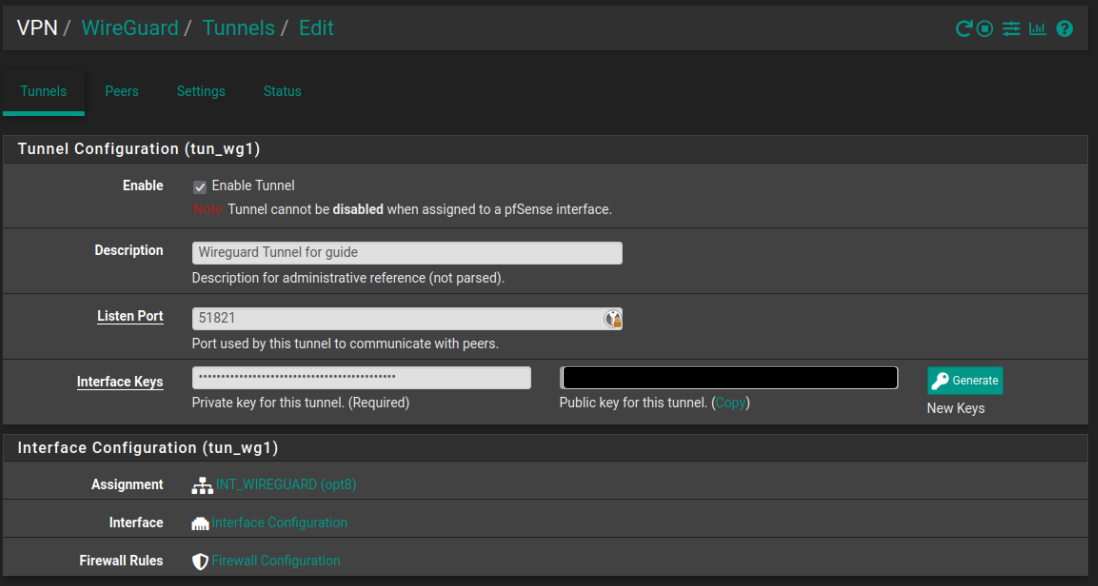
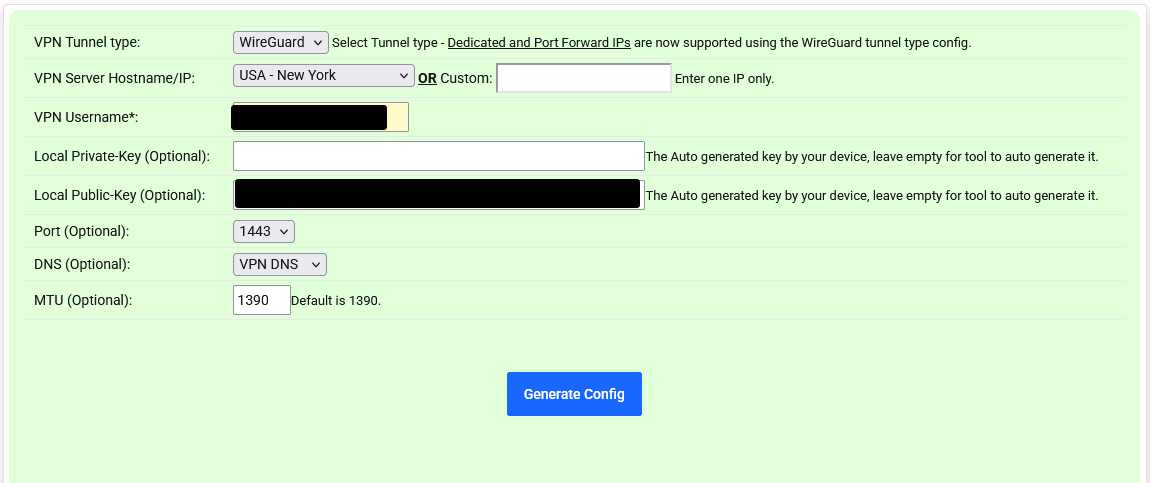
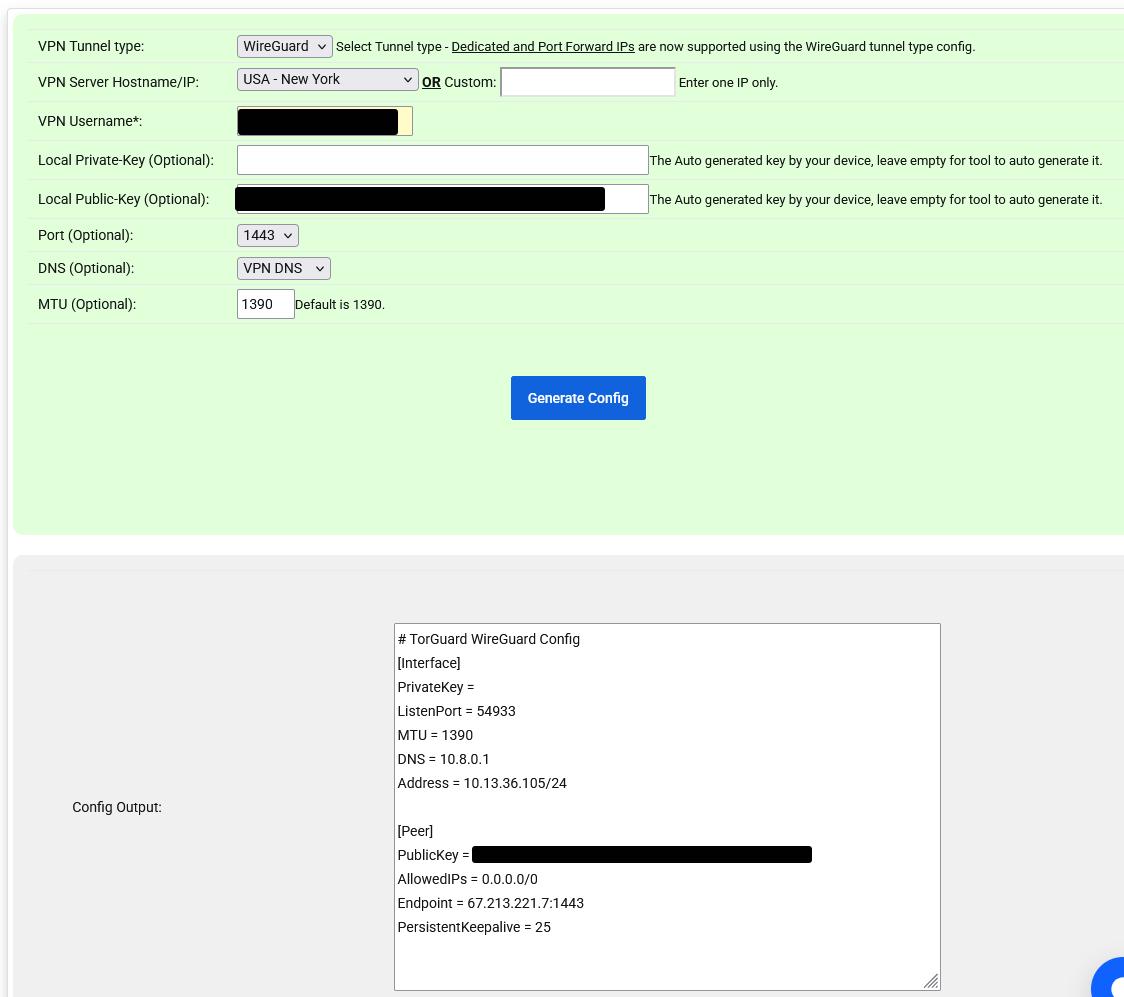
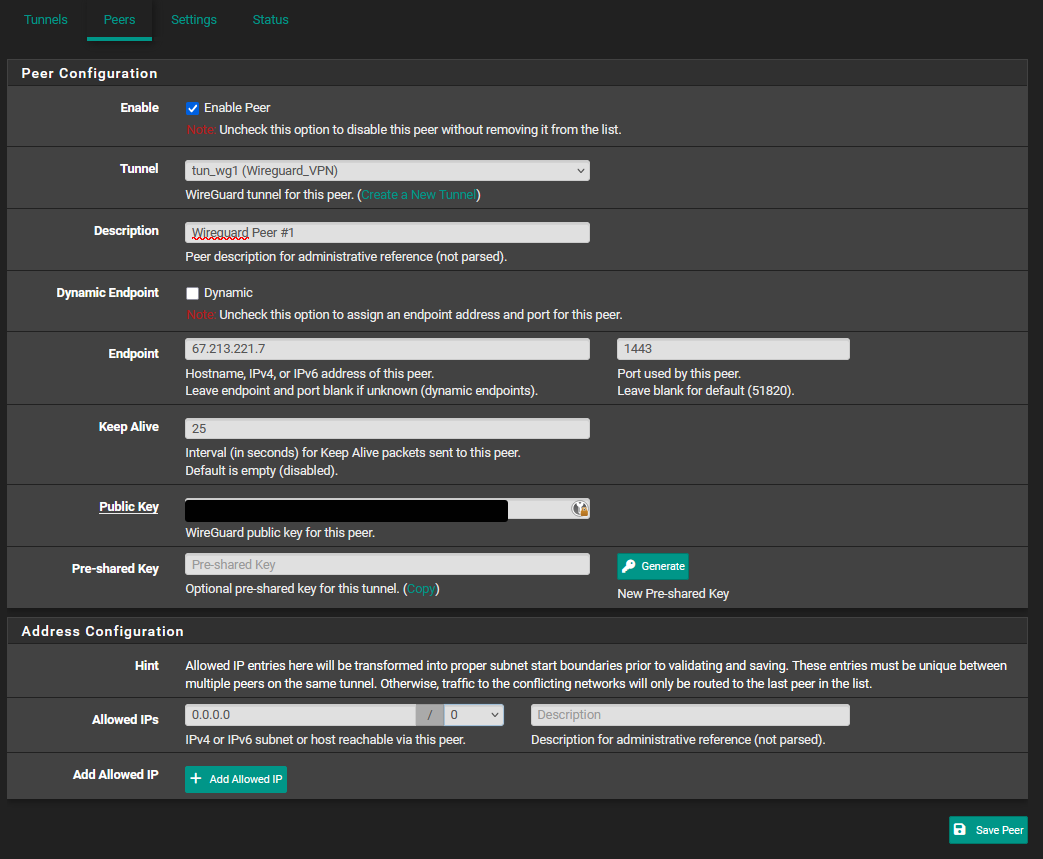
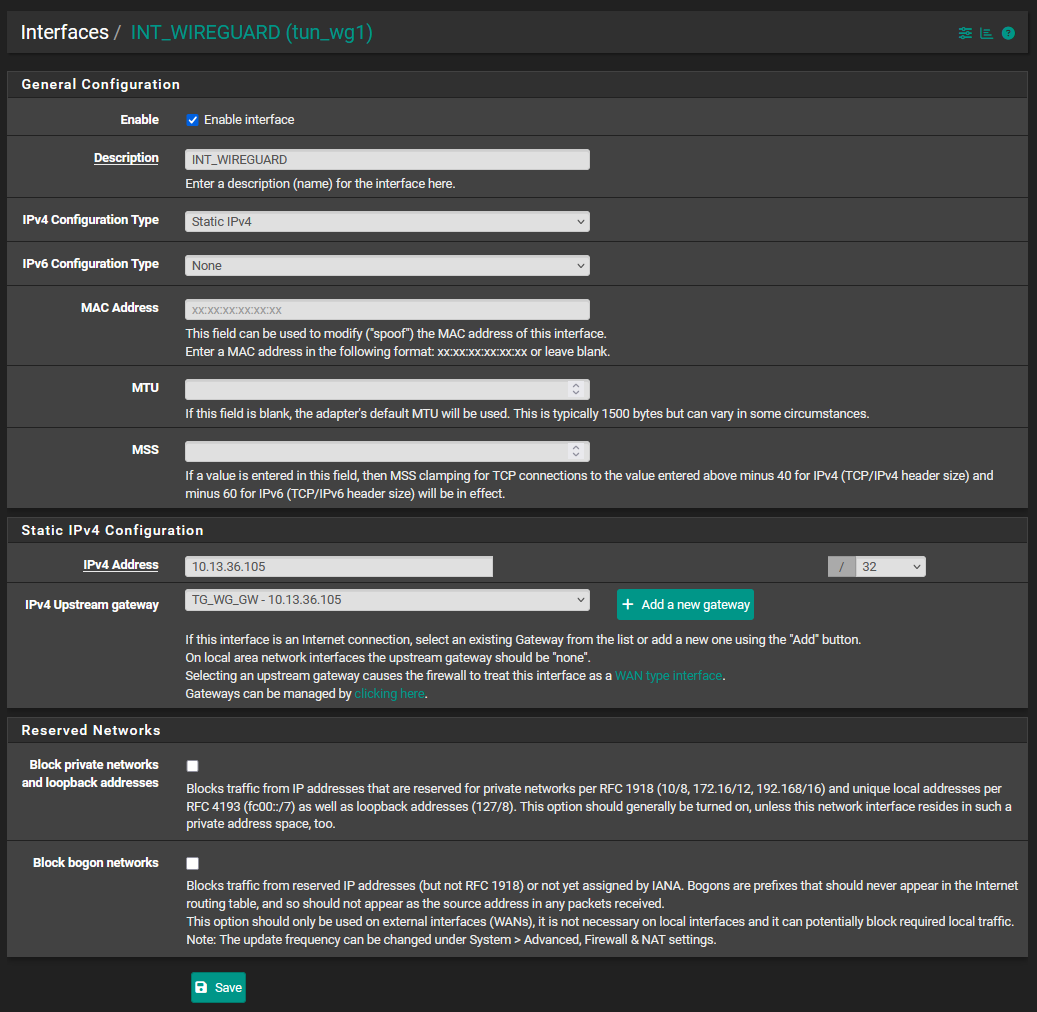
[Guide] Setup a wireguard tunnel to VPN provider (multiple VPN tunnel setup)
-
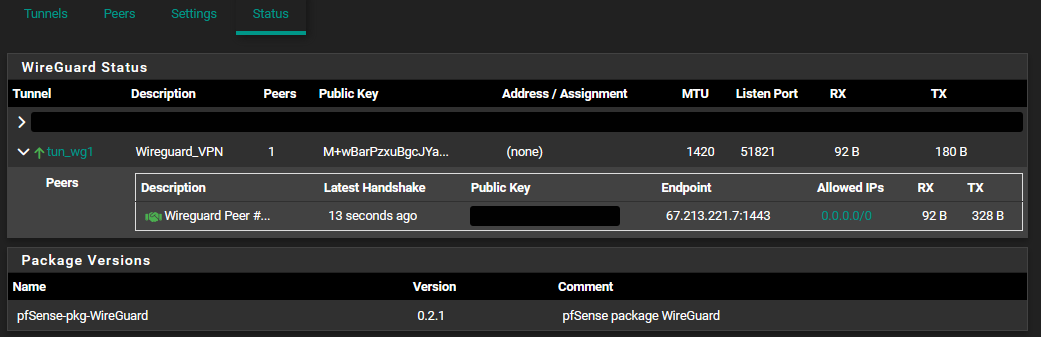
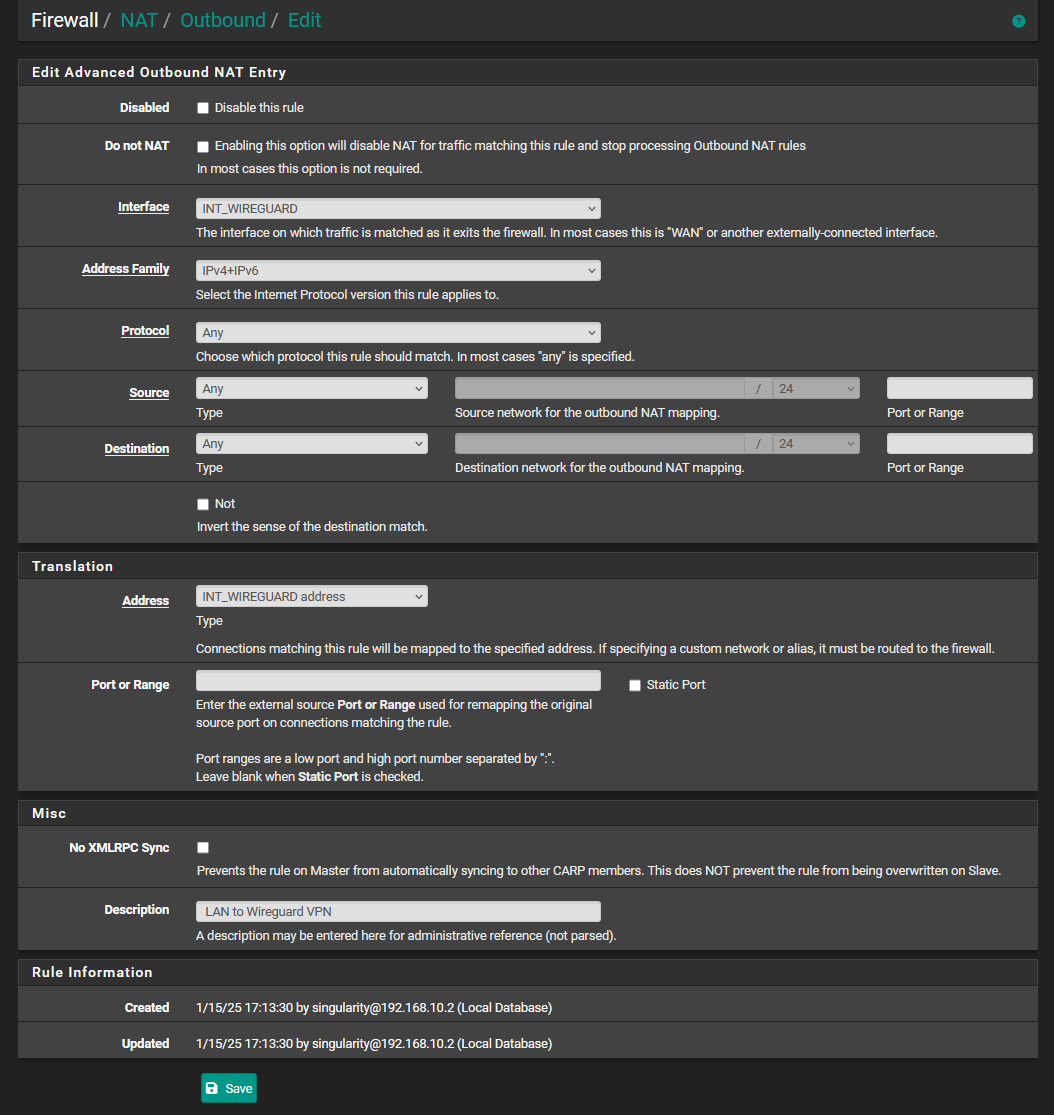
