ATT Internet AIr
-
So after some more work and time for dust to settle after re configuring everthing .. I have gotten 72hr of stable connection from both ATT modems - the one connected directly to the igb2 interface and the one connected to igb3VLAN20
However I was never able to reliably get the dhclient to work and to be able to use DHCP for the connecctions
I got this form my ATT rep yesterday who was able to talk to ATT backend people - the following was thier response :
Below is the response from the ticket I put in:“If a cellular device is in IP Passthrough mode; (NightHawks, AIA-B, etc) they only pass the static IP that is provisioned with a Shared APN, to the backend appliance that is attached, via the RJ45 connection.”
Does that make sense that they [ATT] would do this?
-
Not really sure why they would do that. It could simplify the configuration at their end. That doesn't really explain why it works for a while though.
-
@stephenw10 I agree -- it was even more weird in that when I first connected directly to the interface it configured fine with using DHCP and seemed to remain connected for at lest a couple days. After the VLAN testing started that's when things got really difficult ....
On another note - during my debacle with my pfsense box this past weekend (I have a Protectli FW4B) , I ordered a replacement (assuming possible hardware issue). Apparently it was just a software issue and my original device is functioning as it should. Initially I thought about keeping the new device and keeping a spare around since I have 2 business locations dependant on them. The question is - do you thinnk there is much differnce in the Fw4C that I just recieved and any reason to swap out the FW4B for the FW4C?
-
The only significant difference I see are the NICs. The 2.5G NICs on the 4C are faster but auto-negotiate only. If you ever want to use fixed speed igb NICs will do that.
-
@stephenw10
Hey sir thanks again for all your helpI have another issue realted to my lost pfsense setup this past weekend ....
I have reconfigured haproxy and I think I have things working , mostly
My continued problem (and I wanna be sure I solve in the most direct fashion) is as follows:
if I go to https://mysyno.mydomain.com externally - then things get point to my NAS and more imprtantly to the proper port for the managment program
if I go to https://mysyno.mydomain.com internal (on my LAN) , not only do a get a warning about the website not being secure , when I push past the warning it basically takes me to https://mysyno.mydomain.com:443 (the wrong port)internally if I put https://mysyno.mydomain.com:correctport then it goes corerectly to the management program
bottom line is that internal requests seem to be bypassing haproxy
I had this working correctly in my setup that I "lost" (by stupidly not having a backup) -- what is the most direct way to fix this??
I noticed that in DNS Host Overides section there is no option for entering a port -
mysyno.mydomain.com resolves to the pfSense WAN IP address?
What cert error is shown? What cert is shown?
Is it the pfSense webgui cert? That would imply you're hitting a port forward which you shouldn't need with HAProxy. -
@stephenw10
I have no ports forwarded
Attached is an example of the cert error when going internally to https://mb.mydomain.com
-
and https://mysyno.mydomain.com resolves to the internal IP 192.168.144 but to port 443
and haproxy is supposed to send it to 192.168.1.144:5001 -
@stephenw10 and I mean internall
It works correctly externally
-
So I activated NAT Reflection > Pure NAT
I now can access several of my services internally and externally — all of which are https through harrows
The only remaining issue, even after enabling the NAT reflection, is the firewall interface which is reachable external via https://pf.mydomain.com
But internally only available by adding the port :8000So NAT reflection fixed everything except firewall management page!




-
@ahole4sure said in ATT Internet AIr:
So I activated NAT Reflection > Pure NAT
I now can access several of my services internally and externally
Then it's not using HAProxy since that would redirect traffic past HAProxy entirely. NAT reflection only works with port forwards and you shouldn't have any of those if you're using HAProxy. It sounbds like you must have them though.
You have the pfSense webgui set to use port 8000 directly?
Do you still have the port redirect enabled in Sys > Adv > Admin Access: WebGUI redirect ?
That should redirect http requests to https on port 8000. -
@stephenw10 I have NO port forwards
see picI have been trying to get something else to work. I saw a post where someone did an haproxy frontend on to listen on the LAN and then forward to the correct port
see pic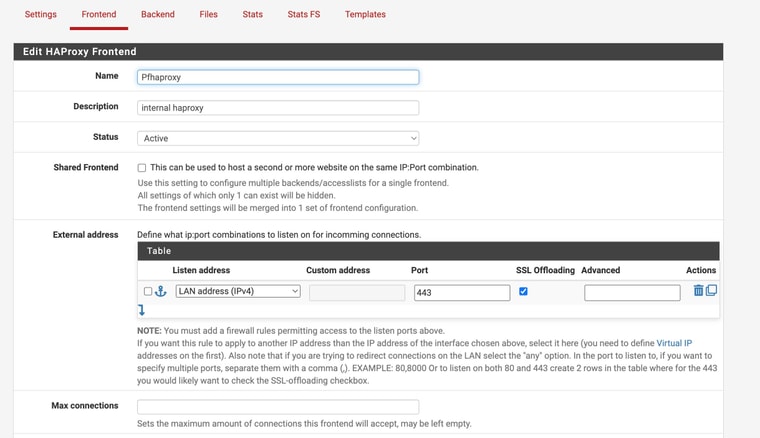
I was thinking it was working last noght but then when I got up this AM it didn't seem to be working , BUT after i reached the firewall by 192.168.1.1:8000 the forst time , it then began working
Also wondering if I should have my wildcard domain cert here or should I leave as the default webui config?
