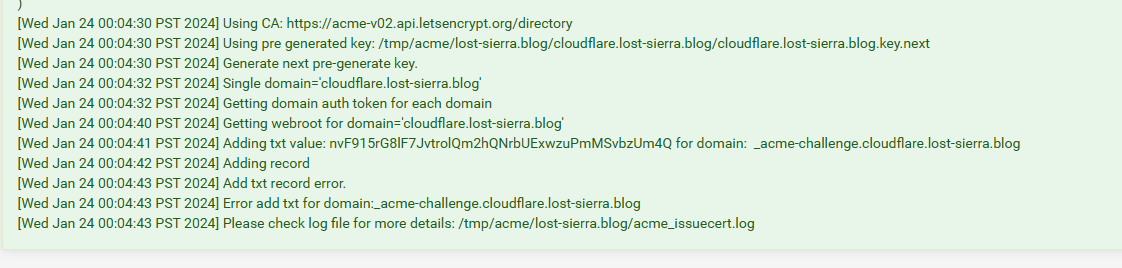
@decidable3195 Ich würde dir ja wirklich gerne helfen, aber ohne zu verstehen, was ihr da wo tut, kann ich es schlicht nicht. Du sprichst von ACME und dann von DNS, jetzt hast du irgendwo irgendwas umgestellt aber postest nicht was. Woher soll man denn wissen, was du jetzt wie verstellt hast? Dass die Seite nicht mehr geht wundert nicht, da viele entsprechend intern mit Umleitungen auf HTTPS etc. arbeiten, dann funktioniert der Login nicht mehr.
Da ihr aber anscheinend keinen Proxy einsetzt kann es auch nicht wirklich was auf der Sense gewesen sein, was das Problem jetzt verursacht?
Also wäre es schön wenn wir mal einen Schritt zurück gehen und wir mal komplett aufdröseln um hier überhaupt Sinn reinzubekommen:
Um welche Dienste geht es hier konkret?
Wo laufen diese und mit welcher internen IP?
Wie greift man von wo darauf zu?
Welche internen Netze (wenn mehrere) sind involviert?
Was hat die Sense damit zu tun? Bei welchem Zugriff ist die überhaupt involviert?
Am Einfachsten wäre natürlich ein kleiner Plan oder Skizze aber wenn dus mal etwas weitergehend niederschreiben würdest, wäre das auch schon eine große Hilfe. So verstehe ich wie gesagt überhaupt nicht was wo wie läuft und warum die Sense da involviert sein soll.
Cheers
\jens
 6
0 Votes19 Posts3k Views
6
0 Votes19 Posts3k Views