DNS Problems since Telekom fiber channel
-
Now I have some configs from pfSense side:
The Dashboard shows, that WAN Connection is up with its IP 91.38....
there are also some WAN incomings tcp/udp...
The update info works
And the shown DNS Servers are from the Telekoms DHCP:
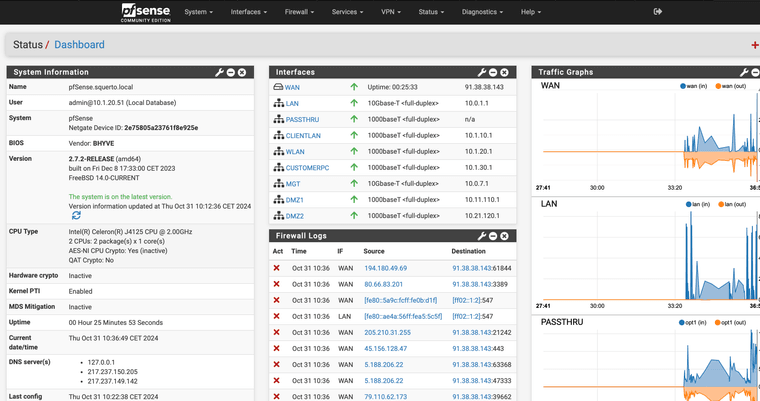
But if I try to perform the update it fails due to "wrong destination"
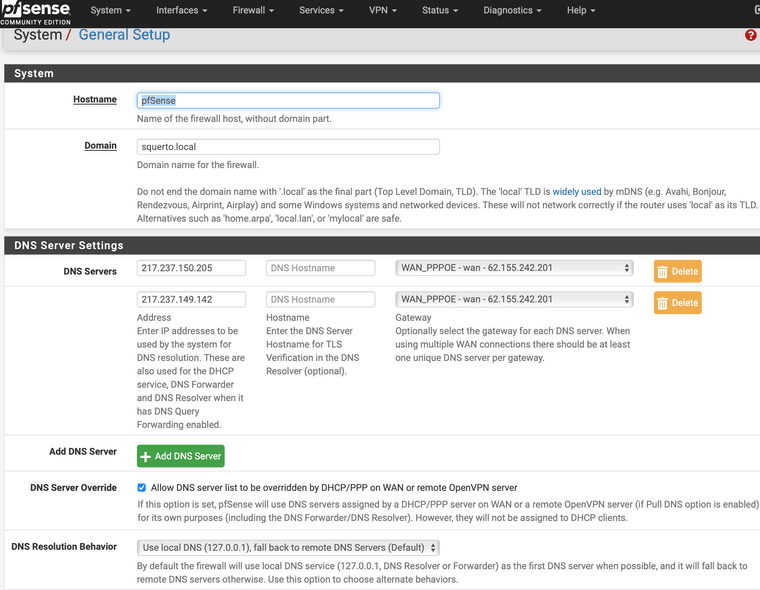
In the General Setup I inserted also the Telekom DNS Servers.
It is allowed to overwrite the DNS servers by DHCP/PPP on WAN:
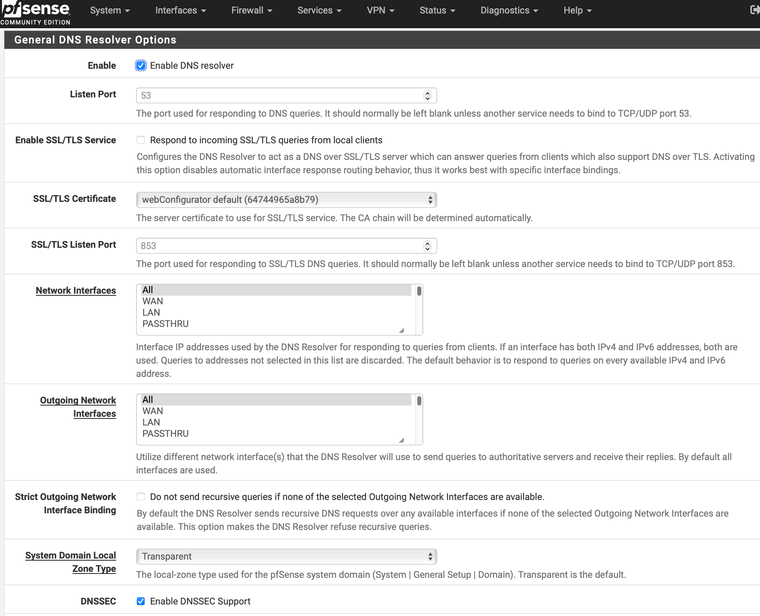
DNS Resolver on the pfSense is enabled:
nslookup google.de works with the answer: 142.250.186.35
ping 142.250.186.35 fails againany help will be appreciated..
