ATT Internet AIr
-
-
-
also btw, I am not sure what .179 is
it is not the device I'm testing form - but the network is large with probably more than 50 or 60 devices connectedThe routing table does not gicve the device a name (like many have) - it just gives a MAC address
-
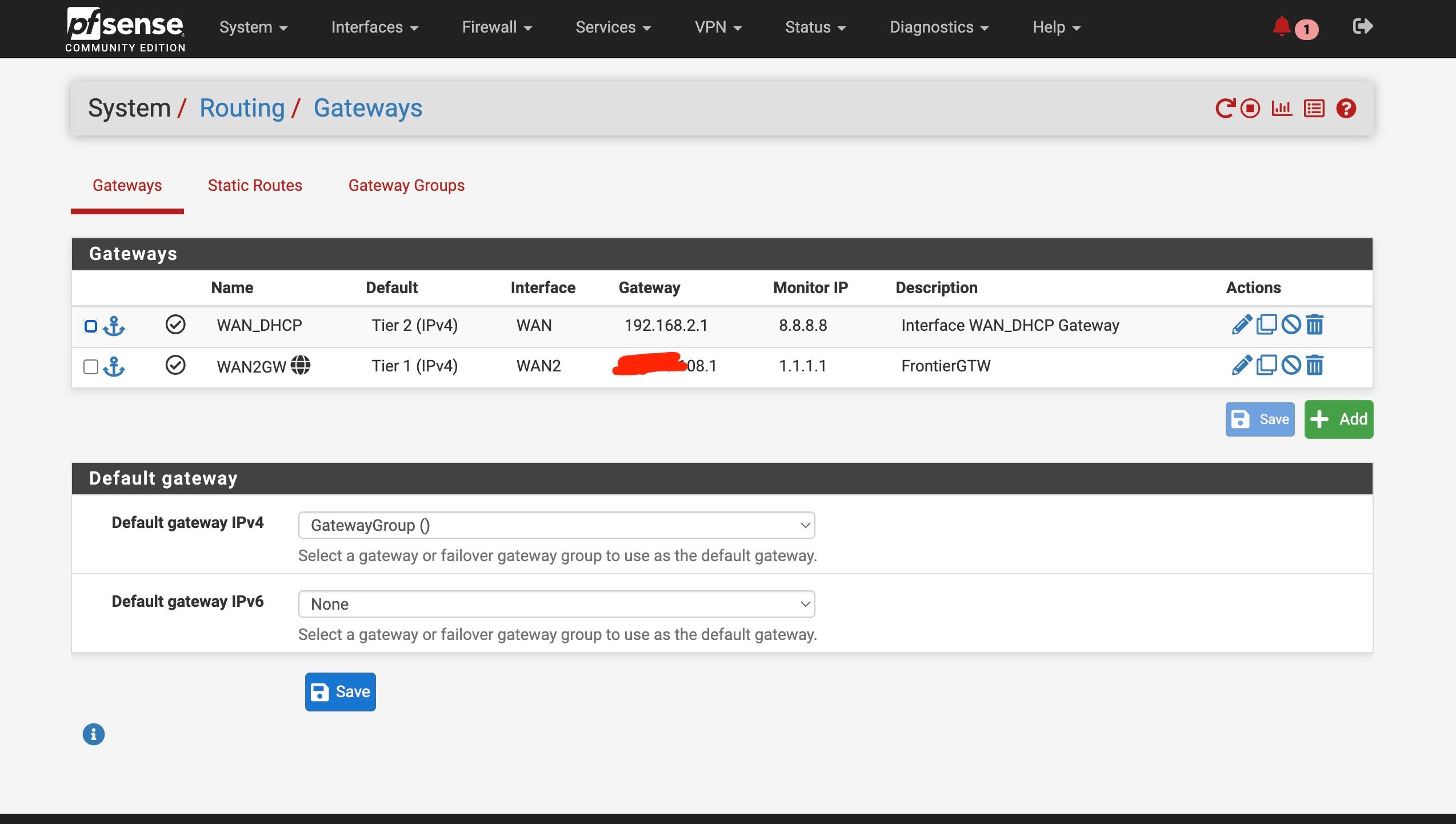
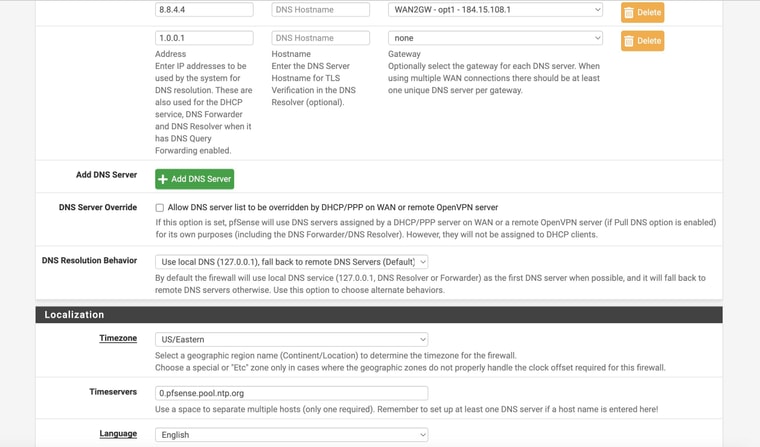
Ok you have some conflicting settings there. You have DNS servers set with specific gateways and you also have the same DNS servers set as monitoring IPs for the gateways. Both those thing add static routes and must match to work correctly.
