Max SANs ?
-
I was trying to create a Server cert including an IP, FQDN & hostname for each of its 6 interfaces. So that's one Common Name and then 17 SANs, all told. The IP SANs are of type "IP Address". I created entries for the host/domain name in the DNS Resolver and checked that they can be resolved using DNS Lookup and pinged.
However, Pf doesn't seem to like this, throwing the error
DNS subjectAltName values must be valid hostnames, FQDNs or wildcard domainsI've made some changes to protect myself online, but below are examples of the FQDNS, hostnames and IPs that I'm trying to include in the cert:
mdf-lan-fir-p-1.thesimpsons.ourhome
mdf-lan-fir-p-1
20.10.0.1
mdf-sin-fir-p-1.thesimpsons.ourhome
mdf-sin-fir-p-1
20.10.10.1
mdf-sot-fir-p-1.thesimpsons.ourhome
mdf-siotfir-p-1
20.10.20.1
mdf-usr-fir-p-1.thesimpsons.ourhome
mdf-usr-fir-p-1
20.10.30.1
mdf-iot-fir-p-1.thesimpsons.ourhome
mdf-iot-fir-p-1
20.10.40.1
mdf-gst-fir-p-1.thesimpsons.ourhome
mdf-gst-fir-p-1
192.168.100.1I looked online, and the max number of SANs is 100, give or take. Netgate's docs, don't specify.
Suggestions here?
-
You are just adding them in the cert manager?
Does it accept them if you use fewer SANs?
What pfSense version are you running?
Steve
-
I'm running 2.7.2-RELEASE (amd64).
And yes, I'm using the cert manager.
I played around with this some more. The largest number of SANs that I can get it to take so far is 6.
Once I go over 6, it goes into a confused state and won't allow me to create the cert until I go down to 3 SANs.
-
Hmm, interesting. Is that with any type of SAN? Only combinations?
Let me try to replicate....
-
I can't replicate that, I can create a cert with any number of SANs. I stopped at 18:
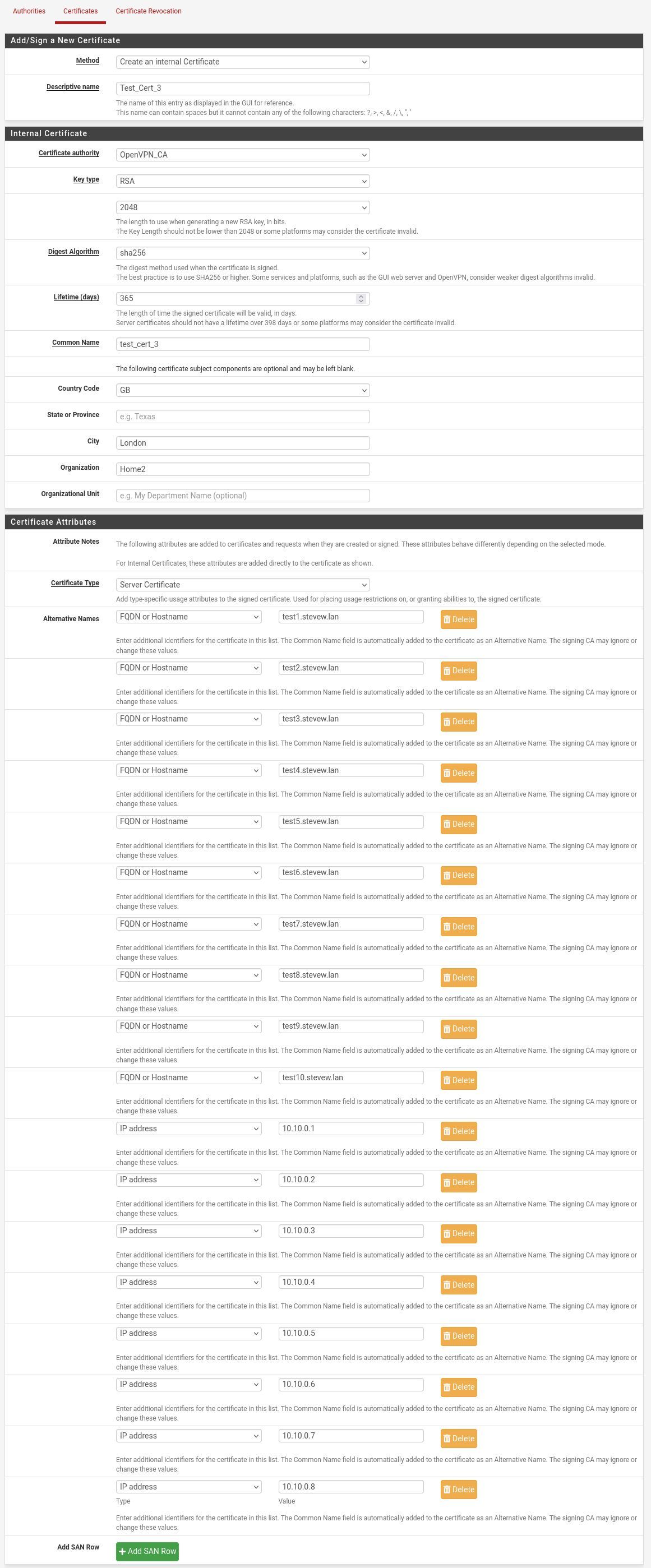
Do you have the recommended patches applied from the System Patches package? I'm not aware of anything that would apply to this though.
