[SOLVED] Route pfsense itself over VPN.
-
@stephenw10 said in Route pfsense itself over VPN.:
You could set static routes for those VPN endpoints via the WAN gateway.
Im sorry, im talking about openvpn clients in pfsense. They fail to connect to mullvad vpn server when rebooted. Can a static route help with that, and if so, how?
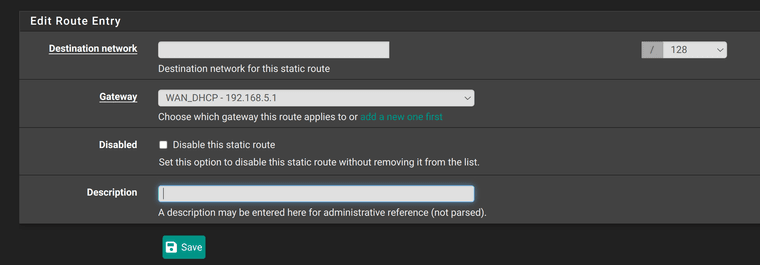
Not really sure what should i set in Destination network.
-
Put in the IP address of the VPN server the client connects to. pfSense uses the system routing table to determine how to route outgoing connections. Adding a static route to the VPN server will route it via the WAN.
-
@stephenw10 said in Route pfsense itself over VPN.:
Put in the IP address of the VPN server the client connects to. pfSense uses the system routing table to determine how to route outgoing connections. Adding a static route to the VPN server will route it via the WAN.
I have 3 openvpn clients in pfsense. Should i create 3 static routes ? One for each vpn server ?
-
Yes, add static routes to anything that needs to use the WAN gateway.
-
@stephenw10 said in Route pfsense itself over VPN.:
Yes, add static routes to anything that needs to use the WAN gateway.
One more question, what should i set as a interface in openvpn client
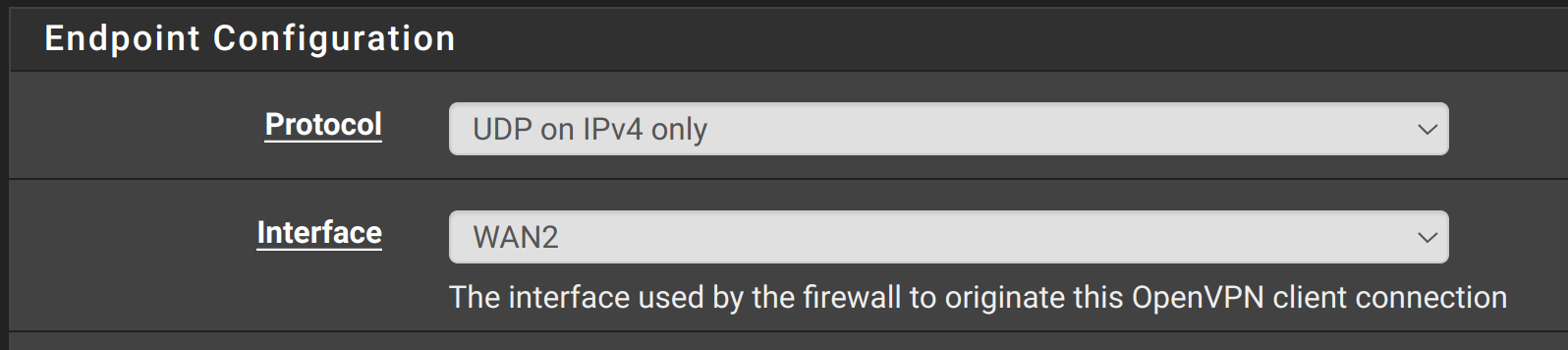
Or it doesnt matter and this is getting overridden by static mapping ?
I also have one wireguard client connected. I assume i need to create a static mapping for it as well ?
-
If you set the interface there it should source the connection from that IP address and route-to should force it via any gateway on that interface. But you seem to be seeing that not happen so adding a static route should correct that. At least as a test. If it still fails to connect then that's not the issue.
-
@stephenw10 said in Route pfsense itself over VPN.:
If you set the interface there it should source the connection from that IP address and route-to should force it via any gateway on that interface. But you seem to be seeing that not happen so adding a static route should correct that. At least as a test. If it still fails to connect then that's not the issue.
I created static routes for all openvpn clients that connect using WAN interface, rebooted, and pfsense got stuck at
Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAM Root mount waiting for: CAMfor 5-6 minutes and then continued to boot and stuck again at
igb5.35: link state changed to UP igb5.100: link state changed to UP igb5.200: link state changed to UP igb5.55: link state changed to UP igb5.65: link state changed to UP igb5.25: link state changed to UP igb5.15: link state changed to UP igb5.45: link state changed to UPI waited for 20 minutes but nothing happened.
Pressing Alt+Ctrl+Del starts the shutdown sequence and system reboots and its stuck again in the same way i described above. Web gui was inaccessible as well as SSH. I could not access command prompt either, so i had to reinstall pfsense again restore my config which, luckily, i have saved today.
I never had crash like this before.
-
That's not a crash it's what you see if you're not looking at the primary console. You should see just before the mountroot something like:
Nov 8 13:08:47 kernel Dual Console: Serial Primary, Video SecondaryYou can force the console to boot with the other one as primary at boot:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/boot-issues.html#booting-with-an-alternate-consoleThe fact it's not booting to the console menu implies it's stuck at something else that only showing on the primary console.
-
I forgot to mention, im not using serial console. I have a monitor and keyboard connected directly to pfsense box. The output i posted in previous post is from the primary console. I just copied dmesg output from fresh installation that works in order to show you where previous installation was stuck stuck.
Hope it makes sense now.
-
Hmm, well it sure seems like it's set to serial as primary console from what you're seeing. But as I say you should be able to see which is set at the vga console.
-
@stephenw10 said in Route pfsense itself over VPN.:
Hmm, well it sure seems like it's set to serial as primary console from what you're seeing. But as I say you should be able to see which is set at the vga console.
Success !!!
I made the mistake when creating a static route by typing ip address of openvpn server and then selecting the subnet. Selecting the subnet was a mistake that caused pfsense to be stuck at boot. I created new static route by typing the openvpn server address, chose the appropriate WAN and saved the setting. After reboot, pfsense booted just fine. I created additional static routes for the remaining vpn clients and everything just worked. Rebooted once again, no issues. Then i selected openvpn client as a default gateway and that was it.
All tailscale clients are now going through vpn, and all vpn clients connect without any issues after reboot.
Thank you very much Stephen. All this would not be possible without your help. Im marking this thread as resolved.
Cheers.