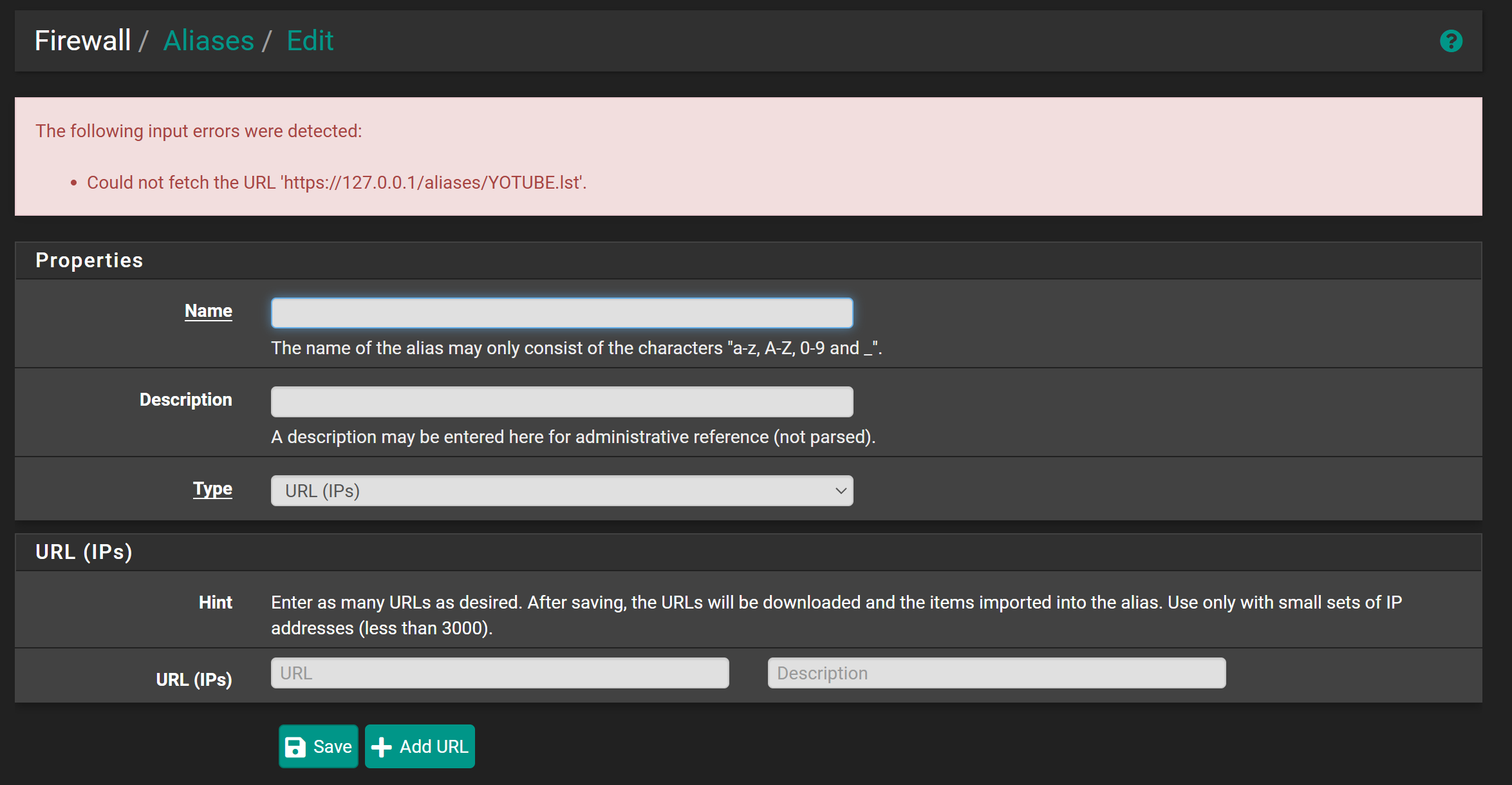
fetch on v2.7.2 gives certificate error.