In your setup you don't need to set gateways on the configured DNS servers because they should work on either WAN and you're using a failover group as the default gateway. Additionally your are resolving directly so the DNS servers configured there are only used as a backup. However the conflicting static routes still breaks DNS for anything trying to use those servers directly. So remove the gateway settings from the DNS servers on the general setup page.
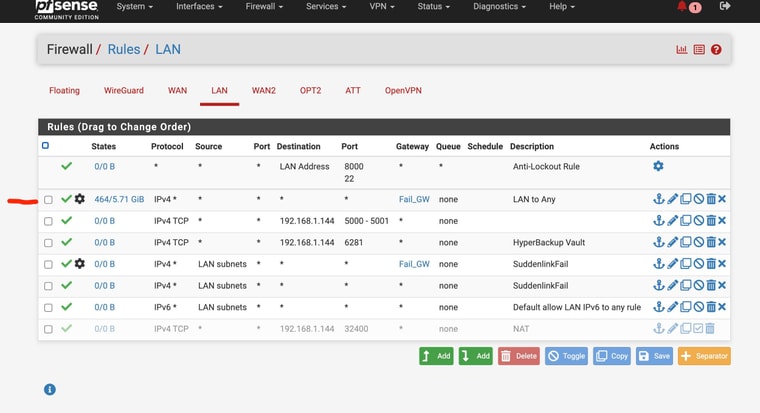
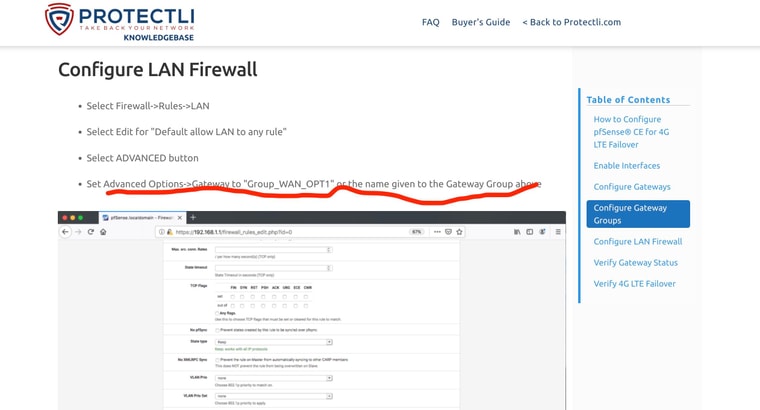
If you add a failover group to the pass rules on LAN you bypass rules for local traffic. That includes DNS traffic from LAN side clients to the LAN interface. Otherwise it will be forced out of the WAN and never reach Unbound in pfSense.
-
Ok. Thank you for advice
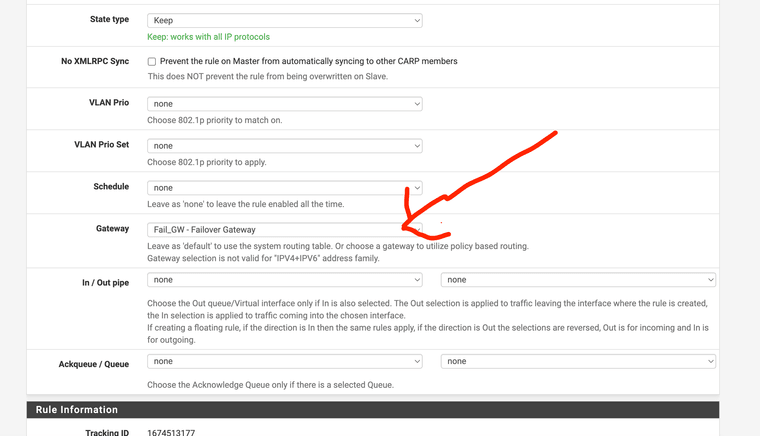
