Network Topology How to set up redundancy
-
After one of my main switches failed due to some unknown reason which I had to power cycle to fix, I am looking for a way to add some kind of redundancy to my setup which will try to keep my network up at least partially.
My current setup is daisy connecting the switches as below. I want to add below connection in red (OPT1) to my setup for a redundant link between pfsense and 2.5g switch but I am not sure how to set this up.Any recommendations here? (All my switches are unifi)
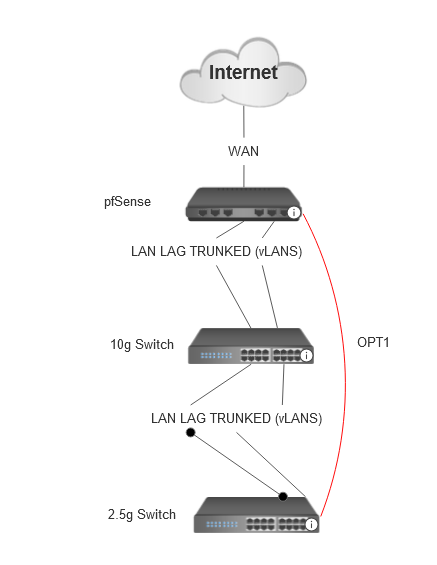
-
@Laxarus I understand the desire for the added link due to your experience, but creating redundancy in that manner is neither a good idea, nor good network design when it comes to a firewall that does not have a built-in switch with spanning-tree support.
To actually do what you are asking you would need to create a Bridge interface in pfSense containing your LAGG to the 10Gbe Switch and the link to the 2.5Gbe switch, and then you would have to run spanning-tree on both switches as well as on the created pfSense Bridge.
Bridges in pfSense is highly UN-recommended because all sorts af issues can arise from using them (And a software switch is just terrible design anyways).
When it comes to uptime/hardware or software failure rate (need to reboot) a switch SHOULD be far more stable than you firewall, so odds are - given decent hardware - that you pfSense box will cause a failure more often than a switch anyways. So I'd start by looking into the quality and firmwares of your switches rather then attempting to jerry-rig your config into a questionable software bridge config in pfSense.
-
@keyser I see, thanks for the info and advise. I was hoping there was a setting or hidden feature on pfsense to use that connection as redundant without a software bridge in case the main link fails.
I think I will stick with my original set up as you suggested in this case if there is no such feature.
-
@Laxarus why daisy chain them if you can run a link from the 2.5ge back to pfsense, just home run back to pfsense and forget the daisy chain.
Daisy chaining like that is never optimal setup, its normally done when there is a restriction in doing the a cable run, or your 2nd switch is too far and you can't run fiber, etc.
-
@johnpoz If I connect the 2.5g switch directly to pfsense, I need to bridge that interface with the LAN interface (which is going to 10g switch). Though, my cpu should be enough to handle the processing of the bridge, I don't want software bridges.
Or I need to rearrange my whole network, remove all the clients from LAN and use VLANs. (Create a new vlan for exLAN clients)
-
@Laxarus ah yeah valid point - the uplinks from the switches wouldn't be able to carry the same vlans.
Normally you would run back to your core switch, that was stacked where you would run the port channel with leg on each switch in the stack. Which protects from single switch failure.
-
@johnpoz well, yeah unfortunately. I was looking to strengthen my current setup but it seems there is nothing I can do for now.