How do I configure SPAN for the WAN port?
-
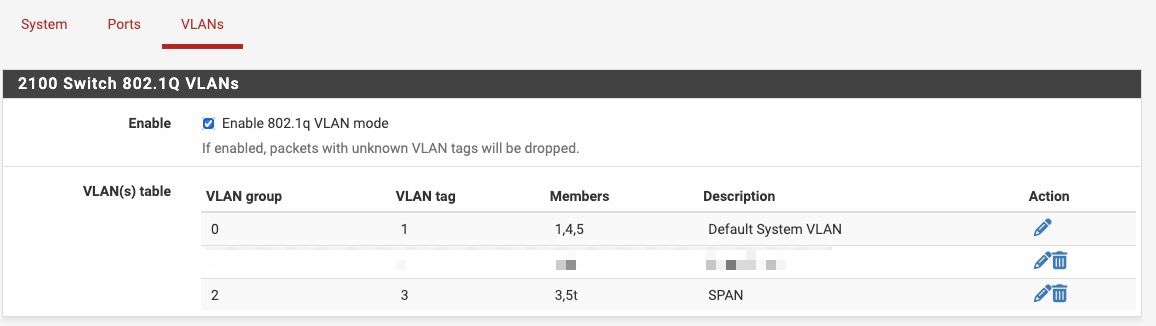
@stephenw10 Yes, I would like the spanned traffic to be tagged with VLAN 3, so I'll set it as 3t,5t
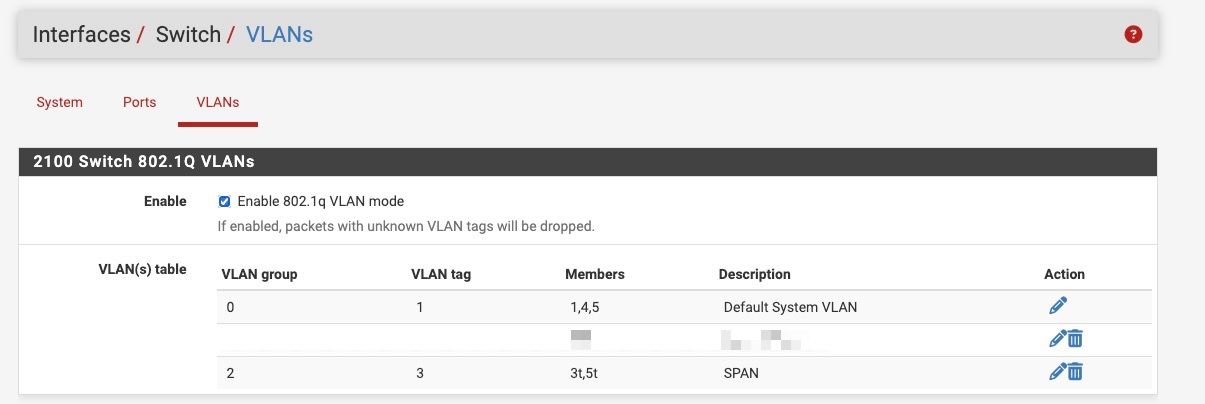
Are there any issues with my bridge configuration or anything else?
The bridge member interfaces is "WAN", and the SPAN port is set as "WANSPAN"
-
Yes that looks correct.
If you are tagging port 3 there is no need to set the PVID there but it also doesn't hurt having it set like that.