I’ll change the DNS settingsSo do I leave the advanced LAN rule like Protectli recommended or change back to not using. I’m sorry I wasnt clear …
-
This post is deleted! -
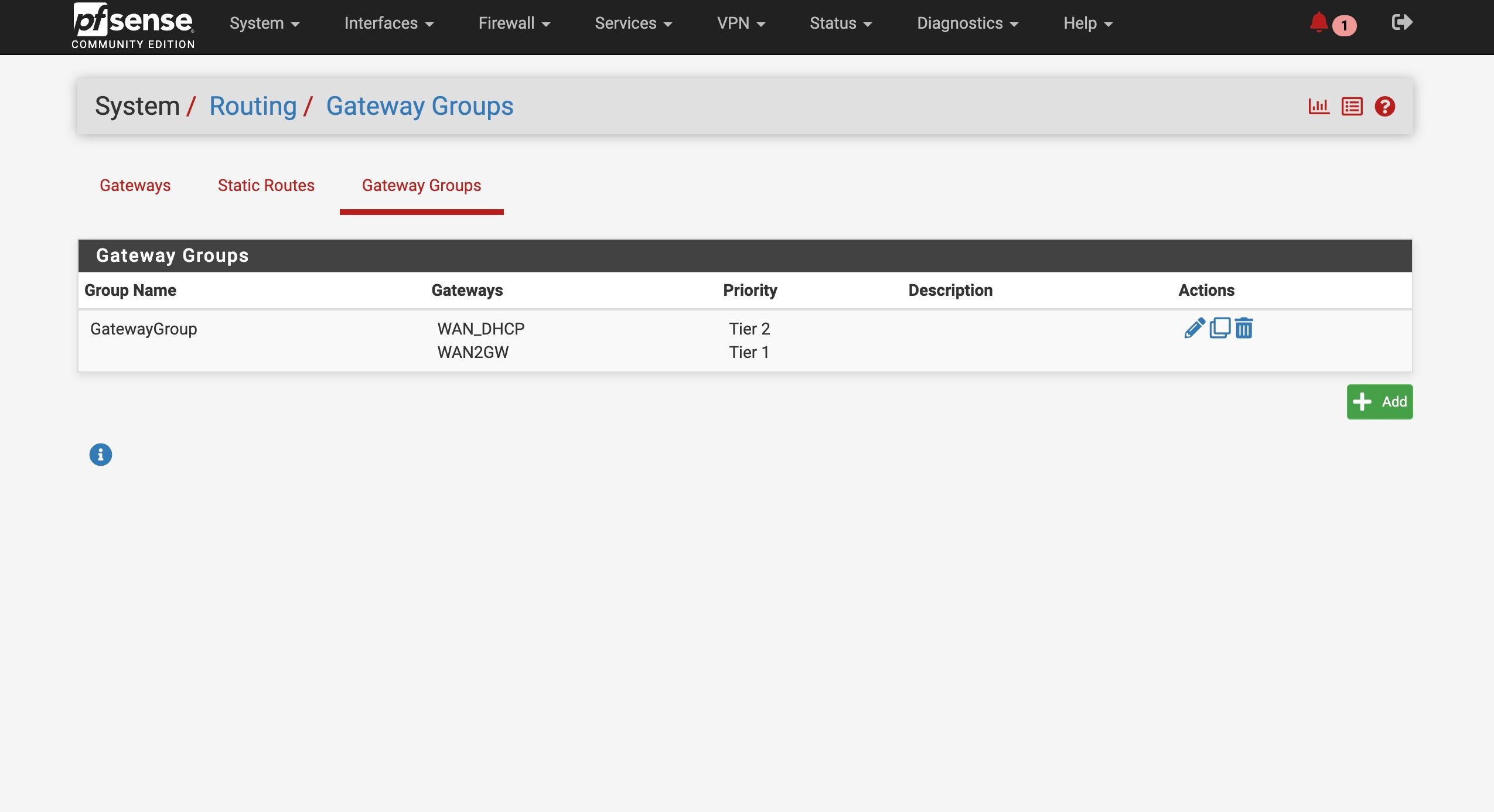
@stephenw10
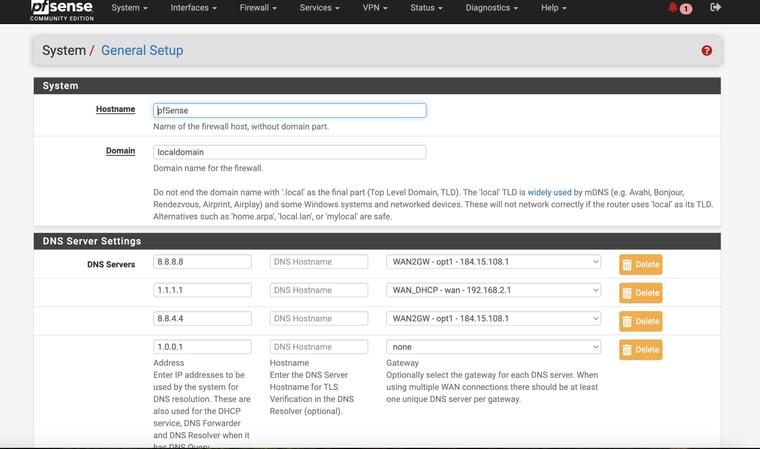
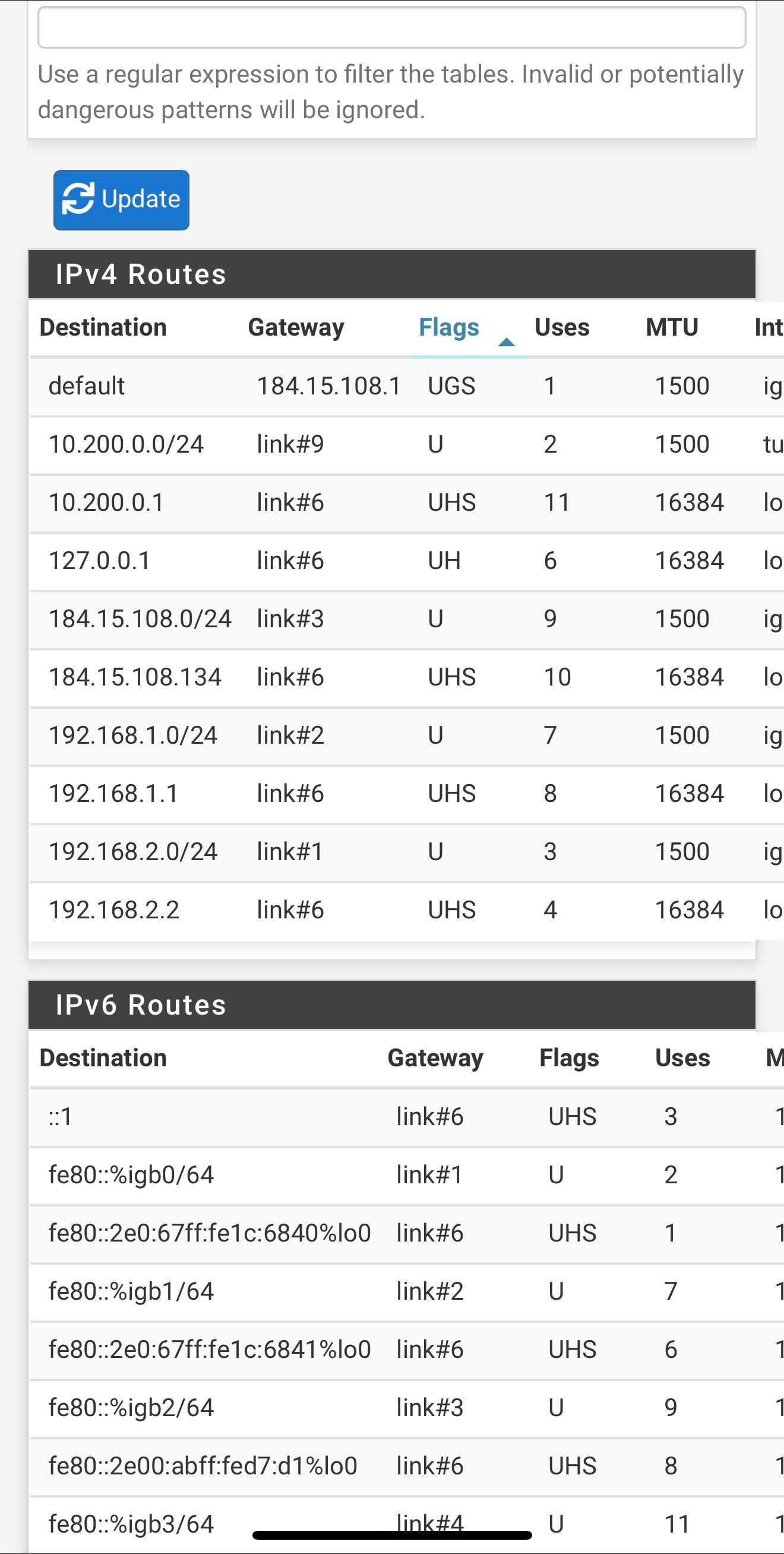
Here is the new routing table after removing the DNS static routes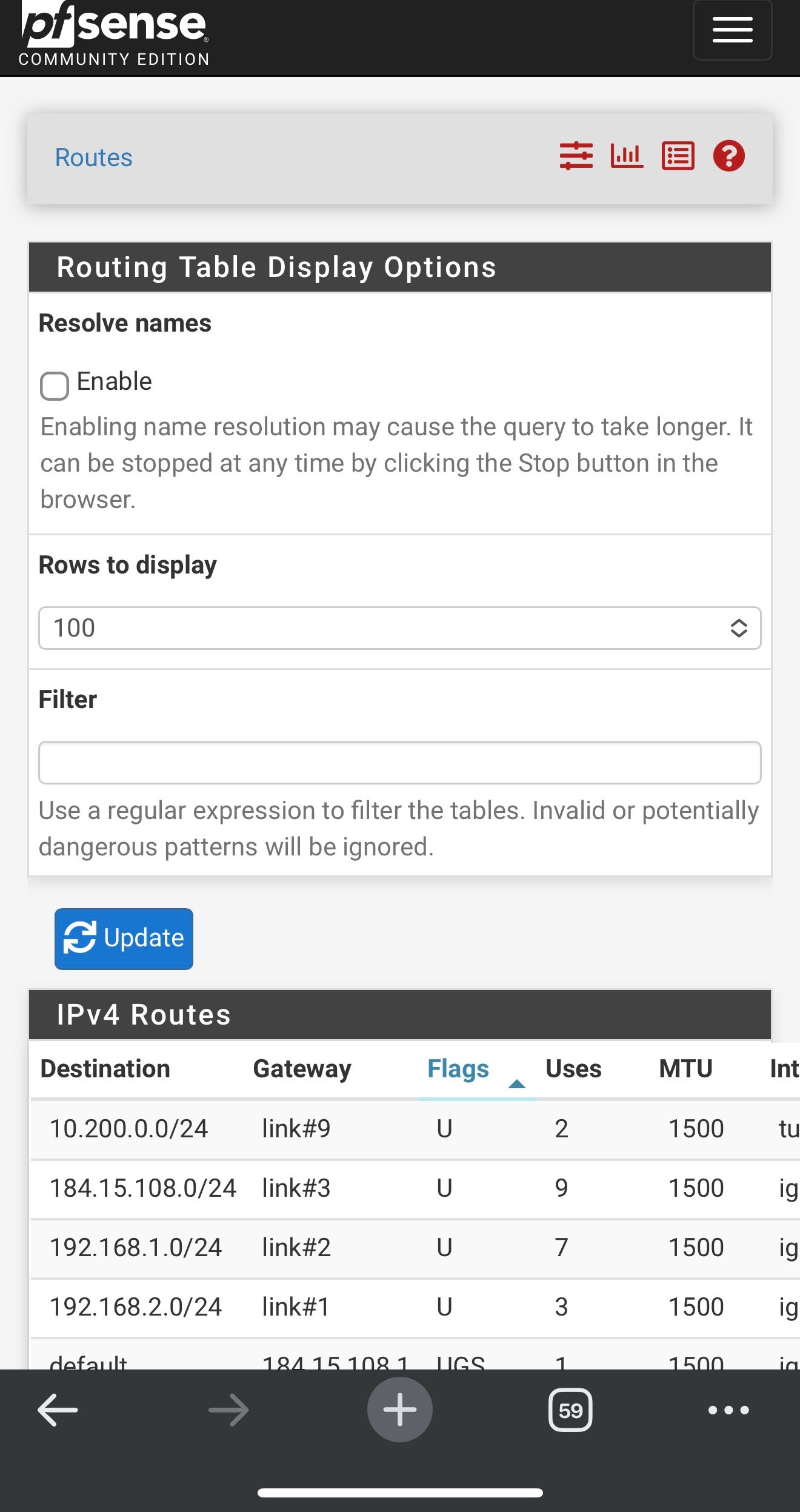
-
Hmm, well I still expect to see the gateway monitoring IPs there, did you remove those too?
