Static route for avoid double NAT
-
Hello community!
Can not to make working my settings.- pfSense router 192.168.20.1
- Asus router 192.168.20.2 ( set in pfSense as statis IP and get IP automaticaly in router)
- Internal router subnet 192.168.100.0/24
What was did: - Assign gateway in pfSesne
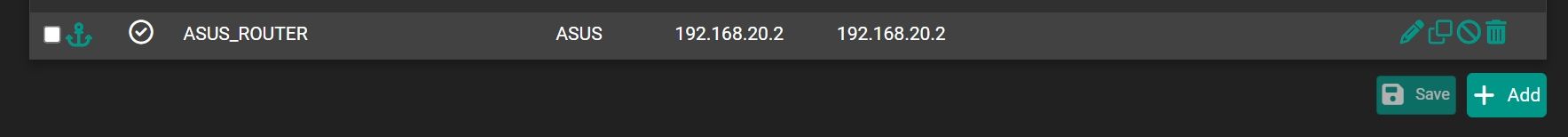
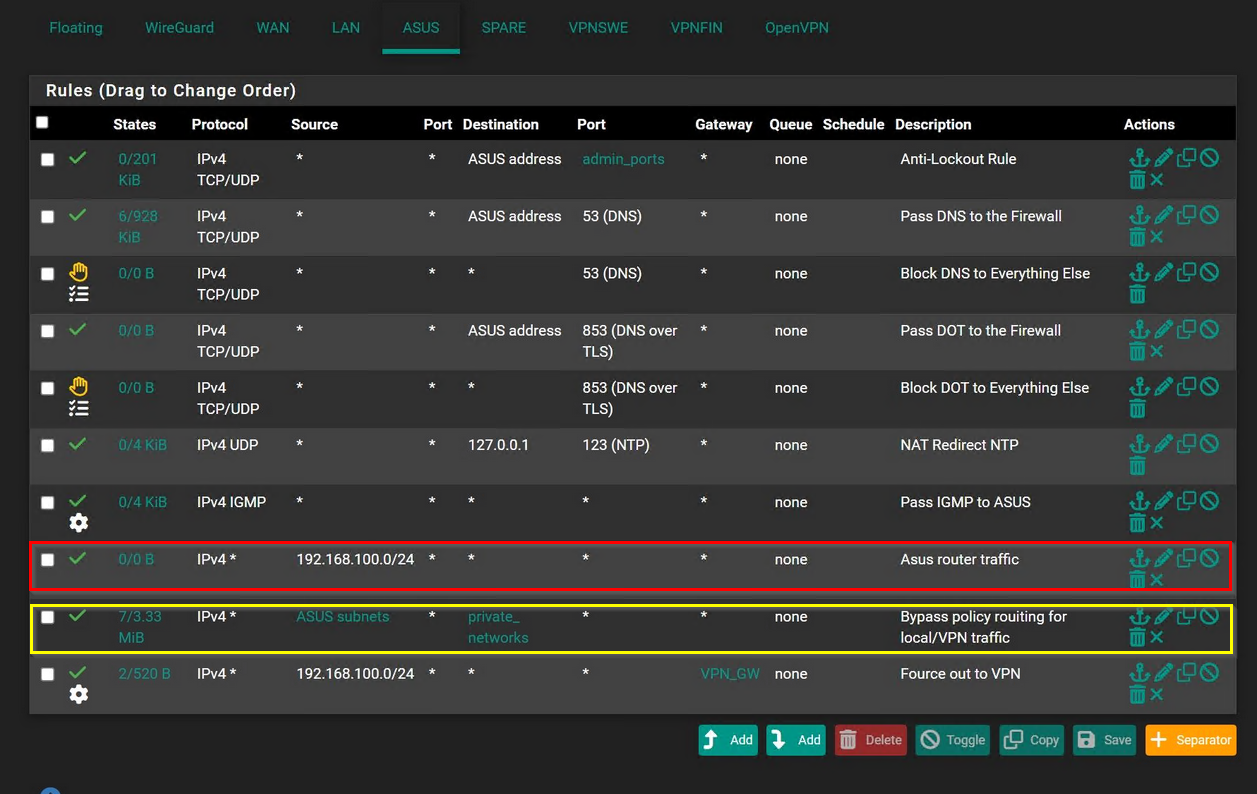