-
@stephenw10 Thank you, there appears to be some problem. To isolate the issue, I removed the tagging on the Interface > switch > vlan and reverted to just
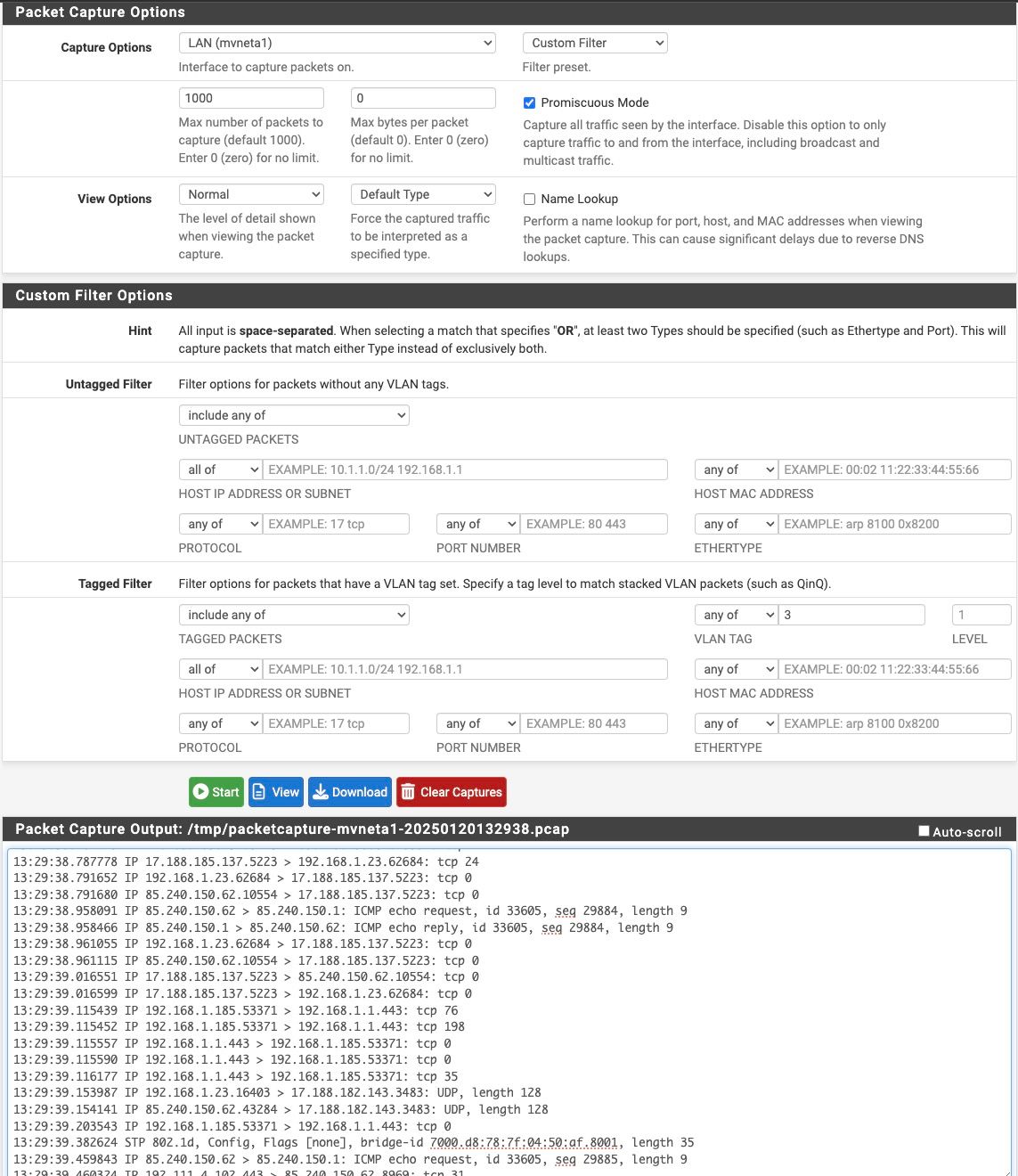
3,5tI started a packet capture on the interface mvneta1.3 and I do the WAN traffic as you can see:
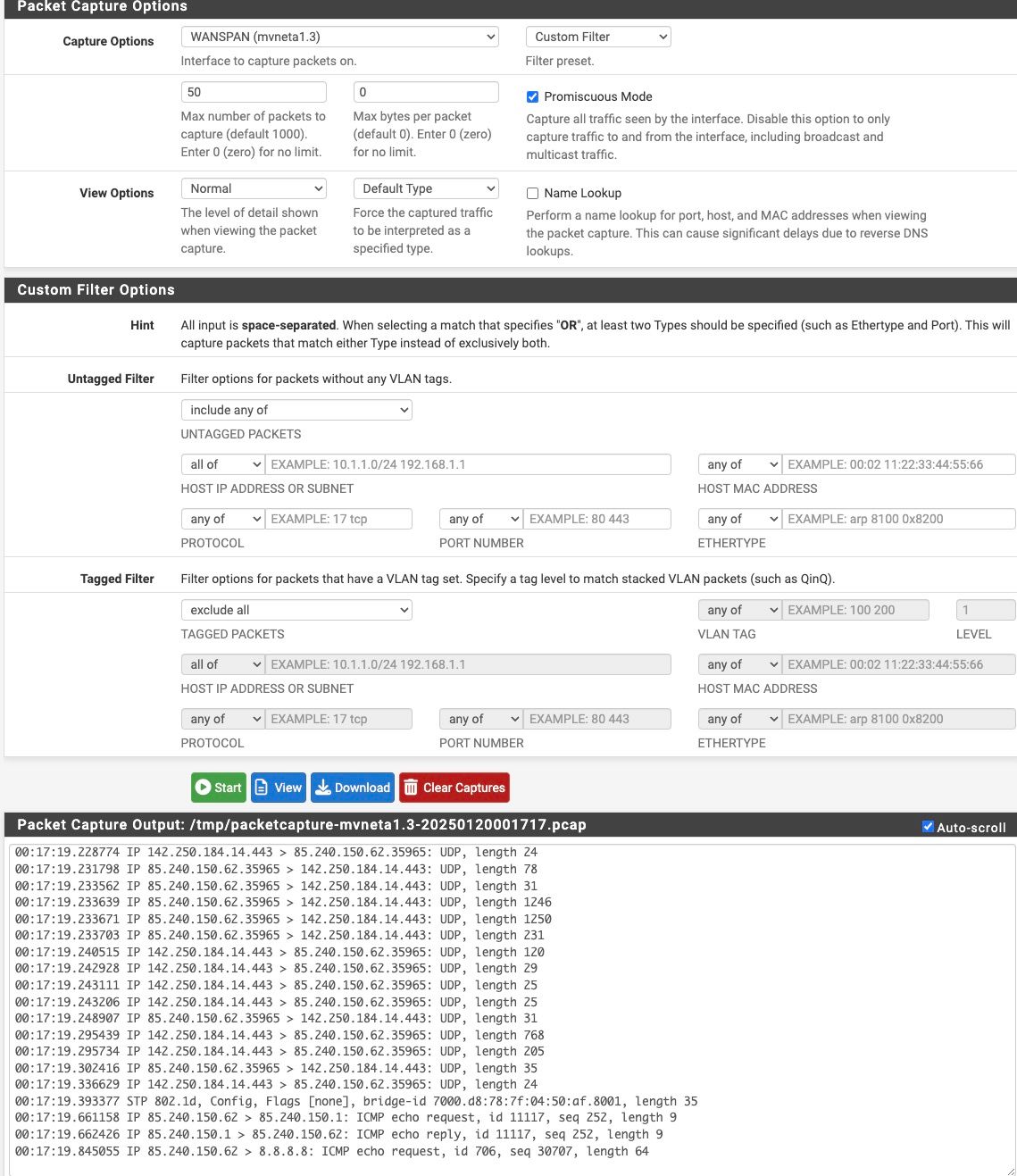
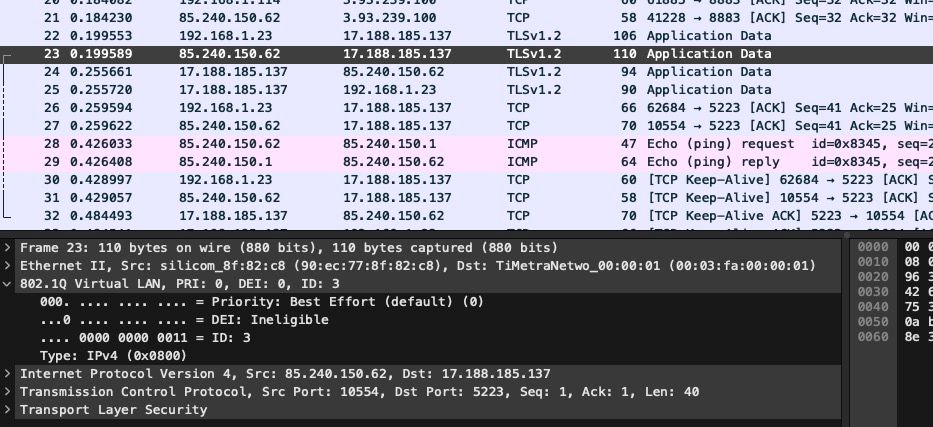
I've connected LAN3 to a raspberry pi which I know is configured for sniffing traffic, and I have been able to see the actual traffic in the past. However, all I see are some STP packets, and BUM traffic, like in the screenshot here:
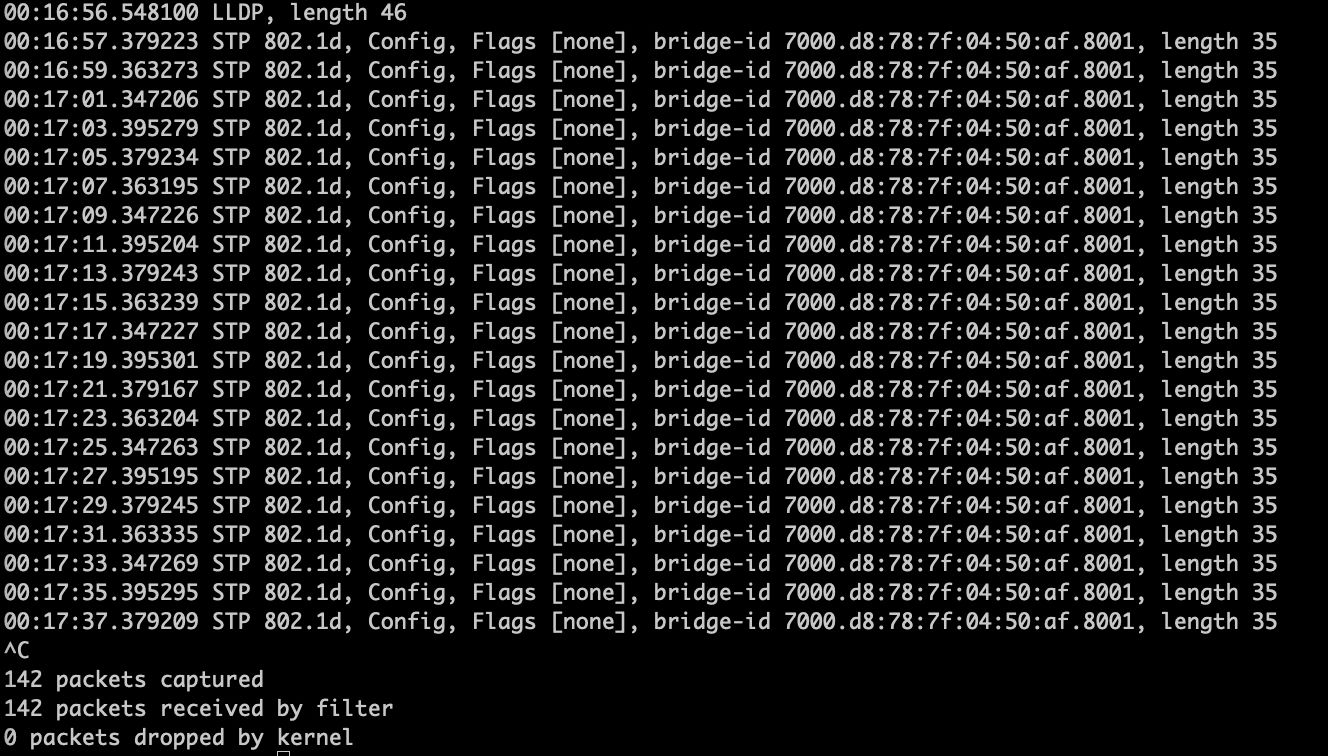
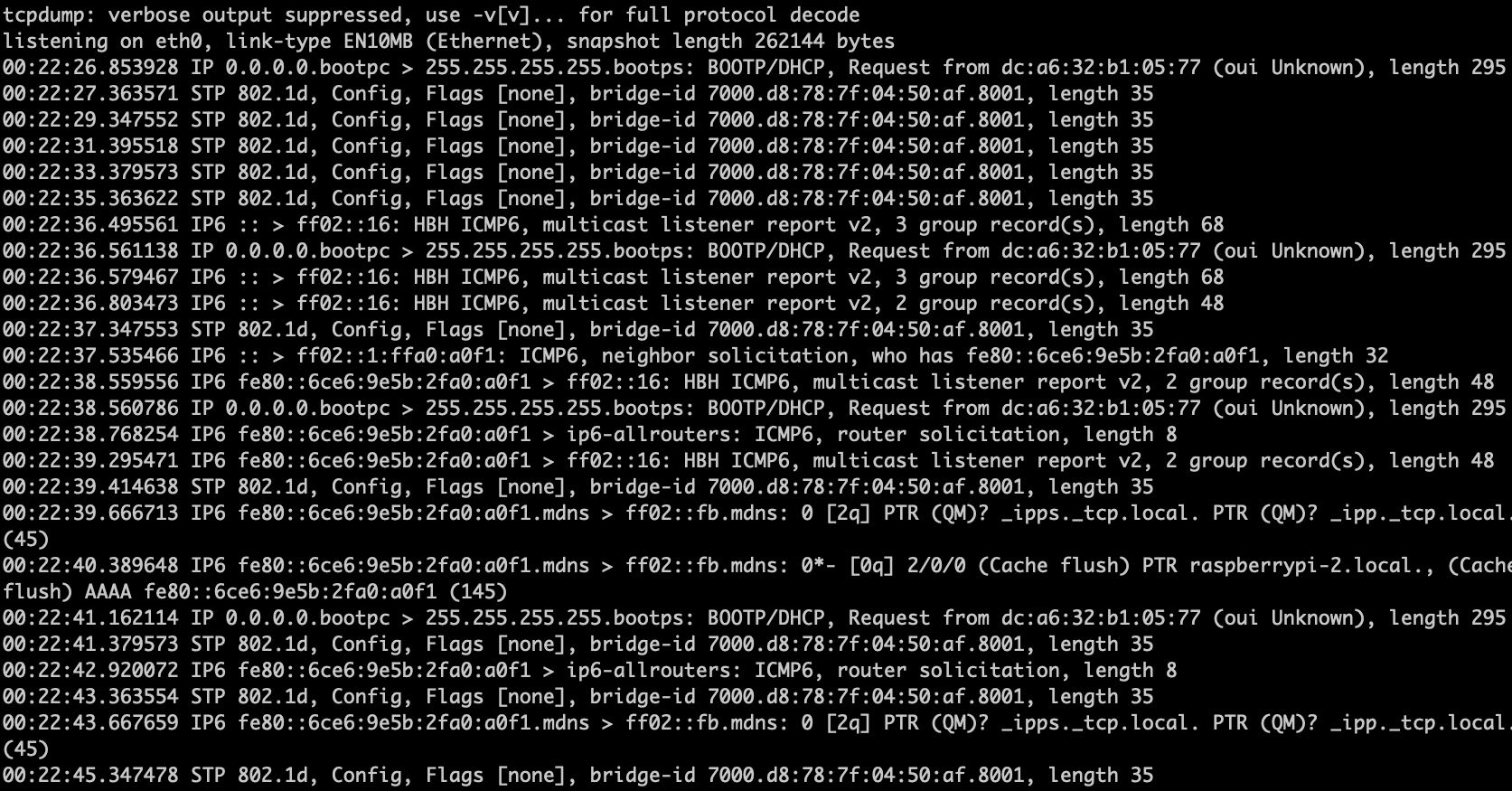
