Safari in Iphone is bypassing FIrewall rule
-
@Uglybrian so if I add new deny rule of adding all the doh address mentioned in the pic, will the safari accessing the internet will be blocked ?
-
@mozmail said in Safari in Iphone is bypassing FIrewall rule:
IP address which is provided by Facebook https://developers.facebook.com/docs/whatsapp/guides/network-requirements/.
Totally not up to date.
And facebook switched to IPv6... also missing. -
@mozmail said in Safari in Iphone is bypassing FIrewall rule:
@Uglybrian so if I add new deny rule of adding all the doh address mentioned in the pic, will the safari accessing the internet will be blocked ?
Well, maybe, but possibly not. As others mentioned, the IP addresses of the DoH servers can change. And some of the services are tied to CDNs that you have to enable to let other stuff work. Apple would be one for instance. If you block everything Apple, then iPhones can't get updates and certain Apple iOS stuff will not work. But allowing the Apple IP subnet blocks then lets the DoH traffic to Apple's servers get through.
I guess my ultimate question here would be "why do you want to restrict them to only WhatsApp?" As you are discovering, such specific filtering in today's Internet environment with so many CDNs and Anycast DNS services is becoming very difficult and heading towards impossible as DoH and QUIC become widespread
 .
. -
@Gertjan said in Safari in Iphone is bypassing FIrewall rule:
And facebook switched to IPv6... also missing.
Missing how.. Just because they enabled IPv6 doesn't mean any of those fqdn changed. And changed implies IPv4 is no longer available - which is just not true. You mean they enabled IPv6
If OP is running IPv6 then sure that would have to be taken into account when blocking IPs/Ports as well.. But if he isn't then means nothing if they have it enabled or not.
-
Private relay on Apple is a setting per each individual Wi-Fi network you connect to. For instance, for my home network wi-Fi settings I have private Wi-Fi addresses off and limit IP address tracking off. With these settings, my iPhone uses my local DNS,able to still get mail, messages, and filtering through PF blocker. On other Wi-Fi networks I joined private relay is turn on.
You can tell the people on campus with iPhone that if they want to use The campus Wi-Fi network these are the settings you need to employ with our network. Turn off private Wi-Fi addresses and limit IP tracking. This will not affect other Wi-Fi networks they use.
PF blocker has a DNBL safe search that you can utilize to block Apple iCloud private relay. There are also of course IP block list for Doh.
I use one from github/crypt0rr/public-doh-servers. -
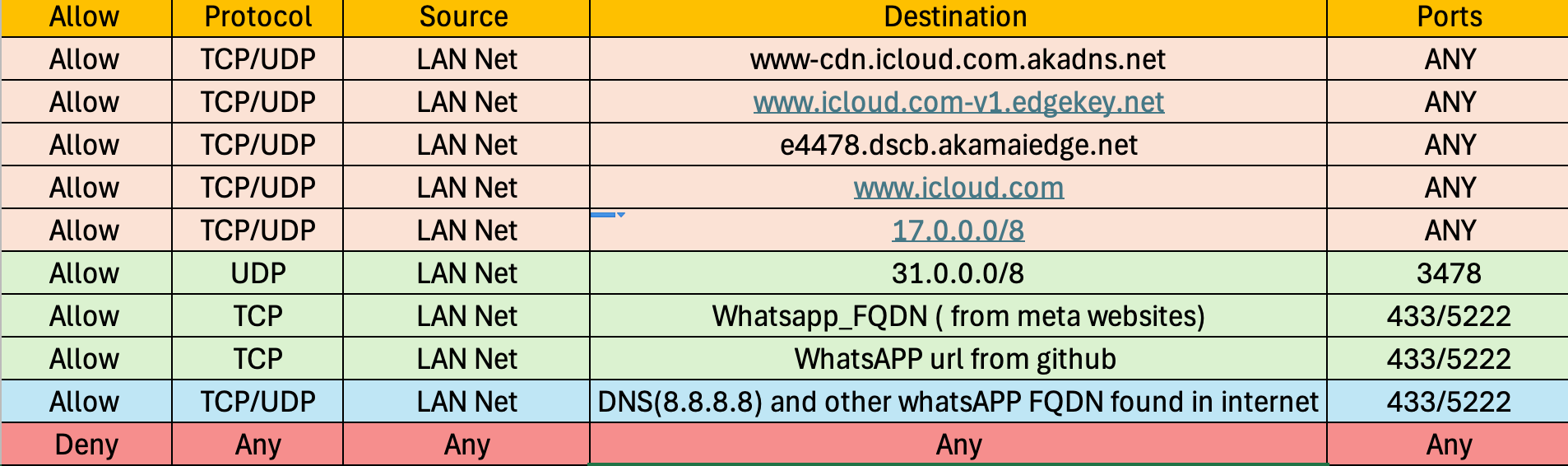
After moving the DHCP server from the distribution switch to the pfSense box for my LAN network, we noticed that Safari traffic is completely blocked on all devices., WhatsApp voice and video calls work perfectly on both iPhone and Android.
