Consistent ~monthly DNS_PROBE_FINISHED_NXDOMAIN error
-
About every few weeks or so, I'll have a bout of internet issues including intermittent connevtivity, and websites giving the 'DNS_PROBE_FINISHED_NXDOMAIN' domain error. This will last for an hour or so.
At the same time, I'll cycle through a dozen or more IP addresses from my service provider. Each one only lasting a few minutes or so. Things eventually stabilize and I won't see this behavior (or not aware) for another month or so.
What is going on with this... ISP issue or something misconfigured in my pfsense?
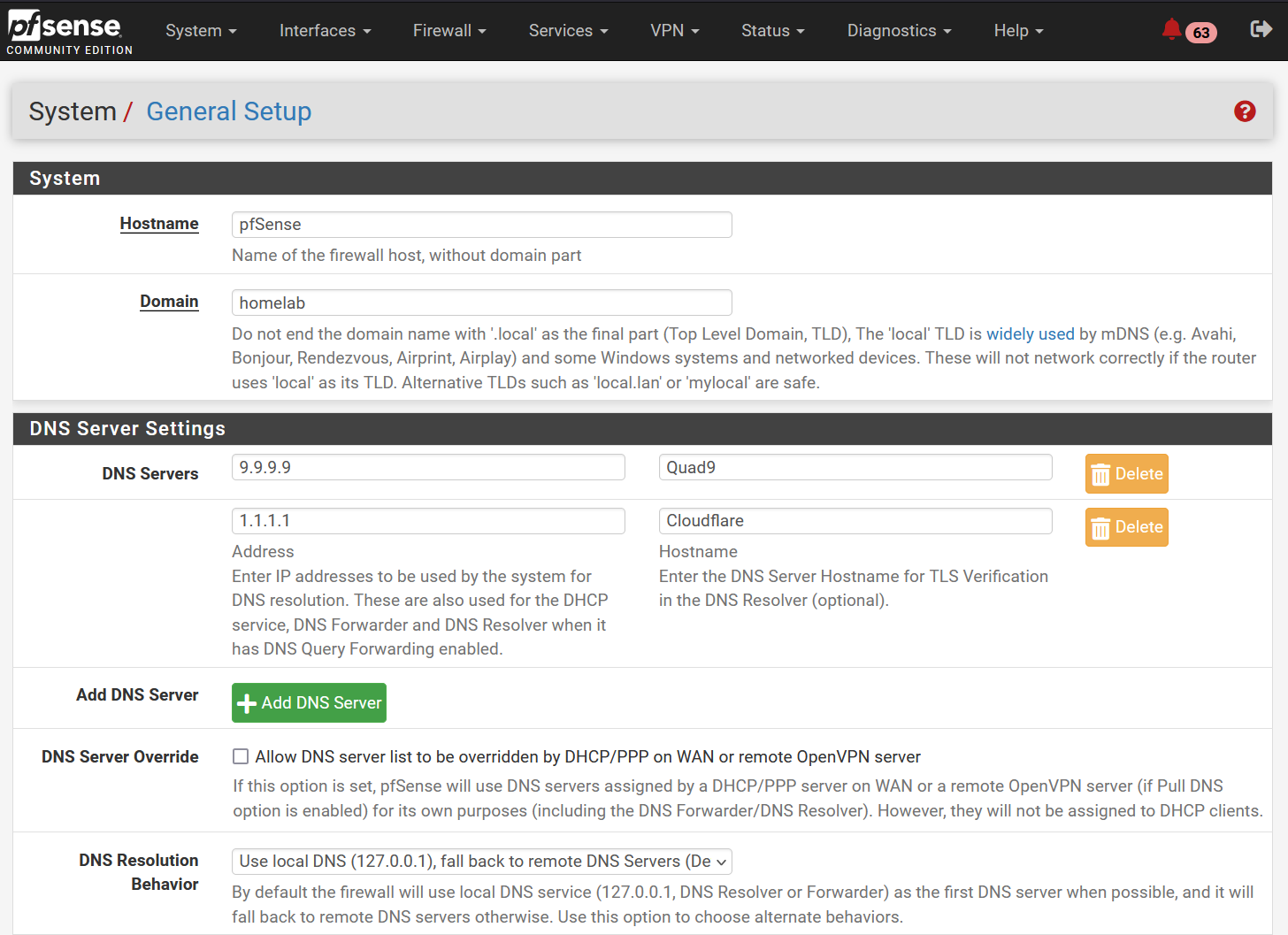
DNS Server settings:
DNS Resolver settings:
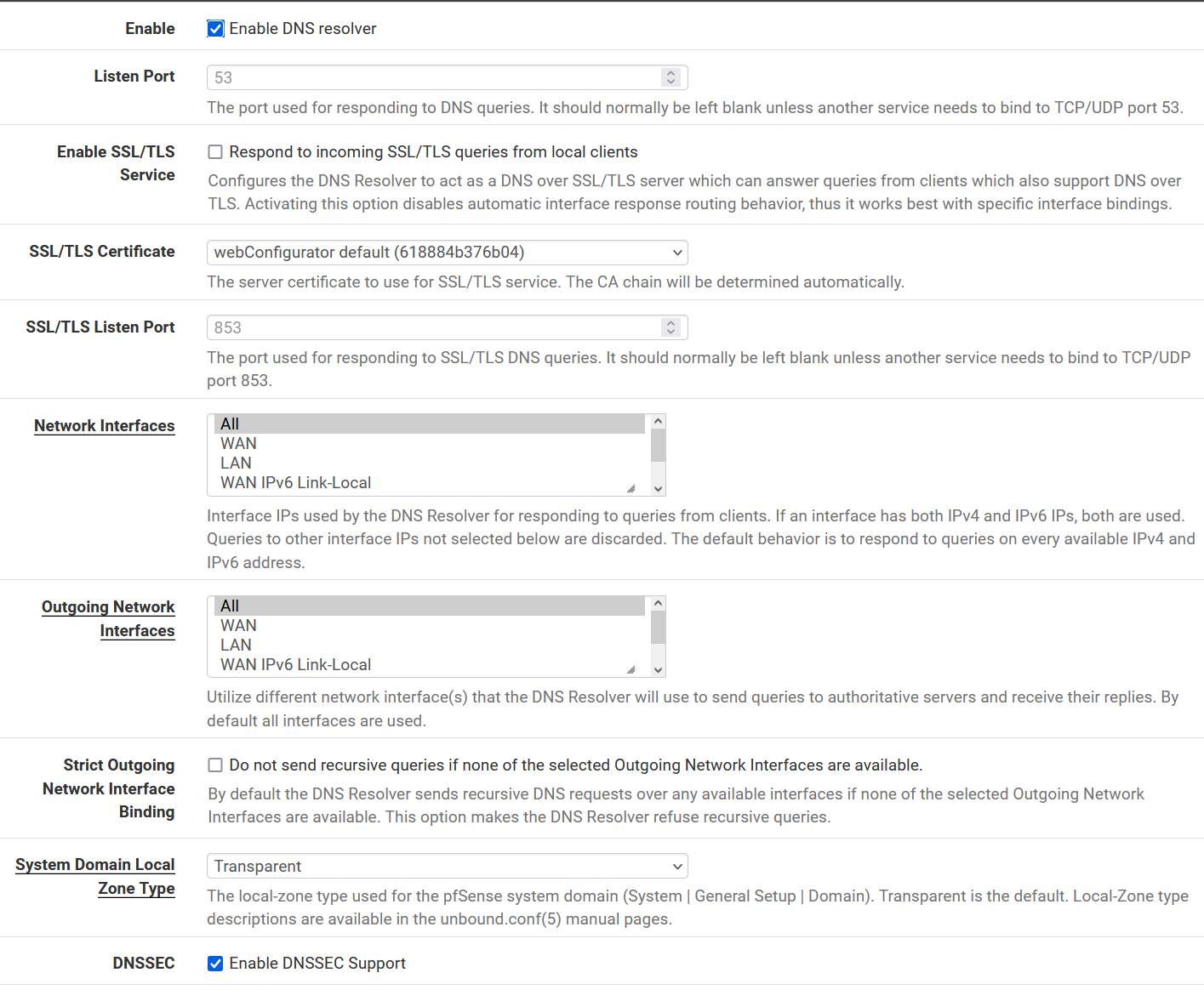
No host overrides, no domain overrides.
-
@liquidity well things that jump out at me - 1st one is the 63 notifications.. I would highly suggest you look into those, and clear/fix whatever they are showing.
2nd.. You have dns servers listed, so your forwarding? Pretty pointless so setup dns in pfsense if your not forwarding.. If your forwarding you have dnssec enabled. Forwarding and dnssec is nothing but problematic and provides nothing but wasted dns queries.
-
Those looked to be some certificate error, but last error was months ago so I cleared them.
I do not have DNS Forwarding enabled, I wanted to provide manual DNS servers and thought that was the place to do it. I now know that that's only active if DNS Forwarding is enabled.
So assuming this is a DNS Resolver issue, is it ISP side then?
-
@liquidity no they are active for pfsense, if the resolver stops.. But only pfsense, no clients would ever use those unless you setup forwarding in unbound.
But if your resolver (unbound) is not working and clients can not get dns, its of little use if pfsense can use dns to check for updates.. Which is pretty much all it ever uses dns for.
-
So in context of my error, this is an ISP issue? Still a bit confused on how to resolve this or why it keeps happening.
-
@liquidity if your resolving and you can not resolve something external, I take it your local resources still resolve, like a client can resolve pfsense fqdn?
I would do a dig +trace on pfsense itself, to see where the dns is failing in the path.
-
@johnpoz Stilll learning about some of this, and need some hand holding here (sorry!)