-
When try to download a certain file on the system using
fetch, this happens:[2.7.2-RELEASE][root@pfSense.home.arpa]/root: fetch https://127.0.0.1/android-chrome-192x192.png Certificate verification failed for /O=pfSense GUI default Self-Signed Certificate/CN=pfSense-6788cc7a4a361 0020A1917D3F0000:error:0A000086:SSL routines:tls_post_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-CE-snapshots-2_7_2-main/sources/FreeBSD-src-RELENG_2_7_2/crypto/openssl/ssl/statem/statem_clnt.c:1890: fetch: https://127.0.0.1/android-chrome-192x192.png: Authentication errorI need to take care of this because I use it to create a URL alias:
Is there a solution?
-
@scilek said in fetch on v2.7.2 gives certificate error.:
Is there a solution?
There is.
Keep in mind that you asked for TLS (== https).
So, the certificate from the 1270.0.0.1 web server is asked, and the certificate must contain this host name, which isn't a host name but an IP address : 127.0.0.1.
Is this the case ?
The web server that runs on pfSense, you control it, you knwo what cert it uses, so inspect that cert.Same way for www.google.com.
Goto www.google.com using https : it works.
Now the IP of www.google.com.
And us it like https://216.58.215.36Now it doesn't work, and better, you now why.
https://127.0.0.1/isn't any different.
When I use the host name I've included in the certificate that the pfSense web server uses, the issue is gone :
[24.11-RELEASE][root@pfSense.bhf.tld]/root: fetch https://pfSense.bhf.tld/android-chrome-192x192.png android-chrome-192x192.png 6479 B 12 MBps 00sbecause I wasn't trying to break 'https' ^^
"bhf.tld" (actually the wild card *.bhf.tld) is part of the SAN list of the cert used. -
@Gertjan Thank you very much for the reply.
I know how HTTPS works. But there was no such problem before. (I just checked, not on v2.7.2 either.)
I also tried giving the router a FQDN, create a cert with with it and then tried again, but it did not work; I still get the same error.
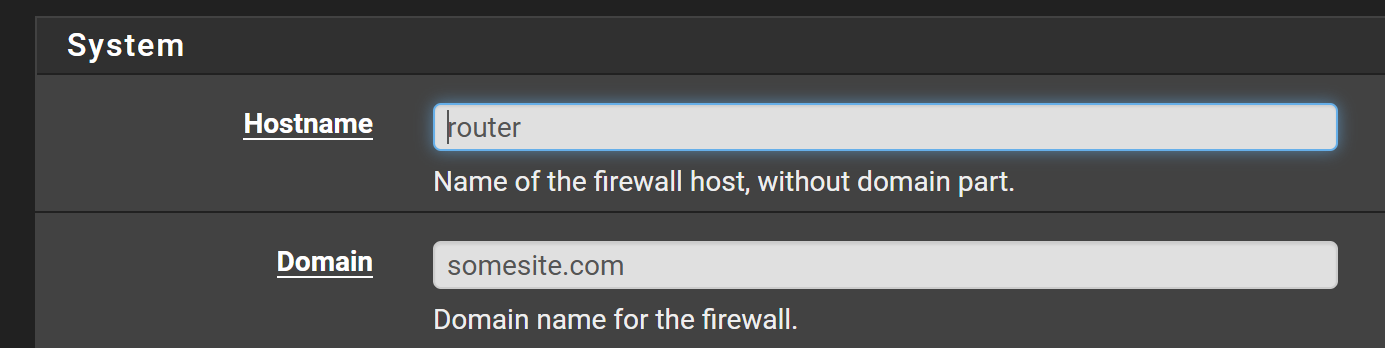
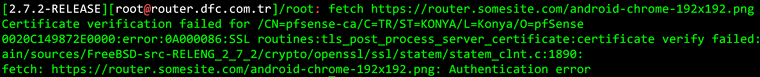
Could something have been broken somewhere?
-
@scilek said in fetch on v2.7.2 gives certificate error.:
But there was no such problem before
The problem** is still there, on 24.11 :
[24.11-RELEASE][root@pfSense.brit-hotel-fumel.net]/root: fetch https://127.0.0.1/android-chrome-192x192.png SSL certificate subject doesn't match host 127.0.0.1 fetch: https://127.0.0.1/android-chrome-192x192.png: Authentication errorThe error it gave is way more clear as yours.
