Question Regarding Default Deny Rules
-
@djtech2k dhcpv6 is not required for IPv6 - prob using slaac
Out of the box pfsense would not setup IPv6 it would get on its wan on its lan.. Do you have IPv6 enable on your wan? Did you enable track interface for a prefix delegation?
If you do not even understand the basic concepts of how IPv6 even gets an address, then yeah I wouldn't have it enabled.
You can track an IPv6 to a device with NDP, it's really the same as arp - but for IPv6.. Here I enabled IPv6 on my machine to show you. I normally have it disabled
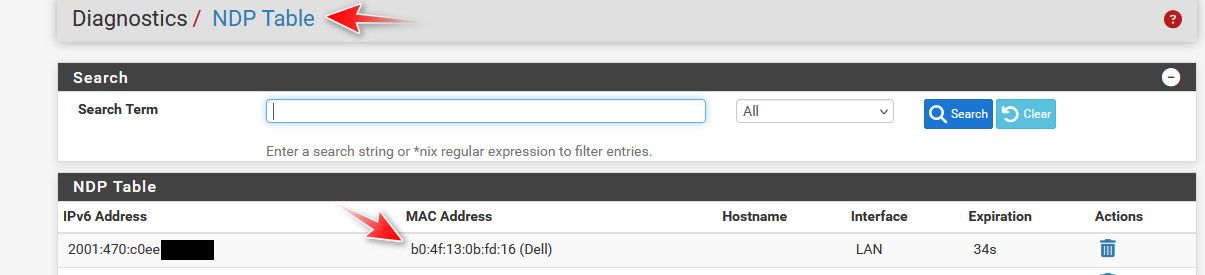
here are some other IPv6 my machine is using now that I turned it on

that fe80 is just a link local address.. Ipv6 clients normally use multiple IPv6 address - that address in my 2nd post with 2001:470 is different than the one I posted in the first pic.
Our resident ipv6 fan boy will prob chime in here soon about how IPv6 is required (its not) most of the planet still doesn't even have it deployed to be honest - my ISP doesn't provide it for example. Here is my advice to any protocol you do not understand how it works or for sure how to manage it - disable it plan and simple.. This is security 101.. If you don't understand how something works, or how to control it - how can it be secure.. And to quiet our fanboy since I think he searches for any mention of IPv6 - yes it is the future, yes it will get rid of that nasty thing called nat..
Hey if I get him to disable it - will I have slowed the snail roll of ipv6 deployment by another fraction of a nanosecond? ;)
edit: back to disabled on my client - because I have less than zero use for IPv6.. Even though I have been using it for almost 15 some years.. It still serves zero purpose on my network.. I turn it on to answer peoples questions.. My phone uses it when its out and about, etc. But locally it has no use to me, so like any security conscious person should do with protocols they are not actively using - they should be disabled.
I have been doing this for 30+ plus years and have worked for a few different companies, and for quite some time worked for a major MSP - not one client of ours was using IPv6.. Not one - we had no use for it anywhere in our own networks in some very large networks.. I actively looked for projects to work on that were using IPv6 - not one could I find... I did at a previous company get them a /32 from arin and got that all setup for them - and they working on a project to use IPv6 for mass car iot sort of deployment thing.. But no local IT resources anywhere in the global company were actually using IPv6, etc.. You can turn it off - and unless your playing some p2p game or something that is leveraging it.. You won't even notice its not there..
When someone like amazon or facebook or any other major player on the internet says - hey you have to have IPv6 to connect to us - that is when IPv6 has arrived.. Until that day arrives, I will for sure be retired if not dead, it is a very slow transition and we will be in a dual stack mode for many many many years to come - no matter how much our local fanboy thinks different ;) So if you do not understand it, don't know how to manage it - then yes disable it.
But if you want to learn about it - then yes I would say go for it.. But its a bit more involved than just a longer IP address ;)
-
They are probably link local addresses that are based on the device MAC address. If so you should be able to find the source devices from that.
However if you're not using IPv6 at all you can just not log it. Or ignore it.
-
So when you say disable ipv6, are you still talking about the client level? That would be a chore to touch all devices and I really don’t know how to disable it on lots of things like the Roku and Amazon echo for example.
You asked about the ipv6 track setting and the answer is yes. That was the default value and I left it. Are you suggesting disabling it at the pfsense level, and if so, what is the best setting/option to do that?
