Two Plex servers on two different ip addresses
-
Hello,
How would I go about running two Plex servers on different ip addresses, because when I port forward to 32400 on different addresses one Plex server seems to go offline, do I need to use a different public port?, is there a conflict when using 32400 on two different ip addresses? Hence why one goes offline?
Any help would be appreciated
Thanks -
@jhmc93 Yes, the two Plex servers would need to be configured for different public ports, and you would need a Port Forward for each.
-
@jhmc93 Server A uses 32400 inside and out.
Server B uses 32401 outside and 32400 inside. You set the alternate port in Plex. The port forward rule sees 32401 on the outside and sends 32400 to Server B on the inside.None of mine use 32400 on the outside.
Edit: fixed the typo, thanks johnpoz for highlighting my typing.

-
@AndyRH very close, maybe a typo.. But you can not change the port plex uses, it always uses 32400.. But the rest of your comment is spot on.. You can use different external ports in your forwards. So 32000 forwards to 192.168.1.x:32400, port 32001 forwards to 192.168.1.y:32400
-
@AndyRH can someone show me how to do that, I have an I isp router that provides the internet. So pfsense is connected to that, how would I go about it
-
@jhmc93 so pfsense has a private IP on its wan..
Put it in dmz mode on your isp router, where all ports get forwarded to pfsense. Then do your port forwards on pfsense. Or forward both 32000 and 32001 to pfsense wan IP on your isp router.
Then your forwards on pfsense..
-
In pfSense, set up port forwarding for two ports of your choosing, such as 32401 for server A, and 32402 for server B.
Then, in Plex, go into Settings -> Remote Access for each of the servers, and check the box that says "Manually specify public port" and input the ports you have chosen.
-
@dennypage thanks - I forgot to mention the plex part ;)
example - here is mine where it uses a different port on the outside vs the 32400 it listens on.
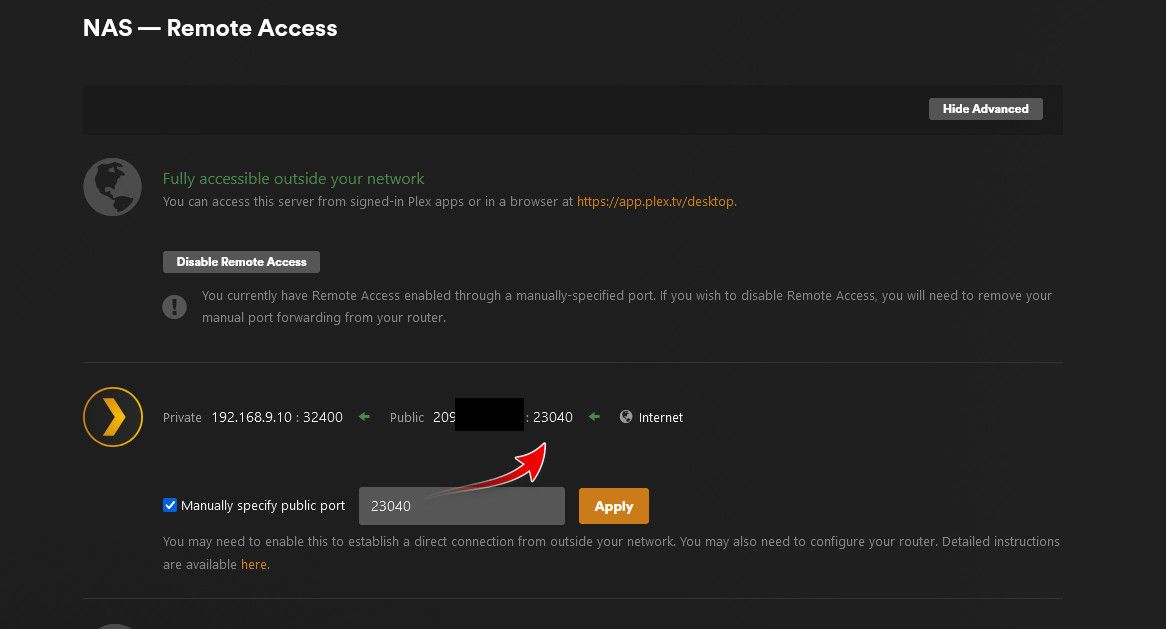
Here is my port forward
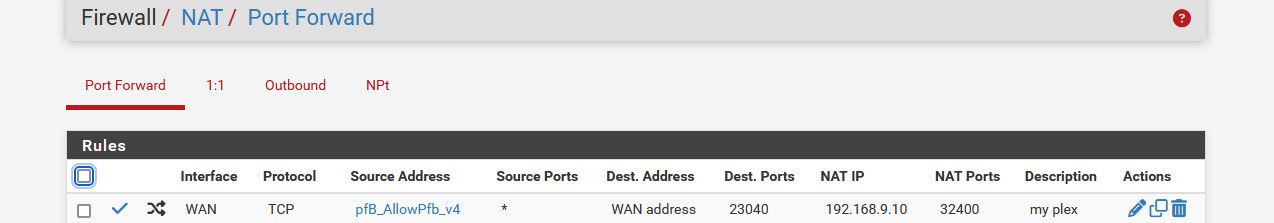
-
@johnpoz is your source address your plex ip?
