ISC DHCP Dynamic DNS feature and Kea DHCP?
-
I've been using FreeIPA bind service for primary and secondary DNS servers for many years. All my pfSenses ISC DHCP are configured for Dynamic DNS updates with FreeIPA bind and this been working flawless for years too.
However, pfSense+ 24.11 Kea DHCP service doesn't seem having this feature, isn't it? Is there a way to add a custom configuration snippet to Kea DHCP - something like:
"DnsServers": [ "192.168.1.1" ], // BIND server IP "DnsUpdate": { "enabled": true, "keyName": "kea-ddns-key", "keySecret": "your-secret-key", "domainName": "example.com", "server": "127.0.0.1", "serverPort": 53 } -
@CapitanBlack try the Kea migration assistant page on the ISC website.
"ISC has developed the Kea Migration Assistant (KeaMA) tool to help users migrate from the legacy ISC DHCP server to the Kea DHCP server. This tool analyzes a valid ISC DHCP server configuration file and provides an equivalent configuration file for a Kea DHCP server."
-
@ahking19 said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
@CapitanBlack try the Kea migration assistant page on the ISC website.
"ISC has developed the Kea Migration Assistant (KeaMA) tool to help users migrate from the legacy ISC DHCP server to the Kea DHCP server. This tool analyzes a valid ISC DHCP server configuration file and provides an equivalent configuration file for a Kea DHCP server."
Thanks! That's a cool solution but how can I use a custom Kea configuration file with pfSense+ ?!
-
Please make this a direct feature in pfSense, especially useful with IPv6.
-
@CapitanBlack there is a Kea config file - /usr/local/etc/kea/kea-dhcp4.conf
My config is pretty basic so I haven't tried editing it and it may get overwritten but that is where I would look to test. At least until Netgate migrates/implements more of the Kea features.
-
@CapitanBlack said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
I've been using FreeIPA bind service for primary and secondary DNS servers for many years. All my pfSenses ISC DHCP are configured for Dynamic DNS updates with FreeIPA bind and this been working flawless for years too.
I've been looking at this.
Long story short : this is the concept : https://www.techtutorials.tv/sections/linux/how-to-setup-ddns-using-kea-and-bind/ (be ware, based upon older kea doc)
and the kea manual : https://kea.readthedocs.io/en/latest/arm/dhcp6-srv.html#ddns-for-dhcpv6
and it actually - no surprise - works.I'm only extending the DHCPv6 server with DDNS (aka D2) as I see no use of sending RFC1918 into my 'global bind domain name server.
So, what follows apply to DDNS IPv6 leases.Why this interests me ?
Because my IPv6 'server' stuff like airco, heating, security, servers, and my NAS on my pfSense can be accessed from 'everywhere' (by me) using IPv6. Now I can use their host names, just like I was at home (work actually).
I've ditched most of the old fashioned NAT IPv4 stuff.
IPv6 uses only firewall rules.
Btw : I still use OpenVPN to access al this. Most of the stuff can't be accessed otherwise, but there are exceptions.Let's start :
I've modified the existing dummy - it is not used right now by pfSense : /usr/local/etc/kea/kea-dhcp-ddns.conf file. I removed also all the comments :
{ "DhcpDdns": { "ip-address": "127.0.0.1", "port": 53001, "dns-server-timeout": 500, "ncr-protocol": "UDP", "ncr-format": "JSON", "control-socket": { "socket-type": "unix", "socket-name": "/var/run/kea-ddns-ctrl-socket" }, <?include "/usr/local/etc/kea/tsig-keys.json"?> "forward-ddns" : { "ddns-domains" : [ { "name": "my-real-domain-name.tld.", "key-name": "update", "dns-servers": [ { "ip-address": "188.165.ab.cd" } ] } ] }, "reverse-ddns" : { "ddns-domains" : [ { "name": "b.e.6.a.7.0.9.0.9.1.b.c.1.0.a.2.ip6.arpa.", "key-name": "update", "dns-servers": [ { "ip-address": "188.165.ab.cd" } ] } ] }, "loggers": [ { "name": "kea-dhcp-ddns", "output-options": [ { "output": "/var/log/kea-ddns.log" } ], "severity": "INFO", "debuglevel": 0 } ] } }Where "188.165.ab.cd" is the IPv4 where my 'bind9' domain name server lives. I could have used its IPv6 also as I'm dealing with IPv6 here after all.