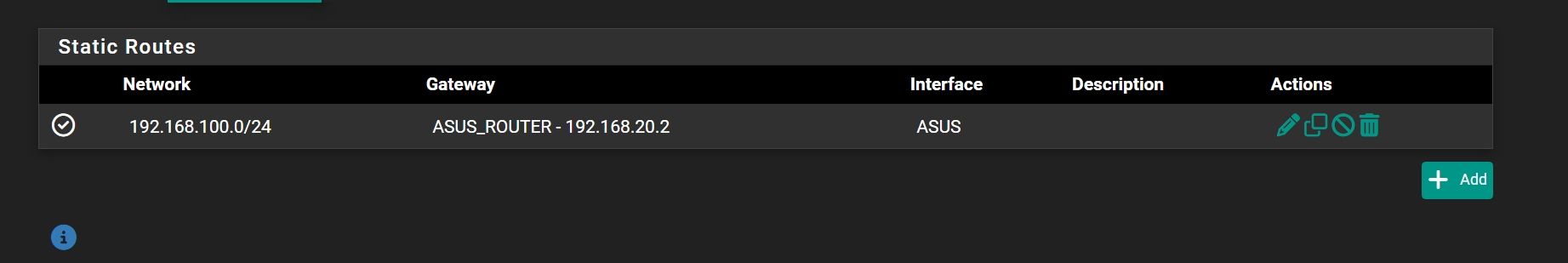
- Made static route
- Disabled DCHP, FIREWALL and NAT in Asus router.
Have a question, do I need to make static route in Asus router, if yes what kind of settings to apply?
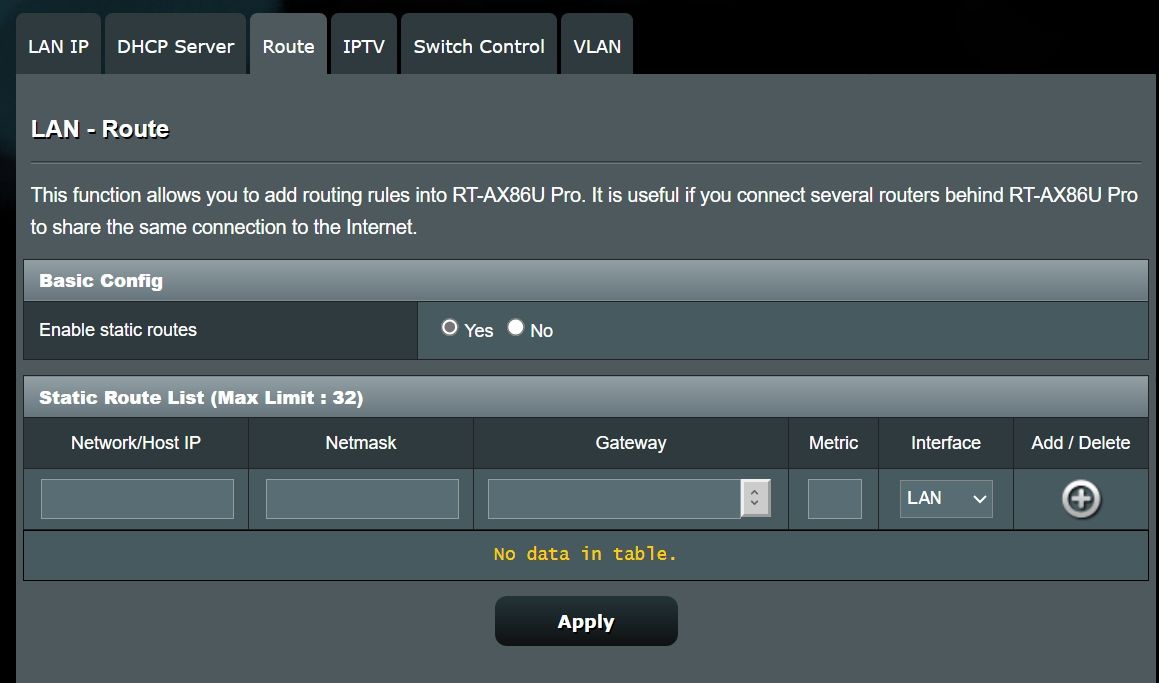
And yes, I can set to AP mode router but want to learn static route to make him work!
