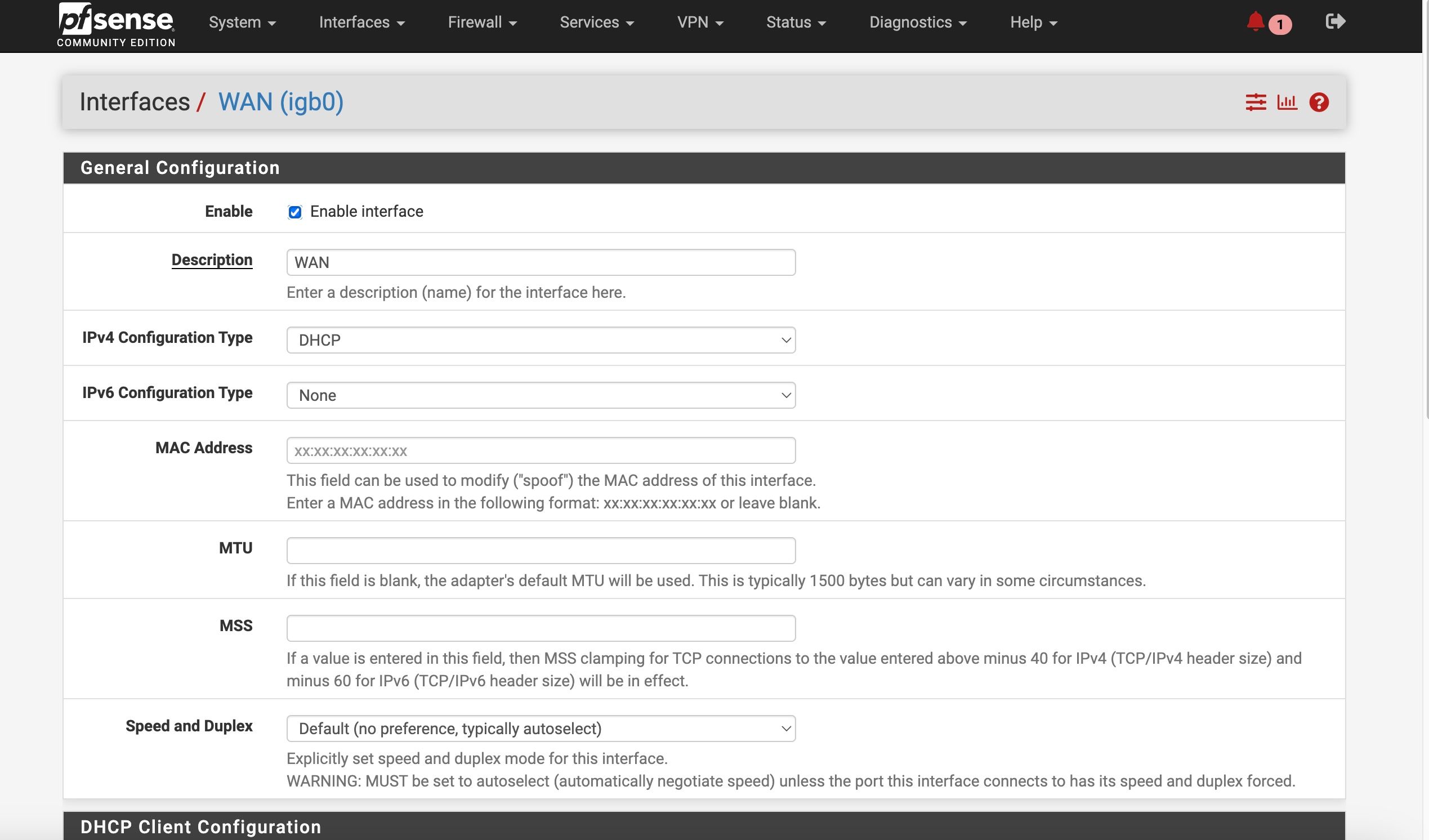
ATT Internet AIr
-
Hmm, I expect to see static routes for 8.8.4.4 and 1.1.1.1 unless you have checked the box to not add them on the gateway config page.
You may need to resave them to add those routes. Though not doing so should not affect DNS.
If you have the DMZ feature setup on the AT&T router you should be able to access the WAN remotely as long as rules allow it. However I'm not sure I would want to try disconnecting WAN2 without being on site to recover it if required.
-
@stephenw10
Weird -- might even be a part of why I need to reboot after a failed state
BUT. I had to completely reboot the box to get those static routes to show back up (the monitor IPs). Resaving the interface settings , restarting the service , etc - nothing brought back the expected routes until I rebooted the box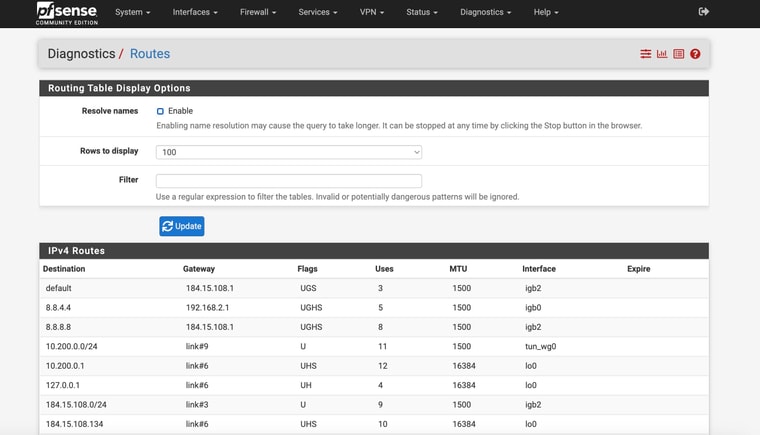
-
Ok, you should not use 8.8.8.8 though since at least one device you have is trying to use it. If you use it as a monitoring IP it can only ever work via that gateway.
