Best VPN for UDP
-
What ? Wireguard doesn't let UDP to go over the connection ?
That will break all DNS for starters ... so no one would use it ....Any VPN type of connection accepts TCP, UDP, ICMP and all the others.
It's the admin (of pfSEnse) who decides what he accepts :
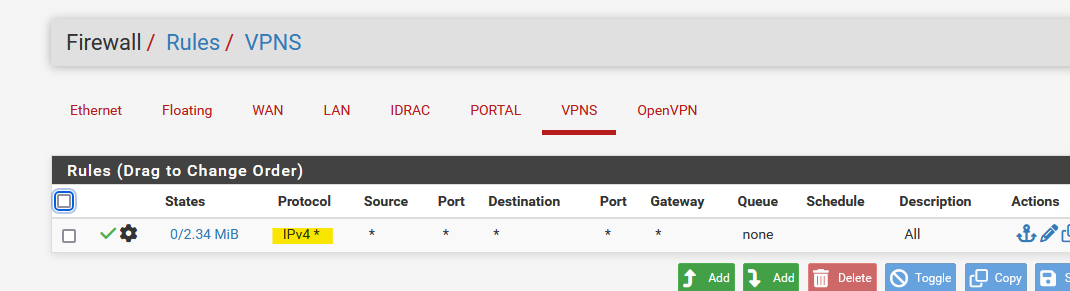
so I accept "IPv4" : all protocols.
This :
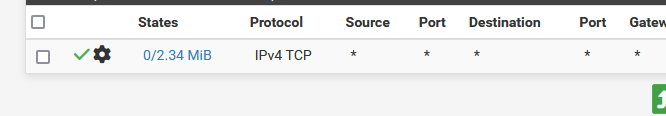
would make my VPN pretty (humm : totally) useless.
-
Yup your firewall rule allowing that traffic is probably still set to pass TCP only because that's the default value for protocol.
-
@stephenw10 , @Gertjan I set Firewalls Rules to "IPv4 ANY" and still traffic UDP Traffic does not flowing through through tunnel.
I have one UDP Source which is providing UDP in the LAN network of Site 1 (able to read it in site 1) and I want to get the same UDP Feed to Site 2 LAN , tried via wireguard tunnel.
Both sides all firewall rules set to *, Still the TCP Ips passing through it but UDP unable to read UDP at site 2.
Am I missing something ?
-
How are you actually trying to connect to the remote UDP service? What error is shown?
-
@stephenw10 . I can check udp via VLC Player by entering the multicast IP and I am checking the same at site 2 via the same VLC but unable to get it play at site 2.
Usually UDP generated a lot of traffic in interfaces and I am unable to see that data flow even in tunnels interfaces too.
-
@getin said in Best VPN for UDP:
Usually UDP generated a lot of traffic in interfaces and I am unable to see that data flow even in tunnels interfaces too.
I created a small test showing UDP traffic.
My pfSense hosts a OpenVPN server, a vanilla setup.I packet captured the DNS port 53 UDP traffic with this :
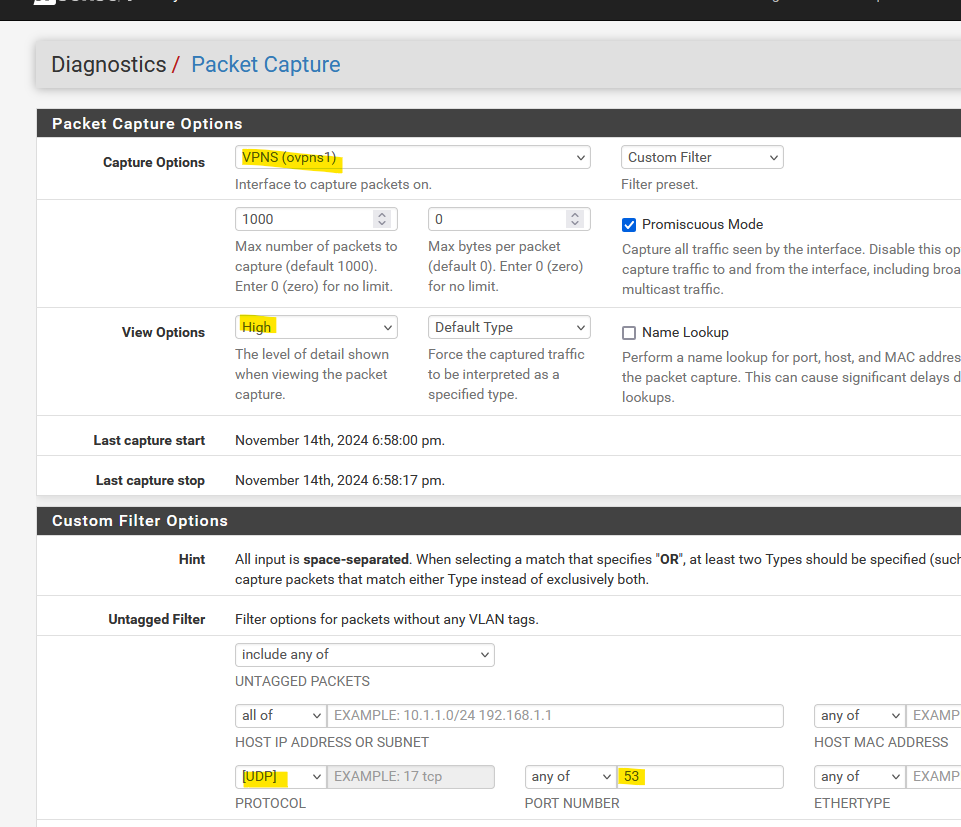
and connect my phone uysing the OpenVPN app.