This is firewall rules on pfSense interface:
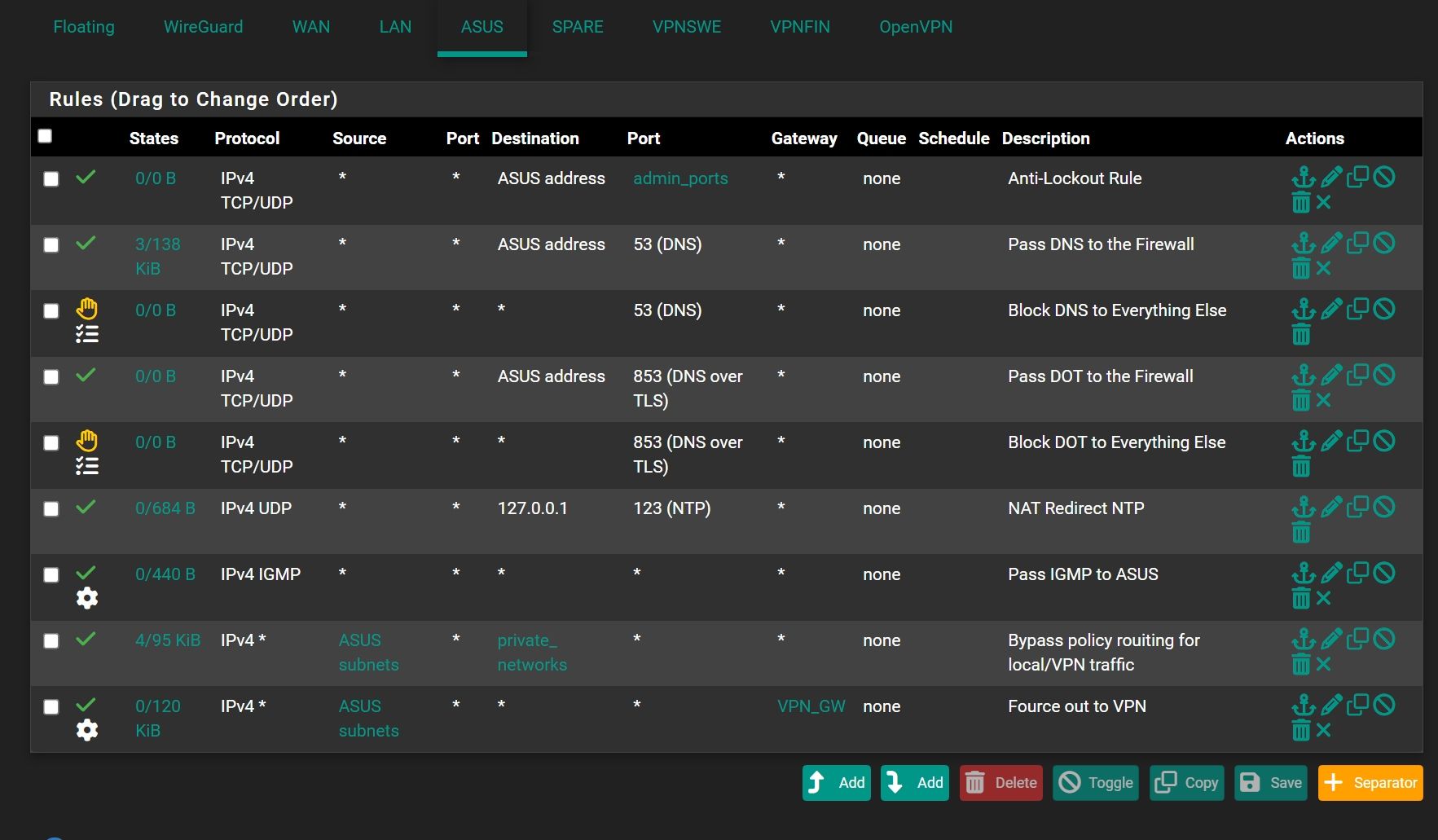
Please assist me to make this to work!
