Allow only ssh login for admin
-
When you login to the admin user via ssh you end up in the root user, correct? Is it possible to enable SSH login via public key for the admin user?
-
@CatSpecial202 have a look at the documentation:
https://docs.netgate.com/pfsense/en/latest/recipes/ssh-access.html#ssh-keys
"When the SSH daemon is set for key-based authentication, it uses the keys defined on user accounts. Add keys to individual user accounts under System > User Manager. The admin user and root user share keys."
-
You can set ssh to key based only but not set that per user. Unless I missed a change at some point.

-
@stephenw10 So, just don't provide an SSH key to the users. Only provide the admin/root account with an ssh key. Then grant only public key auth.
I was thinking something like disabling the admin user from logging into the system like clicking the option below, but granting some permission somewhere that would allow the admin to only login via key based auth via ssh? I want to disable GUI login for the admin and allow only SSH login. Is that possible?
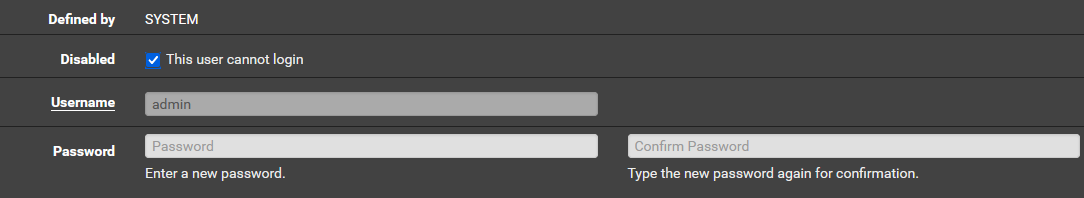
-
Not as far as I know.
If you disable login there it will disable SSH login too.
What you can't do with SSH is force admin to use a key whilst allowing some other user to login with a password. The option to set the login type applies to all users.
-
@CatSpecial202 said in Allow only ssh login for admin:
Is it possible to enable SSH login via public key for the admin user?
Not only possible. Its imho pretty mandatory.
Any every server device you use, rent, buy create, uses initially a SSH connection, and the admin (mostly root) + password is send to you.
Or you created these when installing the OS.Os soon as you enter the first time, you create cert. Export the public part to yoruself, so you can use it with your SSH client, for example Putty.
The 'admin' user on pfSense should have this part :
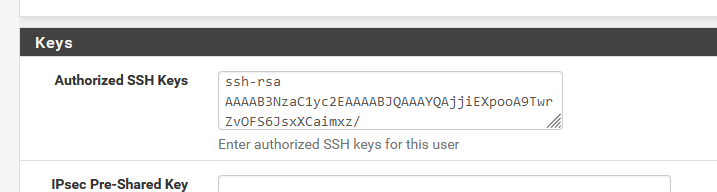
and then you select (again : pfSense) :
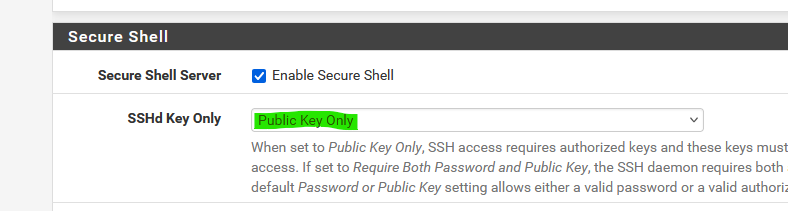
and from now on, your SSH client will be needing the exported cert to be able to connect to pfSense :
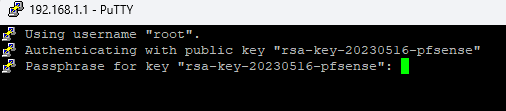
and I have to type in the password == passphrase of the cert, not the admin password.
Do this with pfSense, and any other device you can connect to over SSH - if possible.
edit : don't even bother grating other users access to pfSense with non admin accounts.
pfSense is a router, not some multi media file server.
I always recommend severely creating an ssh admin pfSense so you can have access, when needed.
Some will then never really use it afterwards.
Other - like me - use it several times a day. As I use the same connection with for example WinSCP, so I can explore the file system, and look at things like using Windows explorer. Don't ask me why ^^If needed, block the SSH port TCP 22 to some known LAN IPs.
Lock your own devices, the ones you can use to connect to pfSense, with a DHCP MAC lease, so from now on they will always have the same IP.
Throws these IPs in a Alias.*Use this Alias to create a LAN firewall rule.
From now on, only these IPs can use the pfSense SSH port.Read security nerds will use a dedicates admin LAN, and connect to this LAN with their device to access pfSense SSH.
Now lock your pfSense into a safe. Lock the safe. Done. Now you're close to what they use at Langley.