Is your example list above something you are actually hitting this with?
-
@the-loquitur said in Max SANs ?:
values must be valid hostnames
mdf-lan-fir-p-1
wouldn't be a valid fqdn
-
But it's a valid hostname.
-
I was able to save this no problem:
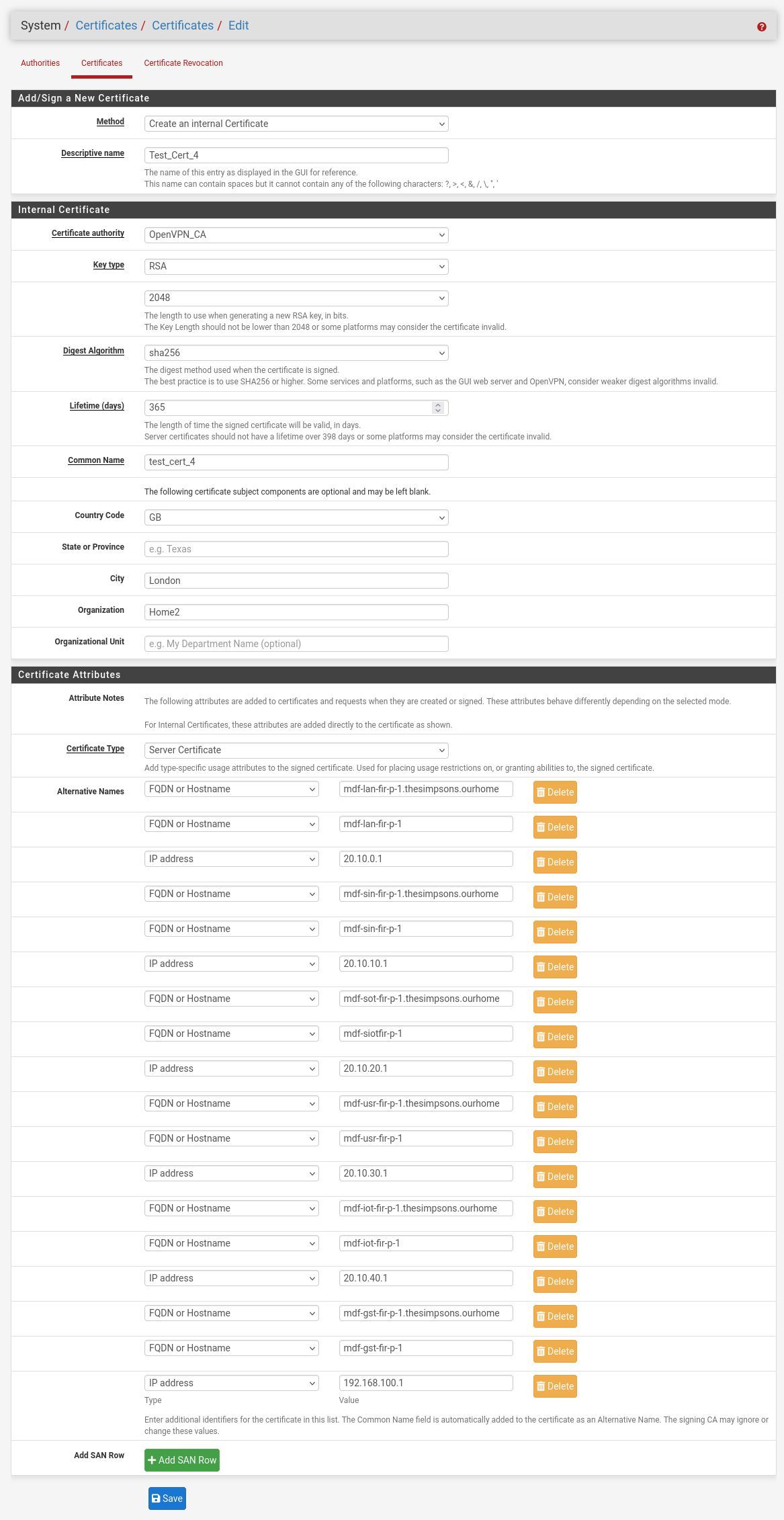
-
Hi. I believe that I've found the use-case where it fails.
