assist in finding matching rule
-
Cant believe im just needing help with this but i assume this is a basic oversight on my behalf.
I have a large rule base for an interface and im debugging a policy routing issue. I dont see my traffic matching a security rule and most of the rules are not logging.
Is there a way to see in the GUI which rule a flow is currently matching? If so, how?Secondly, is there a way to nest aliases into each other.
For example i have a port alias called 'Web Ports' which contains various port numbers.
I have a seperate alias that i would like to nest inside 'Web Ports' but when i do that a traffic flow doesnt matter. Is this possible? -
@michmoor said in assist in finding matching rule:
Secondly, is there a way to nest aliases into each other.
This Nesting Aliases ?
@michmoor said in assist in finding matching rule:
Is there a way to see in the GUI which rule a flow is currently matching? If so, how?
Real time ?
That already difficult to do on the command line (IMHO).This works :
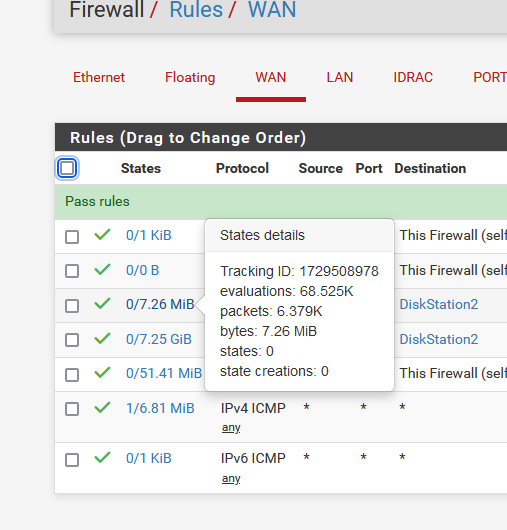
to see some info.
Next-best : I packet capture.
Or I make a rule log, and tail the firewall log file, using grep to show up only the interaction of the rule I'm interested. -
@Gertjan I just need to know which rule is matching. Connectivity is working.
Large portion of the rule base isn't set to log so i was wondering if there was some alternate way to see which flows are being matched by which security rule.Nesting aliases is pretty common actually. If i have multiple alias's there are times when there is a need to combine all those aliases under one. Just curious of pfsense can perform this function.
-
@michmoor
You seen the console (ssh !!) option 9 : pfTop ? -
@Gertjan pftop doesnt show which rule is matching for a flow., It only shows active connections.
-
If there is a state open you can see which rule number opened that state and then look at the rule list to find out what that is.
That's something I would usually do at the CLI though.
For example:
[admin@5100.stevew.lan]/tmp: pfctl -vss | grep -A 2 8.8.8.8 pppoe0 icmp 86.191.93.126:11757 -> 8.8.8.8:8 0:0 age 00:01:48, expires in 00:00:10, 108:108 pkts, 9072:9072 bytes, rule 89, allow-opts pppoe0 udp 127.0.0.1:30721 -> 202.12.27.33:53 SINGLE:NO_TRAFFIC [admin@5100.stevew.lan]/tmp: pfctl -vvsr | grep '@89 ' @89 pass out inet all flags S/SA keep state (if-bound) allow-opts label "let out anything IPv4 from firewall host itself" ridentifier 1000012025 -
@stephenw10 copy that. thanks.
Probably would be low on the priority list but is this something that could be implemented in the GUI? -
You can sort of do it using the pftop state and rules views but you don't get the rule description (label). The label view doesn't really help.