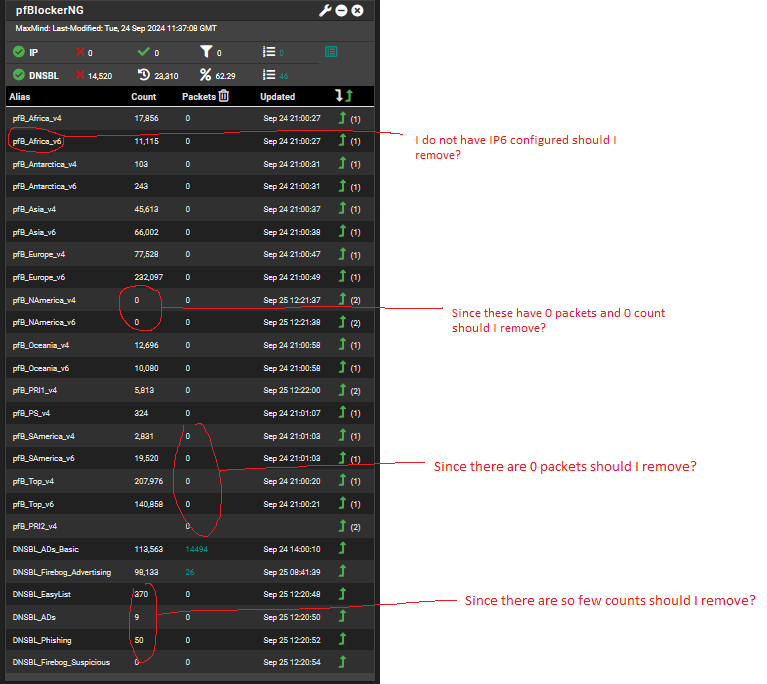
pfBlockerNG Count and Packets Query - Seems like little being captured
-
no need to load the IPV6 versions if you don't use them
The first batch (the pfB_* ones shown) are tied to working rules -- right ? if they are not tied to rules they won't do anything...
then the ones starting with DNSBL are your DNS Blocks
those last 4 are small you might find that no one has attempted to go to whatever is listed in them - you can look at one of the entries in those lists and do a dns lookup (dig) to a name listed. that would "test" at least that one entry on the list.so having a couple of small lists that seem to do nothing could also just be an artifact caused by "you haven't tried to go to anything on the list"
there is no harm in leaving them there for a period of time while you learn what works and what doesn't for you application.that last one actually 0 IPs on the list ? is that what you expect? (if it is a list you think you need then you could check the pfblockerng.log and see if there is an error - generally you won't have an empty list - it has no value)
Now depending on the dashboard widgets setting for clearing those stats, and the time of day you look, you may see zero. - click the wrench icon at the top of the widget and there are two settings
"Enter frequency to clear IP counters" and "Enter frequency to clear the DNSBL/unbound counters" - Weekly is a reasonable choice.. -
@jrey Thanks for the feedback. I went through and deleted all groups, alias' and rules that have any ...v6 assignment after doing so I see the following in the dashboard widget.
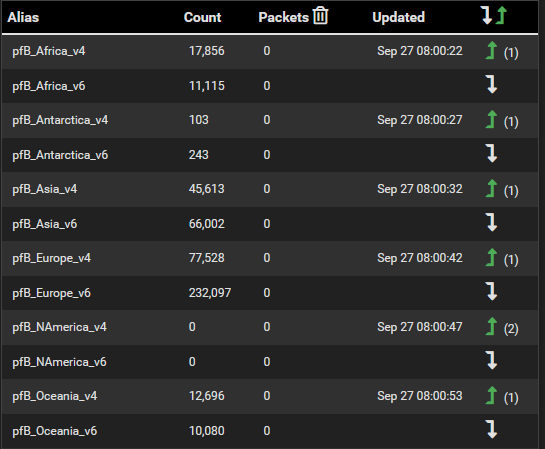
But when I do a reload all of the ...v6 groups, alias' and rules come back and not sure why. I do save my changes where applicable after deleting or making changes and not sure why they reappear after doing the reload.
