Question Regarding Default Deny Rules
-
@johnpoz On the topic of ipv6/pf, is there a way to have blacklist a mac from receiving an ipv6-RA?
The use case would be some android clients which expose no ipv6 config options.
The only way that comes to mind would be to enable ethernet filtering, then set up a rule to block ipv6 ethertype traffic to/from that given mac.
-
Mmm, I'm not aware of anything else. That would probably work though.
-
I have been tuning my rules to calm the noise and its working. Now I am seeing a high percentage of the log is incoming WAN traffic on UDP. For example, I see incoming WAN traffic from a Facebook IP using UDP. Its more than just FB but thats an example that repeats a lot. I know I can block the logging if its noise but I was just curious if anyone else sees that kind of traffic also. Incoming UDP traffic kind of surprises me from something like Facebook.
-
@djtech2k yes there is tons of noise on the internet - why do you think I turned off the default deny... I log incoming syn, and interesting udp ports..
And log the allow rules I want to log..
-
@johnpoz Can you show a screen shot of what your inbound rules look like?
-
@GPz1100 on my wan sure
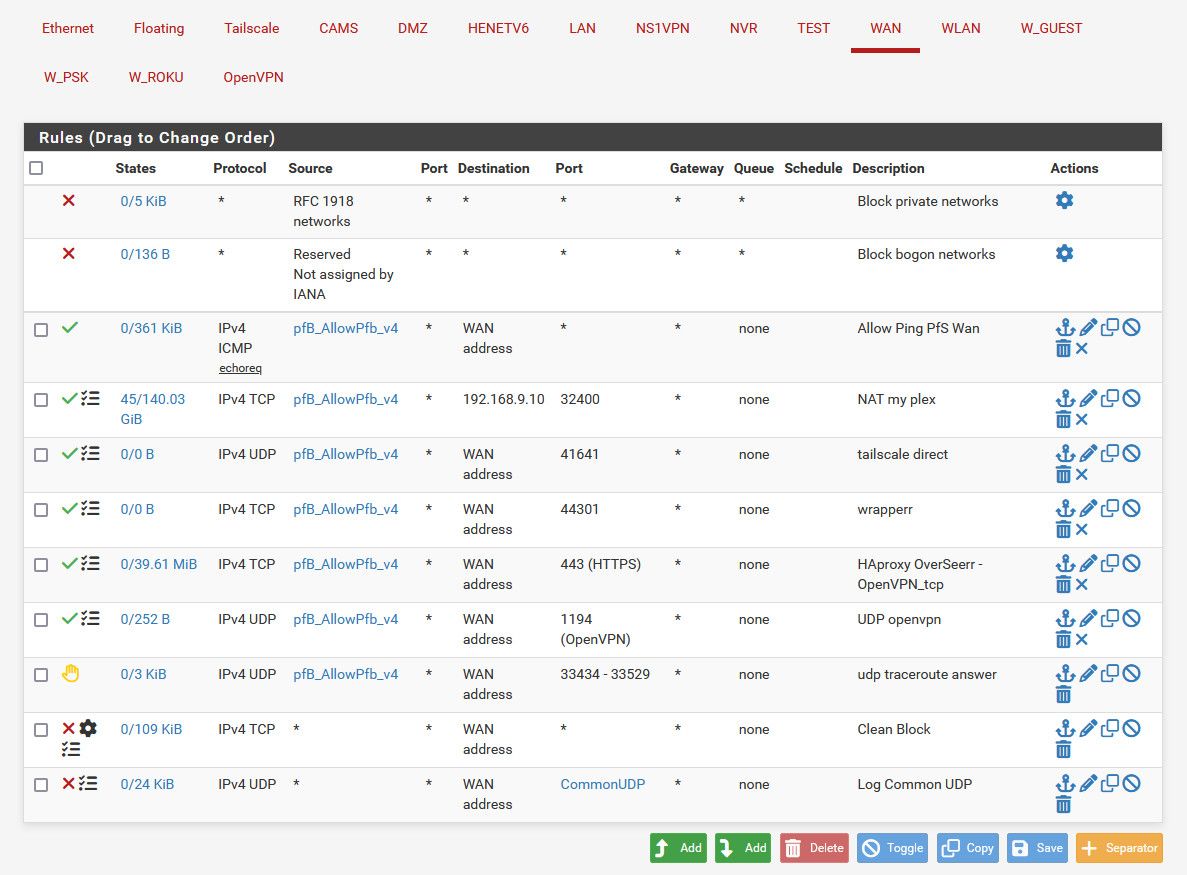
I have some floating rules as well that block stuff before it even gets to my wan rules - shodan IPs, Digital Ocean IPs, some other known scanner networks.. Have zero desire for any of my ports that I do have open to end up in some db somewhere - all that could ever do is attract more noise.