-
@stephenw10
Ok
-
Ok, good. Well with that that one device should work at least.
So to confirm you are still passing the LAN address to clients for DNS?
-
Thanks for hanging in there and helping! Need to buy you a big cup of coffee!
Not sure I understand what you mean with your question. Sorry
-
In the LAN DHCP server config have you entered any DNS servers to pass to clients when they pull a lease?
If you don't enter anything there it will pass the DHCP server address (LAN address) to clients to use for DNS by default. That means they use Unbound in pfSense which should work on both WANs.
If you passed, for example, 8.8.4.4 or 1.1.1.1 that can only work via one WAN.
-
This post is deleted! -
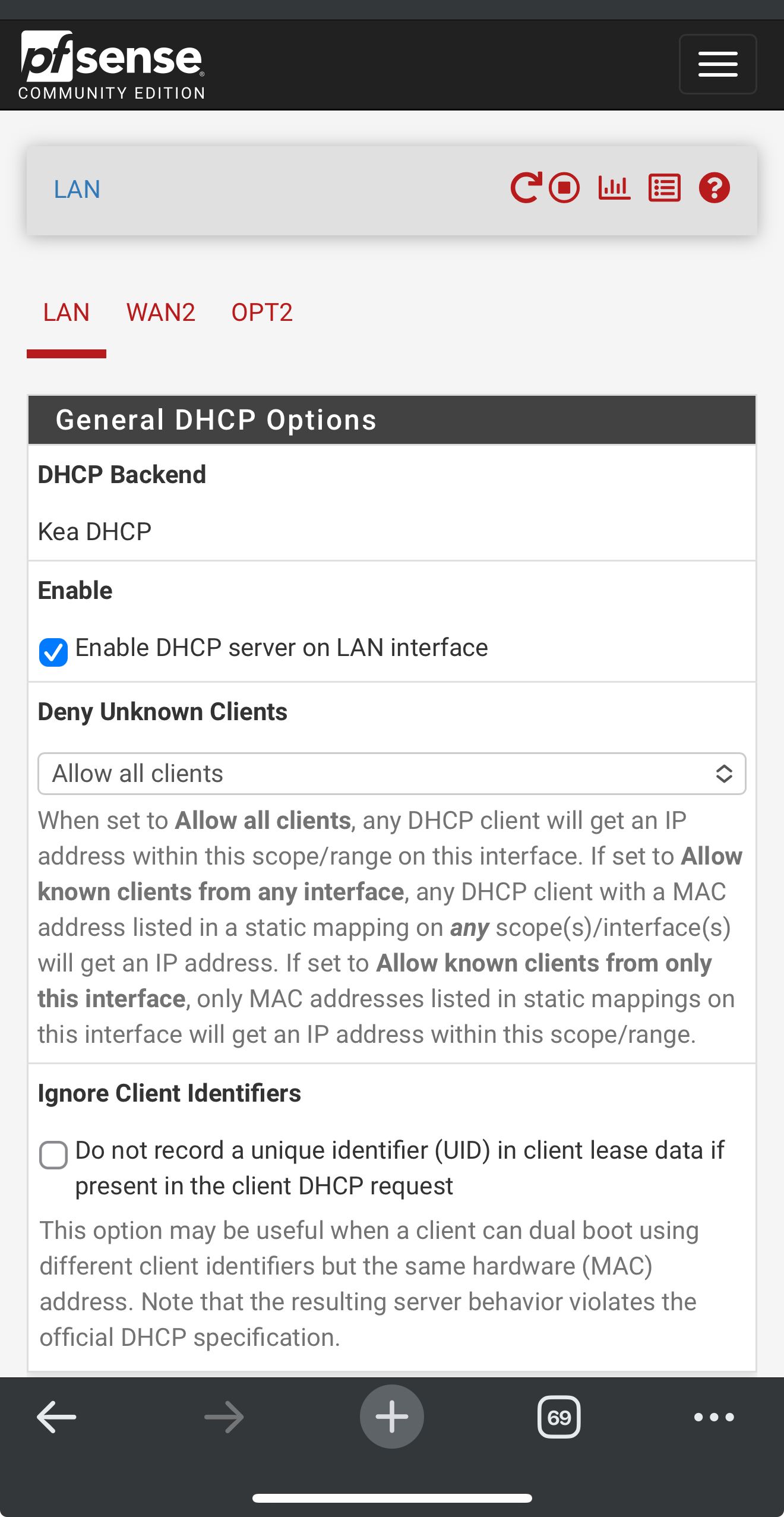
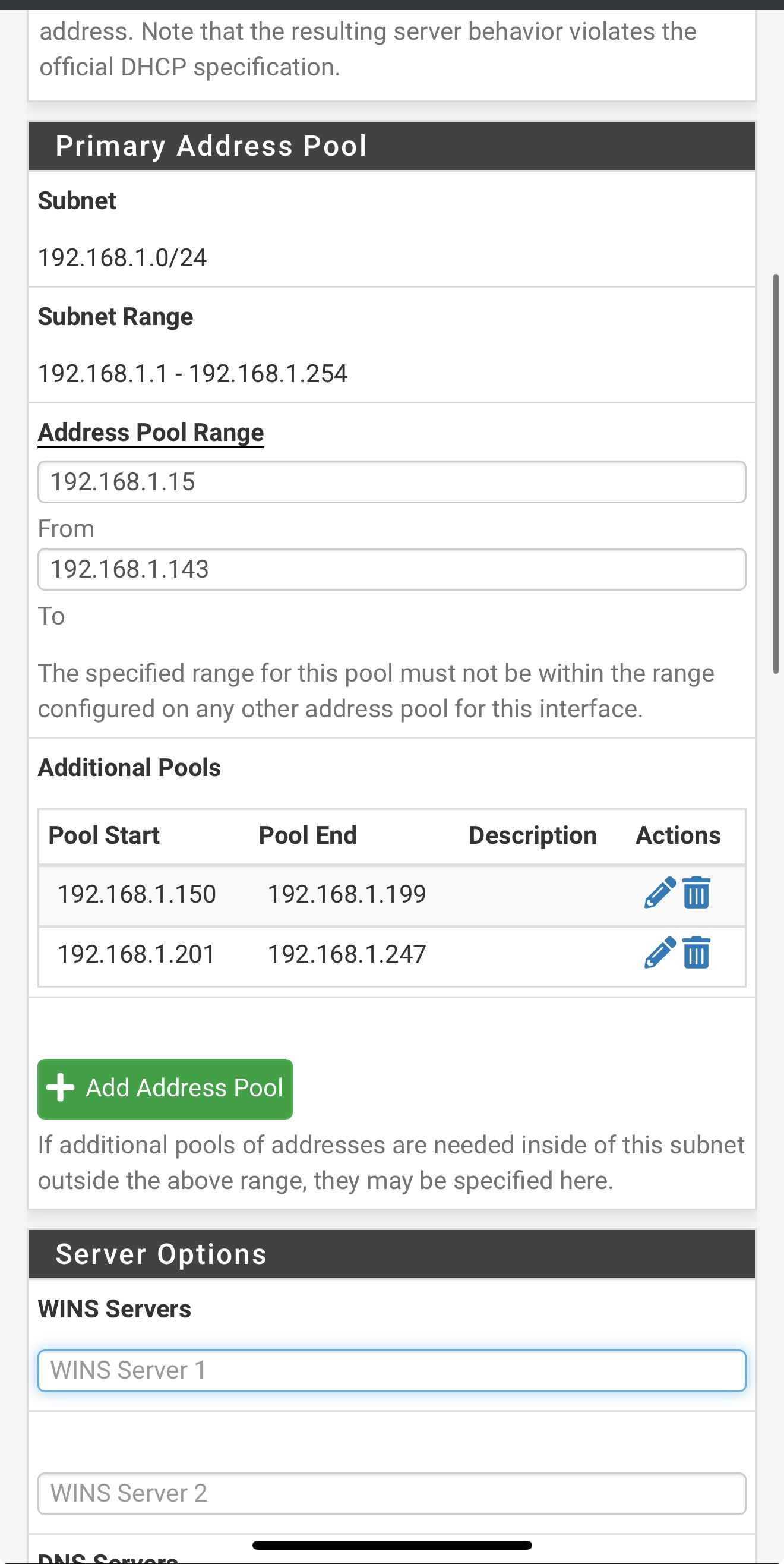
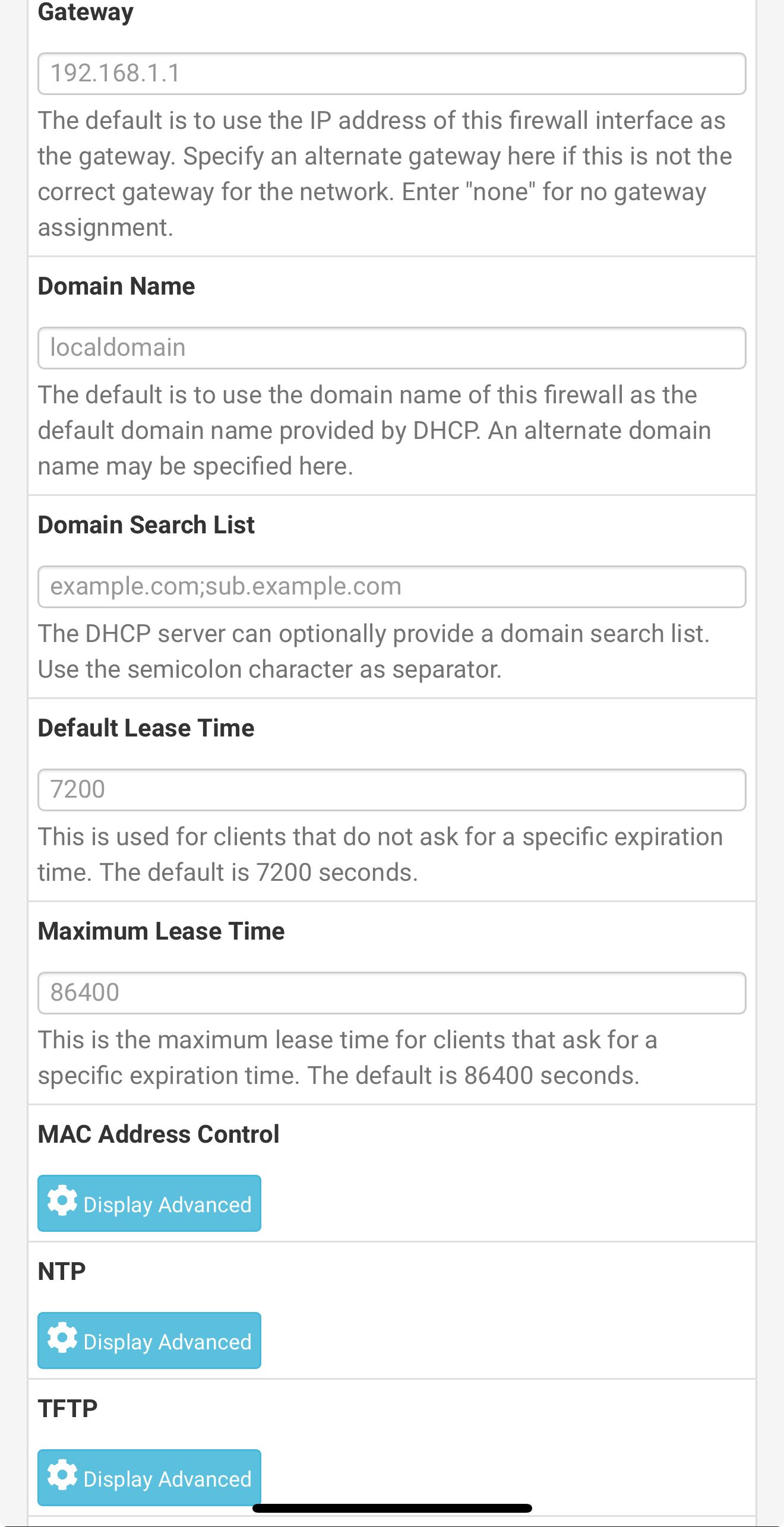
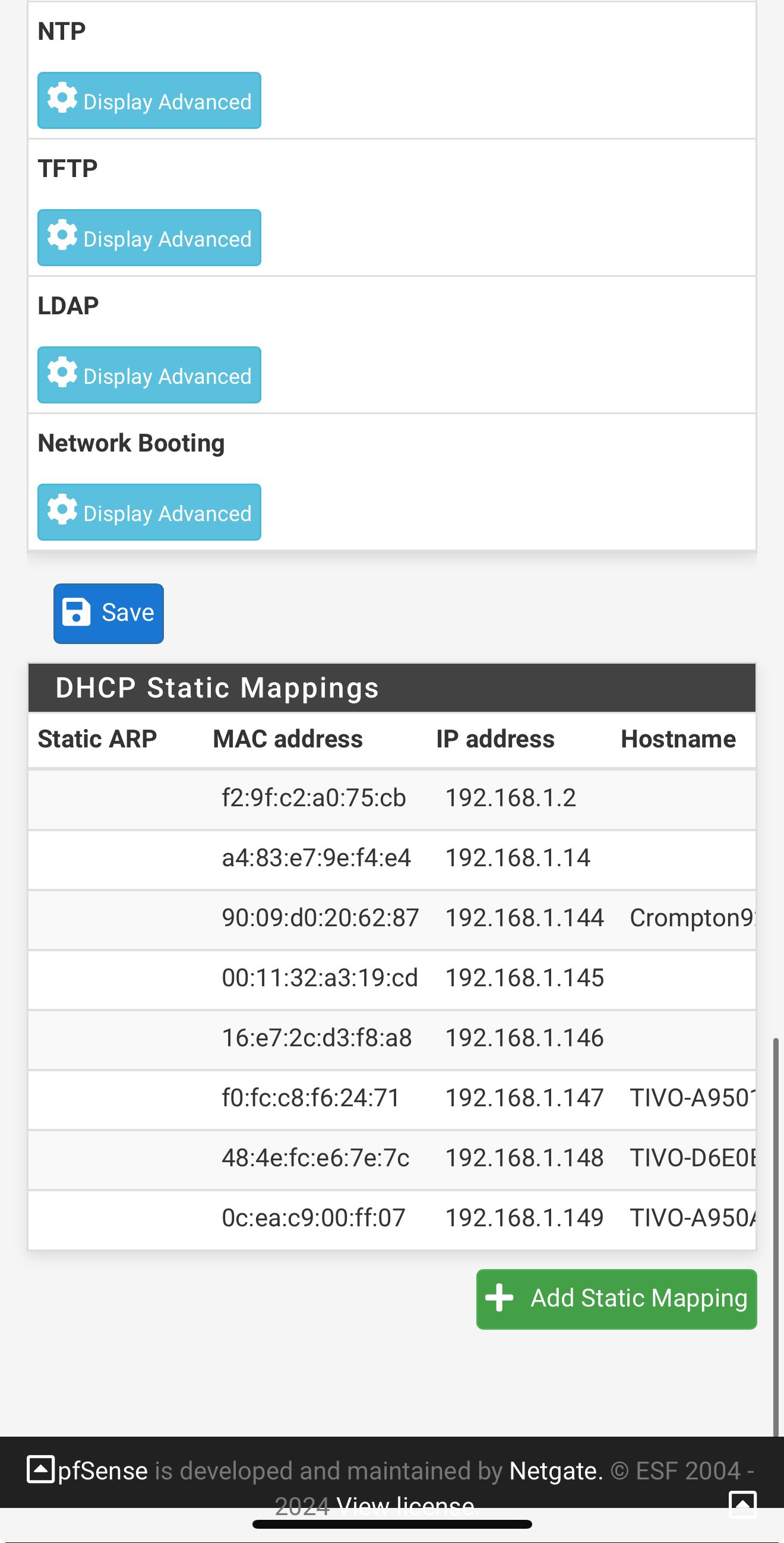
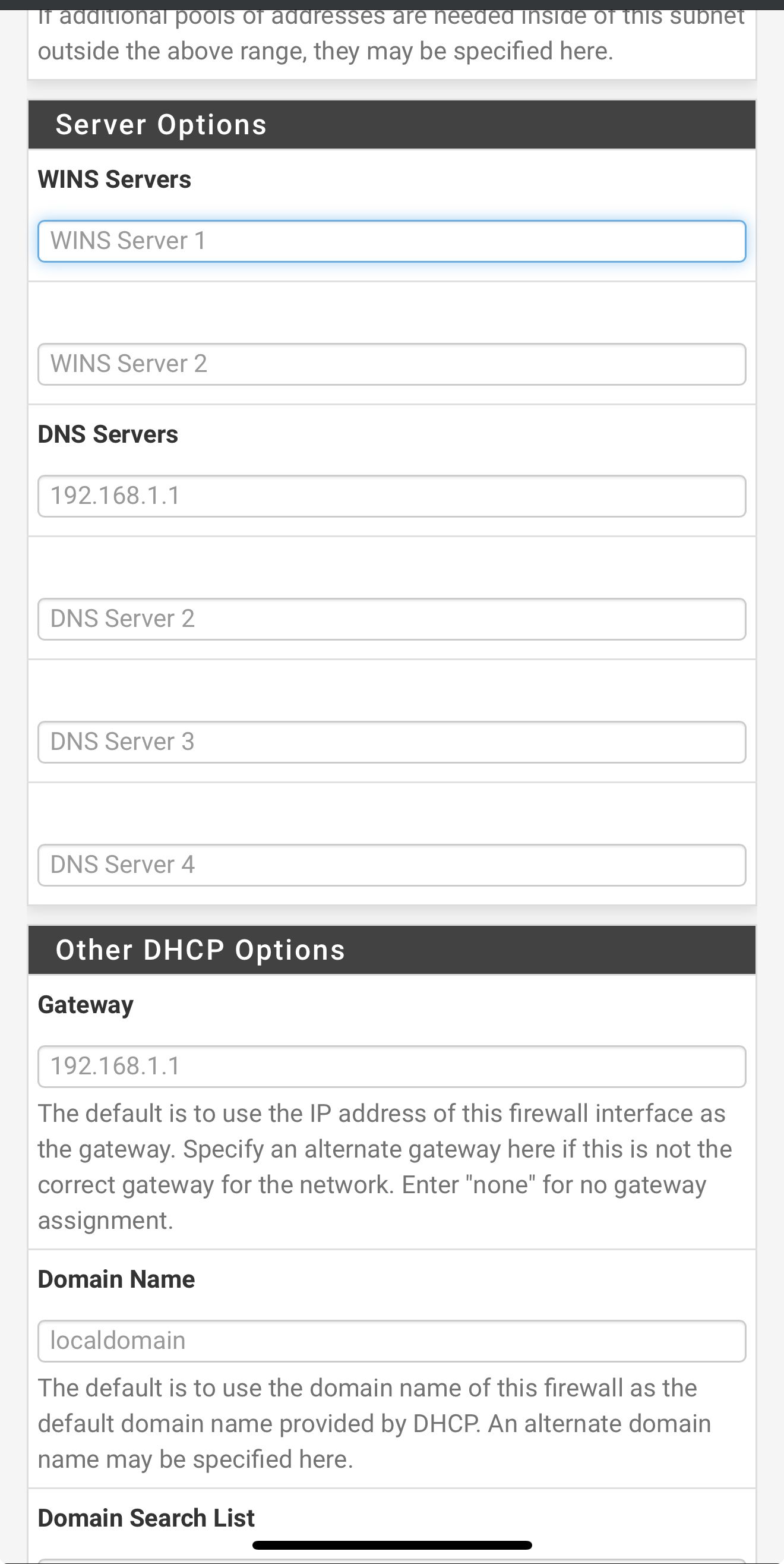
So I’m on my iPhone so it not great screenshots
But here are my LAN DHCP server settingsShould I change something? It’s kinda greyed out but DNS is listed as 192.168.1.1
-
-
-
Ok, so it's passing the LAN interface. That should be fine for anything that uses it. That one client is hard coded to use 8.8.8.8.
The root issue here though still seems to be that Unbound in pfSense is not using the WAN connection when WAN2 is down. I think you will need to test on site though.