I should if not mistaken see only the alias' which were not removed and not the v6 ones which are indicated with a white down arrow.
Any ideas why? Thank you.
-
@LPD7 said in pfBlockerNG Count and Packets Query - Seems like little being captured:
Any ideas why?
Sorry, I don't use Maxmind for GeoIP blocking (I use something else)
These screen captures are all from a test system, so I don't generally expect packet counts as there are really no users going through this system, unless I poke.
However, what is defined on this page?
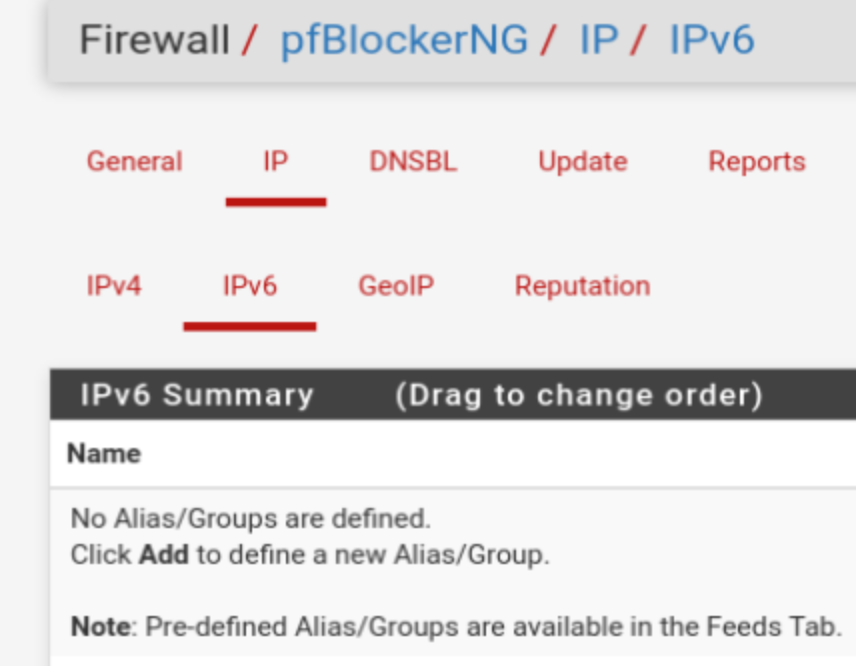
if Maxmind puts them there by "default" you could perhaps disable them or just delete?
because the items you place on the IPv4 and IPv6 directly relate to the lists (alias or rule).
so for example.
like so
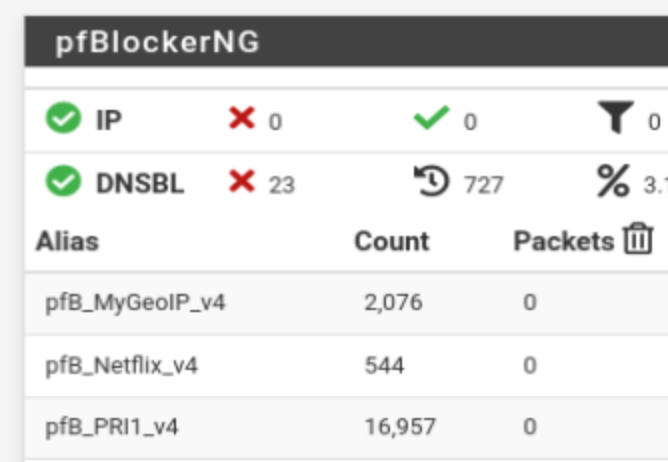
-
@jrey That was helpful, I wasnt aware it was related to maxmind. I went into each geoip category and deselected all ipV6 entries and now things look normal I now also see more aliases logging packets, see below. Thanks for your help.