I’ve seen my ISP address be ipv6 when I checked it online. It comes back ipv4 most of the time and ipv6 sometimes. Not saying this is related to my LAN IPv6 conversation but just something I remembered.
-
@djtech2k if you do not hand out IPv6 from pfsense - no client can use IPv6 be it how much they might want too.
Yes if possible disable it that client - you prob can't do it so much that they don't have it in the stack.. But in windows its pretty simple to turn it off, and prevent the extra noise the windows will be sending out if it has a IPv6 link local even..
Here is my window 10 client..
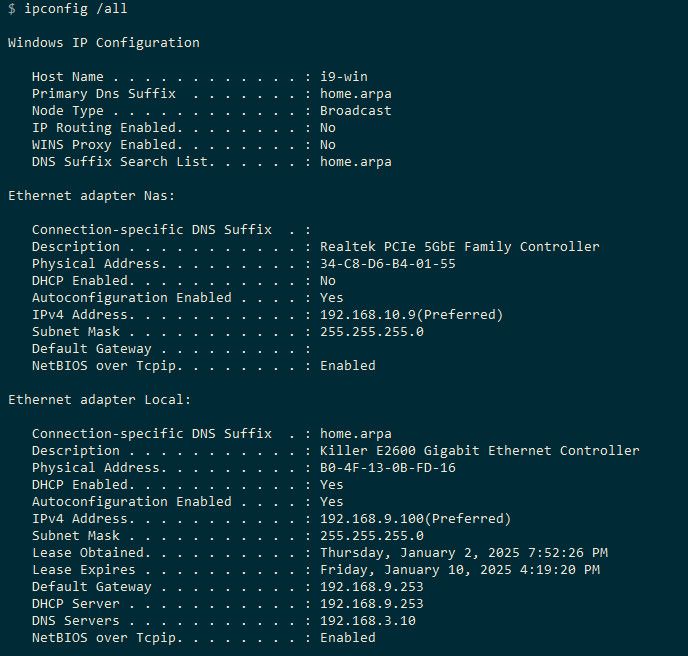
See any IPv6 ;) click on, click off is how easy it is in window 10..
Here is linux box
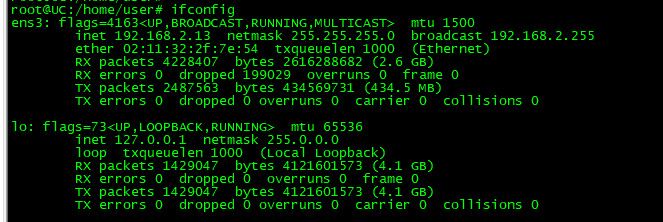
See any ipv6 link local address - nope.. Its still there in the stack on both systems, its not not enabled for any of the interfaces.
With pfsense - it would be more complicated to get rid of the link-local, but there is not GUA or ULA address etc.. here is one of my interfaces I don't even run IPv6 on
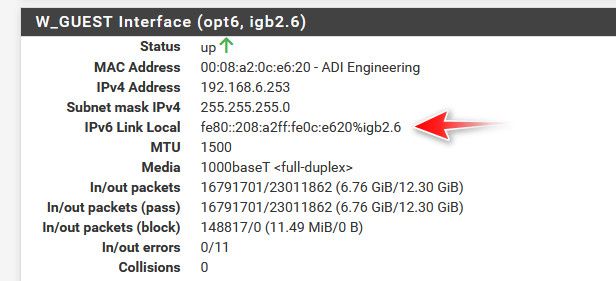
I do have it available on my network - and I can turn it on at will if want to play/test something, etc. But like I mentioned I have been playing with it for going on 15 years for sure.. And I would encourage you to do that as well - BUT!! if you are not ready to dive into it, and you don't understand it it - then from just from a security point of view I would not suggest you enable it if you don't not understand how to control it.. And if you do want to play/learn about it - enable it on a test network and play and learn vs turning it on for all devices in your network.
If you do want to play and learn - I would suggest you go over the IPv6 certification on Hurricane electric - going through the certification will get you familiar with the basics, and hey you can get a free tshirt ;)
https://ipv6.he.net/certification/
One of the users here just posted up that they got their tshirt ;)
-
@johnpoz On the topic of ipv6/pf, is there a way to have blacklist a mac from receiving an ipv6-RA?
The use case would be some android clients which expose no ipv6 config options.
The only way that comes to mind would be to enable ethernet filtering, then set up a rule to block ipv6 ethertype traffic to/from that given mac.