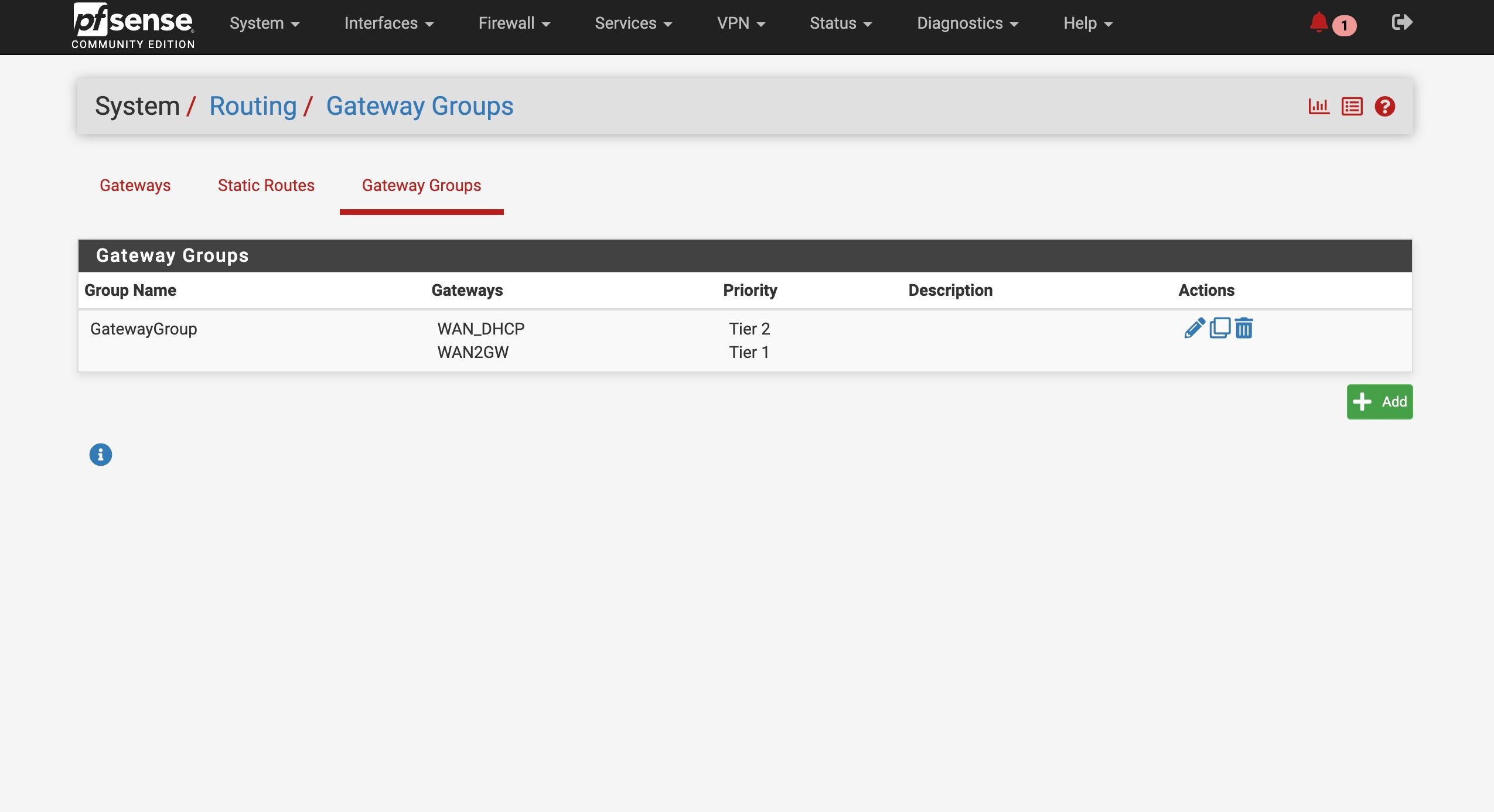
Try setting up another failover group that has WAN as the tier1 gateway. Then try setting that as system default and retest. In that situation Unbound should already be using WAN when WAN2 is disconnected and should continue to work. It should also failover to WAN2.
-
@stephenw10
Back on site
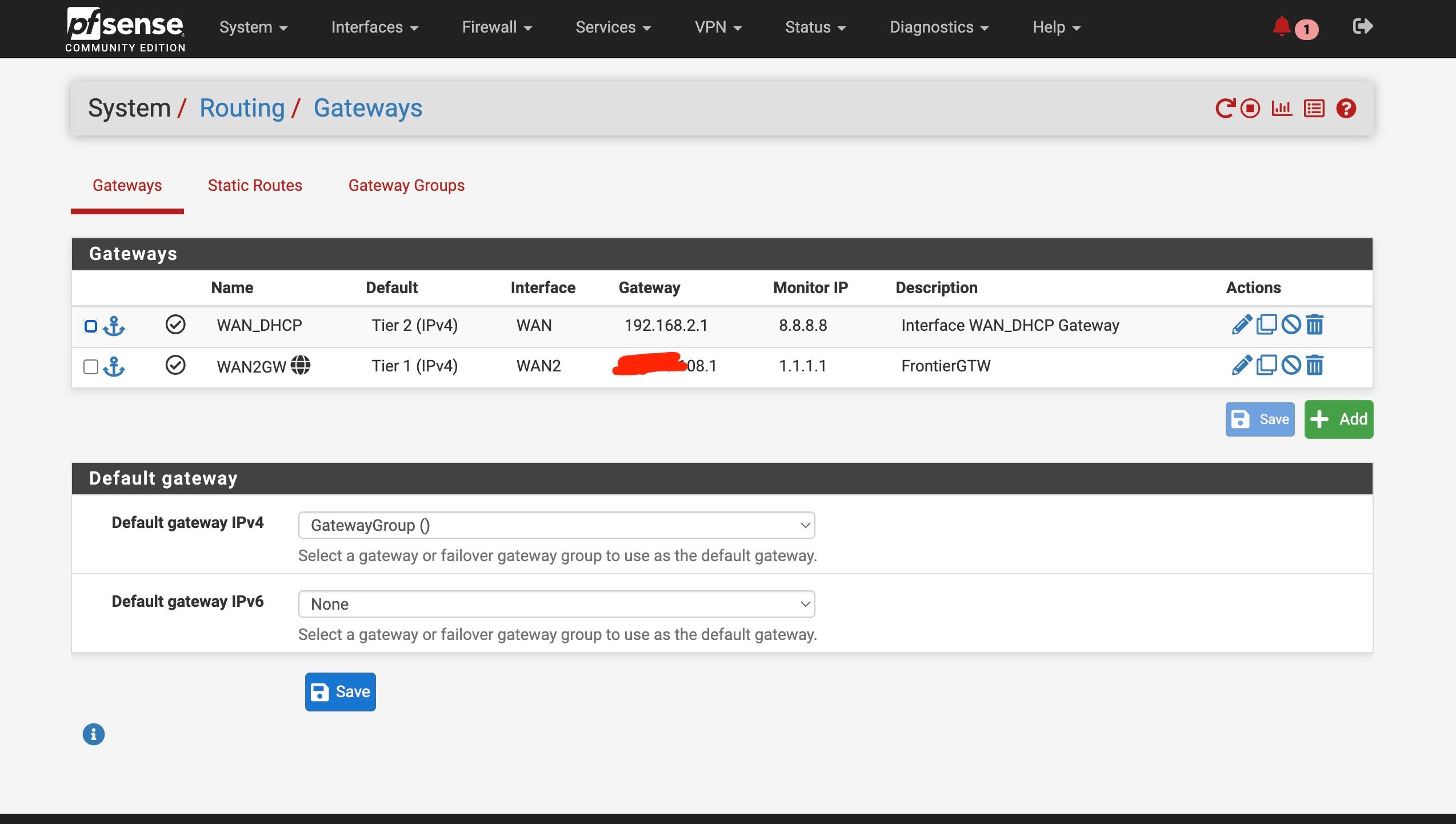
Set up the second test gateway group
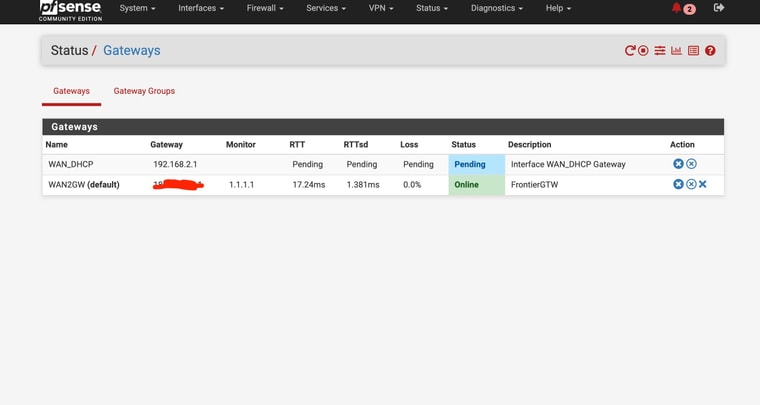
WAN as Tier 1 , WAN2 as tier 2When I set the test group as default, it switched to WAN ——- no internet/ DNS
Switched back to other gateway, internet/DNS returned without reboot
-
