How can I configure our pfSense firewalls to allow Server B, located on a client network connected through a tunnel to our primary firewall, to connect to Server A, which is hosted in our remote office connected via a site-to-site VPN?
-
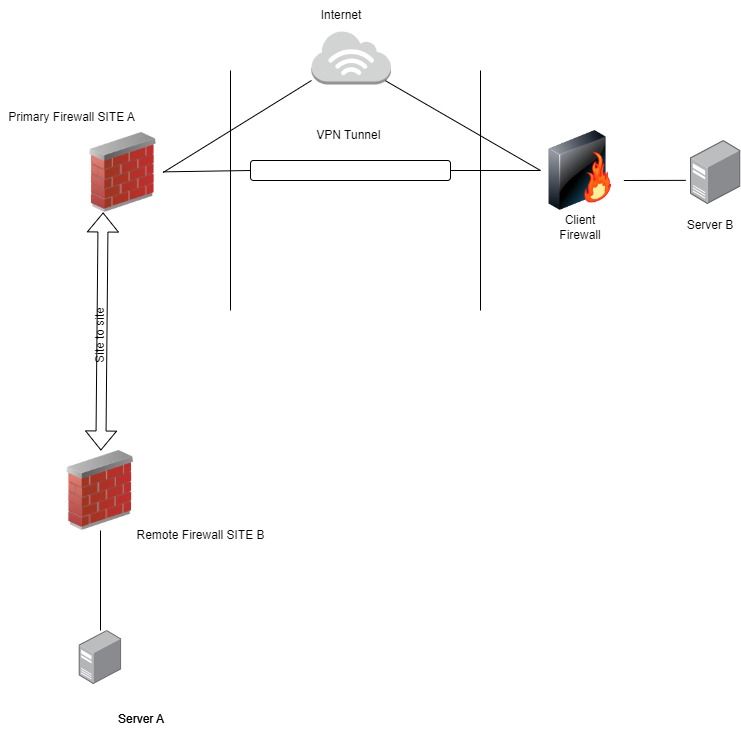
Our company is using Primary Pfsense firewall and a other pfsense for remote office. The remote office pfsense are connected to the primary pfsense by site to site. also the client network are connected using tunnel from the primary firewall. Now the client side Server B want to make connection to Server A that is hosted in our remote office. so how can i resolve this issue & and where i have to write rules.
-
@aneeshksurendran9007 said in How can I configure our pfSense firewalls to allow Server B, located on a client network connected through a tunnel to our primary firewall, to connect to Server A, which is hosted in our remote office connected via a site-to-site VPN?:
also the client network are connected using tunnel from the primary firewall.
Which tunnel?? IPSec as well?
Policy-based IPSec or routed?
-
@viragomann We are using IPsec tunnels to make connection from primary pfsense to client side. Using openvpn client we can connect to the client side. but the issue is that server from the client side want to connect our remote site server .
-
@aneeshksurendran9007
You need to configure both VPNs in play for proper routing the traffic. Hence both are relevant.So in the IPSec you have to add an additional phase 2 on both sites to connect the OpenVPN tunnel network with server A.
Means, on the pimary:
local: network > OpenVPN tunnel network
remote: server A IPOn the remote:
local: server A IP
remote: OpenVPN tunnel networkIn the OpenVPN access server settings, in case you haven't "redirect gateway" enabled, you have to add server A IP to the local networks with a /32 mask to push the routes to the clients.
-
@viragomann you are saying that we need to create another tunnel in remote office firewall? we all ready created P1 & p2 tunnel in main firewall . my question is that if i write rule in remote office firewall, the client server can access the server in site B
-
@aneeshksurendran9007
If your current phase 2 doesn't cover the OpenVPN tunnel network, you need a second one.
IPSec phase 2 must always be added to both sites.You can circumvent this, however, by natting the VPN clients access to an unused IP of the existing p2 at the main office.