How to ensure continued connectivity when LAN interface on primary unit goes down?
-
If LAN interface on primary unit is down, and backup unit CARP status for that interface becomes MASTER, but primary unit's WAN interface is still in MASTER status, how does sNATing to WAN VIP work? Is there a way to tell pfsense to make backup unit MASTER for all interfaces?
-
@mike_vc said in How to ensure continued connectivity when LAN interface on primary unit goes down?:
If LAN interface on primary unit is down, and backup unit CARP status for that interface becomes MASTER
All other interface should follow then. So all interfaces on the primary should go into backup status.
If this is not the case, something is wrong in your setup.
Ensure that the WAN interfaces of both nodes can reach each other on layer 2. -
@viragomann
I did a sanity check. Confirming that my my reality contradicts your assertion, unless I am missing some piece of configuration. In which case, why is this not the default?
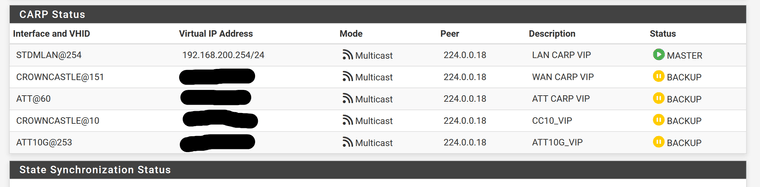
The screenshot above is from the backup unit.When I unplugged LAN interface on the primary unit, I lost connectivity from devices on the LAN to the internet, but could still ping the LAN vip, indicating that the backup unit took over that IP.
My understanding is that it takes over the LAN ip, but the WAN IPs - therefore incoming packets addressed to the WAN VIP IPs, if port forwarded to hosts on the LAN, never reach their destinations, because they end up the primary unit, whose LAN interface isn't active, and my backup unit is not able to NAT outbound packets to WAN VIP IPs because it still considers itself BACKUP for those.
Hoping someone from Netgate can weigh in!
-
@mike_vc
You properly have a network problem on the WANs as mentioned.Go through Troubleshooting High Availability to investigate the problem.
-
@viragomann
This isn't helpful. Of course I have gone through the HA troubleshooting - this problem isn't mentioned on there. I setup HA and CARP according to the Netgate cert training.
There isn't a problem on WANs, because if I unplug one of the WAN interfaces, I can see the backup unit assume MASTER role for that interface. I think you might have misread the problem I described.
The problem is consistent, and it's not with the devices sensing when an interface is down on the primary unit. It is with the backup device NOT assuming MASTER status for all interfaces while the LAN is down. This can be easily reproduced - try it. -
I used to have this issue too, so on every new firewall I setup, I always make sure to add the following values under System, Advanced, System Tunables:
net.inet.carp.preempt 1
net.inet.carp.ifdown_demotion_factor 240Also, make sure that the primary firewall's CARP skew is 0, and the backup firewall's CARP skew is 100.