Cloudflare new 1.1.1.1 for families
-
Hello fellow Netgate community members,
I have just learned that Cloudflare has new options for DNS servers that come built in with anti-malware, and even if you so choose block adult content. This is done with just using
As quoted from Cloudflare
1.1.1.1 for Families categorizes destinations on the Internet based on the potential threat they pose regarding malware, phishing, or other types of security risks. 1.1.1.1 for Families has two default options: Block malware Use the following DNS resolvers to block malicious content: 1.1.1.2 1.0.0.2 2606:4700:4700::1112 2606:4700:4700::1002 Block malware and adult content Use the following DNS resolvers to block malware and adult content: 1.1.1.3 1.0.0.3 2606:4700:4700::1113 2606:4700:4700::1003However if you use DoT like me over port 853 you can also now use
1.1.1.1 for Families also supports DoT if you have a compliant client, such as a compatible DoT router. DoT allows you to encrypt your DNS queries, protecting you from spoofing, malicious actors, and others. You can learn more about DoT in the Learning Center article on DNS encryption ↗. To configure an encrypted DoT connection to 1.1.1.1 for Families, type one of the following URLs into the appropriate field of your DoT-compliant client: Block malware security.cloudflare-dns.com Block malware and adult content family.cloudflare-dns.comThis works at the main dns resolver so much like an upgrade to pfblocking, as the main DNS server does the major blocking for you.
Ref:
https://developers.cloudflare.com/1.1.1.1/setup/#1111-for-families
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html -
DNS over TLS example
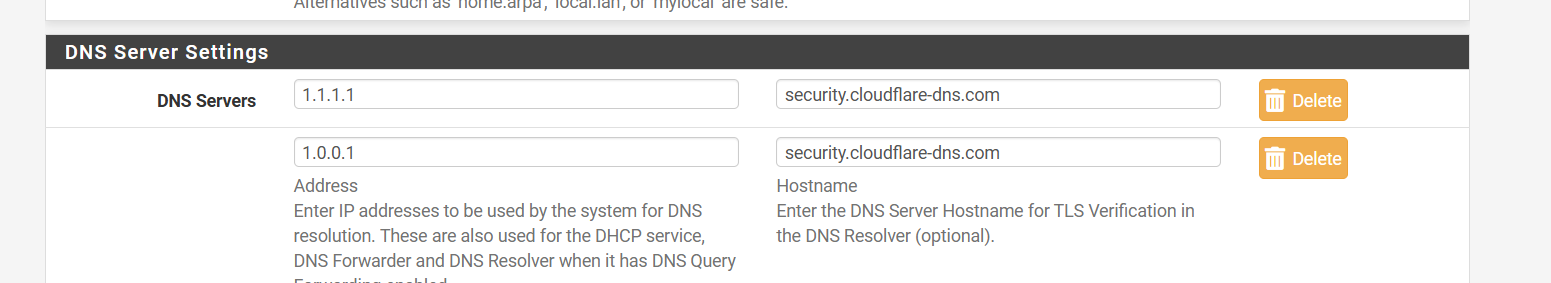
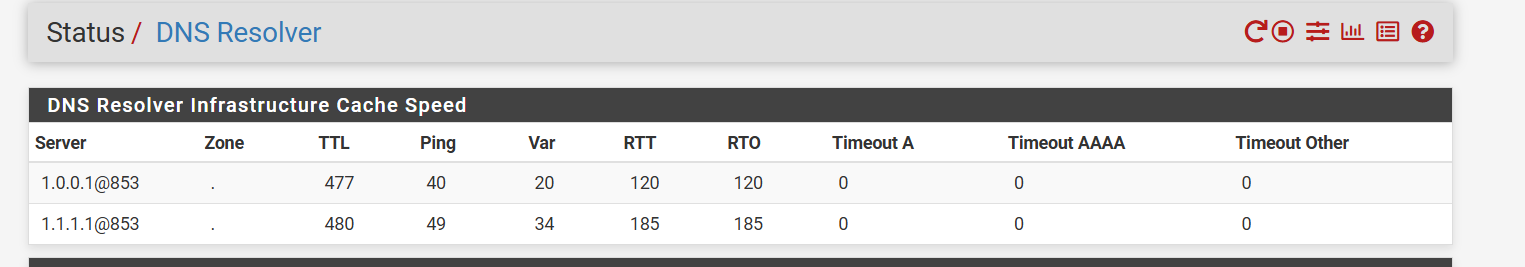
-
@JonathanLee I'll be testing this..