-
Mmm, I'm not aware of anything else. That would probably work though.
-
I have been tuning my rules to calm the noise and its working. Now I am seeing a high percentage of the log is incoming WAN traffic on UDP. For example, I see incoming WAN traffic from a Facebook IP using UDP. Its more than just FB but thats an example that repeats a lot. I know I can block the logging if its noise but I was just curious if anyone else sees that kind of traffic also. Incoming UDP traffic kind of surprises me from something like Facebook.
-
@djtech2k yes there is tons of noise on the internet - why do you think I turned off the default deny... I log incoming syn, and interesting udp ports..
And log the allow rules I want to log..
-
@johnpoz Can you show a screen shot of what your inbound rules look like?
-
@GPz1100 on my wan sure
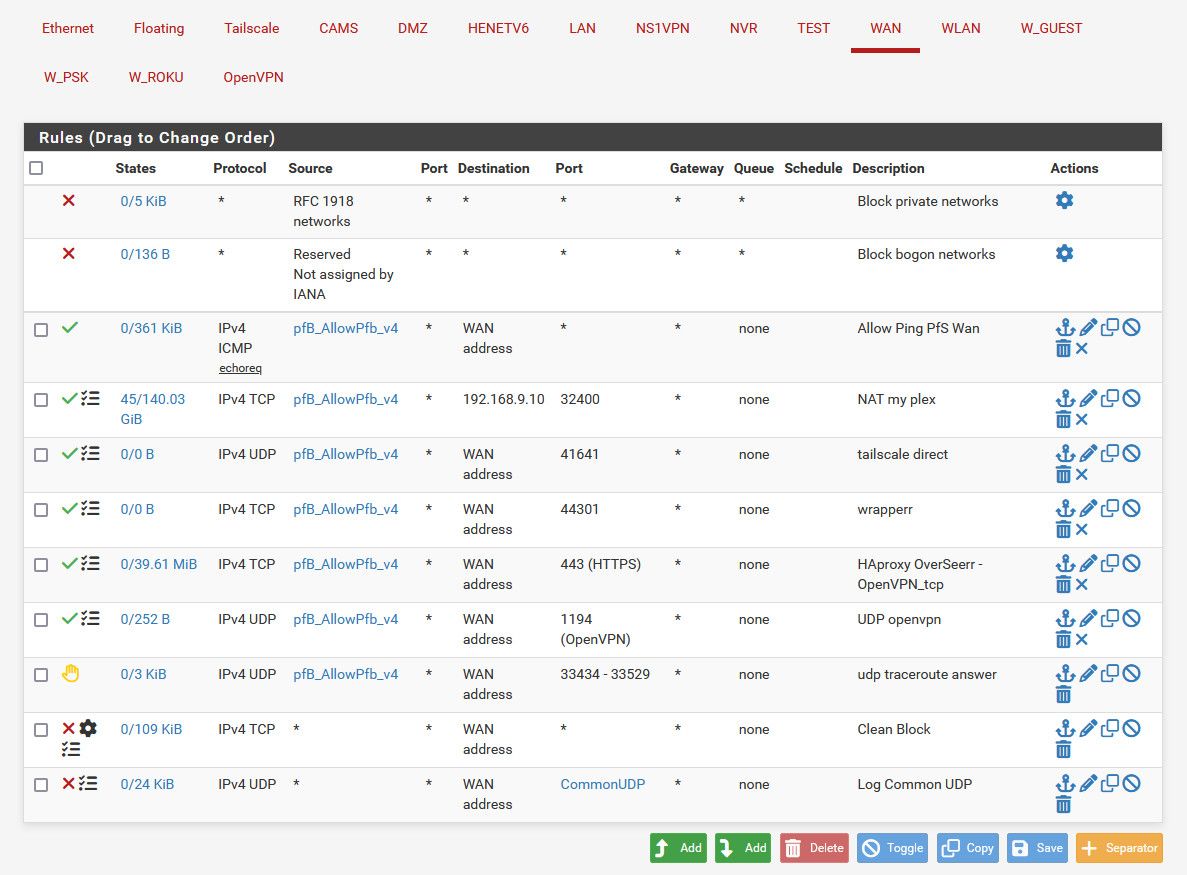
I have some floating rules as well that block stuff before it even gets to my wan rules - shodan IPs, Digital Ocean IPs, some other known scanner networks.. Have zero desire for any of my ports that I do have open to end up in some db somewhere - all that could ever do is attract more noise.