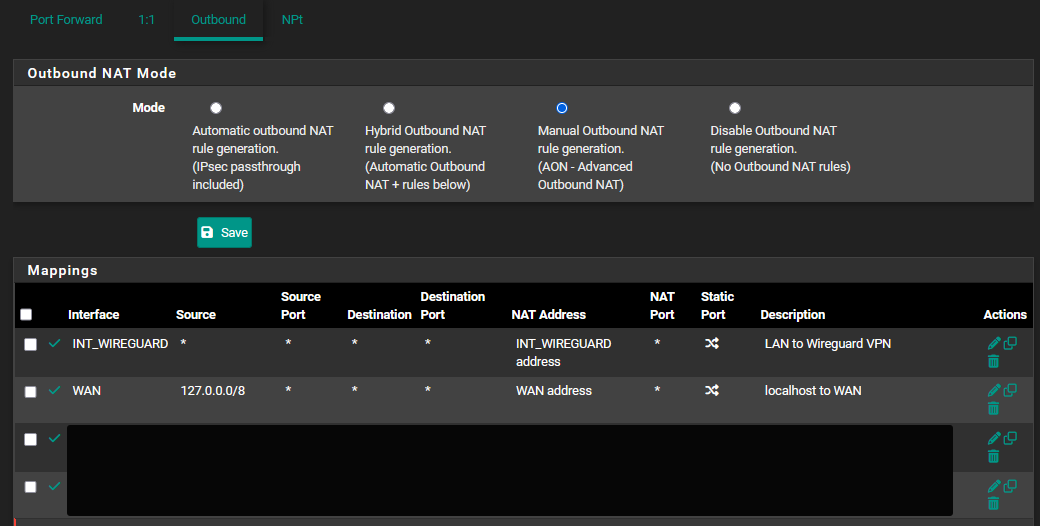
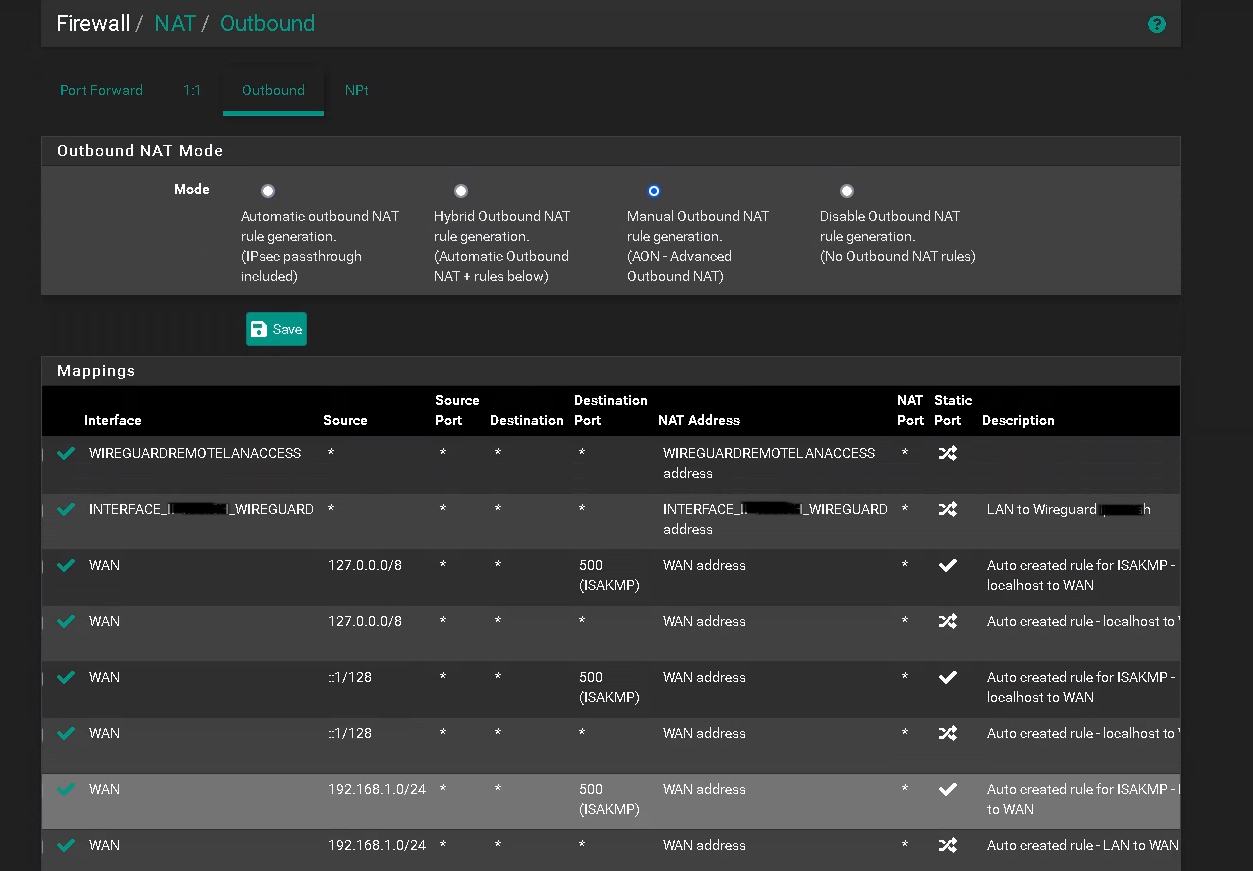
@philjoyal, do you allow NAT Outbound traffic for your Wireguard Client addresses via the Wireguard Gateway?
In Firewall > NAT > outbound you should have something like:
Interface................Source..................NAT Address