pfSesne advanced settings set "Check Bypass firewall rules for traffic on the same interface"
pfSense Unbound in forwarder mode to cloudflare.
pfSesne use OpenVPN as client to mullvad VPN.
pfSense use KEA DCHP. -
@Antibiotic said in Static route for avoid double NAT:
Have a question, do I need to make static route in Asus router, if yes what kind of settings to apply?
It needs a route at least to access devices behind pfSense from its point of view.
If you have stated pfSense as upstream gateway on the Asus router no further routes are needed.This is firewall rules on pfSense interface:
Since you've disable NAT, I don't expect, that pfSense sees packets from the routers IP, when a device behind the router tries to access something.
You will need rules for the source of the router for the routers traffic, but you need also rules to allow traffic from 192.168.100.0/24. -
@viragomann said in Static route for avoid double NAT:
You will need rules for the source of the router for the routers traffic, but you need also rules to allow traffic from 192.168.100.0/24.
Can you please explain more in deep. I need this rules on pfSesne in NAT firewall? NAT port forward or NAT outbound?or firewall rules for this interface?
-
-
@Antibiotic said in Static route for avoid double NAT:
for the routers traffic
It mean 192.168.20.1?
-
@Antibiotic
Your rule set on the ASUS interface doesn't allow any traffic from 192.168.100.0/24 apart from DNS, NTP und IGMP.
So you need to add rules to allow access for the subnet behind the router. -
@viragomann So this is clear , I have to make rule to allow traffic from 192.168.100.0/24 in pfsesne interface. Is it right? But not to clear about NAT rule?
-
@Antibiotic
You don't no NAT rule. You want it to do with routes, as you mentioned. -