Be ware : a new log file is created : /var/log/kea-ddns.log - you better watch this one, as it will 'grow' (disk space !!).
This one : /usr/local/etc/kea/tsig-keys.json - you have to make it yourself also :"tsig-keys": [ { "name": "update", "algorithm": "hmac-sha512", "secret": "eYQiVAutEEAFOjYxxxxxxxxxxxxxxxxxxxxxxyVoCxOQ/jwBeA10EPeE7vwEdFT11QYs1YhO9zDCaJwzkuZp0w==" } ],where "update" is in fact my update name (bind has to be set up with this) and also the 'secret'.
This is all RFC2136 - those who want to deal with ISC DHCP and now kea : you know what this is.
The other : this is DDNS (D2) as it was meant to be.I changed also the file keactrl.con and :
# Start DHCP DDNS server? dhcp_ddns=noto
# Start DHCP DDNS server? dhcp_ddns=yesBut I don't think pfSense actually uses keactrl to control all the kea processes.
It let me do this :
[24.11-RELEASE][root@pfSense.bhf.tld]/usr/local/etc/kea: service kea onestop INFO/keactrl: Stopping kea-dhcp4... INFO/keactrl: Stopping kea-dhcp6... INFO/keactrl: Stopping kea-dhcp-ddns... INFO/keactrl: Stopping kea-ctrl-agent... [24.11-RELEASE][root@pfSense.bhf.tld]/usr/local/etc/kea: service kea onestart Starting kea. INFO/keactrl: Starting /usr/local/sbin/kea-dhcp4 -c /usr/local/etc/kea/kea-dhcp4.conf INFO/keactrl: Starting /usr/local/sbin/kea-dhcp6 -c /usr/local/etc/kea/kea-dhcp6.conf INFO/keactrl: Starting /usr/local/sbin/kea-dhcp-ddns -c /usr/local/etc/kea/kea-dhcp-ddns.conf INFO/keactrl: Starting /usr/local/sbin/kea-ctrl-agent -c /usr/local/etc/kea/kea-ctrl-agent.conf [24.11-RELEASE][root@pfSense.bhf.tld] ps ax | grep 'kea' 33624 0 S 0:00.15 /usr/local/sbin/kea-dhcp4 -c /usr/local/etc/kea/kea-dhcp4.conf 35005 0 S 0:00.10 /usr/local/sbin/kea-dhcp6 -c /usr/local/etc/kea/kea-dhcp6.conf 37777 0 S 0:00.06 /usr/local/sbin/kea-dhcp-ddns -c /usr/local/etc/kea/kea-dhcp-ddns.conf 41629 0 S 0:00.04 /usr/local/sbin/kea-ctrl-agent -c /usr/local/etc/kea/kea-ctrl-agent.conf 79188 0 S+ 0:00.00 grep kea 64413 1 SC+ 0:00.01 tail -f /var/log/kea-ddns.logBtw : in a console, I'm running :
tail -f /var/log/kea-ddns.logfor testing purposes.
Now, let's make 'kea-dhcp6' DDNS (D2) aware :
Modify /etc/inc/services.inc : locate this part :
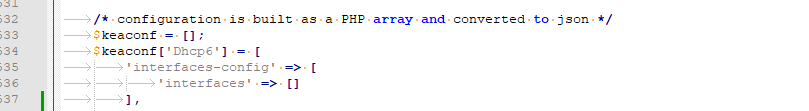
and add the new stuff :
'dhcp-ddns' => [ 'enable-updates' => true, 'server-ip' => '127.0.0.1', 'server-port' => 53001, 'sender-ip' => '', 'sender-port' => 0, 'max-queue-size'=> 1024, 'ncr-protocol' => 'UDP', 'ncr-format' => 'JSON' ], 'ddns-send-updates' => true, 'ddns-qualifying-suffix' => 'my-real-domain-name.tld', 'ddns-update-on-renew' => true, 'ddns-use-conflict-resolution' => false, 'ddns-override-client-update' => true, 'lease-database' => [ 'type' => 'memfile', 'persist' => true, 'name' => '/var/lib/kea/dhcp6.leases' ],So now it looks like :
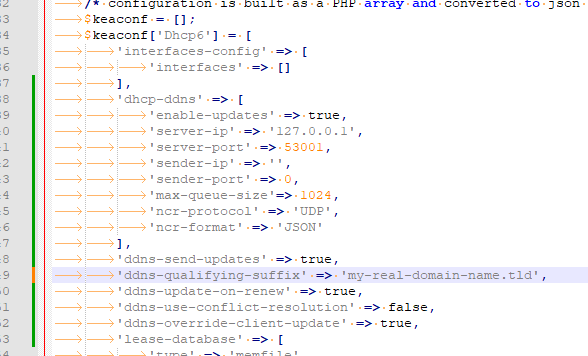
I strongly advise everybody to look up and understand what these :
'ddns-send-updates' => true, 'ddns-qualifying-suffix' => 'my-real-domain-name.tld', 'ddns-update-on-renew' => true, 'ddns-use-conflict-resolution' => false, 'ddns-override-client-update' => true,do and mean.