WG_VPN............10.200.0.5/24...............WG_VPNCan you maybe post a picture of your NAT Outbound rules?
-
-
This post is deleted! -
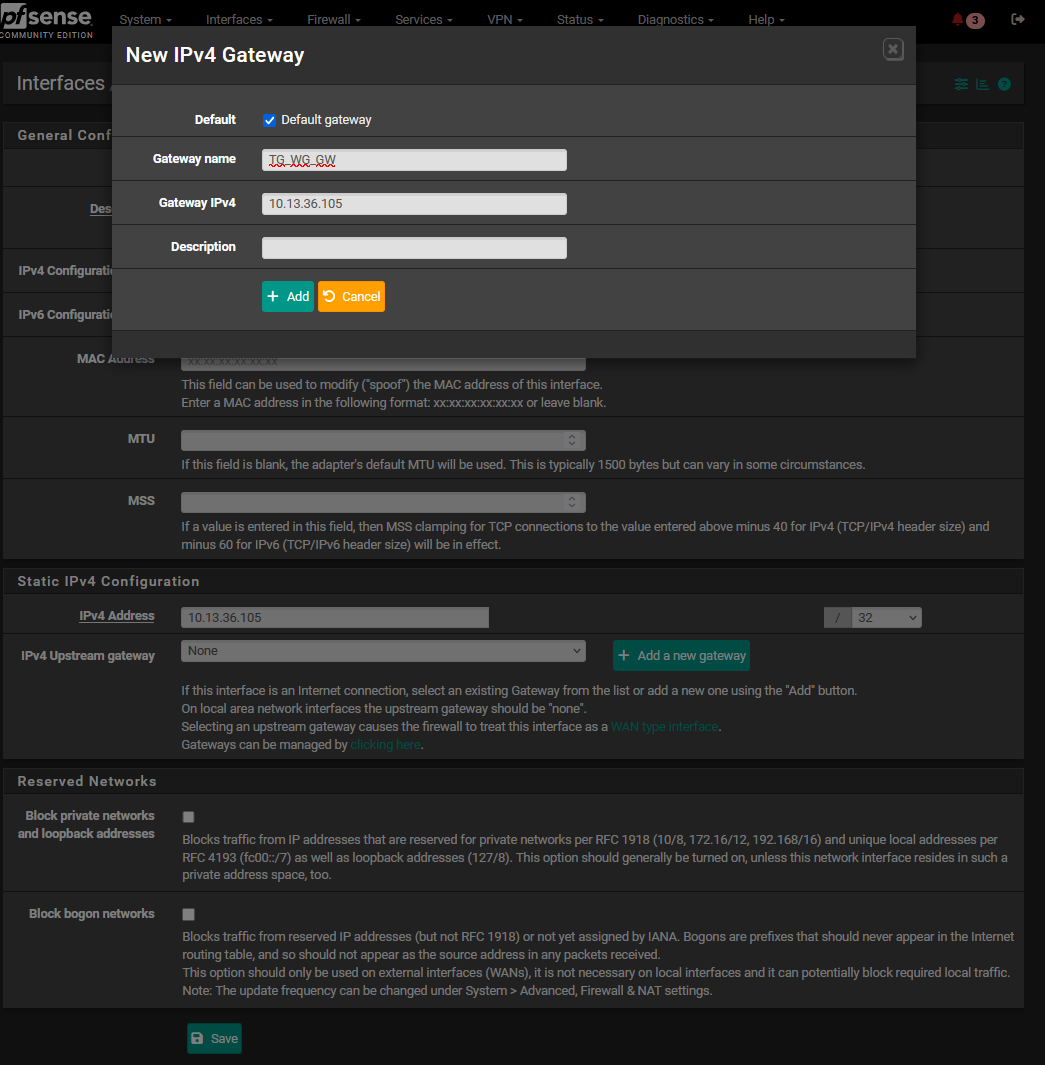
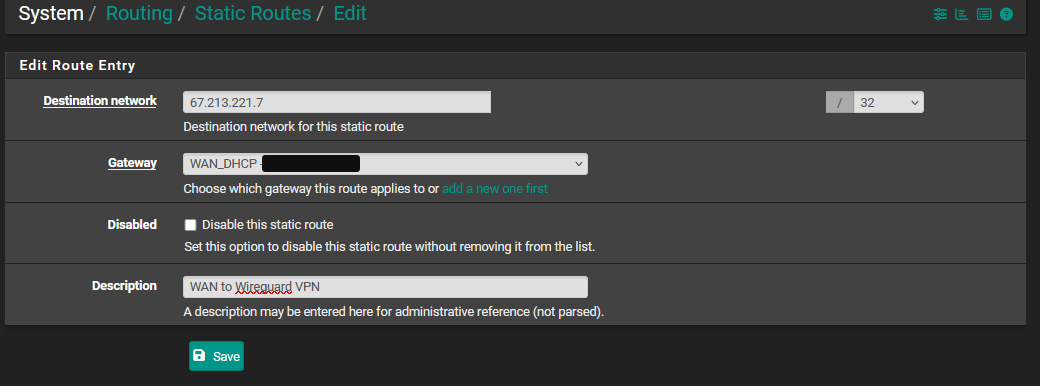
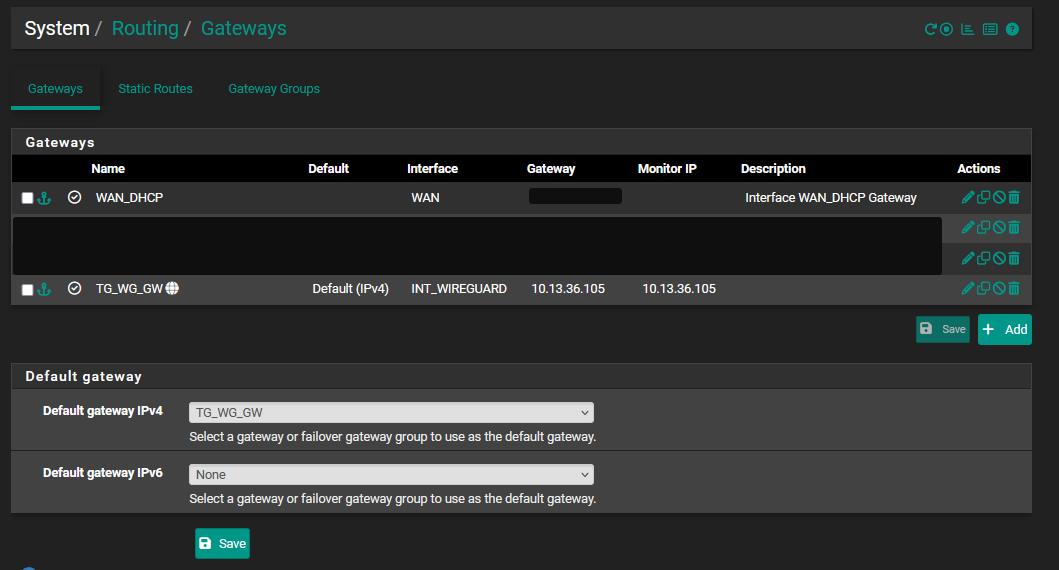
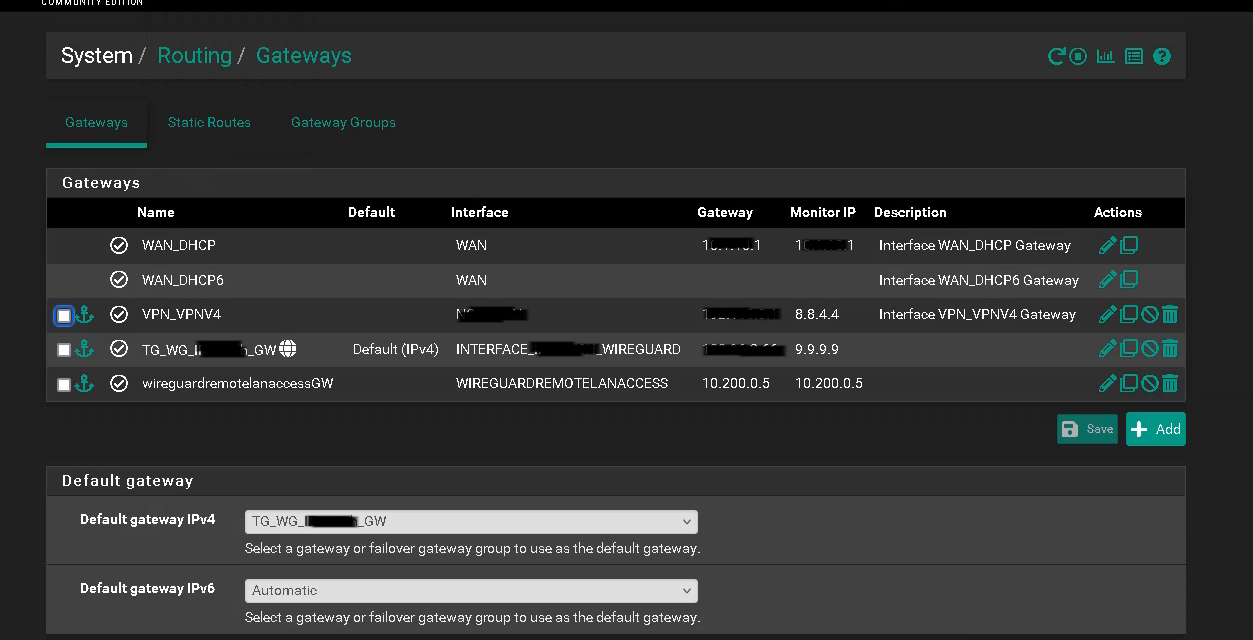
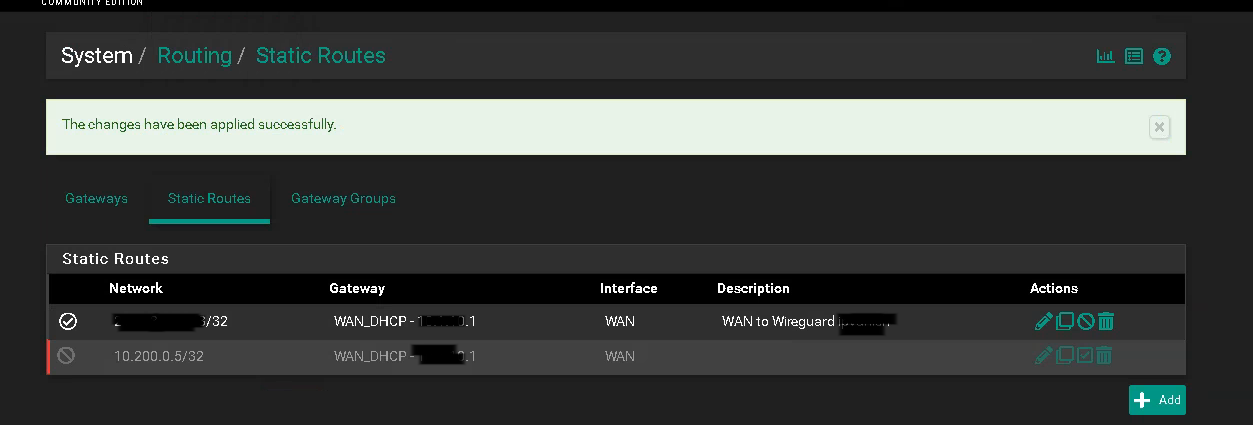