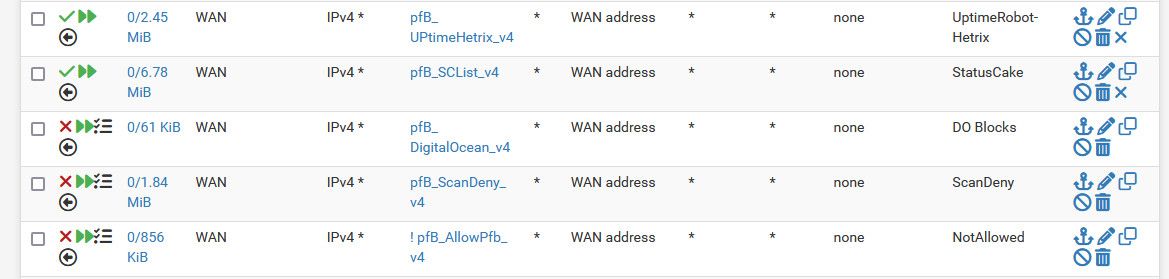
-
@johnpoz Thanks for posting that.
Doesn't this generate a lot of log entries?
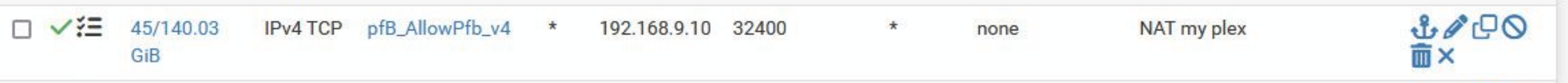
Or is there some way to only log initial packets?

Which advanced settings are enabled for this one? Maybe a screen shot if possible? Define clean block?What do you consider CommonUDP ports?
I too have a number of block lists for inbound. Only inbound traffic for now is tcp/25 and a small block of ~50 upper range udp ports that get forwarded the to voip server for RTP media. I limit that to north american IP's only as there are no none NA calls ever made. This is to satisfy anveodirect who doesn't proxy RTP traffic.
Fortunately floating rules take precedence before the port forward interface firewall rule. This minimizes noise and spam received at the mail server. Default block logging is disabled as im generally not interested what I consider internet noise. But your logging options may be of interest.
The above is interesting; according to https://docs.netgate.com/pfsense/en/latest/nat/process-order.html, port forwarding/nat gets processed before floating/firewall rules. Perhaps one interpretation of this is the port forward (with respect to inbound traffic) is indeed processed before the firewall rules, but then any firewall rules associated with that get processed based on firewall rule processing priority?
-
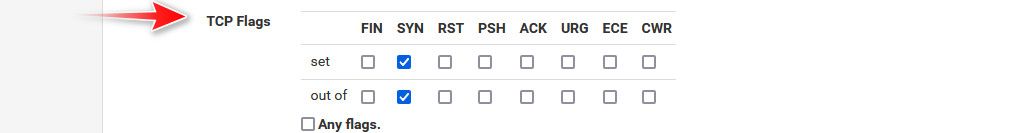
@GPz1100 only the initial allowed is log - it doesn't log all the traffic.
Here is the setting for only logging syn, in the advanced options part of the rule
As to common udp ports - those are just in an alias
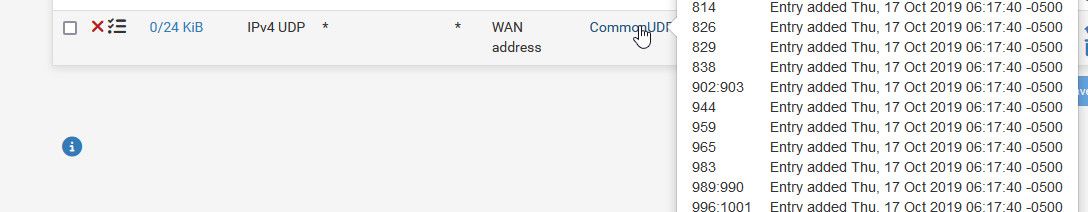
I created that alias quite a few years ago as you can see.. I just did some research on common udp ports.. That rule you can see doesn't really log much. 856KB since most likely when I updated to 24.11 and the counters reset.