It said : "127.0.0.1" isn't part of the cert, so bye bye.** isn't a problem.
In the past, 2.7.2 worked just fine for me.
When you use https, do not (like never) use IP addresses. Use the host name embedded in the certificate, like pfsense.monsite.com
Make be sure the browser or program like 'fecth' knows about your CA. By default, it doesn't.
Or, get (rent actually) a domain name, then, with this domain name, get a certificate recognized by 'everybody' from Letencrypt, import the cert in pfSense cert store, and be done with it ^^.
This is where the pfSense package acme comes in handy.@scilek said in fetch on v2.7.2 gives certificate error.:
I also tried giving the router a FQDN, create a cert with with it and then tried again, but it did not work
The certificate that you created ('signed') by 'yourself'.
Or, have you told ((informed) your browser you use that it should trust the certificate that you signed ?
Out of the box, your phone/pad/PC/MAC/whatever has a build in list with trusted CA's (authorities that signs certificates and these will be trusted by your browser).
The good news is : you can import (add) your own, CA certificates you create @home.
Do that, and suddenly, when you visit https://pfsense.monsite.com/ will show up, and no errors will be shown by your browser.When you fetch https://pfsense.monsite.com/ on the command line of pfSense itself, its the same thing.
It's https, so the command fetch will look up the known CA's in /usr/share/certs/trusted/ (I guess) and if your own - (created in pfSense GUI) isn't there, it will error out.
If you know where the certificate CA is stored, you can probably use a command line option of fetch so it has your CA, and suddenly, no more error ^^Yo can give your own CA (a file, dono where it is stored) :
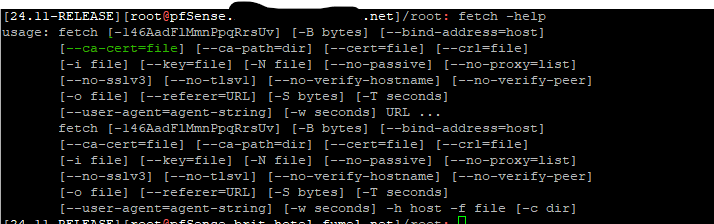 fetch -
fetch -So
fetch --ca-file /some/place/where/your/CA/is https://127.0.0.1/would work just fine if 127.0.0.1 is part of the SAN in the cert.