You probably need to add a static route for your WireGuard Remote Clients VPN subnet (10.200.0.5) to use the WireGuard ISP VPN (WG_VPN)
-
-
@LaUs3r Doesn't seems to work either
-
@philjoyal but that's not showing a static route. You need to add one in the routing tab.
Check out this guide: https://jarrodstech.net/fix-pfsense-remote-wireguard-vpn-clients-access-to-wireguard-site-to-site-vpn/ -
@LaUs3r the static route is shown in the 3rd screenshot
-
P philjoyal referenced this topic on
-
I found this guide years ago. This was back before there were any pfsense VPN guides on the internet. The site has since gone down, but is still on the WayBackMachine. There is a brief explanation of the Wireguard MTU and MSS and how they relate to each other.
DevinMadeThat - Guide: Adding Proton VPN with WireGuard to pfSense
Excerpt:
- MTU: 1420
Maximum Transmission Unit: Because of WireGuard's overhead, you want to set it for 1420 - MSS: 1420
Maximum Segment Size: You want this clamped to 1380, but it's calculated minus 40 (for 40 bytes of v4 header) from whatever you type here. So you want to enter 1420 (1420-40=1380)
- MTU: 1420
-
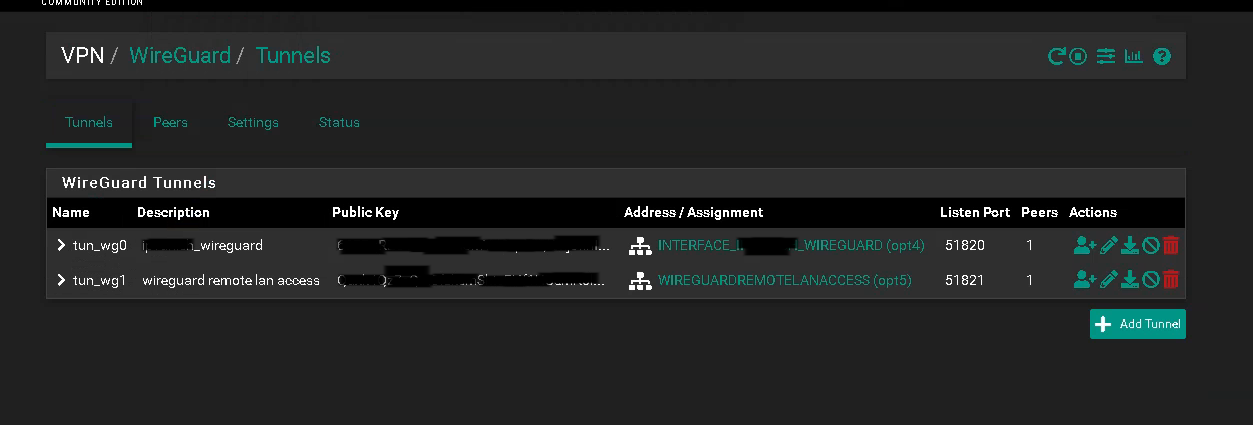
This was a great post to get me started with a dual VPN solution - thanks so much for the write up @LaUs3r . For my use case I desire a wireguard primary interface and a failover wireguard connection if primary goes down or has high latency. I finally got both set up, handshaking and passing traffic.
