Feedback request on home network design
-
I used to run a small Fortigate at home to provide services like firewall, routing, DNS and DHCP as well as inter vlan routing and qos.
A while ago, I wanted to move the equipment into another room upstairs, but the firewall didn't want to boot anymore after running for over a year. There was some issue with the internal storage, even trying to install a new image via tftp ended up in read errors etc.). So I had to quickly change the ISP router back from modem to router mode and it forces 192.168.0.0/24 as LAN.
So I had to renumber all devices at home as well and we have been running in the same network since.On the switch, one port goes directly into my sons (Ilya) room and I do not really care what he is running there. But occasionally he puts the entire network on hold or stuff like this. Out of self defence I enabled dhcp snooping on the port and during my working hours I limit it to 100MBit.
A new firewall needs to be put into the network...
I have a retired Cisco ASA 5512-X and planned out all the network in EVE-NG with full configuration. While doing this, I found some blockers and limitations, for example IDS and IPS is behind a paywall, no DNS service and QoS only policing without queues.
So I looked at pfSense and again planned out the network in EVE-NG, this works great and fills all the gaps. I have not delved too much into the QoS implementation yet.
Here is my current plan:
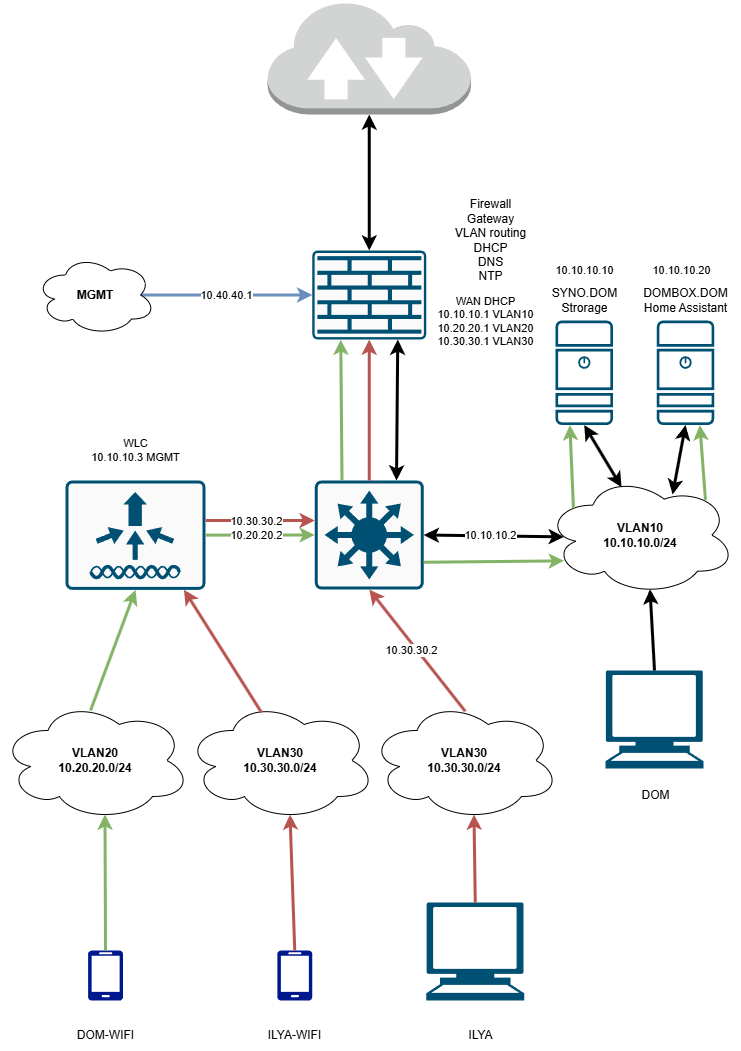
DOM is our normal house network and VLAN30 is the port going into the room of doom. Maybe I call it DOM and DOOM networks... ?