When I create a test CA where I don't bother to fill out the:
Country Code
State
City
Organization
Organization Unitand only fill in the Descriptive Name and Common Name. Then it pukes.
I ended up creating 2 CAs: one with the RDNs and the other without. When I try to create a cert using the no-RDN CA, it fails. When I try to create a cert using the CA with RDNs, it works.
Initially, I was working with FreeRadius for the first time and created a CA for just to use for proof of concept, filling out the very least fields. Then I ran into this.
For me, this is deterministic.
BTW, the GUI form for creating a CA actually says that the RDN fields are optional.
-
Are you entering those values on the server cert if they are not auto filled by the CA?
-
O. I don’t fill them out when creating the CA and then correspondingly, I don’t fill them out when creating a cert using the CA.
At this point, I’m all done with reporting this.
Thanks
-
Hmm, still unable to replicate it here without any optional fields on the CA or cert:
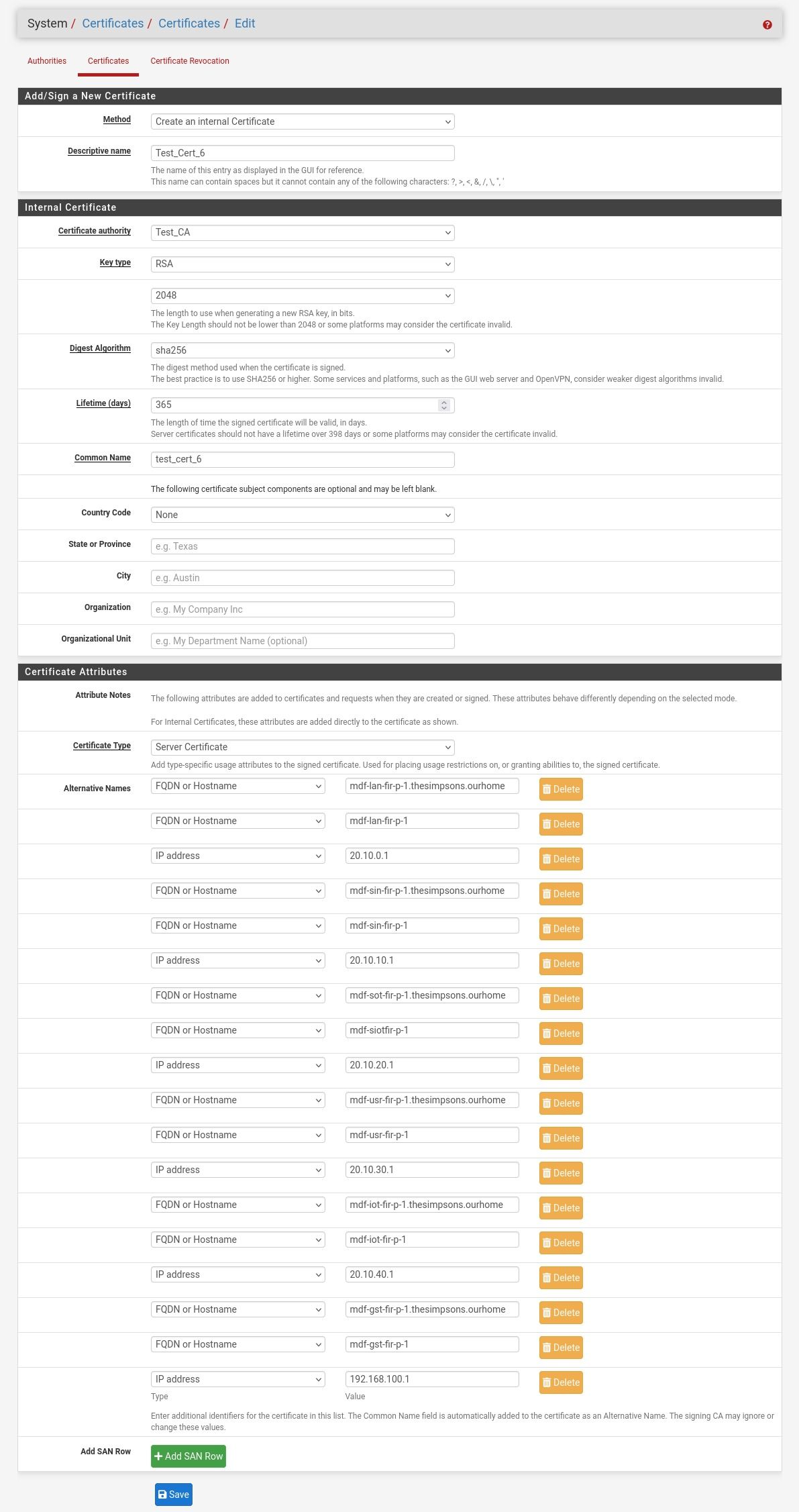
Do you have all the recommended patches applied?