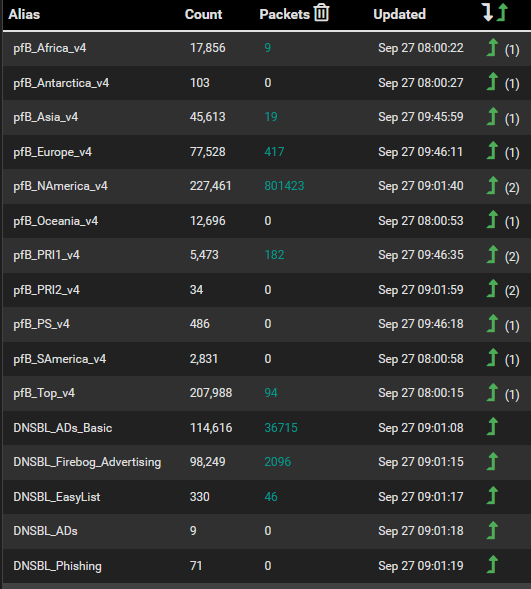
-
@Uglybrian Thanks for your feedback. Do you find the regex.list to be useful? How would I set that up, not something I do often if at all.
-
I am happy with how regex works for me. You will need to try it for your self to see how it preforms for you.
First, you will need pfblocket to be in pythone mode.
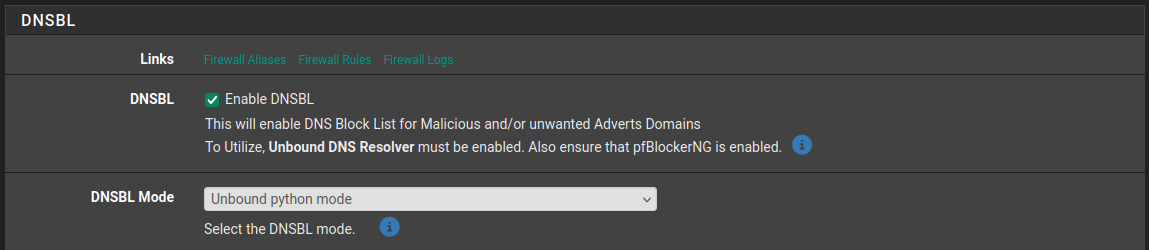
Then on that same page scroll down and you will find Regex Blocking, check to enable. Once enabled, a Python Regex List bar will appear with a + on the far right. Click the + to open, there you will find the field to add the list.
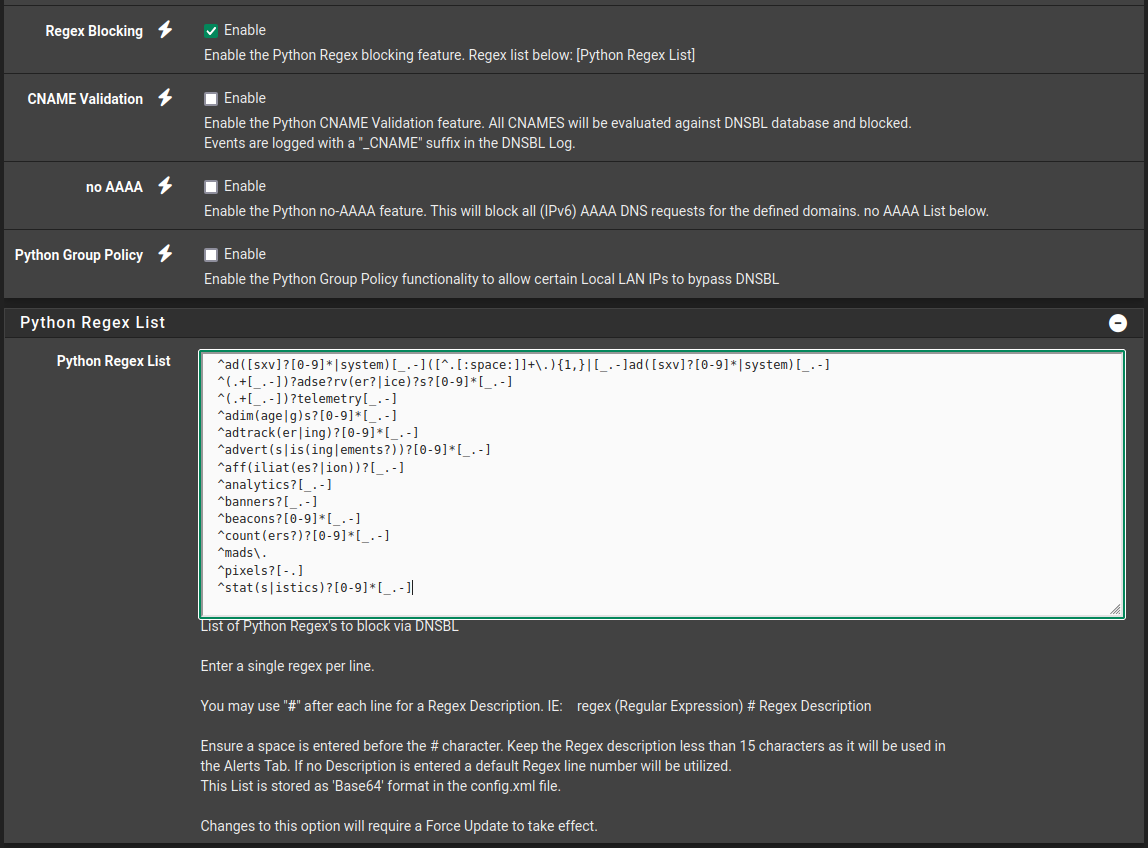
Then save and update your settings. -
@Uglybrian Thanks for that. Would setting unbound python mode break anything I may have setup or is known to not play well with other components? I noticed while looking at this in my system that it says doing so would reduce memory, and had me thinking whether or not doing this would leave me more protected or less simply by way of how reduced resources to me usually means less protection or scanning, etc.
-
I have never heard of python mode breaking anything. I You will be just fine, If not, you could just change it back simple as that.
You need to go back and review what you have read I think you have misread. Python mode requires substantially less memory than unbound mode. The learning curve is steep and it’s easy to get mixed up, even when you are making methodical decisions. -
@LPD7 said in pfBlockerNG Count and Packets Query - Seems like little being captured:
Would setting unbound python mode break anything I may have setup
You would actually have to try it. Hard for anyone to say without knowing what you have setup.
It works well here.
Don't forget out of the box - nothing is getting in (unless you allow it)
choose wisely what users can get out to.some ad block lists have already be mentioned