DNS traffic came in by boatloads :
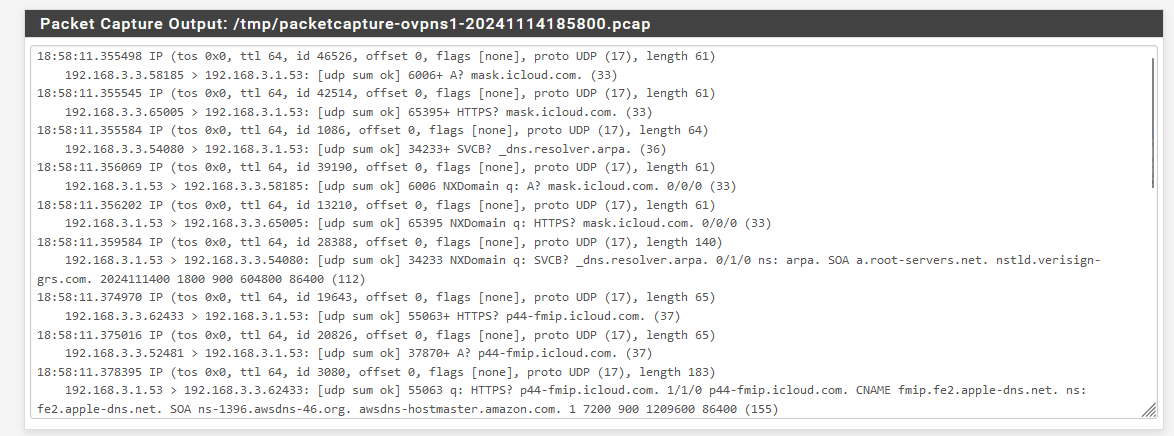
and of course UDP works because it wouldn't be a streaming issue but an overall connectivity issue : without DNS things go downhill very fast.
All this makes me think :
UDP works 'a little bit' or not all all ?
What happens if you 'capture' UDP traffic : there (really) is 'nothing' ? -
OK so you're actually looking at multicast traffic. So at a minimum you will need to set 'enable IP options' on the pass rules.
I assume you have different subnets at each end of the tunnel?
You may also need to setup the IGMP proxy to subscribe to the traffic.
-
@Gertjan , I can see the UDP Traffic when packet capture is in "LAN" Interface at source but Unable to see the UDPtraffic when observed in "Tunnel" interface at source site 1
@stephenw10 , I have made enable options in firewall rules for "LAN" and "Tunnel" and IGMP Proxy enabled at source and detaination with LAN as source, Tunnel as Destination at site 1 and vice versa in site 2, but still unable to get the traffic.
Packet Capture in Tunnel Interface is not showing UDP packets at site 1 but TCP works and The UDP packets are showing in LAN Interface at site 1, dont know if they need to route to tunnel ----
-
Forget about the fact this is UDP the problem is that it's mulicast traffic and you're trying to use it between subnets.
For example if you try to use the remote side DNS server in pfSense that is UDP and should work fine as long as ACLs exist to allow it.
I think we're going to need more details about what subnets are used here and exactly how you are testing.
-
@stephenw10 I fell into this topic! I have experienced a lot; especially since the 24.11 update of blockage of attempts from two of my subnets to 224.0.0.22 - which I understand is all about multicast. Your solution on the subnets is to go to advanced in openvpn and wireguardvpn - these are the two ways I am trying to reach content on my LAN subnets - individual rules allowing access to individual IP's for each LAN subnet - and allow IP options?
-
Yes you will need a least that. But you may also need the IGMP proxy configured, possibly at both ends, so that clients can see the streams and subscribe to them.