The problem arises when users try to send or receive images via WhatsApp on iPhones. It takes more than an hour to send or download a picture, even though they can see the picture notification immediately. Strangely, other features like screen sharing during video calls work just fine.
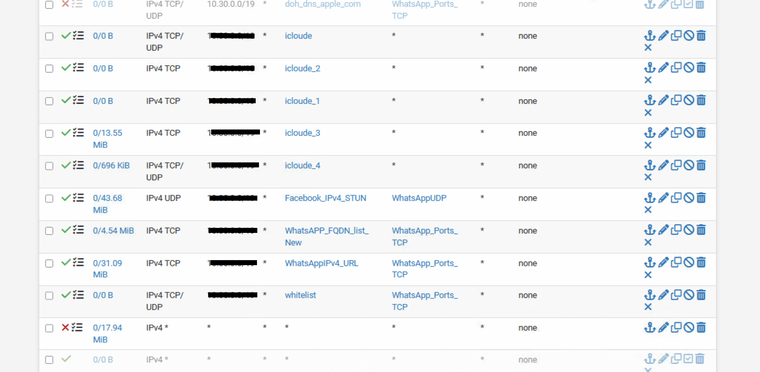
I have attached the current pfSense LAN firewall rule for reference. Any ideas on what could be causing this or how to fix it?
Note: When I checked the WhatsApp URL IP list initially, it had 5 IP ranges dedicated to Apple, so I created a separate allow list named Icloude to see which one gets hit.
-
@Uglybrian said in Safari in Iphone is bypassing FIrewall rule:
You can tell the people on campus with iPhone that if they want to use The campus Wi-Fi network these are the settings you need to employ with our network. Turn off private Wi-Fi addresses and limit IP tracking. This will not affect other Wi-Fi networks they use
how to confirm that they turned off private wifi addresses and limit IP tracking ?
I can able to block the safari traffic after moving the DHCP server from the switch to the Netgate PFsense box. now only whatsapp works in iPhone and Android phones - but new issue is that Iphone uses when ever they try to send/receive pics it takes couple of hours - tested voice video call it works without any delay
-
@bmeeks said in Safari in Iphone is bypassing FIrewall rule:
I guess my ultimate question here would be "why do you want to restrict them to only WhatsApp?" As you are discovering, such specific filtering in today's Internet environment with so many CDNs and Anycast DNS services is becoming very difficult and heading towards impossible as DoH and QUIC become widespread
n Palo Alto and Cisco devices, it's easy to block traffic on an application-specific basis. I’m trying to achieve the same with a pfSense box. For example, on flights, only messaging apps are allowed, and all other internet traffic is blocked—so this use case and implementation already exist in the market. I’m now looking for a way to implement similar application-based blocking using pfSense. Any suggestions on how to do this?
I’ve almost managed to get application-based blocking working on the pfSense box
-
@mozmail said in Safari in Iphone is bypassing FIrewall rule:
@bmeeks said in Safari in Iphone is bypassing FIrewall rule:
I guess my ultimate question here would be "why do you want to restrict them to only WhatsApp?" As you are discovering, such specific filtering in today's Internet environment with so many CDNs and Anycast DNS services is becoming very difficult and heading towards impossible as DoH and QUIC become widespread
n Palo Alto and Cisco devices, it's easy to block traffic on an application-specific basis. I’m trying to achieve the same with a pfSense box. For example, on flights, only messaging apps are allowed, and all other internet traffic is blocked—so this use case and implementation already exist in the market. I’m now looking for a way to implement similar application-based blocking using pfSense. Any suggestions on how to do this?
I’ve almost managed to get application-based blocking working on the pfSense box
Those Palo Alto and Cisco devices have specific application detection technology built into them. That's also why they cost a ton of money to own and license
 . You pay for the priviledge of using that technology and for the labor and time of Palo Alto and Cisco security analysts to keep up with all the application technology changes and issue regular updates to keep the app detection/filtering working. pfSense does not natively offer application layer filtering, but it's also open source and free -- so there is that advantage.
. You pay for the priviledge of using that technology and for the labor and time of Palo Alto and Cisco security analysts to keep up with all the application technology changes and issue regular updates to keep the app detection/filtering working. pfSense does not natively offer application layer filtering, but it's also open source and free -- so there is that advantage.You can do this application detection and filtering on a limited basis, providing your are able and willing to write some of your own rules, with the Snort package on pfSense using its AppID feature.
-
@bmeeks I agree, due to budget we are going with PFsense and that's why checking the best to do with it, I got it working for now. with my above rule list and extra, I added to block the traffic to DNS IP 1.1.1.1 for port 853, from what I see Safari is using DNS over TLS port 853, with that blocked safari is blocked