@Uglybrian saidIn my opinion, it seams you only need the DNSBL_ADs_Basic list.
I have found that my internet usage is best served by two small feeds of Adaway and Dan Pollock/SWC
You may want to try a regex list https://github.com/mmotti/pihole-regex/blob/master/regex.liststart with the one DNSBL - you can always add if something "pops up" - don't get carried away with frequency of updates - daily list updates is usually more than adequate - some lists (like emerging threats etc) you may want to be more frequent - (just understand the list and what needs to be set) take it from there.
Find a balance the works for your use case.
Regex is a good way. Even though I use unbound python mode, I've never found a need for a regex list.. and to follow up @Uglybrian
Unbound Mode:
This mode will utilize Unbound local-zone/local-data entries for DNSBL (requires more memory).
Unbound Python Mode:
This mode is only available for pfSense version 2.4.5 and above.
This mode will utilize the python integration of Unbound for DNSBL.
This mode will allow logging of DNS Replies, and more advanced DNSBL Blocking features.
This mode requires substantially less memoryNothing ventured nothing gained.
-
@Uglybrian @jrey Appreciate the feedback. I have enabled Unbound Python Mode and followed these instructions https://www.vikash.nl/setup-pfblockerng-python-mode-with-pfsense/ as a guide. I did a search for "pfblockerng unbound python mode setup" and only found forums and not app documentation which is why I used the above as a baseline. It is a based on an earlier version of PFB but 99% of it seemed applicable.
Immediately I noticed no difference in the operation of the box, the dashboard was all green, and connections were not impacted. What I did notice is that my memory went up 1% from 15 to 16%. I thought this strange since the main draw to this mode was its lower resource utilization.
I have several feeds enabled, the same as prior to the change. The following are those feeds.