And that's all I did.
I went to Services > DHCPv6 > Server Settings and did a Save + Apply - and double checked that the new kea-dhcp6.conf now contains the 'D2' settings.I one stopped and one started kea on the command line.
service kea onestop service kea onestartand checked what was running :
ps ax | grep 'kea'I ran to a windows PC and ran
ipconfig /renew6The /var/log/kea-ddns.log I was tailing immediately showed very promising stuff :
Example :2024-12-25 11:28:17.078 INFO [kea-dhcp-ddns.d2-to-dns/68140.0x1013c212000] DHCP_DDNS_ADD_SUCCEEDED DHCP_DDNS Request ID 000201E9BEB6D49A87E87473BD807E3BB560DD08F0EA386787BEA86F250F9611B3E65A: successfully added the DNS mapping addition for this request: Type: 0 (CHG_ADD) Forward Change: yes Reverse Change: yes FQDN: [ricoh.my-real-domain-name.tld.] IP Address: [2a01:cb19:907:xxxx::87] DHCID: [000201E9BEB6D49A87E87473BD807E3BB560DD08F0EA386787BEA86F250F9611B3E65A] Lease Expires On: 19700101000000 Lease Length: 7200 Conflict Resolution Mode: no-check-with-dhcidand the bind domain name server side, as there are also logs that really wanted to be seen :
25-Dec-2024 11:28:17.010 update-security: client @0x7fee58308cb0 82.127.26.108#10380/key update: signer "update" approved 25-Dec-2024 11:28:17.010 update: client @0x7fee58308cb0 82.127.26.108#10380/key update: updating zone 'b.e.6.a................ip6.arpa/IN': deleting rrset at '......0.9.1.b.c.1.0.a.2.ip6.arpa' PTR 25-Dec-2024 11:28:17.010 update: client @0x7fee58308cb0 82.127.26.108#10380/key update: updating zone 'b.e.6.a................ip6.arpa/IN': deleting rrset at '......0.9.1.b.cc.1.0.a.2.ip6.arpa' DHCID 25-Dec-2024 11:28:17.010 update: client @0x7fee58308cb0 82.127.26.108#10380/key update: updating zone 'b.e.6.a................ip6.arpa/IN': adding an RR at '........0.9.1.b.c.c.1.0.a.2.ip6.arpa' PTR ricoh.my-real-domain-name.tld. 25-Dec-2024 11:28:17.010 update: client @0x7fee58308cb0 82.127.26.108#10380/key update: updating zone 'b.e.6.a................ip6.arpa/IN': adding an RR at '........0.9.1.b.cc.1.0.a.2.ip6.arpa' DHCID AAIB6b621JqH6HRzxxxxx5lo=Disclaimers :
As always : it works 'for me'. Don't try this at work - only home. If you don't know what you are doing, don't do this.
Be ready to undo what you did, and you'll be fine.
Syntax errors are not allowed. kea is extremely picky. The slightest space, comma, { or [ missing, and it's game over.
This has some manual implications, as I'm not sure what happens when I save the kea dhcp6 servers settings again.
Or restart the dhcp6 kea server or dhc4 kea server from the GUI.