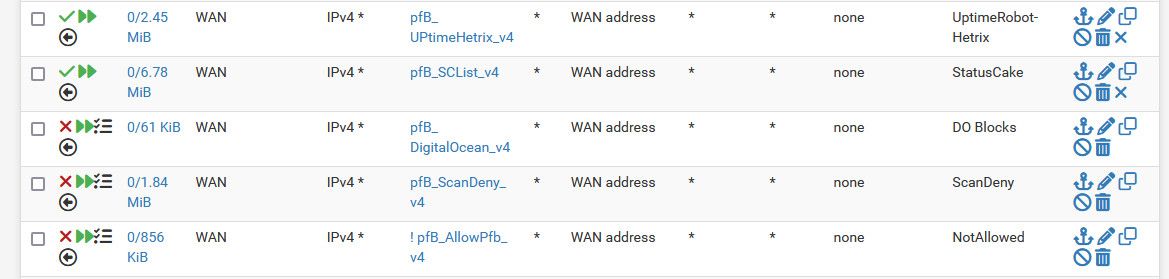
-
@johnpoz Thanks for posting that.
Doesn't this generate a lot of log entries?
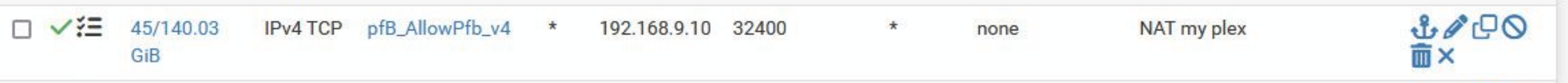
Or is there some way to only log initial packets?

Which advanced settings are enabled for this one? Maybe a screen shot if possible? Define clean block?What do you consider CommonUDP ports?
I too have a number of block lists for inbound. Only inbound traffic for now is tcp/25 and a small block of ~50 upper range udp ports that get forwarded the to voip server for RTP media. I limit that to north american IP's only as there are no none NA calls ever made. This is to satisfy anveodirect who doesn't proxy RTP traffic.
Fortunately floating rules take precedence before the port forward interface firewall rule. This minimizes noise and spam received at the mail server. Default block logging is disabled as im generally not interested what I consider internet noise. But your logging options may be of interest.
The above is interesting; according to https://docs.netgate.com/pfsense/en/latest/nat/process-order.html, port forwarding/nat gets processed before floating/firewall rules. Perhaps one interpretation of this is the port forward (with respect to inbound traffic) is indeed processed before the firewall rules, but then any firewall rules associated with that get processed based on firewall rule processing priority?
-
@GPz1100 only the initial allowed is log - it doesn't log all the traffic.
Here is the setting for only logging syn, in the advanced options part of the rule
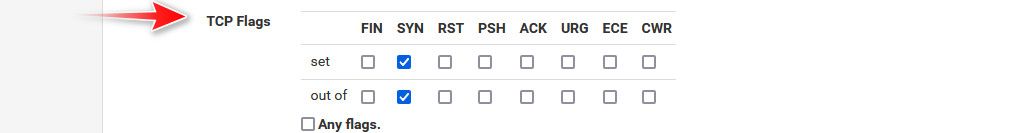
As to common udp ports - those are just in an alias
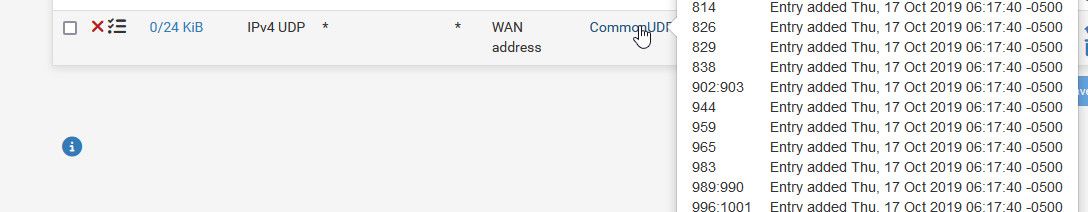
I created that alias quite a few years ago as you can see.. I just did some research on common udp ports.. That rule you can see doesn't really log much. 856KB since most likely when I updated to 24.11 and the counters reset.
Yes port forwards are evaluated first, but there has to be a firewall rule to allow the traffic. If I didn't put in the specific block, then the traffic I don't want to see that my port is open would be allowed.. For example I pretty much allow any IP in the US, and currently Belgium because I have some family living there currently.