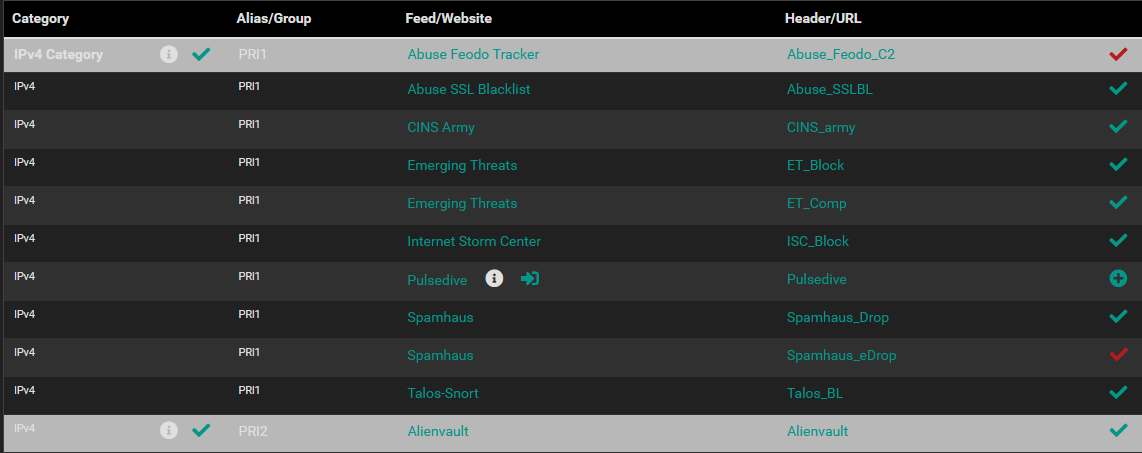





I am not sure why Spamhaus is disabled, I will have to look into it.
I havent setup regex yet, just waiting to see how it runs and what if any suggestions you might have.
Thx
-
I am not sure why Spamhaus is disabled,
Because the list format changed and the list is likely not downloading for you. Should be fixed in pf _17 (but _18 should be just around the corner too, so don't worry about it for a few days)
-
@jrey I have _17 installed so will see what _18 brings, its not an issue right now and actually didnt notice until I looked so that says something.
I did notice after I got rid of the v6 and other feeds mentioned earlier that packet counts for PFB went through the roof. I am thinking I may get rid of the others with a low count and no packets recorded as well.
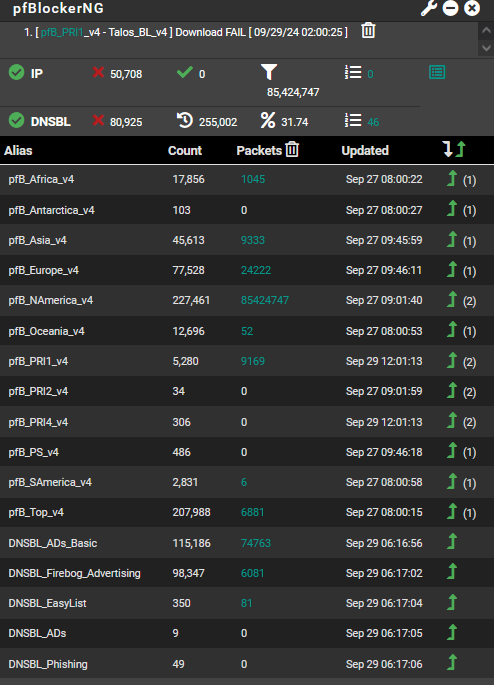
Memory usage went down by 2% (14%) is this the low resource utilization that is mentioned? Want to see what is expected vs what is too much.
I am going to save my config and setup regex and see what happens.
-
@LPD7 said in pfBlockerNG Count and Packets Query - Seems like little being captured:
packet counts for PFB went through the roof.
Did you reset them ?
-
@jrey Yes I either do a reload or cron after changing settings. Is this what you were referring to?
Regex only has a 14 "count" is that right? I am still trying to get used to this, from what I understand the count is the number of targeted ip's and domains and the count is the number of packets that fell into that target range. Based on this understanding I feel like those with low count are probably not worth the resources or reduced performance incurred.