Could you walk me through both the items you mentioned? Client resolving pfsense fqdn and dig+trace on pfsense itself
-
@liquidity so take it pfsense is being used as your dns for a client..
so just do say a ping to pfsense fqdn, mine is sg4860.home.arpa
See how it resolves to pfsense IP 192.168.9.253
$ ping sg4860.home.arpa Pinging sg4860.home.arpa [192.168.9.253] with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64does that work for say www.google.com? if so then there is noting wrong with unbound resolving? Can you ping the ip of whatever fqdn your browser is complaining about.. For all we know your browser is using doh, without even asking you if it should/could - they like to do that of late.
if your ping test to www.google.com does not come back with an IP, then yeah dns failed for some reason - go on pfsense via console or ssh and do a dig fqdn +trace
example
[24.03-RELEASE][admin@sg4860.home.arpa]/root: dig forum.netgate.com +trace ; <<>> DiG 9.18.20 <<>> forum.netgate.com +trace ;; global options: +cmd . 78700 IN NS l.root-servers.net. . 78700 IN NS j.root-servers.net. . 78700 IN NS f.root-servers.net. . 78700 IN NS h.root-servers.net. . 78700 IN NS d.root-servers.net. . 78700 IN NS b.root-servers.net. . 78700 IN NS k.root-servers.net. . 78700 IN NS i.root-servers.net. . 78700 IN NS m.root-servers.net. . 78700 IN NS e.root-servers.net. . 78700 IN NS g.root-servers.net. . 78700 IN NS c.root-servers.net. . 78700 IN NS a.root-servers.net. . 78700 IN RRSIG NS 8 0 518400 20241113050000 20241031040000 61050 . fYDbt3f4fnJ+NYpXj7e4NknpuMSoZl4H/OwQ5am4UdyvtpW8xIFMwMgW ZLps0HOzJ8Ia6pz3Y6cGOVSw455vKosRIGzeuBaek7mRdkVP2fDHUWQp 5VJ6v6oOGY5r3/rJc0qexe93wR1Lcb8RL3ksG1FudNUStJTdwNpsG7Pz qQ8t7xxNnVxoY9tb5oDtb7Rn9M7NFYf0pwj8h8TwhXeIpoIOiLuysYAD KGP7258lZ67w1VtwC6OkNht0cJ+3zhGhzR5Kdj6kj0Ke4MRonodv+Y33 6BWOMwB9jibUrIL4MXgYhfWpXKsNtpE1CMhg4rV5aw1kVi+TdFmsef7m bkH4rQ== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 19718 13 2 8ACBB0CD28F41250A80A491389424D341522D946B0DA0C0291F2D3D7 71D7805A com. 86400 IN RRSIG DS 8 1 86400 20241113170000 20241031160000 61050 . mRj9l6Xf3a0fx1R0RnAfMzy4ymu95VpVcLvMfbA006on5PzkIJKRVC4w qDScV8eIDF1SdhuARDTKLPk7e+kgWYa76xtUkiDEUaXYC/F3qHTKO9rU yo+zGRQSE7NCloBO76VCgtDhBS1gz0L3M2oYVxShOO947odr9uZBqfW0 PaW9pmQHAGrp1/HWvHDOZwDhOI5tjXgjz4ISIWMKpDCcj6DStSr4WQ85 9i2PjFd3RmIcCx3KqtnJO7CGBcBSD07aqR3/HLoFPIu24WuIUekJwZfG s10AxohnbwGVugPWdhvQmRckA+RQUl/3Q8kMv4x5XCZ4e7F3KpFrt0L4 9uybzQ== ;; Received 1180 bytes from 2001:dc3::35#53(m.root-servers.net) in 58 ms netgate.com. 172800 IN NS ns1.netgate.com. netgate.com. 172800 IN NS ns2.netgate.com. netgate.com. 172800 IN NS ns3.netgate.com. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 900 IN NSEC3 1 1 0 - CK0Q3UDG8CEKKAE7RUKPGCT1DVSSH8LL NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 900 IN RRSIG NSEC3 13 2 900 20241104002556 20241027231556 29942 com. 91X1yPcVakmmDBB4610js+PlS6tsWXkckWFbTVELLHTxMPp59zhHBr4l tmpQNcq+1jif9HVX3wzuMqzt562zlw== 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 900 IN NSEC3 1 1 0 - 2U54JL908MKCE6VDBRTOBQM3A838AA3F NS DS RRSIG 2U53SUOKS8OJJV178M90A8BMNI9USDVJ.com. 900 IN RRSIG NSEC3 13 2 900 20241105001627 20241028230627 29942 com. zRD7EMzYCFXLTHZWndVPumbBCIUgEj0be9sO7TyvDfqv7xbP0dv6Kh91 4GmdyBNMLHG6/zZURPkF8WWEExk8+g== ;; Received 589 bytes from 2001:503:d2d::30#53(k.gtld-servers.net) in 15 ms forum.netgate.com. 60 IN A 208.123.73.77 netgate.com. 3600 IN NS ns3.netgate.com. netgate.com. 3600 IN NS ns1.netgate.com. netgate.com. 3600 IN NS ns2.netgate.com. ;; Received 276 bytes from 34.197.184.5#53(ns3.netgate.com) in 36 ms [24.03-RELEASE][admin@sg4860.home.arpa]/root:This will show you how something is resolved, and where it is failing - if it is.
or you can do from gui
