Apply persistent standard log filter
-
Hi pfSense gurus!
First of all, I am not sure if it's really possible what I want to achieve, but that's the reason I am putting my question here

Problem description:
- I use Check_MK to monitor my home infrastructure. Part of the monitoring is my pfSense firewall. Amongst other services I check if the SSH daemon is running on pfSense. This is a standard check of Check_MK which is performed every 1min.
- Each check is logged in pfSense (Status / System Logs / System / General) and gives me the following entry:
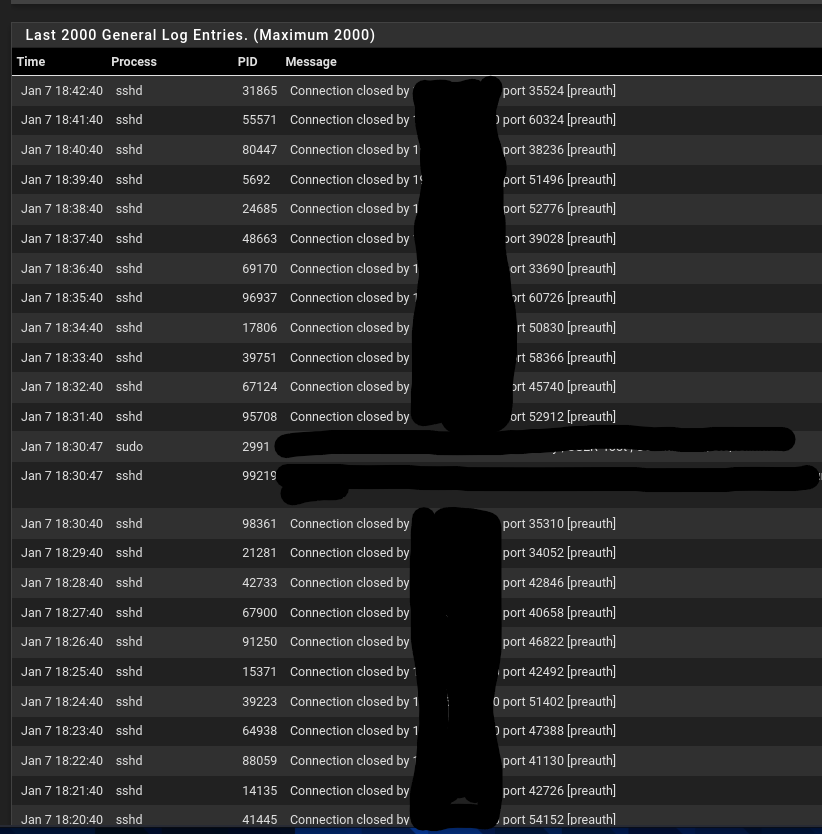
Jan 7 18:42:40 sshd 31865 Connection closed by <IP-of-Check_MK-server> port xxxxxx [preauth]- As those entries completely flood the the logs, I need to filter the logs manually by excluding the above message in order to get a readable log file (Message filter: !Connection closed by <IP-of-Check_MK-server> port)
Question:
Is there a "reasonable way" in pfSense to PERMANENTLY define a sort of standard filter for the logs in order to exclude exactly those sshd-message from that specific Check_MK client?Cheers!
-
No, there is no way to exclude those entries from the logs selectively as far as I know.
-
@LaUs3r said in Apply persistent standard log filter:
Is there a "reasonable way"
Sure.
What about not starting up a SSH login sequence ?
You could also check if the SSH daemon is running.SSH logging a line in the system logs is part of the security, as you really want to see if 'some' is trying to logging.
Btw : seriously : every minute ?
edit :
You asked for it.
This : https://man.freebsd.org/cgi/man.cgi?query=syslog.conf&sektion=5&manpath=freebsd-release-ports tells you what you want to know.The details are here : https://man.freebsd.org/cgi/man.cgi?query=syslog.conf&sektion=5&manpath=freebsd-release-ports#PROPERTY-BASED_FILTERS
and because we shouldn't even trust the manual, let's check the source :
https://github.com/freebsd/freebsd-src/blob/cad1d13af789b82d829923795cccbf37cdf93b51/usr.sbin/syslogd/syslogd.c#L2767
( I'm still not sure that this is, line per line, the syslogd binary that is compiled, build and present in our pfSense .... I'll leave that up to you ^^ )so now we know that messages can get filtered (discarded) using the good old 'grep'.
So ....