Orfetch --ca-file /some/place/where/your/CA/is https://pfsense.monsite.com/You've created the pfsense.monsite.com cert, the web server GUI is using it for its https needs, now all you need is trust the CA that was used to create the cert.
-
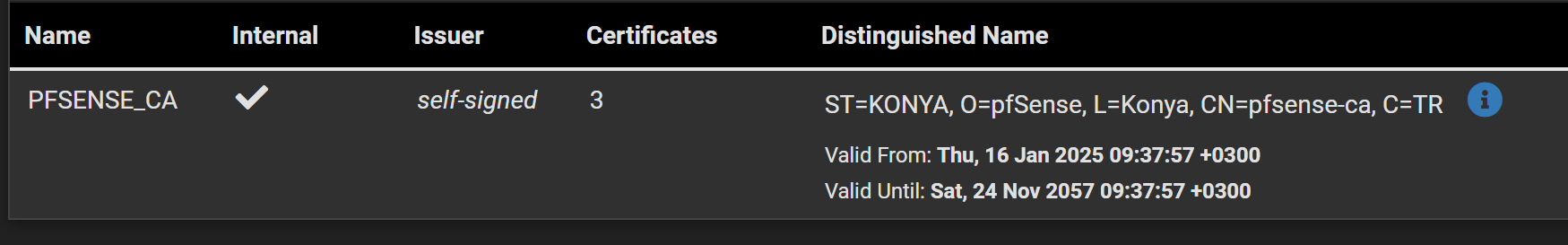
I don't think pfSense stores the certificates anywhere, they are all in the
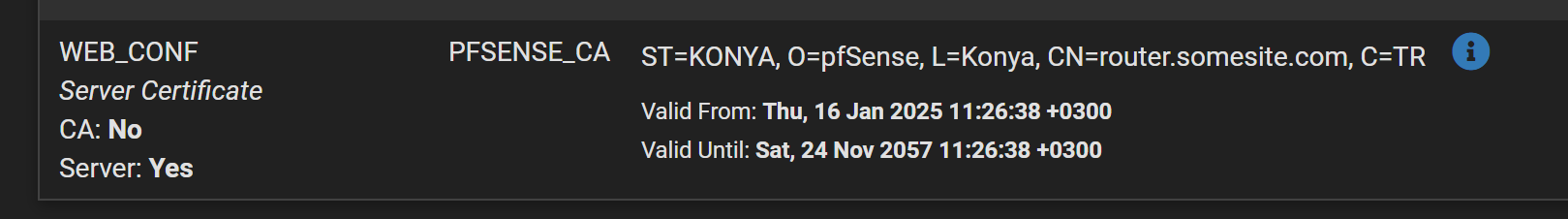
config.xmlfile.Also the custom CA I have created (is PFSENCE_CA) is trusted:

-
@scilek said in fetch on v2.7.2 gives certificate error.:
I don't think pfSense stores the certificates anywhere, they are all in the config.xml file.
Example :
The web server ("GUI"), if it has https enabled :
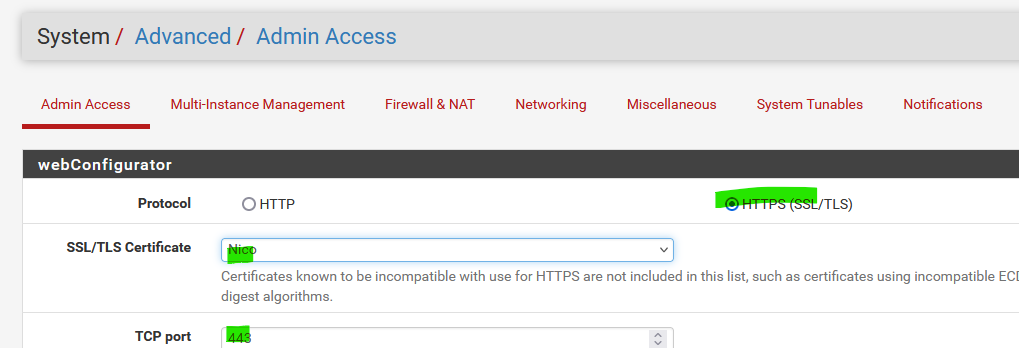
it needs to have a cert, mine is called 'Nico'.
Let's have a look :[24.11-RELEASE][root@pfSense.bhf.tld]/root: cat /var/etc/nginx-webConfigurator.conf # # nginx configuration file pid /var/run/nginx-webConfigurator.pid; user root wheel; worker_processes 2; error_log /dev/null; events { worker_connections 1024; } http { include /usr/local/etc/nginx/mime.types; default_type application/octet-stream; add_header X-Frame-Options SAMEORIGIN; .... Bla bla ..... server { listen 443 ssl http2; listen [::]:443 ssl http2; ssl_certificate /var/etc/cert.crt; ssl_certificate_key /var/etc/cert.key;So there they are : pfSense placed the certs it used for the web server here :
/var/etc/cert.crt
/var/etc/cert.keyDo a
cat /var/etc/cert.crtand you see everything is there, the cert itself, the intermediate, and the CA.
Ok, cool.
What's left to do, is finding the actual file name, and .... don't know where it is.
Look also here /etc/ssl/ and /etc/ssl/certs/ etc.This worked for me :
[24.11-RELEASE][root@pfSense.bhf.tld]/root: fetch --ca-cert=/var/etc/cert.crt https://pfsense.bhf.tld/android-chrome-192x192.png android-chrome-192x192.png 6479 B 17 MBps 00s -
@Gertjan
Well, thanks. That did work:[2.7.2-RELEASE][root@router.somesite.com]/root: fetch --ca-cert=/var/etc/cert.crt https://router.somesite.com/android-chrome-192x192.png android-chrome-192x192.png