THX
-
@tp147 said in DNS Problems since Telekom fiber channel:
there are also some WAN incomings tcp/udp...
I saw the firewall logs on your dashboard.
You can continue showing them for a couple of hours, and then you uncheck this :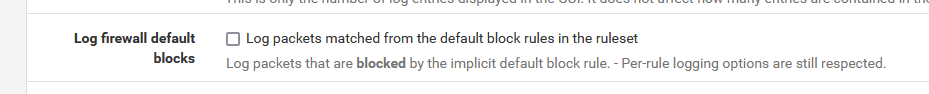
from now on, everything that hits the WAN port (== source : the entire Internet) will go silent.
You WAN IP always had these incoming traffic, it is just there to try if any access is possible. It's the so called Internet back ground noise.@tp147 said in DNS Problems since Telekom fiber channel:
The update info works
So your internet connection is fine.
These :
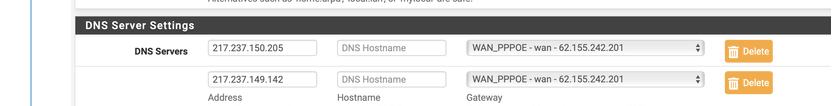
you can most probably remove them all.
pfSense has a resolver, and doesn't need any other DNS. The DNS from your ISP exist because back in the good old days (before 2000) an internet connection was metered, slow, and a close by DNS was a real advantage. These reasons are all gone now. pfSense taps in the original one and only DNS system of the internet, the way it was meant to be used.
Bonus : when resolving (default setup) it will make use of DNSSEC. -
Thanks for reply :)
@Gertjan said in DNS Problems since Telekom fiber channel:So your internet connection is fine.
not at all from my point of view!
removing all DNS Server from the general Setup does not work.
now I entered the DNS Servers from openDNS in the general setup and can ping and nslookup them (208.67.222.222 is resolver1.opendns.com)
with DNS Resolver enabled the pfSense answers, otherwise the external DNS Server answers.
But only the Servers are listed in the general setup
If the Telekom Servers are removed I cannot ping them!?that's all weird to me! Why is it not possible to ping a simple address like 8.8.8.8
-
Playing around I've found this:
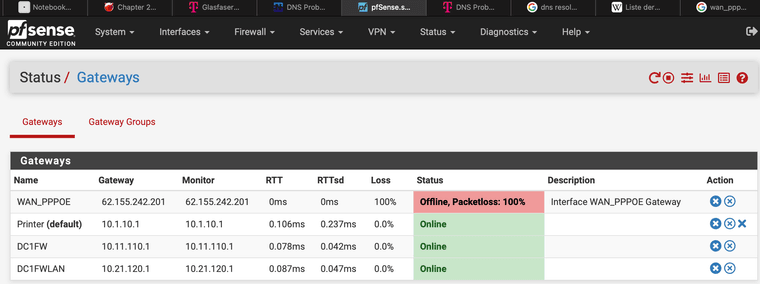
May be this is a good hint to solve my Problem...
How to bring the Gateway up?
-
In this Moment 1 step forward:
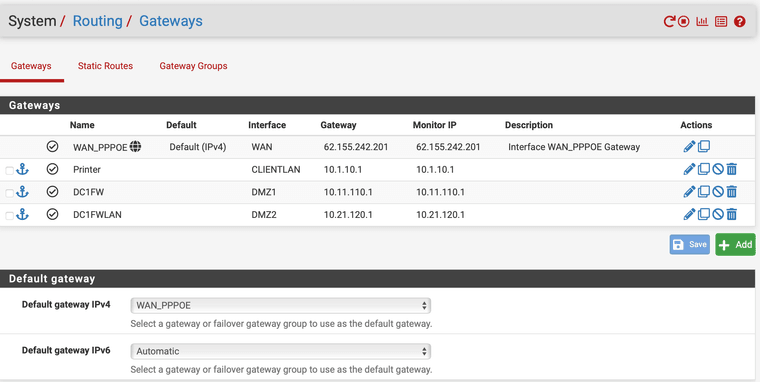
The Default Gateway IPv4 was the Solution.