Open /etc/syslog.conf :# Automatically generated, do not edit! # Place configuration files in /var/etc/syslog.d !* include /var/etc/syslog.d # /* Manually added files with non-conflicting names will not be automatically removed */so the solution is this : create a file like
msg, contains, ".*Connection closed by authenticating.*"and call it assh.conf
and place it in /var/etc/syslog.d/
and restart syslog.That's it.
Start your ssh client, connect to pfSense, don't do anything, don't login, just close the ssh client.
Normally, you should see a line like this in the system log :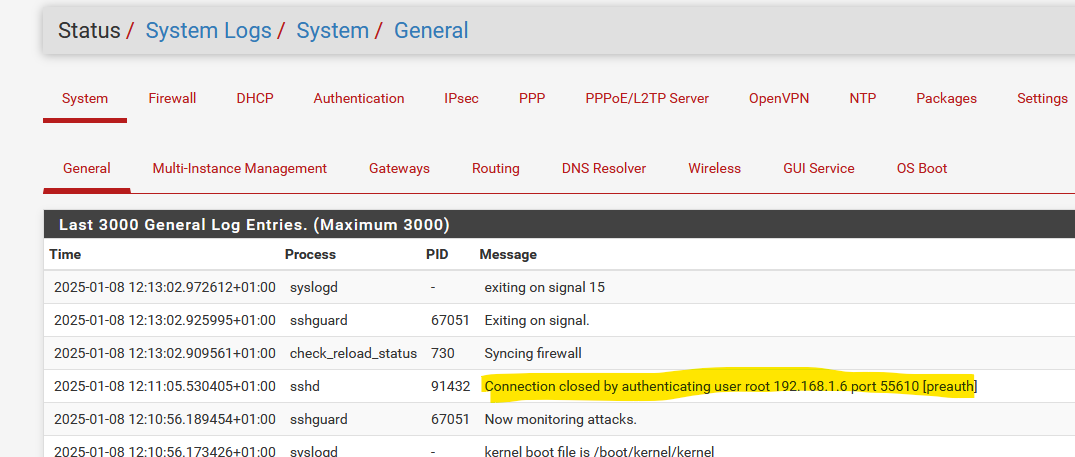
but now, you see nothing.
I advise you strongly not to use the 'grab all' like this
".Connection closed by authenticating."Change it to something like this :
".Connection closed by authenticating user root 192.168.1.6."where 192.168.1.6 is the IP your testing from.
but add the IP you use to test the SSH access, so only log lines from this IP get discarded.
Whatever you decide : IMHO, this can create a security issue, as all SSH access tried from this IP will be unnoticed by the sshguard process ....
If something goes wrong, delete the assh.conf file, restart syslog, and you'll be back to square one.
-
@Gertjan , thx very much. I was looking in the wrong direction obviously.
I tried your suggestion and also did searches in the FreeBSD forums, but somehow the messages are not suppressed.
I managed to set the filter correctly to re-route the log messages to another file for example.Any hints what might be wrong with the additional syslog-file?
:msg, contains, "Connection closed by xxx.xxx.xxx.xxx port"--> no success
I tried:
:msg, !contains, "Connection closed by xxx.xxx.xxx.xxx port"--> no success
The redirect to another file works:
:msg, contains, "Connection closed by xxx.xxx.xxx.xxx port" *.* /var/log/other.log--> the message are written to the other log file, but still appear in the pfSense GUI
If I use the ".value." as you recommended and which is also in the official man pages, the filtering does not work at all. Removing .* works.
-
@LaUs3r said in Apply persistent standard log filter:
:msg, contains, "Connection closed by xxx.xxx.xxx.xxx port"
Didn't work for me neither.
This was working :
msg, contains, ".*Connection closed by authenticating.*"I removed the starting ':' and used grep style wildcard '.*'
I'm using 'syslog' for many years now :
On my MOOS ::msg, contains, "(root) CMD (/usr/local/rtm/bin/rtm 25 > /dev/null 2> /dev/null)" ~ :msg, contains, "(/usr/local/rtm/bin/rtm 30" ~ :msg, contains, "closed by 127.0.0.1 [preauth]" ~ :msg, contains, "connect from localhost.localdomain[127.0.0.1]" ~ :msg, contains, "disconnect from localhost.localdomain[127.0.0.1]" ~ :msg, contains, "pam_unix(cron:session): session closed for user root" ~ :msg, contains, "pam_unix(cron:session): session opened for user root by (uid=0)" ~ :msg, contains, "pam_unix(cron:session): session opened for user www-data by (uid=0)" ~ :msg, contains, "pam_unix(cron:session): session opened for user munin by (uid=0)" ~ :msg, contains, "pam_unix(cron:session): session closed for user www-data" ~ :msg, contains, "pam_unix(cron:session): session closed for user munin" ~ :msg, contains, "Disconnected, ip=[::ffff:127.0.0.1]" ~ :msg, contains, "Connection, ip=[::ffff:127.0.0.1]" ~Most of the 127.0.0.1 are there for the same reason as why you were looking to suppress log lines : these come from my 'munin' that test for running processes by connecting to it.
