Delegate IPv6 subnet to only specific MAC addresses
-
So if we let IPv6 auto assign to tenant routers, at what point could the subnet assigned to a tenant router change? Obviously if they replace it, but outside of that...?
I'm thinking this might work:
- set building router to hand out IPv6 blocks
- create firewall rule on LAN to only allow IPv6 from known MAC addresses (one rule per MAC)
- create a firewall rule on LAN to assign each subnet to the correct limiter
It's a bunch of extra steps though.
In pfSense how do I find out the subnet a given tenant router is using? Can I connect the Status/DHCPv6 Leases, Delegated Prefixes info to the known MAC?
Option 2 is we set it up for us and wait until someone asks for IPv6. :)
-
Just to follow up, I set it up for us, with static IPv6. It took me longer than I'd care to admit to add firewall rules to allow IPv6 ICMP since we'd never set up IPv6 rules on the building router.

-
@SteveITS Never done it with pfSense but with my first router (fritzbox) towards my pfSense. It says something like this: Allow Ping6, open firewall for the delegated prefix, make this host the exposed host.
-
@Bob-Dig I realized my comment might be unclear so I came back to edit it but you beat me… IPv6 was allowed on the inner router due to the HE tunnel but it had never been allowed outbound on the building/outer router LAN interface since that wasn’t necessary (due to the tunneling).
#ComputersDoExactlyWhatYouTellThemNotWhatYouWant
-
I'm back again. After our Comcast router restarted last night we lost IPv6 to the inner subnet. I am pretty sure it lost the route back. However the Comcast router only allows me to configure an IPv4 static route. Thinking back, possibly it had set up the route while I was experimenting with the various delegation/DHCP settings, and lost it upon restart. Boo.
So I started all over, and set it up using Track Interface and prefix delegation, with the building router DHCPv6 Server set with "Deny Unknown Clients" to allow only known clients. I had to allow any temporarily just to find the DUID of our router.
By the time I got back to set it to allow only known clients again, the building router had allocated another IP and prefix. However, it added a route to this other prefix and would not add a route for our office router prefix. So eventually I gave up and added a static route in our building router, pointing the subnet that had been delegated to our office router, to our office router.
So overall it looks like it should have worked with "deny unknown clients" except there was no route created from the outer pfSense to the inner pfSense, like there was for other routers in the building. ٩(͡๏̯͡๏)۶
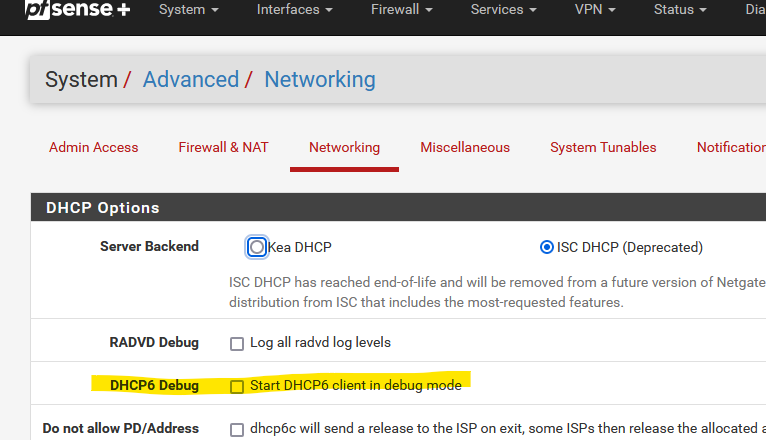
Side note: the "Start DHCP6 client in debug mode" option seen referenced on this forum several places does not seem to exist on either of these routers' WAN interface settings? I thought I'd enabled that before, was that removed? Is there a trick to displaying that?
-
@SteveITS said in Delegate IPv6 subnet to only specific MAC addresses:
Side note: the "Start DHCP6 client in debug mode"
Hidden here :
-
@Gertjan D'oh! I knew I had seen it, thanks.
Unfortunately this was broken twice this morning.
- my static route was no longer in the routing table
- DHCPv6 started handing out IPs again despite being set to allow only known clients.
In limited testing it looks like the problems were:
- DHCPv6 Server does not add a route for delegated prefixes to reserved IPs
- if I restart DHCPv6 Server, my static route is removed from the routing table
- I had to edit and save the route, to get it to work again
I kept banging on it. I set Router Advertisement to Managed so clients couldn't get an IP. However RA is still advertising prefixes to other routers, they are just failing.
At some point I re-saved the office router WAN interface and now that Delegated Prefix shows on the DHCPv6 Leases page. So maybe it was in some weird limbo state from above? I didn't try deleting the static route yet since we're into the workday.
However DHCPv6 Leases still shows leases and prefixes for other routers. Does it just not honor the "Deny Unknown Clients" setting?
Confused about the path forward, do I need to turn off DHCPv6 Server on the building router, and use a static route?
-
...and the route is gone again, don't know why.
Edit: Seems like all the DHCPv6 Server settings are ignored?
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv6.html"The DHCPv6 daemon can only run and be configured on interfaces with a Static IP address, so if a tab for an interface is not present, check that it is enabled and set with a Static IP. It is not currently possible to adjust settings for tracked interface DHCP service."
I suppose one could read that as "shouldn't be visible" vs "we'll ignore everything". It does seem to be using the configured address pool though.