Anyway that device at 192.168.1.79 should work fine trying to access 8.8.8.8 directly.
I'm assuming (because it's the default) that your LAN side clients are being passed the LAN interface address to use for DNS?
-
@stephenw10
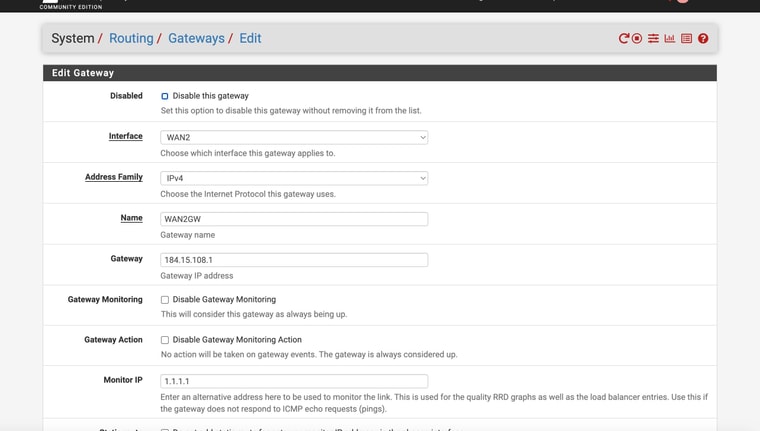
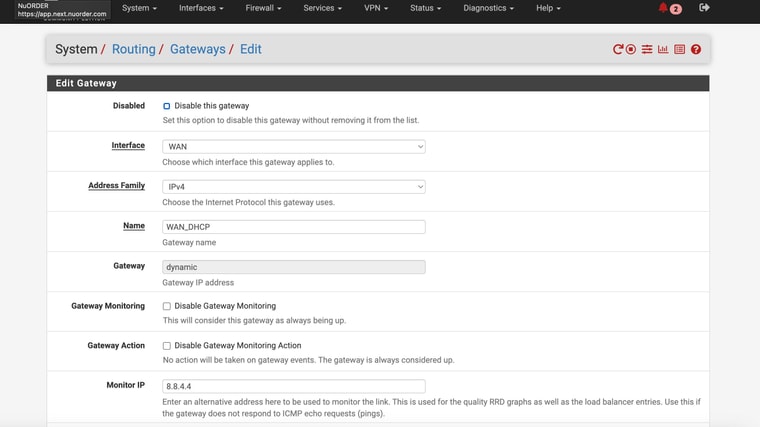
I didn't change the monitor IP's on the gateways
??
Is this what you were referring to?
-
I'm not on site until Tuesday - not sure how to safely test while being remote (unless you have ideas on how to "fail" the main internet and not lose connection ??
-
Hmm, I expect to see static routes for 8.8.4.4 and 1.1.1.1 unless you have checked the box to not add them on the gateway config page.
You may need to resave them to add those routes. Though not doing so should not affect DNS.
If you have the DMZ feature setup on the AT&T router you should be able to access the WAN remotely as long as rules allow it. However I'm not sure I would want to try disconnecting WAN2 without being on site to recover it if required.
-
@stephenw10
Weird -- might even be a part of why I need to reboot after a failed state
BUT. I had to completely reboot the box to get those static routes to show back up (the monitor IPs). Resaving the interface settings , restarting the service , etc - nothing brought back the expected routes until I rebooted the box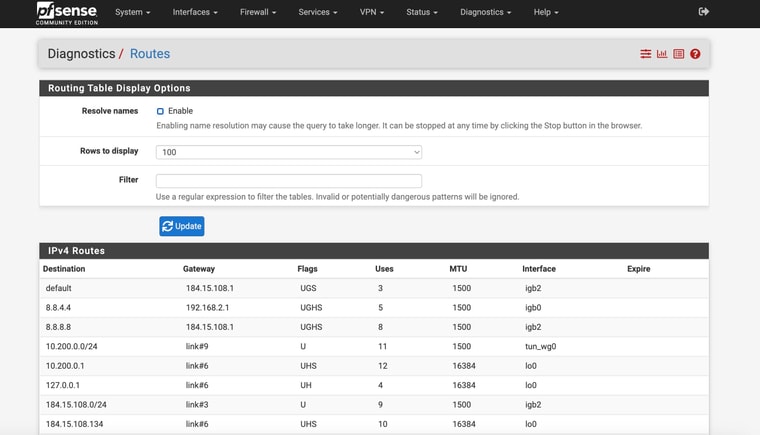
-
Ok, you should not use 8.8.8.8 though since at least one device you have is trying to use it. If you use it as a monitoring IP it can only ever work via that gateway.