Thanks
-
@mcury If you want to use port 853 you will first have to follow the instructions on this guide from netgate.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html
Otherwise you can just use the adapted dns addresses
-
@JonathanLee I'm checking it right now.
I have dual WAN here, so I can't use general settings like you did.Edit:
Unless I use 1.1.1.1 for one WAN and 1.0.0.1 for the other..
hmm
Edit2:
Left the gateway option empty in general settings, added both family.cloudflare-dns.com for 1.1.1.1 and 1.0.0.1, disabled DNSSEC and enabled forwarding and Use SSL/TLS for outgoing DNS Queries to Forwarding Servers.Testing now.
-
@JonathanLee said in Cloudflare new 1.1.1.1 for families:
DNS over TLS example


Since you're using the DoT FQDN of security.cloudflare-dns.com, need to change the IPv4 addresses to the corresponding 1.1.1.2 and 1.0.0.2.
I have a little note on my phone keeping track of a few public DNS resolvers. Here's what I have for Cloudflare:
Cloudflare 1.1.1.1 1.0.0.1 2606:4700:4700::1111 2606:4700:4700::1001 DoH: https://cloudflare-dns.com/dns-query DoH: https://mozilla.cloudflare-dns.com/dns-query DoT: cloudflare-dns.com ---------------------------- Malware 1.1.1.2 1.0.0.2 2606:4700:4700::1112 2606:4700:4700::1002 DoH: https://security.cloudflare-dns.com/dns-query DoT: security.cloudflare-dns.com ---------------------------- Malware + Adult 1.1.1.3 1.0.0.3 2606:4700:4700::1113 2606:4700:4700::1003 DoH: https://family.cloudflare-dns.com/dns-query DoT: family.cloudflare-dns.comI used Cloudflare DoT and DoH (in all browsers) for quite a few years but in the past year or two switched to Quad9 after a Lawrence Systems video compared a handful of public DNS resolvers' ability to block malware sites. The results showed that Quad9 blocked significantly more than Cloudflare.
Here's the listing I have for Quad9:
Quad9 9.9.9.9 149.112.112.112 2620:fe::fe 2620:fe::9 DoH: https://dns.quad9.net/dns-query DoT: dns.quad9.netThe only drawback with Quad9 I've noticed compared to Cloudflare is there's no option for adult site filtering like you get with 1.1.1.3/1.0.0.3 and family.cloudflare-dns.com
-
@Finger79 said in Cloudflare new 1.1.1.1 for families:
The only drawback with Quad9 I've noticed compared to Cloudflare is there's no option for adult site filtering like you get with 1.1.1.3/1.0.0.3 and family.cloudflare-dns.com
For me there is another drawback, which is latency, unfortunately.
-
Also looks like Cloudflare's filters aren't that good...
https://techblog.nexxwave.eu/public-dns-malware-filters-tested-in-september-2024/ -
@JonathanLee said in Cloudflare new 1.1.1.1 for families:
DNS servers that come built in with anti-malware ...
What I make of that : they use a DNSBL, the one we don't have (?), the one with all the sites that host malware.
Isn't that a bit like "Use XyzVPN and you don't risk anything anymore on the net ..." ? It makes me .... sad to realize that there are really people out there that actually believe that. But also somewhat upset, as these people really don't care about there own devices (the data on it, etc) and that their actions can take down entire home networks and companies.Ours browsers can't get any mall-ware, as they can only download html, php css and harmless other files. It us, the ones with a mouse in ours hands that give the order to download another type of file.
Because you clicked on that promising button, so the file got loaded on your system.
Then, because it was that "Free Office Microsoft 365 for Live" installer that you were looking for, you execute it ....