Do you have any ideas why might this be happening? (I know that the rpi is not an issue because just moments earlier I was capturing spanned traffic from another network and for testing purposes I've connected it to LAN3 on this netgate appliance)
BTW, I also tried to enable/disable promiscuous mode on mvneta1.3 but that had no effect unfortunately.
-
Hmm, if it makes it to the VLAN on mvneta1 I'd expect that switch config to work. Bridging and VLANs can be painful though.
If you run a pcap on mvneta1 directly and include vlans tagged packets do you see that mirrored traffic all tagged 3 correctly?
-
-
@stealthmode if you want to span your wan traffic - I would put a real switch that can do span between pfsense and where you connect it for your wan.
I run my wan through my switch just for this purpose. If I ever need to span this this traffic its as simple as turning it on in my switch.
You can pick up a smart switch that can do this for like 20-40 bucks. But I just run it through my main switch as a vlan.
cable modem - switch - wan pfsense.
-
Yet you see nothing at port 3 still?
I wonder if the switch simply drops all that traffic because the MAC address of the connected device doesn't match any of it. That could be hard to workaround.... There is no setting in the switch we have access to that might allow it.
The only thing I could imagine working there would be some encapsulation between pfSense and end client . A gif tunnel perhaps.
-
@stephenw10 I thought the same, which is why I removed the switch and connected it directly to the pi....
This pi is already configured correctly to sniff traffic, I was doing this in the past.
-
I mean the built-in switch in the 2100. It may ave some setting to allow it but we don't expose it. It may not even be accessible in the switch driver.
-
@stephenw10 What does enabling promiscuous mode on that interface do in this case?
-
Promiscuous mode would allow all traffic to pass on the local interface. But that doesn't help traffic pass through the switch. I would still expect to see broadcast traffic there though.