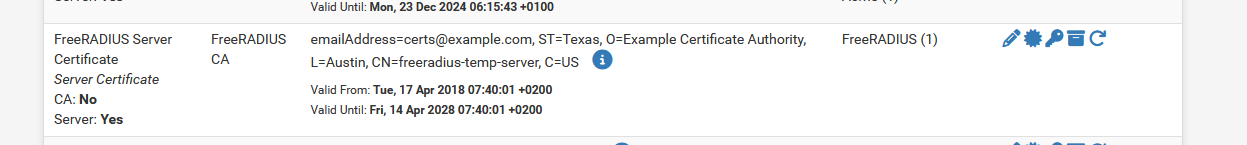
and the "FreeRADIUS Server" is under Certificates :
A Freeradius (actually VPN in my case, the sage is the same) user that use these two (uses a certificate derived from these two) :
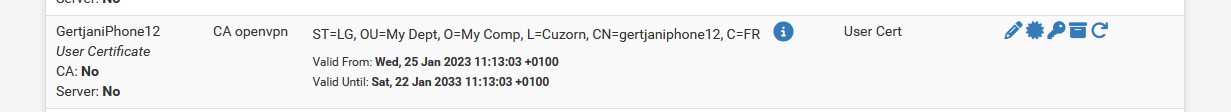
because I made these certs, I opted for "10 years".
90 (60) is pure pain as users need to have these renewed certs every time they renew ...
10 years seems fine for, I'm half way I saw and when the time comes, I'll make a new CA, a new Intermediate, and all new certs for everybody and I'll deploy them. -
@Gertjan said in freeradius3 seemed to use old certificate expiration date:
You only need to answer one question : do you trust yourself ?
Of course I trust myself but do my devices trust me? On Android there is an option to "trust on first use" for certificates and "do not verify". I thought Apple devices didn't have this option but apparently they ask to trust on connection. I still have to see how Windows is going to complain. I think it may not connect automatically but rather ask each time. It's inconvenient. With valid Letsencrypt certificates devices don't ask or complain, just connect.
Thanks for prompting me to try a self-signed certificate. I tamed my phones. I will see how other devices are going to behave. If they trust this certificate and don't ask every time it will be convenient as this certificate will be "valid" for 10 years.
However, what I experienced is a separate issue. I wonder if anyone else encountered this bug. It's just weird.
-
@pfpv I use eap-tls with multiple devices, windows pc, iphone and ipad and and android tablet none of which has asked to trust again after trusting once.
-
@johnpoz, Thanks. Was the certificate added to devices on first connect or you had to manually add it to each device beforehand? The tutorials I read (long time ago) called for adding certificates to devices manually which was no go for me.
-
@pfpv from what I remember the android was the biggest pain.. And someone at the time there was a thread going about on it couldn't get his android to add the ca at all.. But our versions were different.
With ios, I do recall having to do something with the password on the cert or pk12 because it didn't like just blank so used openssl to add a password.. I think you can do it now in the gui.
Windows I had to manually change the mode of the connection to enterprise I believe.
Oh and think there was something about having to set legacy in the openssl cmd to get accepted as well.. But what I can tell you for sure is once their added it doesn't ask you to retrust them on every connection, etc.
Haven't played with it long time, sorry.. But my iphone is using it - and its gone through multiple upgrades to the IOS and still working, etc.