ssee pics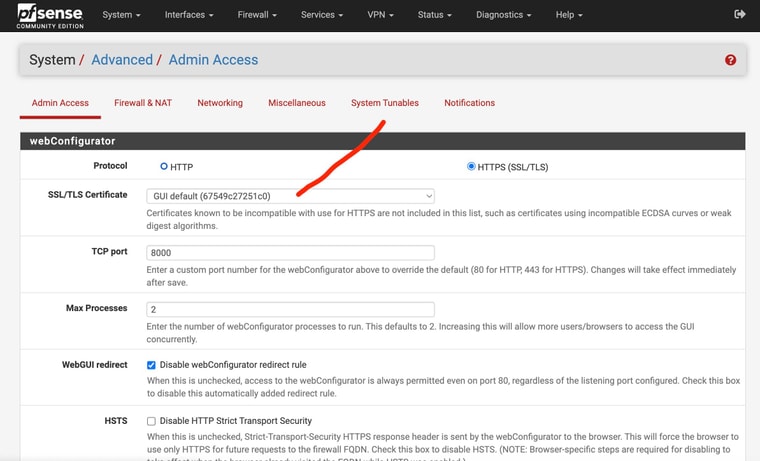
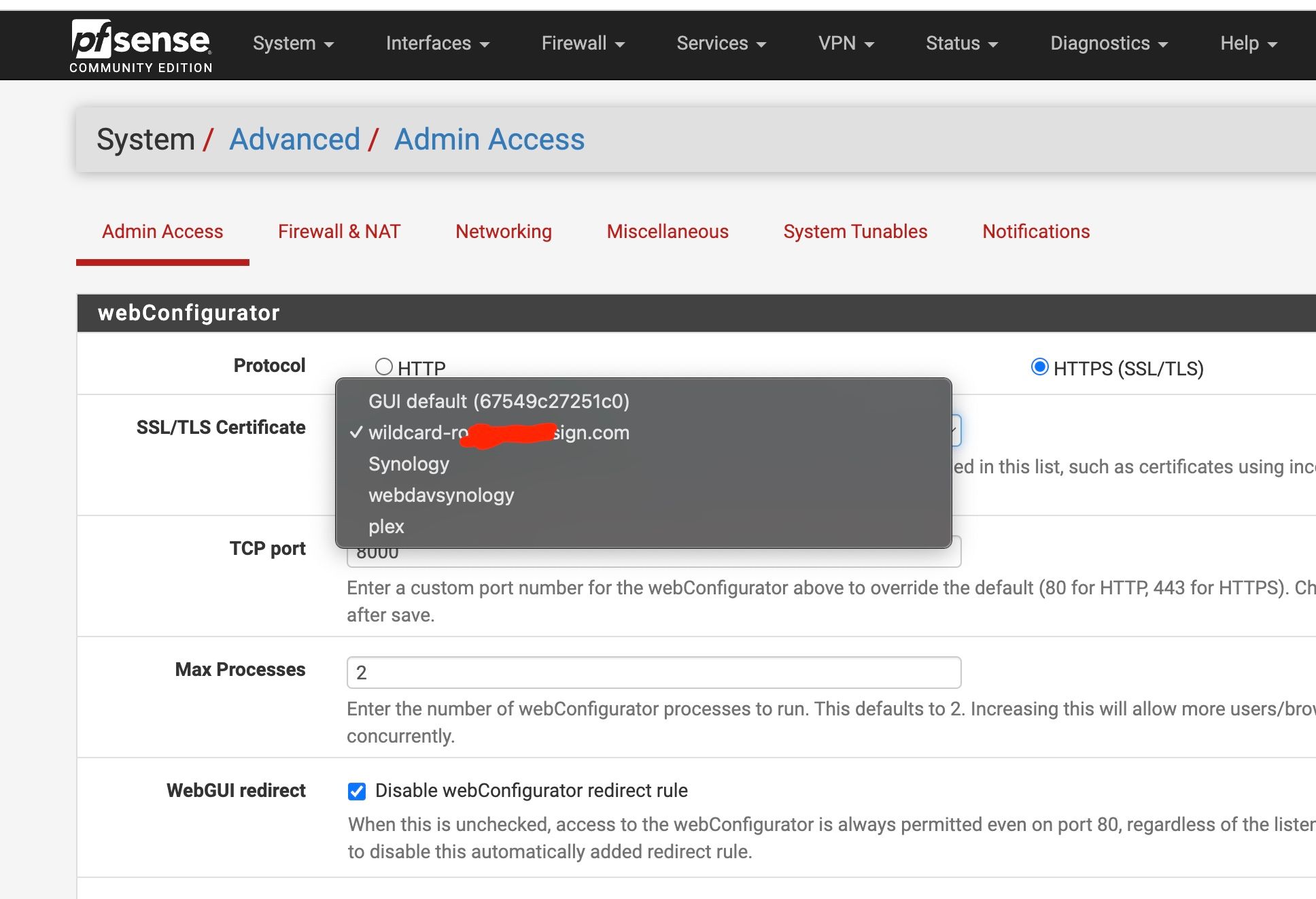
-
Well you have disabled the webgui redirect which is why you have to enter the port directly.