Hmm, were you able to see DNS traffic on WAN in the states?
Starts to look like the WAN connection just blocks or intercepts DNS for some reason.
You can try to test that directly from the pfSense command line with something like:
dig @8.8.8.8 netgate.com -b 192.168.2.2 -
@stephenw10
No joy directly from command line!If I knew for sure another failover device/method would for sure work I would consider returning the Internet Air devices - lol
Now it's just irritating that this is so difficult (esp with expert help like you)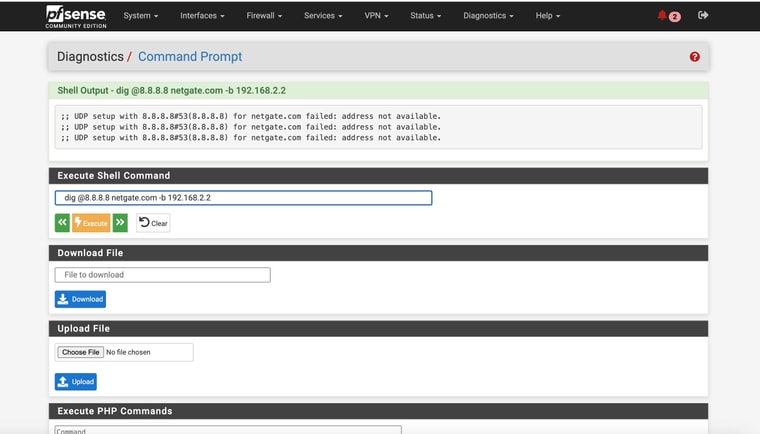
-
Did the WAN IP change from 192.168.2.2? By binding to that address the query is forced to use the WAN.
