Open Ports (53, 80, 123, 443)
-
@Bob-Dig Probably?

What's a likely cause? I'm not familiar with Pfsense.
-
@Skiny did you add rules to your wan, out of the box no unsolicited inbound is allow.. To allow any traffic you would have to create rules to allow.
Your actually scanning from outside, not just your WAN ip from the lan side? Ie using something like grc?
123 is the odd one to be honest because ntp doesn't use tcp at all.. So where you scanning from using udp? Many of the external services don't do udp.
-
Did you try to scan your external IP via the LAN side? If so, what the firewall is doing is simply redirecting the scan to LAN facing side.
Use Steve Gibson’s Sheilds Up!
https://www.grc.com/x/ne.dll?bh0bkyd2
-
My ISP sent a message regarding an NTP Mode 6 vulnerability.
I checked the IP on Shodan and it showed those ports as being open.
Just tried https://www.grc.com/x/ne.dll?bh0bkyd2 and it shows:
Port Scan Results (Ports 0-1055)
Total Ports Tested: 1056
Open Ports: 0
Closed Ports: 2 (Ports: 135, 445)
Stealth Ports: 1054Summary:
NO OPEN PORTS were detected.
CLOSED PORTS identified: 135, 445
All other ports are in STEALTH mode.
TruStealth Status:FAILED: Not all tested ports are in STEALTH mode.
NO unsolicited packets were received.
NO Ping reply (ICMP Echo) was received.I have OpenVPN setup and blocked a few IPs being accessed from my network and that's about it from what I can see remember.
I set everything up about a year ago to start to use Pfsense but haven't touched it since due to lack of time.
-
Do you have a static IP? Could just be an old report.
Those closed ports are probably blocked by the ISP so nothing you can do about that.
-
@Skiny said in Open Ports (53, 80, 123, 443):
Closed Ports: 2 (Ports: 135, 445)
Noop.
A default pfSense will show :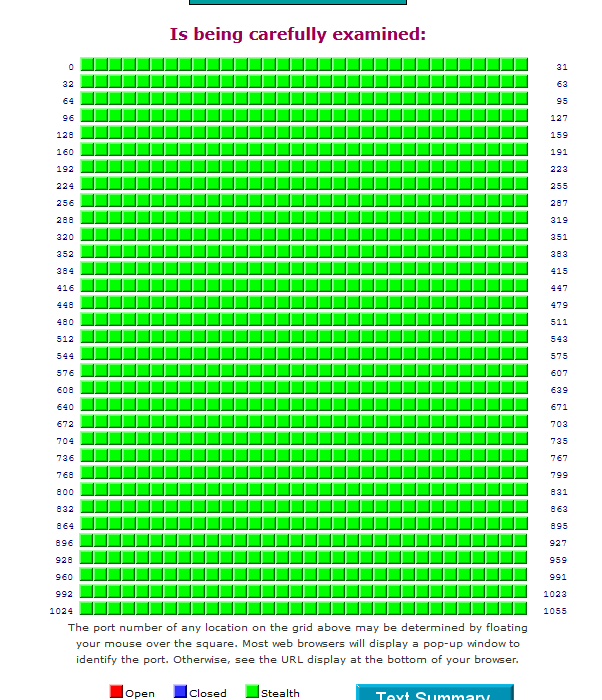
But lets talks about the device you have in front of your pfSense WAN.
What is it ? -
@stephenw10 said in Open Ports (53, 80, 123, 443):
Do you have a static IP? Could just be an old report.
Those closed ports are probably blocked by the ISP so nothing you can do about that.
Not a static IP, no.
@Gertjan said in Open Ports (53, 80, 123, 443):
@Skiny said in Open Ports (53, 80, 123, 443):
Closed Ports: 2 (Ports: 135, 445)
Noop.
A default pfSense will show :
But lets talks about the device you have in front of your pfSense WAN.
What is it ?Mine was the same, except for 2 in blue / closed.
In front of it there's just the cable modem.
-
Those ports are commonly blocked by the provider. No-one should ever allow incoming connections on them!
-
Closed Ports: 2 (Ports: 135, 445)
Pfsense sure isn't going to do anything on those ports, at least not what they are normally used for.. So yeah those are prob blocked by something in front of pfsense. But you would think they should show just that stupid term stealth vs closed.
But yeah the isp will block some ports even in a modem - there was recently a port about that, you can sometime view what ports are blocked via a snmp query.
-
@Skiny said in Open Ports (53, 80, 123, 443):
NTP Mode 6 vulnerability.
Thanks for all the replies.
Why would Shodan show those 4 ports as being open? And my ISP warning of an NTP Mode 6 vulnerability (which I assume was related to port 123)?