-
@stephenw10
Ok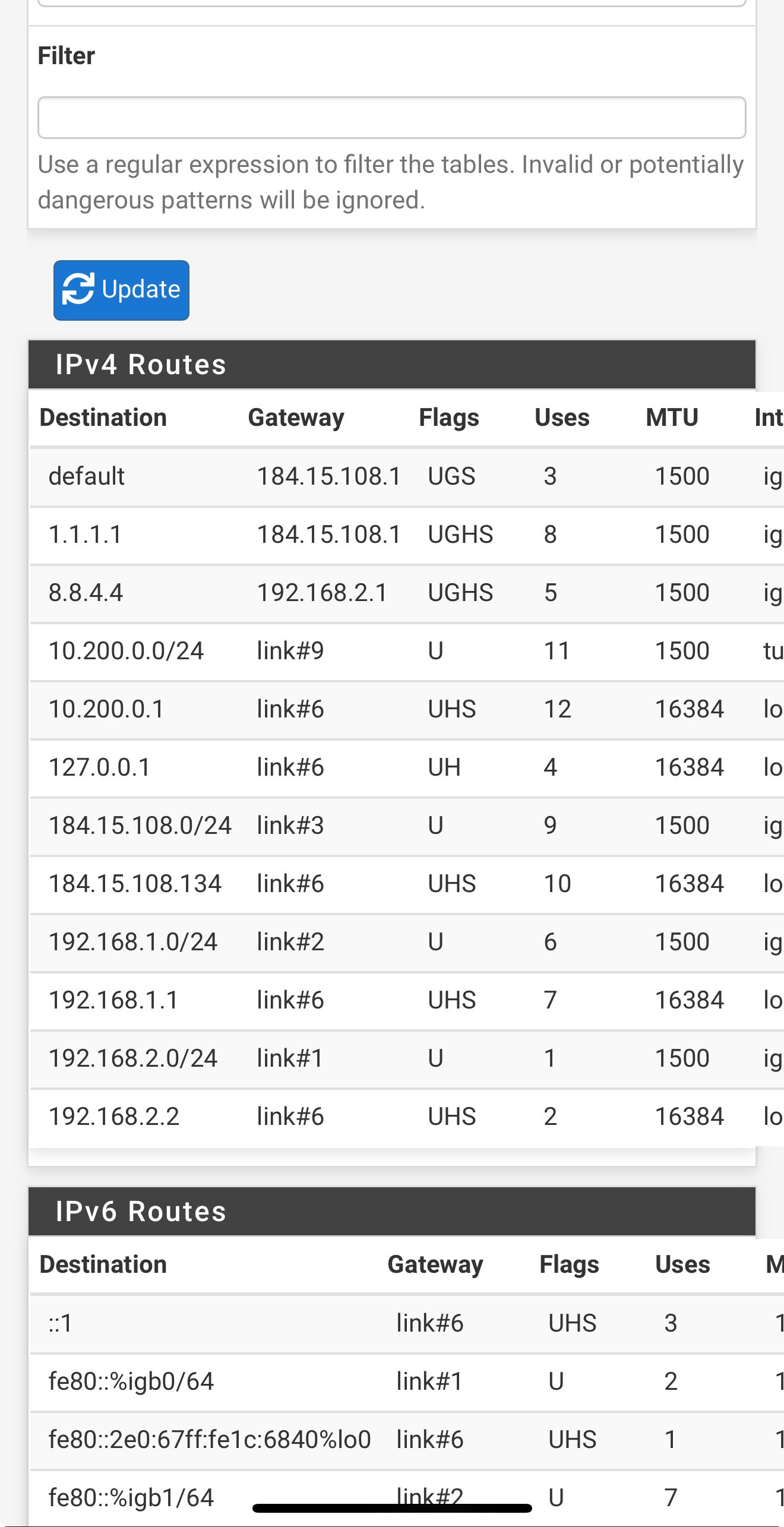
-
Ok, good. Well with that that one device should work at least.
So to confirm you are still passing the LAN address to clients for DNS?
-
Thanks for hanging in there and helping! Need to buy you a big cup of coffee!