-
@jhmc93 my source IP is a pfblocker alias that contains geoip for US, and currently Belgium (some family living there currently) and some lists of IPs that plex uses to validate plex is available remote, and some other monitors I have.. But I have no need for anyone else to be able to talk to my plex ports, which is why I use an alias that limits the IP that can talk to it.
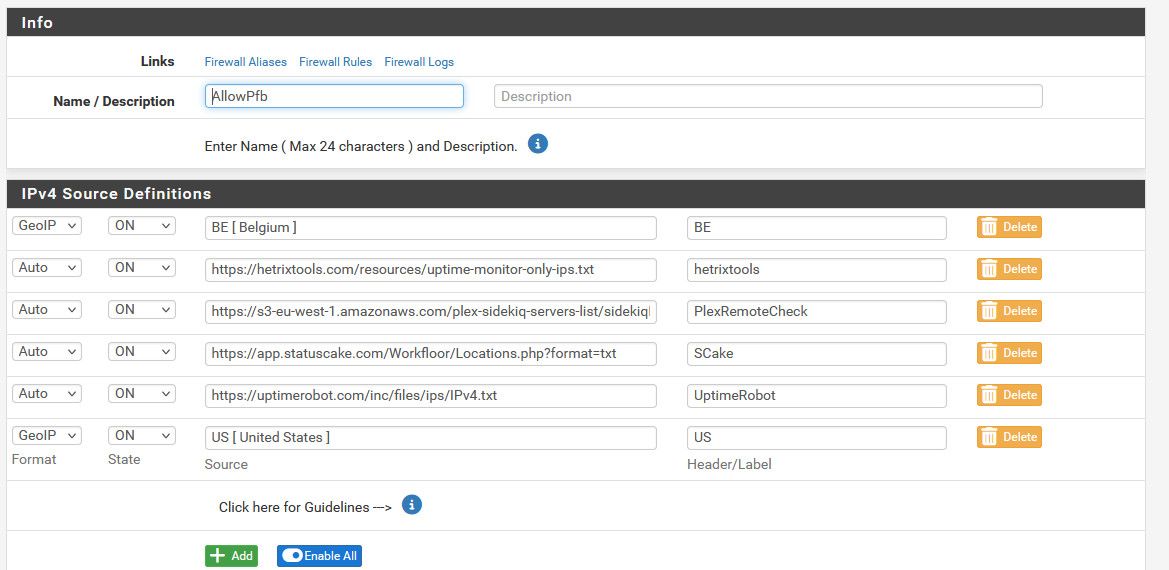
I currently have 3 different services (all free) monitoring if my plex is available remote because well they are free ;) and I like to get notified if my plex is offline.. I normally know its offline within 5 minutes of it going down, well before my users start bugging me if plex is down ;) I could prob drop that to just 1 service, but again they are free and why not.. I didn't start with 3, but it has grown to that because I like to see the differences in the different services, etc. Doesn't hurt to have more than one - and even if one fails to notify me, one of the other 2 for sure will ;)
-
@johnpoz I do something very similar, but use an explicit firewall rule rather than the nat rule for source enforcement.