VLAN10 and VLAN20 are trusted and VLAN30 is not. I will create another WLAN for VLAN30 on the WLC (Mobility Express) for the house.Current controls:
I only allow TCP/UDP/ICMP traffic out the WAN port for everyone.
I force DNS queries to use the internal DNS (at least for 53 and 853) for everyone.
I force NTP queries to use the internal DNS (at least for 53 and 853) for everyone.
I block TOR exit nodes for everyone.
I only allow traffic between (VLAN10 <> VLAN20) > WAN, while VLAN30 is only allowed (VLAN30 <> VLAN30) > WAN.Questions:
- I read that if I enable QoS for VLAN30, it is also applied on the WAN interface for all traffic? I used the wizard and it created something in EVE-NG. Maybe if someone knows some standard settings to promote VOIP and demote P2P/Gaming?
- Is there a way to control or monitor Proxy and SSLVPN traffic without running a proxy myself on the firewall for all traffic for deep inspection? He is gaming and would complain about latencies... will this dramatically slow down the WAN access?
- What else should I do?
p.s. updated diagram
-
@disi1 said in Feedback request on home network design:
if I enable QoS for VLAN30, it is also applied on the WAN interface for all traffic?
Shaping on WAN out is after the NAT happens, so either you have to make a pass rule on VLAN30 with your queue/limiter, or you have to jump through a couple hoops to "tag" packets from ILYA in order for pfSense to know which they are as they go out WAN.
https://docs.netgate.com/pfsense/en/latest/trafficshaper/advanced.html#shaper-rule-matching-tips"To match by a private address source outbound in WAN floating rules, first tag the traffic as it passes in on a local interface. For example, match inbound on LAN and use the advanced Tag field to set a value, and then use the Tagged field on the WAN-side floating rule to match the same connection as it exits the firewall. Alternately, queue the traffic as it enters the LAN with a pass rule instead of when it exits a WAN."
re: inspecting encrypted traffic, the PC would need to trust a cert on the proxy which decrypts the traffic. So, could be an issue for phones or other devices. I know the Bitdefender GravityZone we use for clients can do that on the PC by adding its own cert to Windows and then it intercepts traffic on the PC.
-
@SteveITS said in Feedback request on home network design:
@disi1 said in Feedback request on home network design:
if I enable QoS for VLAN30, it is also applied on the WAN interface for all traffic?
re: inspecting encrypted traffic, the PC would need to trust a cert on the proxy which decrypts the traffic. So, could be an issue for phones or other devices. I know the Bitdefender GravityZone we use for clients can do that on the PC by adding its own cert to Windows and then it intercepts traffic on the PC.
I did register a domain and issued a valid certificate (Let's encrypt) to all internal services, including the firewall (wildcard which I know I have to manually renew every three months). To be clean and potentially use the Squid proxy*.
Before I changed our network over, I did experiment with squid on the exact hardware, using the old setup as the uplink and it produced a lot of overhead on the firewall.
The good news:
Since I use pfSense for all networking and isolated the VLAN30, there were no issues. Before I had extreme lags when I used ZScaler and Pulse VPN for work. It seems the network runs overall smoother. This is without any Traffic Shaping or QoS,Only today I switched the ISP router to Modem Mode.
p.s. if anyone else wants to split WLAN into VLAN using Mobility Express, it took me some time to figure this out (where 10.10.10.3 is the wlc management interface, but the management vlan needs to stay 0 or the APs cannot join).
switch port access vlan 10 -> IP for the AP
switchport trunk allowed vlan 10,20,30 -> for the wlc interface and the WLANs
switchport trunk native vlan 10 -> needs to be the same as the APs vlan (10)interface GigabitEthernet1/0/16 description VLAN20_POE switchport access vlan 10 switchport trunk allowed vlan 10,20,30 switchport trunk native vlan 10 switchport mode trunk power inline port poe-haDon't forget the ip helper to point to the DHCP for each vlan on the switch.
- For Squid transparent proxy you do need a CA, not only a valid certificate. I thought process was wrong. But it doesn't hurt to have a valid certificates in the network.