@viragomann So, I need only one rule to allow traffic 192.168.100.0/24 ?And static route.
-
@viragomann Oh god I did a rule and start working))))
Thank you my friend)))
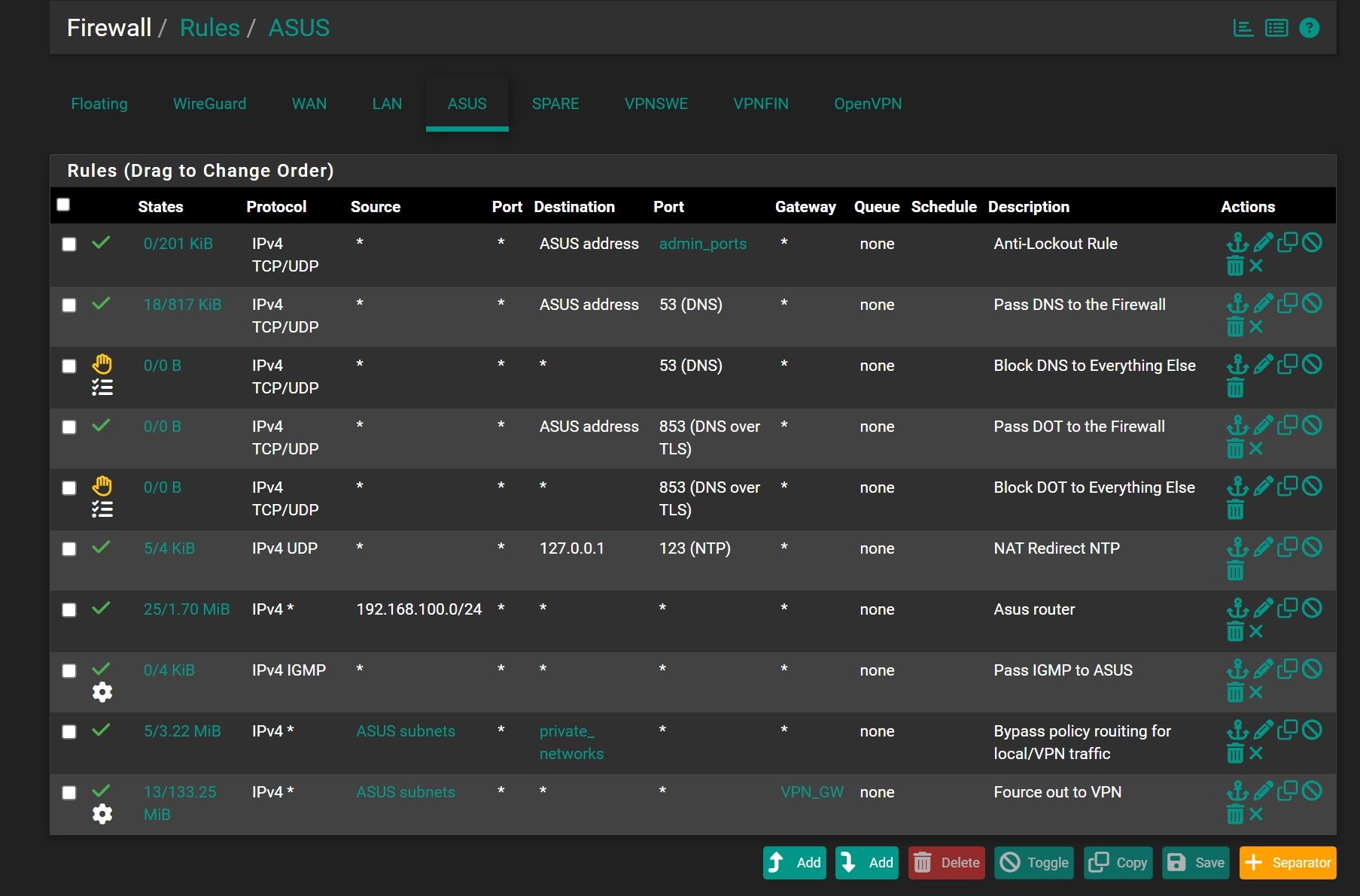
But it will correct order or better to set first as rule or doesn't matter? And also "any" ports destination gateway will correct in this rule regarding security?
-
@Antibiotic
The order of the router and the routers LAN doesn't matter.For the security point, just restrict access for 92.168.100.0/24.
If you want to give it only access to DNS, NTP, IGMP and internet limit the rule accordingly. -
@viragomann OK thank you, but the second problem now traffic going over default gateway not over VPN gateway. But if set to VPN gateway in rule traffic not going at all?
-
@viragomann said in Static route for avoid double NAT:
If you want to give it only access to DNS, NTP, IGMP and internet limit the rule accordingly.
In this case set protocol to TCP/UDP only?
-
@Antibiotic said in Static route for avoid double NAT:
OK thank you, but the second problem now traffic going over default gateway not over VPN gateway. But if set to VPN gateway in rule traffic not going at all?
You have already a policy-routing rule with the VPN gateway at the last position. Edit it and change the source to 192.168.100.0/24.
Then delete the other rule for this subnet.
If you want to give it only access to DNS, NTP, IGMP and internet limit the rule accordingly.
In this case set protocol to TCP/UDP only?
You have already proper rules for these protocols above. No need to add additional.
-
This post is deleted! -
@viragomann said in Static route for avoid double NAT:
You have already a policy-routing rule with the VPN gateway at the last position. Edit it and change the source to 192.168.100.0/24.