But I sure don't want a shodan IP to get to that port, so while my port forward might allow that - my block in floating doesn't so they never see that port open.
Once I started blocking the scanners and such - I don't really see a lot of hits on my clean block any more.
here is example of one of those scanners being blocked - sketchoid
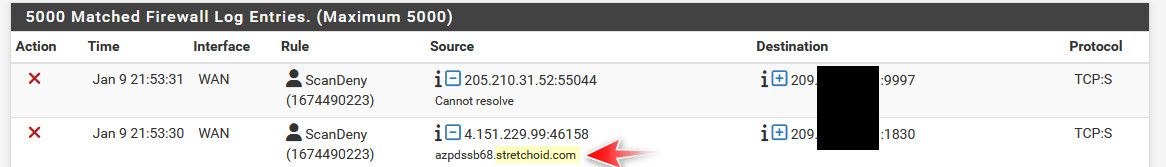
I don't have that port open anyway - but there is zero reason to answer them if they happen upon a port I do have open..
That first IP there is owned by Palo Alto Networks, they have scanners searching the net as well for open ports.. They have zero reason to see mine ;) You are suppose to be able to get on their no scan list, but have had little luck with those - so I just block their IPs.. Scan your customers that want that service - have zero reason for my IP to get put into your db that I have a port open on X.
Also when you have specific rules that block specific things, other than just anything like the default deny - its easier to filter to look for specific things.. And you know you can bump what does get shown in your gui to more lines - notice mine is 5000 entries.. So with ability to filter, and more entries its easier to keep an eye on your log. If you are really curious, you could send them to a syslog - and then you can get really fancy with all kinds of stuff - what geo location are most of your blocks coming from with bigger blobs on a graph, etc.. It can be some interesting eye candy - I ran such a setup for a while - but then got board with having to run the resources on a vm to provide what amounts to nothing more than eye candy.
-
@johnpoz I'm still digesting your post.
You got me curious about stretchoid. I haven't seen any hits in the email server from them for some time (many months). Was trying to find which list was blocking it but unsuccessful.
DO is already blocked at ASN level.
-
@GPz1100 said in Question Regarding Default Deny Rules:
stretchoid
maybe you opted out?
https://stretchoid.com/
But those seem to never work - so I just block their IPs.
-
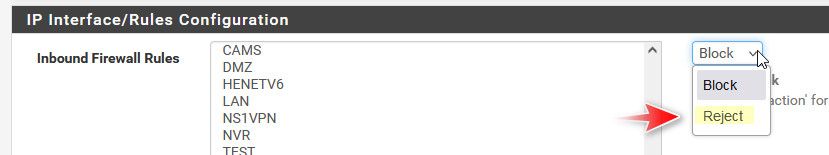
I have noticed that the pfblocker fw rules all show up as rejected instead of blocked. Any idea why? I was thinking that a block would be better than sending a response back. I could certainly be wrong but I was wondering why it was reject and not block.
-
@djtech2k because you set them that way? Personally I don't use any sort of auto rules in pfblocker - I just use it to create aliases that I then use in my own rules.
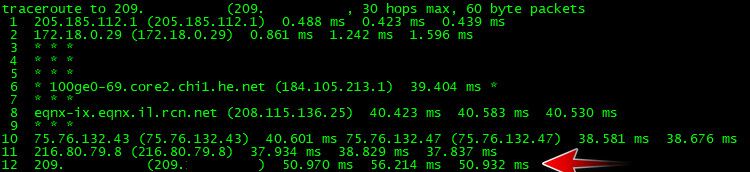
Yeah its not good practice to send reject external, its fine locally and can save some retrans that client will do if it just doesn't get an answer.. Only time you would want to send reject is like in my rules and the ability to traceroute through/to pfsense, etc. To see the hop that is pfsense you would need to send the reject.
See if I do a traceroute to my IP from out on the internet (vps of mine) the last hop which is my IP answers
-
This post is deleted! -
I just went back and looked and it shows pfblocker sets Block as the default for Inbound rules and Reject for outbound rule. I guess I was thinking it was reject on WAN, which did not make sense to me. I get it now.
-
@djtech2k yeah I was going to say - a reject on local would make sense as default..
If device on your network wants to go to somethingblocked, might as well reject it - or he just going to retrans multiple times wanting an answer back from where he wanted to go.
If you tell him right away - hey you not going there, then it shouldn't spend any time doing retrans.