Did you do that to prevent it interfering with some other service?I'm not seeing a screenshot of your port forwards page. Unless it was much earlier in the thread?
-
Back again lol
Trying to get ready for the holidays so my side line IT job has sufferedDuring the last week- both of the ATT moderns gateways have remained online ( one with the direct interface connection and the other with the VLAN connection ) - that is with the static IP configuration.
Got around to a few fail over tests. Latest one tonight.
Upon unplugging the WAN cable from the fiber modem fail over is successful but 2 issues remain1 ) the ATT modem just doesn’t seem to behave as far as DNS resolution (will ping IP addresses but can’t resolve DNS) - unless I check Enable DNS Forward Mode in the DNS Resolver settings. We explored this before but never figured out why
- possibly bigger issues - when I plug the fiber modem cable back in the Frontier fiber internet cable just won’t come back online. Even if I “reset all states” it won’t come back online. The only way I can get the fiber modem Tier 1 gateway back online is to full reboot pfsense.
Ideas?
Thank you
-
@ahole4sure Hmm, how have you set up your resolver? Which interfaces have you selected in the list?
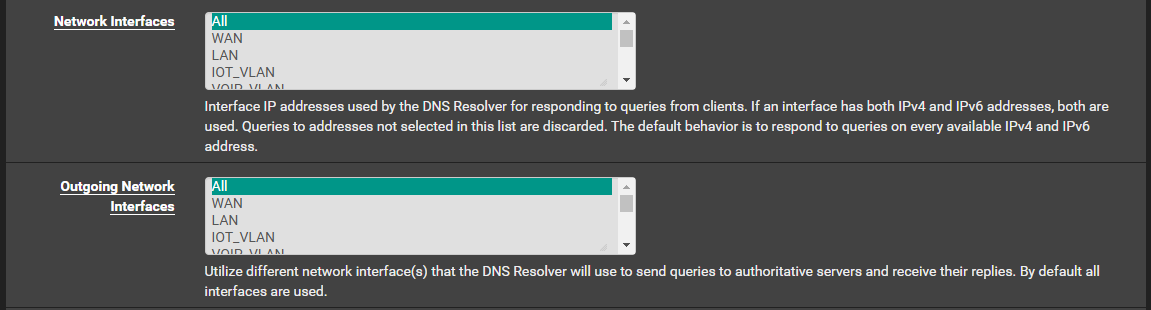
-
Hmm, odd. Unbound should be able to resolve directly via any outbound interface as long as it's selected. By default it tries to use all interfaces.
Do you see any blocked traffic? Do you see states on port 53 when failed over to the AT&T modem?The Frontier gateway shows as off line? Or the NIC never links?
-
I did not check for "blocked traffic". If I test again this PM would I just fail the WAN and then check the logs for the firewall? And where / how is best way to monitor or look for "states" on port 53?
As far as the Frontier WAN interface -- the gateway on the status page shows red or "offliine" for much longer than expected (like a couple minutes), then it flashes to blue "unknown", then back to offline, then back to blue unknown -- ultimately after 4 or 5 minutes it settles in on blue unknown and just never links back up. I then tried reset states --- Ulitmately the only thing that lets it reconnect is just go to Diagnostics and choose "normal reboot". Back online , like normal, after the reboot.
-
@ahole4sure I guess the two problems are separate and not necessarily related. So on the first one about the DNS issue, which I responded to, have you checked the settings for the resolver? Which interfaces have you selected for it to use?
In the forwarder, there is no such setting and I assume it's automatic as @stephenw10 suggests. -
Go to Diag > States and filter by
:53What is logged in the System and Gateway logs when you reconnect the Frontier modem?
How are you running the failover test? Physically unplugging something? -
@stephenw10 I'll have to retest and check the logs
And yes to fail - I just unplug the ethernet cord from the back of the frontier modem