Will "/usr/local/sbin/kea-dhcp-ddns -c /usr/local/etc/kea/kea-dhcp-ddns.conf" get restarted ? (I guess not)
Is in 'dangerous' that I have also "/usr/local/sbin/kea-ctrl-agent -c /usr/local/etc/kea/kea-ctrl-agent.conf" now running ?Anyway : Kea with DDNS using IPv6 is very possible.
-
I was told by Netgate support that eventually Kea DHCP will get the same features set as ISC DHCP - including Dynamic DNS updates.
Meanwhile I guess I'll stick with ISC DHCP.
If they remove it BEFORE Kea DHCP will get this feature - I'll migrate to Kea and will be be using pfSense DNS forwarder as the main DNS server for my networks. -
@CapitanBlack said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
I was told by Netgate support that eventually Kea DHCP will get the same features set as ISC DHCP - including Dynamic DNS updates.
Meanwhile I guess I'll stick with ISC DHCP.
If they remove it BEFORE Kea DHCP will get this feature - I'll migrate to Kea and will be be using pfSense DNS forwarder as the main DNS server for my networks.The dynamic DNS update works properly in the latest pfSense Plus update (24.11). But the Kea component in the current 2.7.2 CE release of pfSense does NOT perform dynamic DNS updates.
I suspect (but have no confirmation) that the dynamic DNS update feature will get incorporated into the next release of pfSense CE which will probably be 2.8. Until then, if you are using the CE (Community Edition) version, you should probably stick with using ISC for the DHCP server. The ISC server will not disappear before the new Kea component matches it in feature parity.
-
@bmeeks said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
@CapitanBlack said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
I was told by Netgate support that eventually Kea DHCP will get the same features set as ISC DHCP - including Dynamic DNS updates.
Meanwhile I guess I'll stick with ISC DHCP.
If they remove it BEFORE Kea DHCP will get this feature - I'll migrate to Kea and will be be using pfSense DNS forwarder as the main DNS server for my networks.The dynamic DNS update works properly in the latest pfSense Plus update (24.11). But the Kea component in the current 2.7.2 CE release of pfSense does NOT perform dynamic DNS updates.
I suspect (but have no confirmation) that the dynamic DNS update feature will get incorporated into the next release of pfSense CE which will probably be 2.8. Until then, if you are using the CE (Community Edition) version, you should probably stick with using ISC for the DHCP server. The ISC server will not disappear before the new Kea component matches it in feature parity.
I use pfSense+ but fully agree. I'll stick with ISC DHCP until pfSense Kea DHCP will support DDNS and OMAPI (or another way of programmatic leases manipulation).
-
@CapitanBlack said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
@bmeeks said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
@CapitanBlack said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
I was told by Netgate support that eventually Kea DHCP will get the same features set as ISC DHCP - including Dynamic DNS updates.
Meanwhile I guess I'll stick with ISC DHCP.
If they remove it BEFORE Kea DHCP will get this feature - I'll migrate to Kea and will be be using pfSense DNS forwarder as the main DNS server for my networks.The dynamic DNS update works properly in the latest pfSense Plus update (24.11). But the Kea component in the current 2.7.2 CE release of pfSense does NOT perform dynamic DNS updates.
I suspect (but have no confirmation) that the dynamic DNS update feature will get incorporated into the next release of pfSense CE which will probably be 2.8. Until then, if you are using the CE (Community Edition) version, you should probably stick with using ISC for the DHCP server. The ISC server will not disappear before the new Kea component matches it in feature parity.
I use pfSense+ but fully agree. I'll stick with ISC DHCP until pfSense Kea DHCP will support DDNS and OMAPI (or another way of programmatic leases manipulation).
Sorry, I did not pay close enough attention to your original post. Your issue is updating secondary DNS servers and not the
unbounddaemon running on pfSense.Kea is unable to do that at the moment. And on pfSense CE it can't even update the local
unbounddaemon in the 2.7.2 release. -
@bmeeks said in ISC DHCP Dynamic DNS feature and Kea DHCP?:
Your issue is updating secondary DNS servers and not the unbound daemon running on pfSense.
Correct. All hosts on my network get IP addresses from pfSense ISC DHCP servers those sends dynamic updates to FreeIPA-integrated BIND DNS servers.
Why use FreeIPA-integrated DNS? Because FreeIPA is a great OpenSource identity management software and it also uses ISC DNS service.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic
G Gertjan referenced this topic