Yes port forwards are evaluated first, but there has to be a firewall rule to allow the traffic. If I didn't put in the specific block, then the traffic I don't want to see that my port is open would be allowed.. For example I pretty much allow any IP in the US, and currently Belgium because I have some family living there currently.
But I sure don't want a shodan IP to get to that port, so while my port forward might allow that - my block in floating doesn't so they never see that port open.
Once I started blocking the scanners and such - I don't really see a lot of hits on my clean block any more.
here is example of one of those scanners being blocked - sketchoid
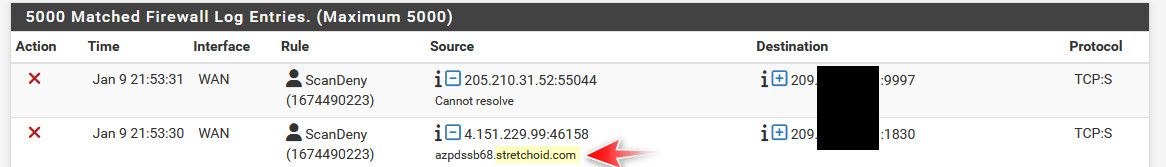
I don't have that port open anyway - but there is zero reason to answer them if they happen upon a port I do have open..
That first IP there is owned by Palo Alto Networks, they have scanners searching the net as well for open ports.. They have zero reason to see mine ;) You are suppose to be able to get on their no scan list, but have had little luck with those - so I just block their IPs.. Scan your customers that want that service - have zero reason for my IP to get put into your db that I have a port open on X.
Also when you have specific rules that block specific things, other than just anything like the default deny - its easier to filter to look for specific things.. And you know you can bump what does get shown in your gui to more lines - notice mine is 5000 entries.. So with ability to filter, and more entries its easier to keep an eye on your log. If you are really curious, you could send them to a syslog - and then you can get really fancy with all kinds of stuff - what geo location are most of your blocks coming from with bigger blobs on a graph, etc.. It can be some interesting eye candy - I ran such a setup for a while - but then got board with having to run the resources on a vm to provide what amounts to nothing more than eye candy.
-
@johnpoz I'm still digesting your post.
You got me curious about stretchoid. I haven't seen any hits in the email server from them for some time (many months). Was trying to find which list was blocking it but unsuccessful.
DO is already blocked at ASN level.
-
@GPz1100 said in Question Regarding Default Deny Rules:
stretchoid
maybe you opted out?
https://stretchoid.com/
But those seem to never work - so I just block their IPs.
-
I have noticed that the pfblocker fw rules all show up as rejected instead of blocked. Any idea why? I was thinking that a block would be better than sending a response back. I could certainly be wrong but I was wondering why it was reject and not block.
-
@djtech2k because you set them that way? Personally I don't use any sort of auto rules in pfblocker - I just use it to create aliases that I then use in my own rules.
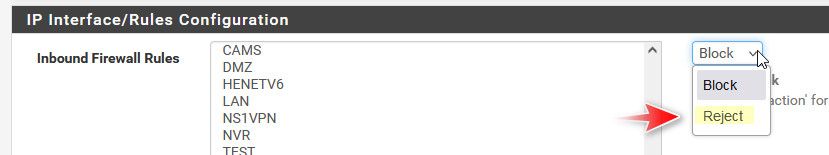
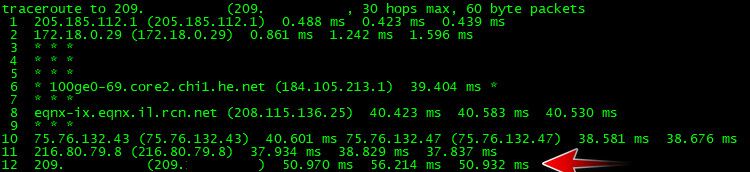
Yeah its not good practice to send reject external, its fine locally and can save some retrans that client will do if it just doesn't get an answer.. Only time you would want to send reject is like in my rules and the ability to traceroute through/to pfsense, etc. To see the hop that is pfsense you would need to send the reject.
See if I do a traceroute to my IP from out on the internet (vps of mine) the last hop which is my IP answers
-
This post is deleted! -
I just went back and looked and it shows pfblocker sets Block as the default for Inbound rules and Reject for outbound rule. I guess I was thinking it was reject on WAN, which did not make sense to me. I get it now.
-
@djtech2k yeah I was going to say - a reject on local would make sense as default..
If device on your network wants to go to somethingblocked, might as well reject it - or he just going to retrans multiple times wanting an answer back from where he wanted to go.
If you tell him right away - hey you not going there, then it shouldn't spend any time doing retrans.