-
@stephenw10
OMG, sorry
I'll have to get back on-site this afternoon - looks like the WAN device went offline or something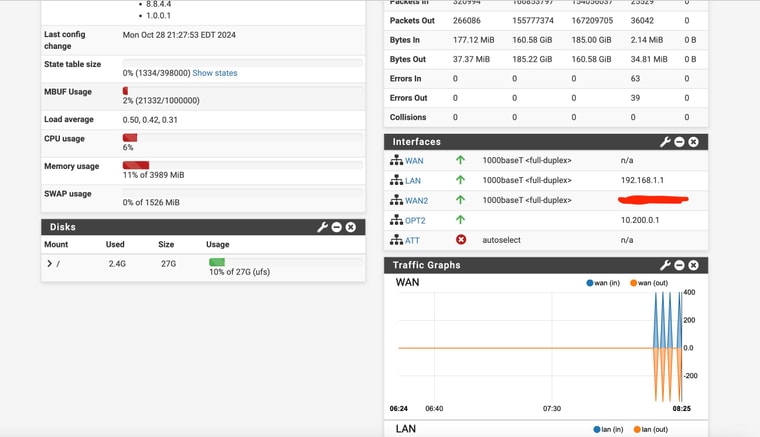
-
Ah, that would do it.

-
@stephenw10
Got back on site and restarted the WAN
It is back up and going on 192.168.2.2
If I do the test gateway group , I am still losing DNS/Internet with WAN as Tier 1 and primary internetBut I did get differnt result with the command line
see below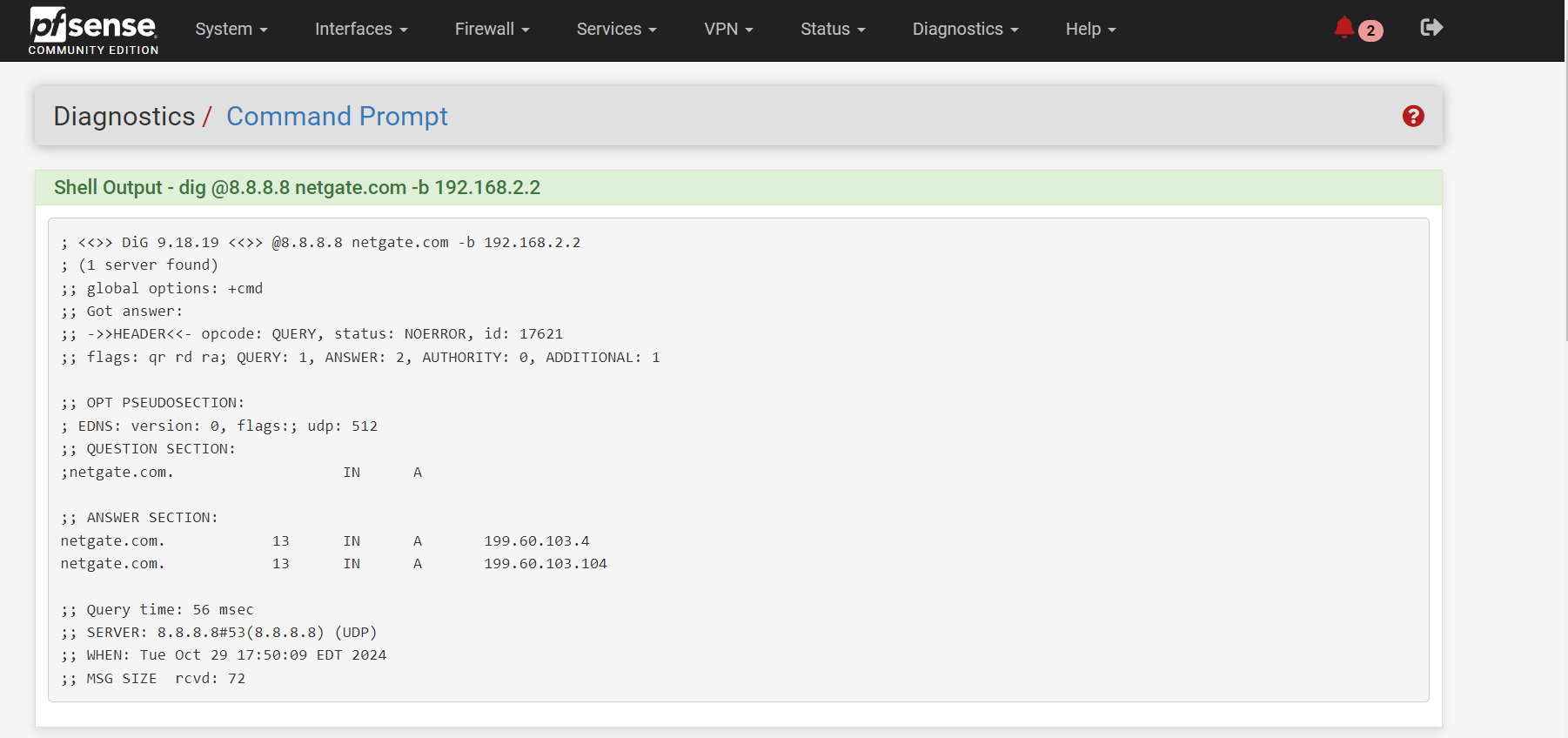
-
Hmm, well that looks OK. Try setting Unbound (DNS Resolver) to forwarding mode so it uses the configured remote DNS server directly. You should also disable DNSSec whilst testing that.