ACME with a private CA (step-ca)
-
Hi,
I'm working on providing certificates via ACME inside my internal network. That already works for most services via acme.sh.
But the ACME package for pfSense requires me to create an account at one of the listed CAs.
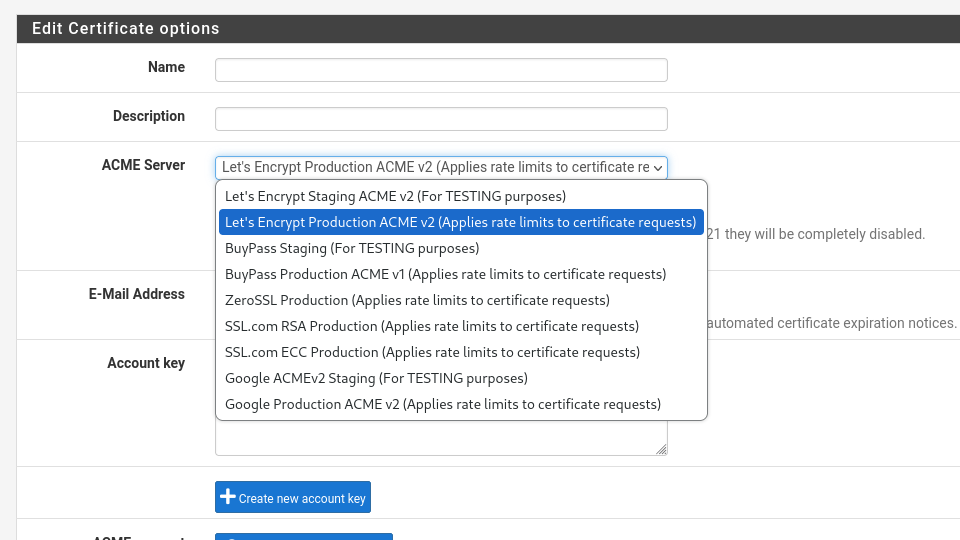
I looked into the documentation but couldn't find the setting to use an intern domain or ip for the ACME Server.
I couldn't find a thread in this forum for it, so I create this one.How can I use a private CA for ACME?
kind regards
seism0saurus[Edit: fixed typo]
-
@seism0saurus said in ACME with a private CA (step-ca):
ut couldn't find the setting to use an intern domain or ip
Check with Letsencrypt here. Or any of the others as, afaik, the same conditions apply.
So, no need to create an account @ Letsencrypt.
But : an certificate mus contain a host name, not an IP. If you want a certificate with an IP as a 'SAN' then you've no choice : you have to chose another certificate broker. These are the ones you have to pay.
Ok that you use an so called "intern domain" which must be real domain name, a domain name that is 'accessible' from the Internet. These are normally not free. You can pick whatever registrar you want, and do not forget to check if this registrar permits you to use a acme.sh dns method, the most famous one being called "DNS-NSupdate / RFC 2136".
@seism0saurus said in ACME with a private CA (step-ca):
How can I use a private CA for ACME?
If you created your own CA, a so called auto signed certificate, you can then create your own certificates based on that CA. You don't need acme.sh, or Letsencrypt or anybody else.
Copy the cCA cert into your browser's trusted certificate store, and from now on your own certificates will be trusted by your browser. because you trust the stuff you make yourself ^^
-
Thank you for your reply.
I should clarify my request a little bit more.
- acme.sh is only one of the many ACME clients. It's not a CA. I mentioned it to show, that my internal CA has a working ACME endpoint
- The pfsense has a real domain but is not a publicly reachable domain. Only an internal one like pfsense.home.arpa. .home.arpa is reserved for internal usage
- The pfsense is reachable from the internal CA so it could solve http, tls or dns challenges
I could manually sign a long living certificate for the pfsense, but it's easier and more secure to have short lived certificates with automatic renewal.
But the ACME client implementation does only support some of the big public CAs seen in the screenshot for the account selection.Maybe it's better to create an intermediate CA in the pfsense and sign it with my own root CA. Then pfsense can issue it's own certificates for the UI.
-
@seism0saurus said in ACME with a private CA (step-ca):
more secure to have short lived certificates with automatic renewal.
How so? Who would be sniffing or trying to hijack your sessions locally? How does changing the cert every X days mitigate that risk anyway?
I mean are you really concerned about someone on your local network listening in on your session with your printer gui?
Not seeing any sort of real risk case here.. Create a CA, sign a cert for 10 years and be done with it.. Have your browser trust this CA..
Do you think acme only does 90 days because they are worried about "security" of the cert in some way - or that if the domain you say you own and provide a cert gets compromised that cert isn't good for 2 years is all..
Its not because hey in 91 days that cert can be hacked and traffic viewed, etc.
Such a concern doesn't come into play when your on your local pc talking to your printer gui for example on your network.
-
Certificate Revocation Lists are basically broken.
So the most feasible workaround is to use certificates with a short lifetime. The potential impact of a compromised certificate is smaller, if the time an attacker has is shorter.It really depends on the network and what services you offer. A printer may be a very valid target for attacks in a network with sensible data printed. But to decide that is part of Thread Modelling.
-
@seism0saurus said in ACME with a private CA (step-ca):
Certificate Revocation Lists are basically broken.
That issue is linked to main foundation reason of Letsencrypt : "Certificates for everybody".
Maybe not 'broken' but a complete hassle to work with.
"Because we haven't done the manipulation very often"
It's like changing your Netflix password several times a day 'so your account doesn't get hacked, while you use your account on several devices.@seism0saurus said in ACME with a private CA (step-ca):
A printer may be a very valid target for attacks in a network with sensible data printed.
That's the chick-and-egg problem (special edition) :
You would steal the golden eggs that the chicken 'printed' ?
I would steal or clone the chicken. -
@seism0saurus said in ACME with a private CA (step-ca):
Certificate Revocation Lists are basically broken.
Which has really ZERO to do with the cert you have on your local printer or switch, or some software your running gui like the unifi controller or your nas..
What is the scenario where I would need to revoke this cert? It is accessed by me, on my local network. To be honest I could just use http for this but the browser complains.