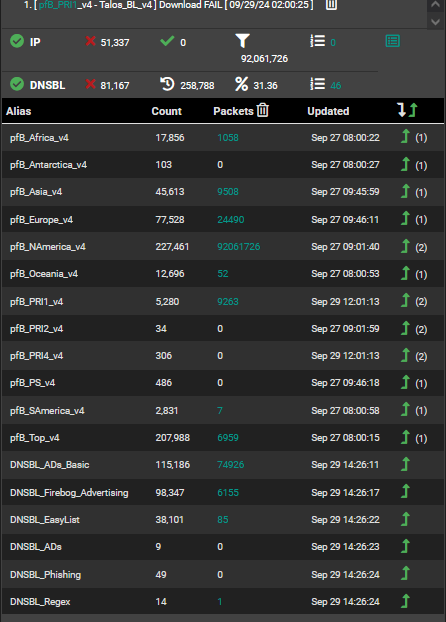
-
14 is correct for regex. - it uses the patterns in the list -- not specific names.
sorry, you had said the packet counts went through the roof -- so the question have you reset them (the counters) relates to that .
if you click the wrench icon at the top right of the pfBlockerNG dashboard widget the "settings" will display at the end of the list. Personally I use weekly and the counters get set to 0 then.
(Never IMHO is a poor choice, because although it can make some impressive (large) numbers, it is harder to visually pick up a trend of what works vs what doesn't.
The options there are Never, Daily and Weekly.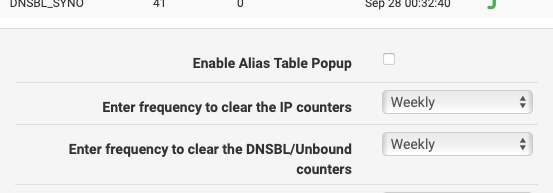
I don't know your use case, but with the traffic here, and who is using, and after just observation over time, I can tell you what the approximate numbers should be for any day of the week. the Never option obscures that at least for me.
-
@jrey Great suggestion, I just set them to weekly. I am going to keep an eye on it for a week and see how it goes and see where I go from there. Thanks for your help.
My wife has me on a crusade. I am trying to see if there is a way to force devices that have cell data but get an IP from PFS DHCP to go through the FW and not the cellular so we can control access. The kids dont always adhere to the rules and I am looking to block their IPs from accessing the internet but still be locally connected/controlled and not able to bypass this by using cellular data. In my mind what I see is once they get an IP from PFS DHCP that setting is primary and overrides any cellular settings. Not sure if that or something similar is possible, I vaguely recall something like this but not certain.
-
@LPD7 said in pfBlockerNG Count and Packets Query - Seems like little being captured:
trying to see if there is a way to force devices that have cell data but get an IP from PFS DHCP to go through the FW and not the cellular so we can control access.
short answer is "yes" there is a way.
When the device is connected locally (wifi) easy part.
When the device is connected by Cell, VPN (settings so the traffic goes through the VPN/Firewall)All our mobile devices switch seamlessly between wifi and VPN (when on Cell) all DNS and access is controlled through the NetGate.
You likely want to ask those questions when they come up, in new posts in the appropriate forum areas.
. -
@jrey Its good to know there is a way. I will tackle that after I take a breather. Have a good your week.
-
@jrey I just noticed cpu usage is up to 20+% which is about double from a day before. When I go into system activity I see the cpu as idle which is confusing as I would think an idle state would see lower cpu%. Am I not looking at this correctly?
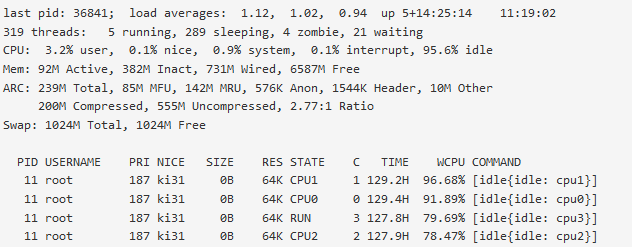
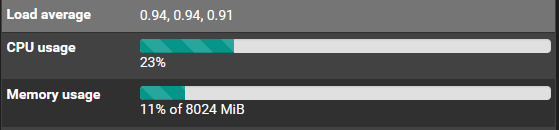
-
That is read as percentage at idle. your first core is at idle 96.68 % And only working .32%