I'm pretty sure this always happens to the same persons.Anyway, I've this site, www.papy-team.fr, This site isn't not used anymore, and exists for historical reasons. Google is still very active on it, crawling all over the place. The server logs tell me this.
This site, afaik, isn't blocked no-where. So I've uploaded a mild mall ware on it some 10 days ago. It's not hidden really, neither in plain sight. I'll see when 1.1.1.1 stops suggesting my own site.1.1.1.1 scans like Google the entire Internet for bad content ?
If I find bad content, I have to call them to tell them ? Notify them ? I mean, how did they get the knowledge my site is bad ?
My, how do we call it ? "Microsoft Security center", contacts 1.1.1.1 if it flags a mall-ware somewhere ? I'm pretty sure it will call home with this info, but not 1.1.1.1.
Ok, 'Home' (Microsoft) gives .... sorry, I'm rude, sells ( !! ) this info to the most bidder, like 1.1.1.1 ?And
So, afaik, 1.1.1.1 uses a DNSBL. Ok ...... I've already my own DNSBL.To terminate my rant (as it is ;) ) : Glad to know that 1.1.1.1 also uses a DNSBL these days.
And yes, I know, I get it, if you have a household with kids, or run a prison, you'll be looking for solutions. What's wrong with the ancient method ?
-
@Gertjan said in Cloudflare new 1.1.1.1 for families:
And
So, afaik, 1.1.1.1 uses a DNSBL. Ok ...... I've already my own DNSBL.To terminate my rant (as it is ;) ) : Glad to know that 1.1.1.1 also uses a DNSBL these days.
And yes, I know, I get it, if you have a household with kids, or run a prison, you'll be looking for solutions. What's wrong with the ancient method ?
I used to have a DNSBL list here too, but adults list are huge.
And DNSBL lists have a big impact in IO on the drives.
So, I decided that having IP lists and some geoIP lists are fine, but DNSBL would be better in my case to use a third party service. -
 Thanks - that a good motive.
Thanks - that a good motive.For example this one :
will explode a "1100" and even my "4100" has a hard time loading, storing, indexing and using it.
edit : I tried to use it again. The Xxx list, 4.5 million host names.
It loaded ... ( took 2 minutes )
Half an hours later : new events in the system logs :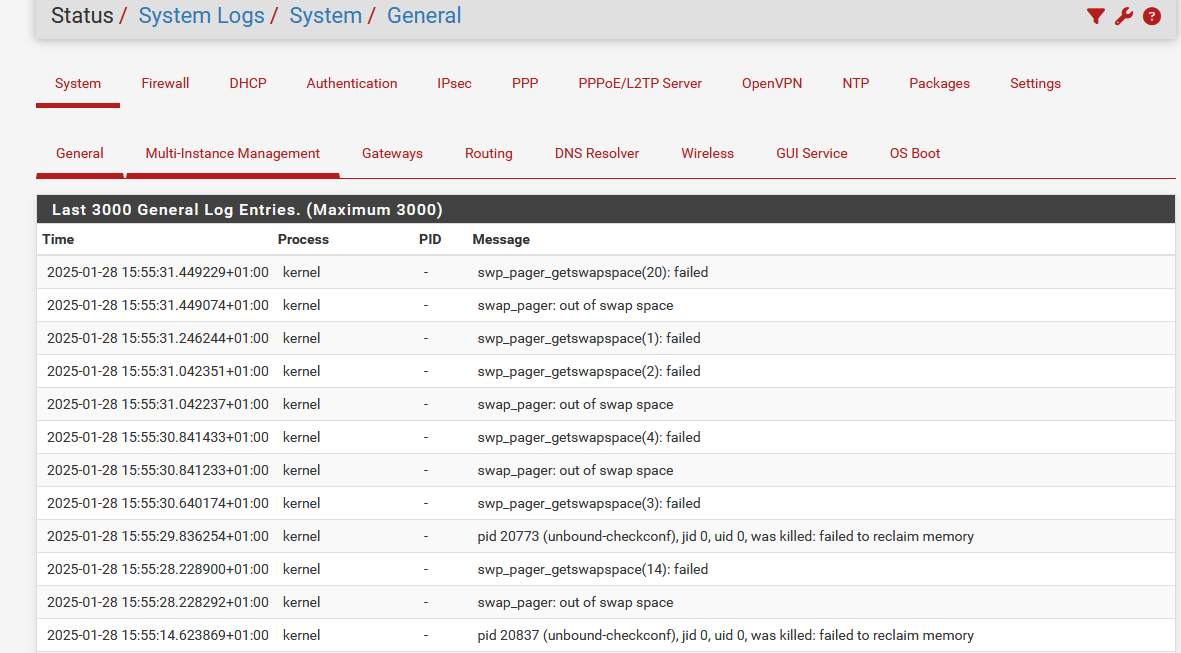
Info : I'm using a 4 Gbytes RAM 4100 (and a huge drive).