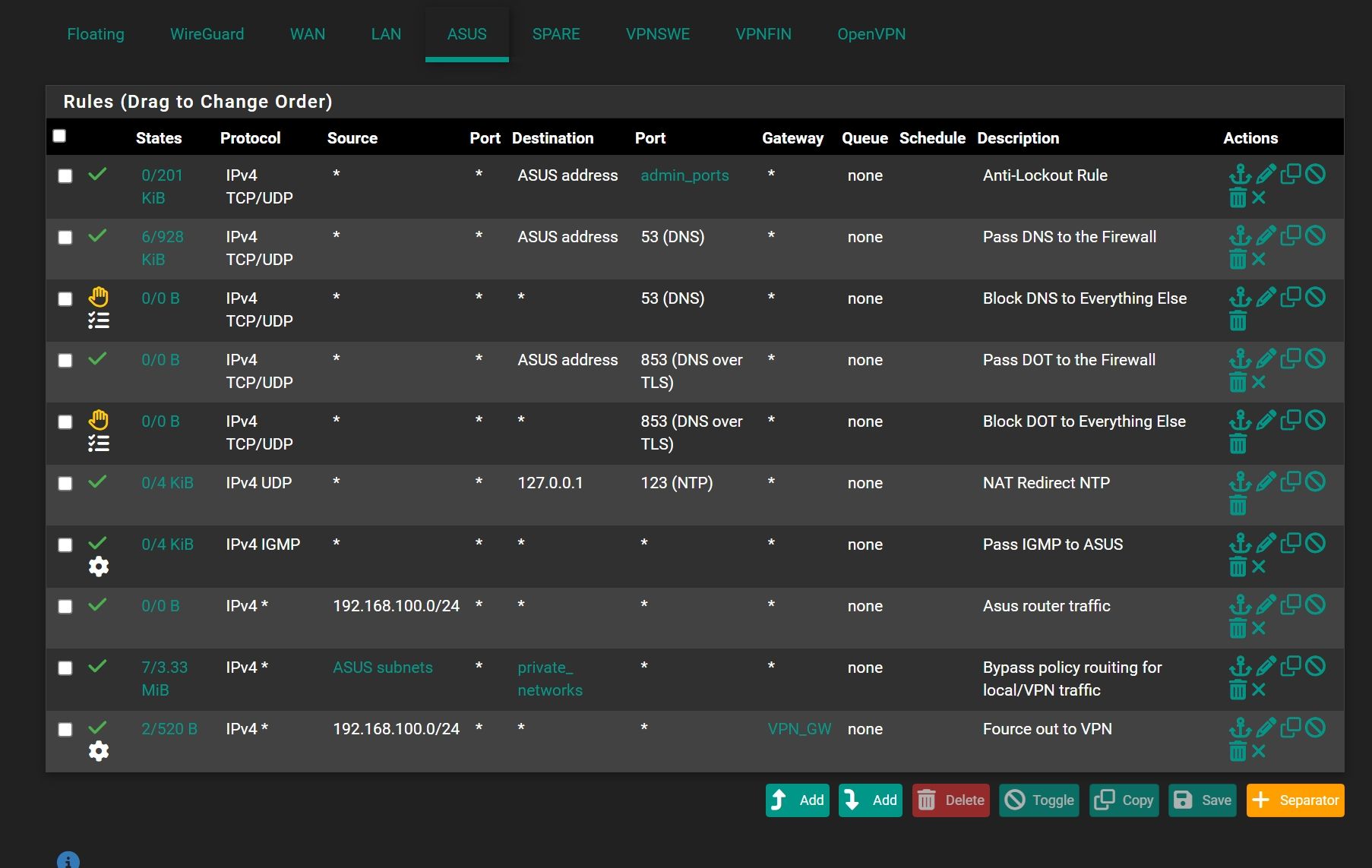
Not to clear, what should me delete?
If me delete 3rd rule from down internet not working -
The red one.
In the yellow you might want to change the source address accordingly.
Also remember, that you have to change the source in the outbound NAT rule on the VPN interface to the new network.
-
@viragomann I would like to tell you a big thanks, now everything start working over VPN! What I have now Asus router in router mode, because want to use QOS , statistic and etc and eliminated double NAT. Thank you my friend))) Tried to make to work this static route a few times without success, now I'm happy)))
-
@viragomann said in Static route for avoid double NAT:
Also remember, that you have to change the source in the outbound NAT rule on the VPN interface to the new network.
That was a point))))
-
@viragomann But in this settings pfSesne firewall will logging this network 192.168.100.0/24 and pfblockerNG will see this network?