-
As I said above if you don't have a static IP it's probably just an old report.
-
@stephenw10 said in Open Ports (53, 80, 123, 443):
have a static IP it's probably just an o
My ISP keeps sending the warnings regarding NTP though, so must be an on-going issue?
-
@Skiny what are the rules on your wan? Do you have any rules in floating.. Again out of the box there is no unsolicited inbound traffic allowed.. Yes pfsense can run ntp, and yes it can listen on wan.. But if you did not create a rule to allow it.. Then it would not be open to the internet.
I just tried simple ntpdate to all the ips you have used to talk to the forum with, and don't get any answer..
-
Other than the 2 default rules, I have one for OpenVPN, using the standard port. Otherwise there's nothing bar 2 old disabled rules.
Nothing in floating.
My current IP ends .128
Normally I wouldn't suspect anything, except for regular ISP warnings, and then what I saw on Shodan.
-
@Skiny yeah I test one that ends in .128, no response to sending ntp query on port 123 udp
Even sniff while doing so to see if maybe sending something back that wasn't viable to sync ntp with.. no responses at all
-
@johnpoz said in Open Ports (53, 80, 123, 443):
something back that wasn't
It's very strange, I can't think of any explanation for it.
-
Is it a static IP address? Do you have more than one IP?
-
@Skiny as can see from ips you have talked to forum with there have been changes..
Also mode 6 issues was many years ago.. even back then the default ntp config in pfsense mitigated them - while depending on the scanner might not account for that in how it tested. So even if your ntp server was open at some point..
These isp mess up all the time, and sometimes right hand doesn't know what the left is doing. So the guy that had the IP before might have had an open ntp server?
What I can tell you is currently none of the ips you have used to talk to forums with answer ntp at all..
Here is another thing you can do, as a sanity check - is your ntp server listening on your wan even?
Go into ntp and select only the interface(s) you want it to listen on - notice mine isn't set to listen on wan.
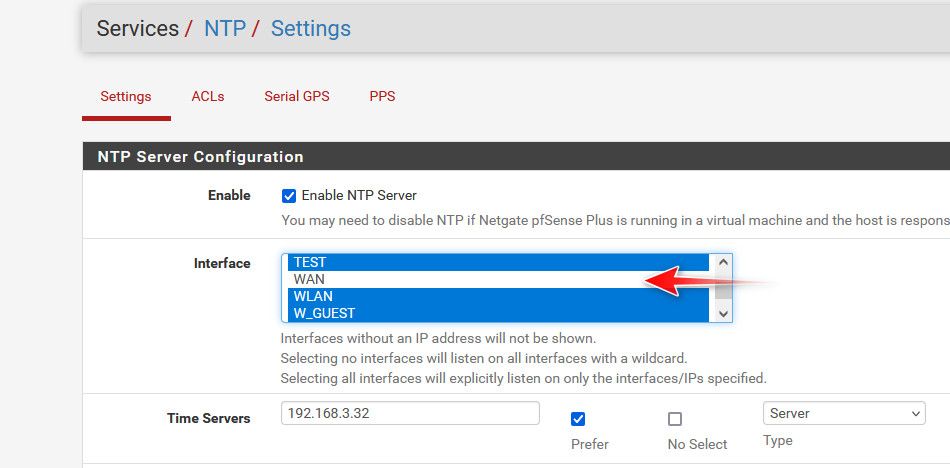
Here I limited this to only ipv4, because didn't want to have to hide my gua IPv6 address, but it doesn't listen on the wan interface Ipv6 either.. And you can see ntp isn't even listening on my public wan IP
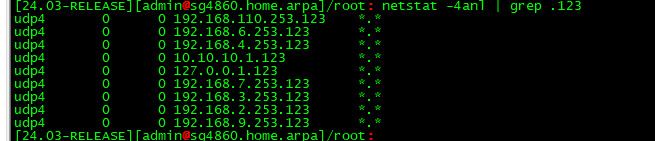
I mean you could contact your isp about it - saying hey look I am not running ntp all, let alone open to mode 6.. Why do you keep sending me this email.. But that would most likely be an exercise in futility..
-
@johnpoz said in Open Ports (53, 80, 123, 443):
So the guy that had the IP before might have had an open ntp server?
Yup that would be my bet.
@johnpoz said in Open Ports (53, 80, 123, 443):
..that would most likely be an exercise in futility..
As, unfortunately, would that!

-
@Skiny said in Open Ports (53, 80, 123, 443):
In front of it there's just the cable modem.
So you're good for a test.
Remove pfSense.
Connect a PC to the modem, and set up the connection.
Do the same test again.Surprise ......