The Xxx list needs way more memory - at least 6 Gbytes or so. At least a 6100 could work. -
@Gertjan it makes me sick to my stomach how the adult content and malware is out there. my SG-2100 when running the full block lists in squid guard would grind the thing to a just loading them it’s unreal. Finally a simple one button setting solution for networks. It has reporting tools, testing linking, it’s simplified. It’s a gargantuan block list managed by a major dns provider, this opens up all sorts of consumer bases that want the one button simplified solutions. The fact that a major dns made a solution makes me happy
-
@mcury said in Cloudflare new 1.1.1.1 for families:
@JonathanLee I'm checking it right now.
I have dual WAN here, so I can't use general settings like you did.Edit:
Unless I use 1.1.1.1 for one WAN and 1.0.0.1 for the other..
hmm
Edit2:
Left the gateway option empty in general settings, added both family.cloudflare-dns.com for 1.1.1.1 and 1.0.0.1, disabled DNSSEC and enabled forwarding and Use SSL/TLS for outgoing DNS Queries to Forwarding Servers.Testing now.
I had mixed results re leaving gateway option empty, so set one to each.
-
@mikey_s 1.1.1.2 and 1.0.0.2 you mean right they use and adapted IP. I think the company is branded as 1.1.1.1 so they still have the corporate branding and symbolism but to use the family settings if you read it they are .2 or .3.
I am wondering what software development model they used for this if it was a rational unified process, or waterfall model, incremental development, or integration and configuration? Maybe Integration and config or reuse oriented model. It kind of appeared without any advertisement that’s why I question the model. The cost of evolution of this product must be big, they just eat that? Where or how is the url black lists obtained? They had to have one ready to get to work so fast, think about all the urls you submitted to blacklist sites over the years, that database did not occur overnight.
-
@JonathanLee said in Cloudflare new 1.1.1.1 for families:
@mikey_s 1.1.1.2 and 1.0.0.2 you mean right they use and adapted IP. I think the company is branded as 1.1.1.1 so they still have the corporate branding and symbolism but to use the family settings if you read it they are .2 or .3.
I am wondering what software development model they used for this if it was a rational unified process, or waterfall model, incremental development, or integration and configuration? Maybe Integration and config or reuse oriented model. It kind of appeared without any advertisement that’s why I question the model. The cost of evolution of this product must be big, they just eat that? Where or how is the url black lists obtained? They had to have one ready to get to work so fast, think about all the urls you submitted to blacklist sites over the years, that database did not occur overnight.
Correct, the 1.1.1.3 and 1.0.0.3 servers.
Two WAN connections, one is 4G failover.Originally I had both assigned to the primary WAN and Quad9 assigned to the 4G backup.
My other firewall is a Sophos XG and the failover / multi WAN setup on that is nice.
-
@mikey_s said in Cloudflare new 1.1.1.1 for families:
I had mixed results re leaving gateway option empty, so set one to each.
Changed, testing now.
Disabled DOT btw.EDIT:
I'm getting around 40ms to quad9's DNS servers, but decided to test it in my network.
Using 9.9.9.11 and 149.112.112.11, each one of them assigned to a different WAN.
Using DOT: dns11.quad9.net
DNSsec enabled.Everything seems to be working perfectly so far..
Missing the adult filter.EDIT2:
Do you guys know if Unbound in pfSense is compiled with ECS support ?