After setting up OpenVPN server, I cannot remotely access computer after the VPN connection.
-
I set up the OpenVPN server, and after configuring everything, I'm able to connect to the VPN server outside the network, and I can successfully ping and connect to the Router and to a Windows Server acting as an Active Director through the Remote Desktop.
However, I cannot ping other computers in the network, nor I cannot connect through RDP using the Remote Desktop app on Windows. I'm trying to connect this one PC. I have it with a static IP configuration, and it's not even pingable. For background information, while inside the network, I can ping and connect via RDP to the computer, but not when using a VPN connection.
I have tried disabling the firewall and turning off IPv6, and I can only then ping the computer, but I cannot connect through RDP.
The thing I cannot understand is that if I can connect and ping the router and the server, why can I not connect to other computers? This is driving me crazy, because if I wasn't able to connect to anything, the problem would be more clear.
I used this tutorial to set up the VPN server https://www.comparitech.com/blog/vpn-privacy/openvpn-server-pfsense/
-
@mhweb
Remember that your VPN client gets an IP out of the OpenVPN tunnel pool, which is a separate network segment.
You computer will block access from outside of there subnet (LAN), however, by their own firewalls. So you will have to go to the firewall settings on the destination computer and allow access from the VPN tunnel.Alternatively you can masquerade the VPN tunnel subnet with the LAN address with an outbound NAT on pfSense. But this is recommended only if the VPN is for your own private purposes, but not for multiple users.
-
@viragomann Thanks for your reply. Yes, I get that the VPN client will get a different IP, but I have used other routers in the past, and it was never an issue.
I see you are suggesting changing the firewall in the destination, but why it doesn't work when I disable the firewall completely on the system? And why I'm able to ping and connect through RDP to the server?Can you point me to a guide on how to do this? masquerade the VPN tunnel subnet with the LAN address with an outbound NAT on pfSense....
Thanks,
-
@mhweb said in After setting up OpenVPN server, I cannot remotely access computer after the VPN connection.:
Yes, I get that the VPN client will get a different IP, but I have used other routers in the past, and it was never an issue.
Consumer routers often do masquerading by default.
Access devices from a VPN client without specific routing also presumes that the VPN endpoint (pfSense) is the default gateway on the destination device. But I think, this is given.
but why it doesn't work when I disable the firewall completely on the system?
If it's a Windows computer I wouldn't give my ass that disabling the firewall means really disabled.
You can do a simple test: On pfSense go to Diagnostic > Ping. Enter the computers IP and ping it with default settings. I expect, that this will succeed.
Then change to source to the OpenVPN server and try again. Does it still work?
If not the devices firewall is probably blocking it, because the source IP is from outside of its subnet.Can you point me to a guide on how to do this? masquerade the VPN tunnel subnet with the LAN address with an outbound NAT on pfSense....
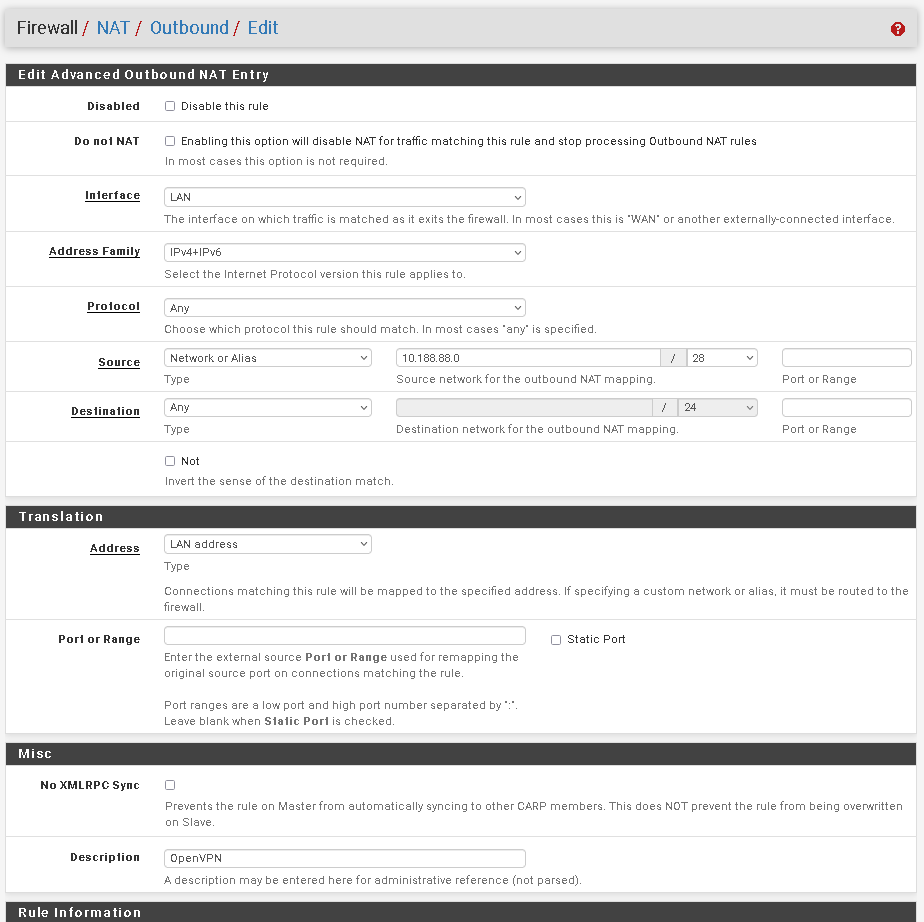
Masquerading means, that the router translates the source IP into its respective interface IP (S-NAT).
To enable this, go to Firewall > NAT > Outbound. Select the hybrid mode and save it.
Add a new rule:
interface: LAN
source: OpenVPN tunnel network
dest.: any
translation Address: LAN address
Enter a proper description and save it. -
@mhweb said in After setting up OpenVPN server, I cannot remotely access computer after the VPN connection.:
Can you point me to a guide on how to do this? masquerade the VPN tunnel subnet with the LAN address with an outbound NAT on pfSense....
Thanks,
as @viragomann stated, the target must allow the traffic. if the target firewall is disabled, then the next question is are you sending the traffic to the target? if it is enabled, are you allowing traffic from the openvpn network subnet?
If this were me having this issue, I would start with something like this:
- verify that no local ip on the testing machine is on the same subnet as the target internal lan subnet. so that traffic is seen as remote and routes through the openvpn tunnel.
- You didn't say if you were connecting by IP or name. if using name then validate DNS resolution is working as expected or switch to using IP address for now. Then fix DNS once things are working as desired.
- capture on the LAN network interface icmp traffic with a destination of the target host IP. then ping the target from the openvpn client while not connected to the internal network and see that the traffic is leaving the LAN interface on the firewall.
- if it is not, you have a firewall issue. look for issues with firewall routing and rules.
- if it is you have something on the target computer blocking traffic. look for issues on the target machine.
I suspect as @viragomann suggests, you will see the ping leave the firewall lan interface to the target, but you will not see a response from the target.
For testing you should not be connected to the internal network and connected to the VPN client at the same time, nor should the test client have a local IP that resides on the internal LAN subnet configured.
I don't use NAT unless necessary, as it hides the true source of the traffic. I would try to make it work without NAT first.
-
@mikek
You advised a port forwarding rule (D-NAT). However, for masquerading he need an outbound NAT rule (S-NAT).
-
@mikek DOH! thanks! I thought of that right after I posted but haven't edited yet. how is that ;)
Still doing a lot of learning myself. trying to get involved and posting forces me to thing through these scenarios.