-
@SteveITS If you have static IPv6, use it. If it is dynamic then don't. Latter one is not running that well in pfSense. For instance, I get a new prefix every night. I have to reboot my pfsense via cron afterwards to get it working well. But with static IPv6, I don't see that (only have HE).
-
@Bob-Dig I can't really tell without going to the office and testing by booting the Comcast router, which kicks everyone off, but I think Comcast doesn't keep the routes after their router boots. They have a "static IPv6" /56 as they label it but it's handed out to their router automatically by them, and if I configure our pfSenses with all static then there isn't a way for me to configure a static route for the "self-delegated" IPV6, on the Comcast device. It only allows IPv4 routes.
Currently it's working with:
building WAN: DHCP6
building LAN: Track Interface
office WAN: static IPv6
office LAN: static IPv6
building router: needs static route for office LAN
building router: DHCPv6 Server off
building router: RA offI suspect when I was banging on it a month ago the Comcast router kept the route for the delegated prefix, until it booted. So having the building router Track Interface and request a /62 prefix hopefully will keep that route in the Comcast router. Guess I'll find out in the next few months if/when it restarts. And then the fix and that point is probably just to reacquire the building LAN IPv6.
Done automatically I expect it will all work just fine, the problem is we need control over how to hand out addresses.
There's also some sort of a bug I ran into again where if I add an IPv6 gateway on the WAN interface page, it flips the IPv4 gateway to Automatic and disconnects Internet (even though there's only one IPv4 gateway). But that's another story...
-
S SteveITS referenced this topic on
-
@SteveITS said in Delegate IPv6 subnet to only specific MAC addresses:
Currently it's working with:
building WAN: DHCP6
building LAN: Track Interface
office WAN: static IPv6
office LAN: static IPv6
building router: needs static route for office LAN
building router: DHCPv6 Server off
building router: RA offFollowing up, when the Comcast router boots (3am so an ISP update I assume) our building pfSense router loses its static route. I tried restarting it this morning to try to recover, and, fun times, it decided to revert to a 23.09 boot environment, removing a bunch of settings. Super confusing but easily fixed once I figured it out. However after that it still didn't have the route. Re-saving the static route as-is didn't create it either.
Is there something in the code perhaps that doesn't/can't set up the route if the IP subnets are incorrect/inaccessible? Is there a good way to recover from that?
Per this post it sounds like maybe Kea is required for "deny unknown clients" to work correctly for IPv6, so that could be something I try down the road when it's stable/finished.
-
@SteveITS Fun times indeed. I am seeing problems with PPPoE together with RAM-Disk. And then BE can come into the mix too. I deleted every BE other than current.
I never did what you did, so only thoughts but is your Prefix really static or is it not? If it is static, why do you need to use Track Interface? If it is not static, then forget all of this is my advice, it is such a hassle. pfSense and/or FreeBSD is really bad when it comes to dynamic Prefixes. When the change only occurs early in the morning, you could make a cron to reboot pfSense. And, I kid you not, rebooting every switch with a Smart-Plug afterwards. But then, who would do something like that in a commercial environment.
Another thought, if you made static routes, have you ever considered to use fe80::-addresses for the routes? Never did it myself though. ULA also could work I guess.
-
@Bob-Dig said in Delegate IPv6 subnet to only specific MAC addresses:
I never did what you did, so only thoughts but is your Prefix really static or is it not? If it is static, why do you need to use Track Interface?
I've had my prefix for almost 6 years. However, it's still DHCPv6 so the possibility of it changing remains.
-
@Bob-Dig said in Delegate IPv6 subnet to only specific MAC addresses:
is your Prefix really static or is it not
Comcast labels the /56 "static" in a business account portal but how it is delivered to the router I don't know. The last router swap was all auto-configured, the guy just stood there for a few minutes waiting for it to pull its settings.
The problem is 1) what subnet block gets delegated to the inner router, and inner router's LAN, changes when redelegating happens (if the route inward is lost and I start over trying to fix it), and 2) if I set them up as static in the pfSenses, AFAICT the Comcast router doesn't know where to route the innermost subnet...and its GUI only allows IPv4 static routes, and 3) if delegated automatically sometimes the building pfSense still doesn't create a static route.
So ideally I could set it up automatically and only have our one "inner" router get IPv6, and my hope would be routing is auto-configured, but I don't seem to be able to do that without other "inner" routers getting IPv6.
And if I didn't say above, the reason we need to do that is to allow access only to paying tenants, and to set bandwidth limits accordingly.
One possibility (?) is that the building router reacquires IPv6 when the Comcast router boots, but the inner/office router doesn't request delegation because it was already configured and doesn't know it needs to?
I spent quite a bit of time yesterday trying to figure out how to find the DUID that will be used on pfSense. "od -h /var/db/dhcp6c_duid" will show it, with the bytes reversed ("8550" = "50:85").
System > Advanced > Networking has a "DHCP6 DUID" dropdown but on this router if I choose Raw and enter in a DUID, and save the page, it changes my choice to DUID-LLT. I can use DUID-LL and enter a MAC but the output of "od" above includes extra output when I do that, which was confusing. (eventually had to enable DHCP6 debug mode on that page, and restart, to see it in the logs)
And then after all that I still found another router had acquired an IPv6 IP+delegation so had to turn that off again.
All I need is for the static route on the building pfSense to not disappear and I think it should work.
</mini-rant>