I'm probably a bit over my head here and did a lot of trial and error to get things going so sorry if stupid question but once thing still isn't working for me correctly. wg0 and wg1 are both passing traffic like a round robin load balance situation - each successive connection alternates which one is being used - but that isn't the behavior I want.
I want to only send traffic to wg1 if wg0 fails (or gets high letency and packet loss). I created a gateway for each and a gateway group. In the gw group I have wg0 as Tier 1 and wg1 as Tier 2 but they seem to be treated equal. I also created an interface group for my NAT rules that contains VPN1(wg0) and VPN2(wg1)
I think I am missing what rules/process steers the traffic to the gateway group and how the NAT works and maybe somehow I'm sending traffic to both gateways ignoring the group tier and priority.
Any ideas where I should look in more detail to figure this out?
TIA
-
I tried following your guide to set up the Surfshark WireGuard server configuration in pfSense as default gateway, but I got stuck at the static routes step.
In my case, the endpoint isn’t a numeric IP — it’s listed as us-bna.prod.surfshark.com. How should I add this to the static routes?
In my configuration:
Endpoint: us-bna.prod.surfshark.com
Address: 10.14.0.2/16
So what exactly should I enter in the static routes? after switching the default gateway from WAN_DHCP to the WireGuard VPN my Interent doesn't work so adding static routes is mandotary
(Im using inside vmware)
-
@subhan2k said in [Guide] Setup a wireguard tunnel to VPN provider (multiple VPN tunnel setup):
I tried following your guide to set up the Surfshark WireGuard server configuration in pfSense as default gateway, but I got stuck at the static routes step.
In my case, the endpoint isn’t a numeric IP — it’s listed as us-bna.prod.surfshark.com. How should I add this to the static routes?
In my configuration:
Endpoint: us-bna.prod.surfshark.com
Address: 10.14.0.2/16
So what exactly should I enter in the static routes? after switching the default gateway from WAN_DHCP to the WireGuard VPN my Interent doesn't work so adding static routes is mandotary
(Im using inside vmware)
nslookup us-bna.prod.surfshark.com Server: 127.0.0.53 Address: 127.0.0.53#53 Non-authoritative answer: Name: us-bna.prod.surfshark.com Address: 82.26.162.48 Name: us-bna.prod.surfshark.com Address: 82.26.162.53That should do it

Just take 1 of the 2.And in general, don't use domain names but only IP. Before you start, choose 1 of the 2 IPs and use it for the whole process
-
@LaUs3r ok I use this 1 IP It works initially, but after every restart the handshake fails. I believe Surfshark assigns a new dynamic IP each time, and even when I update that IP in the peer, static route, and firewall rule, the handshake still doesn’t work because it needs a temporary connection (like WAN) to establish first.
-
do you have a guide for setting up a Multi-Hop VPN inside pfSense (running on VMware)? Right now, I have an extra server running OpenVPN, and I want to route it through a Multi-Hop setup. Do you know how to do it? I’ve also heard that Multi-Hop setups are prone to more leaks, so it needs to be configured properly.
-
@subhan2k , SurfShark offers some tutorials how to set up wireguard on openwrt, etc.
https://support.surfshark.com/hc/en-us/articles/7161303618834-How-to-set-up-WireGuard-on-a-DD-WRT-router#01HJ8AJJW5SRFKFRBQF9P550Q7
How does the config look like with regards to the server location? I mean there must be some specific IP for the server be included. Maybe it makes more sense to use this.
For example, I use TorGuard: when I have a config file created for us.torguard.com, I get an IP in the config and not the domain name
-
@subhan2k said in [Guide] Setup a wireguard tunnel to VPN provider (multiple VPN tunnel setup):
Multi-Hop
Sorry, no experience here.
-
@LaUs3r surfshark WG config include
Use this configuration with WireGuard client
[Interface]
Address = 10.14.0.2/16
PrivateKey =
DNS = 162.252.172.57, 149.154.159.92
[Peer]
PublicKey =
AllowedIPs = 0.0.0.0/0
Endpoint = us-bos.prod.surfshark.com:51820 -
@subhan2k, I guess you only have issues with the domain name when trying to add the static route.
What you could do is to add a static route like the following:us-bos.prod.surfshark.com resolves to 43.225.189.108 and 43.225.189.118.
Regarding the static route in pfSense:
- destination network: 43.225.189.0 / 24 (/24 is the key here)
-
@LaUs3r Yeah, I added those IPs, but after restarting pfSense, the WireGuard status says “handshake failed.”
Also, when I do nslookup us-bos.prod.surfshark.com, I get two different sets of IPs.
For example:• The first time I get 43.225.189.108 and 43.225.189.118
• The next time I get 149.40.50.216 and 149.40.50.290So I was wondering can I add both sets of IPs, and put a “0” at the end of each, and use /24 for both IPs?
I reached out to Surfshark support, and they sent me their official pfSense WireGuard setup guide
see the guide herein the guide they mention 10.14.0.2 for static routes
-
@subhan2k , sorry I've been quite some time on a business trip and not be able to reply.
The guide seems quite comprehensive. Did you follow and get it to work meanwhile? What was the Surfshark reply to your ticket?