Port forward:
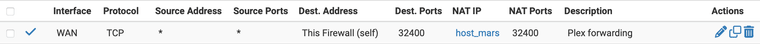
Firewall:
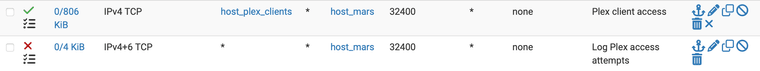
-
@dennypage oh putting it on the port forward auto puts it on the firewall rule as well
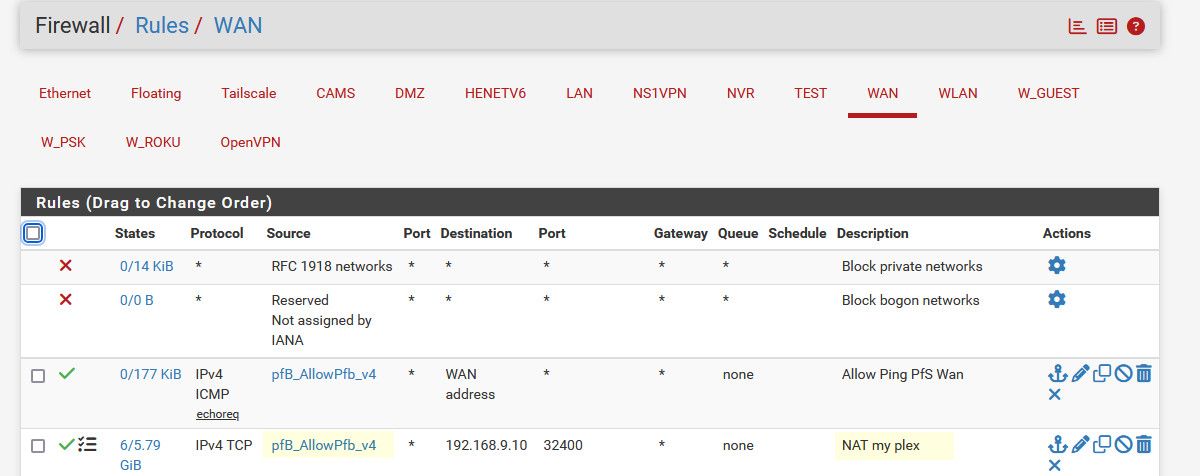
Seems kind of odd that you would be using the this firewall alias and not just the wan address. That contains all IPs of pfsense.. Wouldn't your traffic only be coming in on your wan IP..
-
@johnpoz Yes, the addition of an automatic firewall rule is an optional in port forwarding. It's just my preference to keep them separate. I have a bunch of separators with descriptions in my firewall lists, and when things get moved around automatically it causes me discomfort.

As to using Self rather than WAN address, you have a point. It used to be required due to the fancy redirection I used to do, but probably isn't necessary anymore. I'll have to test it.
-
@johnpoz is that easy to setup?, I have a VPN running on my pfsense network but only my two plex servers are exposed to the internet where as my other machines are running through vpn, I'm trying to be as secure as possible as I don't want someone hacking me and deleting my stuff, as it has happened to a mate of mine. I have my mates in scotland watching my plex plus one of my cousins who's in the same city i'm in, but at the moment my port forward looks like this:
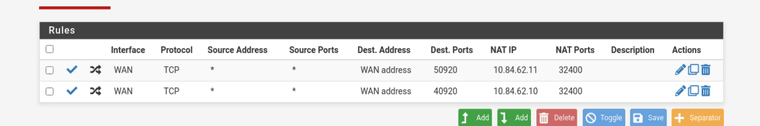
-
@jhmc93 in pfblocker it is very easy to setup geo IP based aliases.. You can add your Country and your mates Scotland..
The only thing would suggest is you also add the IPs from this list, because they do change now and then - and they could be from different countries.. And if the test from plex shows your offline remote, you could have issues and only be able to relay vs direct access, etc.
https://s3-eu-west-1.amazonaws.com/plex-sidekiq-servers-list/sidekiqIPs.txt
Currently I show both of those IPs being in Dublin, IE - but I have seen them change - not all that often mind you.. But in this scenario if your not allowing IE then to plex you wouldn't be available remote.
Does this prevent you from being hacked - no not really.. But all of the issues I have heard about with plex has been their account was compromised.. ie if they guess/know your password your kind of screwed.. Which is why users were screaming for a really long time about 2FA.. Which they now have, and I would suggest you enable that... Also your plex password shouldn't be P@55w0rd! for example - mine is currently a random 20 character password.. Good luck guessing that ;) hehe Its a pita to have to put in, but really you don't really have to do that more than once... And linking new devices, you put in the code on the tv and auth via your pc or phone that you have the password saved in anyway.
Also just good common sense - your email should be the most secure.. Because if they gain access to your email, they prob can get into almost all your stuff, etc. For me this is even longer password, and 2FA..
My guess to these users that have their plex account accessed is they used a shitty password, or used it in multiple places and one of those places were breached, etc. You should use secure password, and have 2FA on and not use that password for any other stuff. But it can't hurt also limiting who can actually directly talk to your plex either, and it very simple to do with pfblocker geo based aliases. So why not do it.. Its always possible that at some point there will be a exploit to plex direct access, or a misconfiguration in plex that allows remote admin access.. So it makes sense to limit the exposure. I sure don't have anyone that should be accessing my plex in RU for example.
-
@johnpoz Sounds complicated, I'm very new to pfsense so a lot of my work on it have been guided by videos and how to guides, I have not longed started with pfsense and I am still getting used to it.