Not sure I understand what you mean with your question. Sorry
-
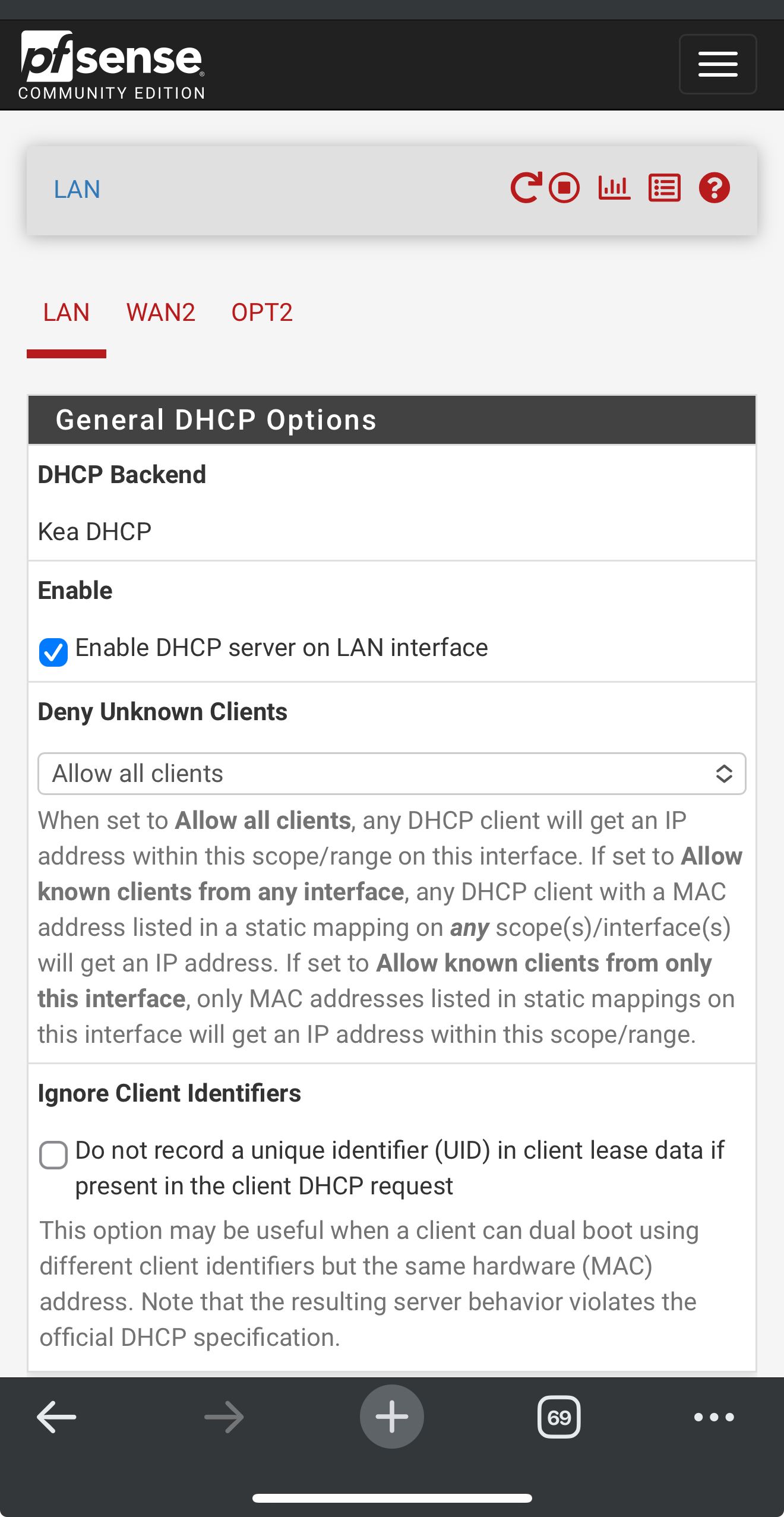
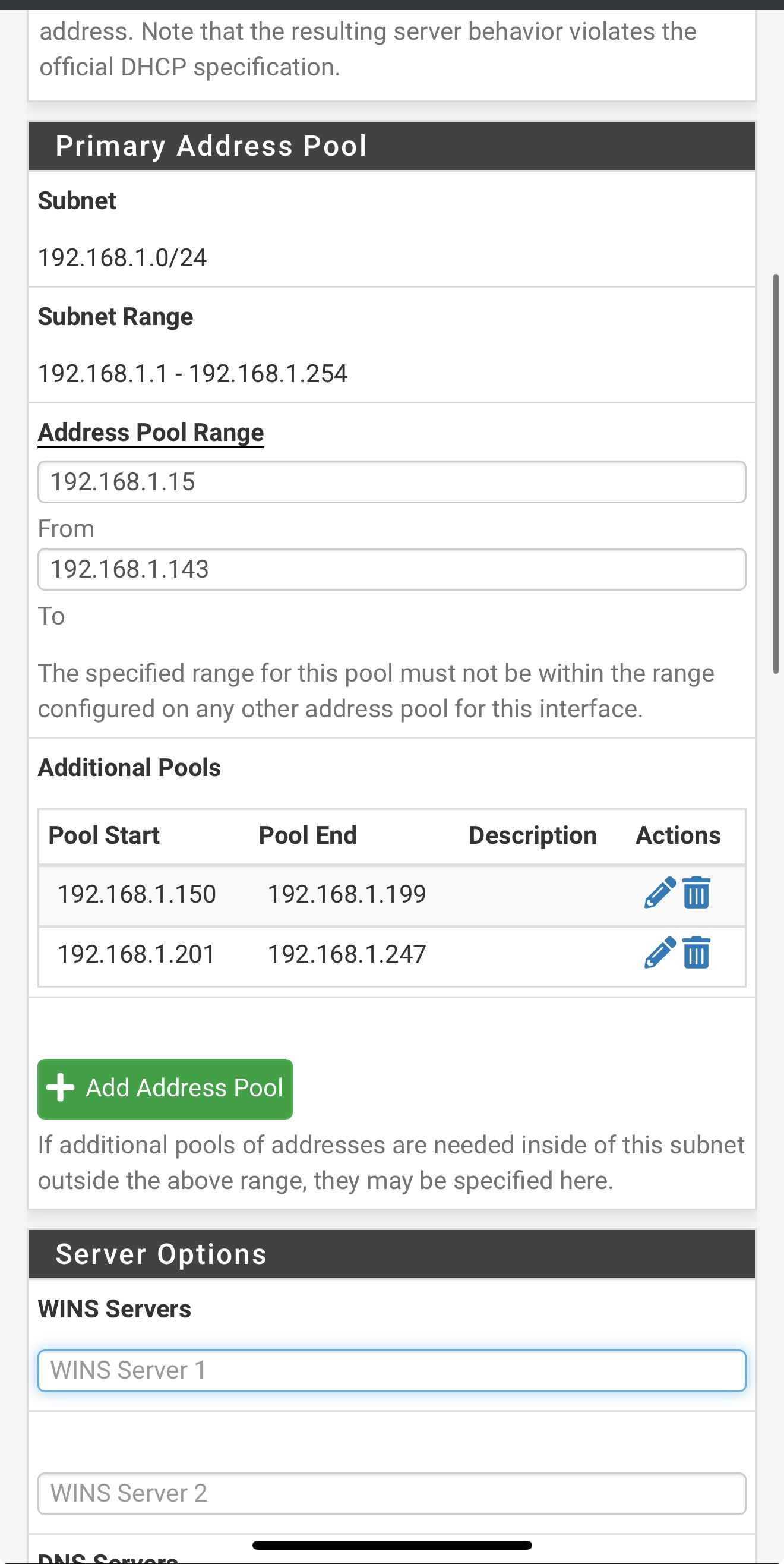
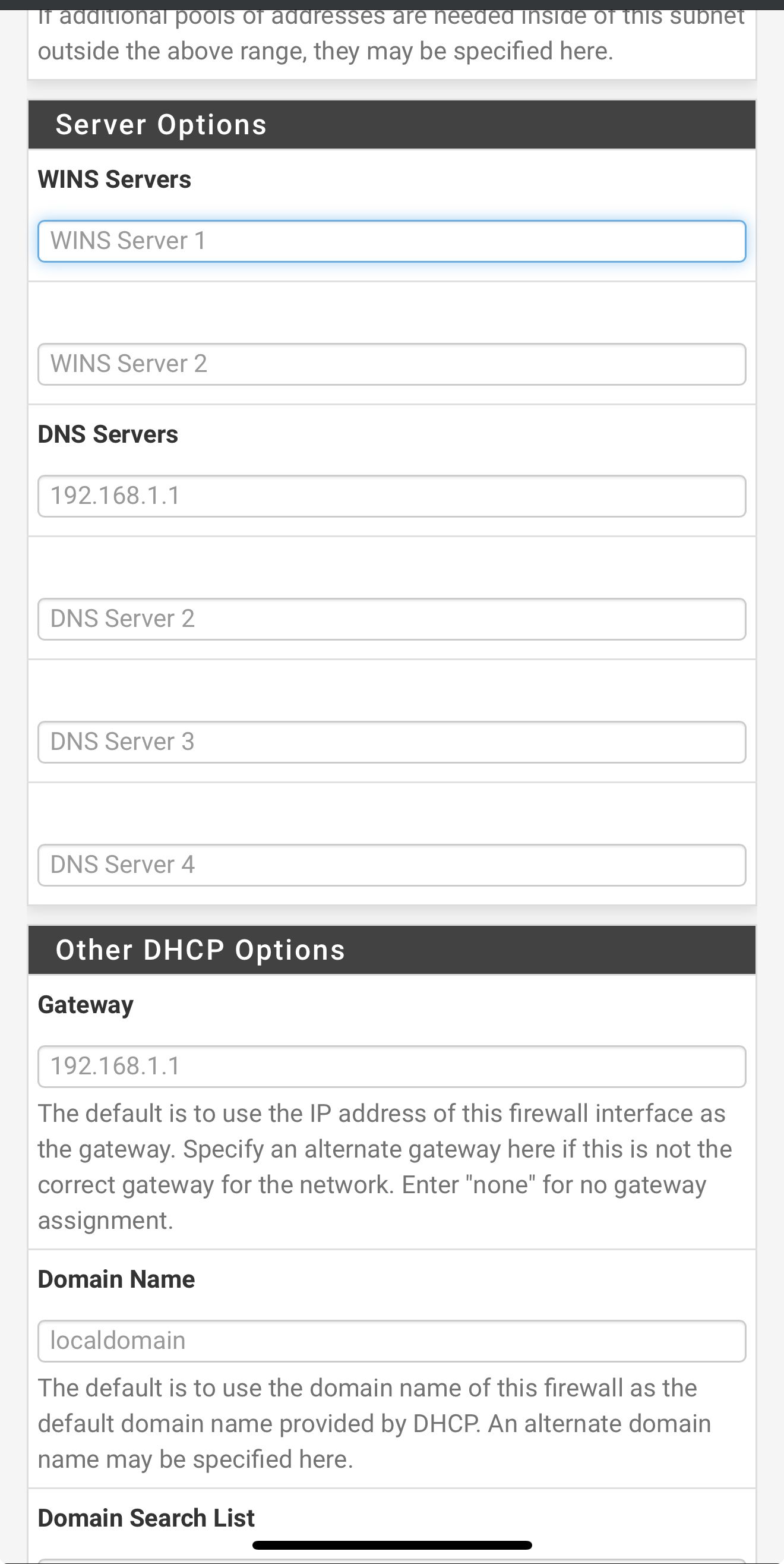
In the LAN DHCP server config have you entered any DNS servers to pass to clients when they pull a lease?
If you don't enter anything there it will pass the DHCP server address (LAN address) to clients to use for DNS by default. That means they use Unbound in pfSense which should work on both WANs.
If you passed, for example, 8.8.4.4 or 1.1.1.1 that can only work via one WAN.
-
This post is deleted! -
So I’m on my iPhone so it not great screenshots
But here are my LAN DHCP server settingsShould I change something? It’s kinda greyed out but DNS is listed as 192.168.1.1
-