That said, my test interval I uses is already a sickening "5 minutes" ^^ and these test scripts create a lot of useless log lines. For example, I know who "127.0.0.1" is and normally 127.0.0.1 wouldn't attack my server as it is .... my server. So no security risk in my case afaik.Keep in mind that the snippet shown is from a Debian 15 (== MOOS) syslog system, not a feebsd syslog, so the congratulation might be somewhat different.
-
Mmm, interesting! Does that not get overwritten if you make any change to the logging in he gui though?
-
@Gertjan said in Apply persistent standard log filter:
Btw : seriously : every minute ?
I feel the same way - that seems overly chatty to me, how about every 10 minutes or better yet once an hour.. To be honest I don't recall ssh ever going down on pfsense.. Connectivity sure I have broken my switch config before, I even locked myself out of it before I added my IP to the login protection bypass.
But I don't recall it ever just crashing or something.
-
@stephenw10 said in Apply persistent standard log filter:
Mmm, interesting! Does that not get overwritten if you make any change to the logging in he gui though?
You mean : removed ?
See the pfSense 'core' syslog config file /etc/syslog.conf :# Automatically generated, do not edit! # Place configuration files in /var/etc/syslog.d !* include /var/etc/syslog.d # /* Manually added files with non-conflicting names will not be automatically removed */the last line

the file I proposed has to be added to the /var/etc/syslog.d/ folder.
A system re install, or may an upgrade will clean out the /var/etc... but for me, it's still there after many syslog restarts. -
Thx for the replies guys.
I got the right syntax figured out now which is to use a "!" in order to suppress certain log messages.
Example:
:msg, !contains, "Connection closed by xxx.xxx.xxx.xxx port"The working example I used is this:
/var/etc/syslog.d/myssh.conf!sshd :msg, !contains, "Connection closed by xxx.xxx.xxx.xxx port" *.* /var/log/myssh.logThis logs now everything related to the sshd except the above defined string.
Eventually, I am pretty sure that this will not work with pfSense.
The reason for this is that the automatically created pfSense log config (based on the GUI) is also stored in the same dir: /var/etc/syslog.d/pfSense.confIn this config, all auth message are logged:
# Automatically generated, do not edit! !* auth.*;authpriv.* /var/log/auth.logChanging this is not possible as all changes are reverted once the syslogd is restarted. Therefore all sshd activities will be logged despite what is defined in additional config files in /var/etc/syslog.d/
Regarding the Check_MK check interval of 1min:
this is the default check interval for the active checks. To change this of a single check is not possible to my knowledge, but only for ALL active checks for a dedicated host. But maybe this is the way to investigate for me.Appreciate the help here!
-
@LaUs3r said in Apply persistent standard log filter:
Eventually, I am pretty sure that this will not work with pfSense.
I'm less sure ^^ (and more positive)
The files in /var/etc/syslog.d/ are parsed one by one during syslog startup, and the instruction are build from the files that syslog found.
If the pfSense.conf file, build by pfSense is read first, and then your file, mssh.conf, that the settings were set in the correct order, and the last one wins ^^
No you know why I named it assh.conf.
If files are read in in alphabet order. As we have the source code that can be checked.
Or, if the files are read in one by one on a physical order in the folder, then delete both files.
Put your mssh.conf in place, and then restart syslog, so pfSense.conf will get build, and that file will have the second physical position.I leave my version of the syslog filtyer in place, where I filter out the less usefull
I well leave this message in place :
just to be sure, and that I know that sshgaurd restarted again.
Will post back here after a week or so, to see it it will stay in place.
Tip : Install the Notes pfSense package. Add a note : the file, then content and the reason why you made this system edit. If you have to re install pfSense, (and you have always a backup of the config, right ;) ) you know what to do without the need of recalling all the details..
-
@Gertjan , thx again very much for you input.
Still it does not work.
I removed the pfSense.conf file, created a assh.conf with different content, but eventually I still get the log entries.
At least I manged now to change the check interval, so that I only get the log entry every 1h
-
Strange.
I've created a "a;conf" with :
!sshguard :msg, contains, ".*Exiting on signal.*" ~( No !, and I've added the ~ )
and restated the syslog daemon.
No more
for me.