This Post is written through the Firewall
Any suggestions due to the Offline GateWay???
TIA & Regards
Thorsten
-
@tp147 for starters those other gateways make zero sense.. A gateway is something pfsense can use to get to other networks.. Is your printer a gateway to other networks??
You should not be setting gateways on interfaces that can not be used to get to other networks.. Or pfsense thinks they are WAN interfaces.
-
@johnpoz said in DNS Problems since Telekom fiber channel:
@tp147 for starters those other gateways make zero sense.. A gateway is something pfsense can use to get to other networks.. Is your printer a gateway to other networks??
You should not be setting gateways on interfaces that can not be used to get to other networks.. Or pfsense thinks they are WAN interfaces.
Hm, I've never created these Gateways.
They appeared after creating 2 static routes, e.g. the printer of the clientLAN should also be used from other LANs
The other Route is for connecting WLAN Devices to the Media Server in DMZ2 of DC1 for streaming music from my own repository to streaming clientsregards
Thorsten
-
@tp147 why would you be creating static routes? You do not need any routes for networks pfsense is directly attached too.
Lets say I have 2 networks, lan and say dmz..
lan 192.168.10.0/24
dmz 192.168.20.0/24if a device on the lan, wants to talk to any IP on the 192.168.20 pfsense knows how to get to it already, there is no reason for a static route.
You would need a route to get to some other network that pfsense is not attached too, this route tells pfsense which gateway to talk to get to that remote network.
Normally this is just your default, ie your wan gateway - which is used to get to say the internet. The only time you would have need of other routes, is if you had another router.. For example lets say I wanted to get to 192.168.30.0/24, and pfsense should use say 192.168.20.42 on dmz network to get there. Where this .42 was another router on my network, that had the 192.168.30 network hanging off of it.
-
@johnpoz said in DNS Problems since Telekom fiber channel:
@tp147 why would you be creating static routes? You do not need any routes for networks pfsense is directly attached too.
Lets say I have 2 networks, lan and say dmz..
lan 192.168.10.0/24
dmz 192.168.20.0/24if a device on the lan, wants to talk to any IP on the 192.168.20 pfsense knows how to get to it already, there is no reason for a static route.
You would need a route to get to some other network that pfsense is not attached too, this route tells pfsense which gateway to talk to get to that remote network.
Normally this is just your default, ie your wan gateway - which is used to get to say the internet. The only time you would have need of other routes, is if you had another router.. For example lets say I wanted to get to 192.168.30.0/24, and pfsense should use say 192.168.20.42 on dmz network to get there. Where this .42 was another router on my network, that had the 192.168.30 network hanging off of it.
Hm, thanks so far, but:
beside the standard VLAN1 from my Cisco switch all other VLANs are provided by the Firewalls.
Without routing I can only reach the broadcasts .254 on the switch and the gateways .1 on the Firewall.
The WLAN client (iPhone) from the 10.1.20 Network (VLAN20) has to talk to the upnp Client in the 10.1.40 (VLAN40) Network.
My only solution was to implement static routes... -
@tp147 said in DNS Problems since Telekom fiber channel:
provided by the Firewalls.
so you have more routers in your network other than pfsense - this gateway you call printer, is actually a firewall/router?
So these networks 10.1.10, 10.11.110, 10.21.120 are transit/connector networks - Ie no hosts on them?
-
@johnpoz
Yes, there is a perimeter Firewall behind FC modem. At the LAN Interface are the clients, WLAN, upnp ...
Further there are two Datacenter Firewalls for DC1 and DC2 for HA.The ClientLAN 10.1.10 there are some Clients
everything is virtualisesed (bhyve, BSD UNIX) on 3 little quad-core celerons and a old QNAP
I don't need this really, it is only for playing around and understanding virtualization, ZFS, SDN networking, routing, network security and also standard systems as apache Webserver, tomcat, SQL Database, LDAP, on premise cloud ... everything HA clustered and all the other crazy things...
... so I have some more servers (4 native, 20 virtual) as I have clients (3)cheers
Thorsten