Source NAT and port forwarding
-
Hi All,
I have a pretty generic task.
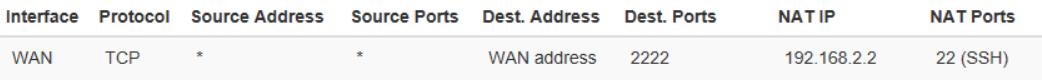
I need to make source NAT and port forwarding in pfsense, for example:
A client with src 1.1.1.1:<any port> should connect to 2.2.2.2:2222 and have the next values after NAT
src 192.168.1.1:<any port>
dst 192.168.2.2:22
I found out how to do the port forwarding, but I can't understand how to add here the source nat option.Could you help me on it?
-
@tramp_sergey its just an outbound nat. On the 192.168.2.2 interface..
Here I have one.. couple actually
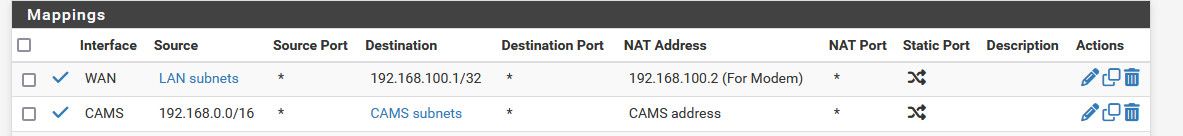
So my cameras which are behind my nvr, and use the nvr as their normal gateway are on a 10.1.1 network. I have a leg of pfsense in this 10.1.1 network so my other local networks can get there. But the cameras would send the answer back to the nvr on 10.1.1.1 which wouldn't get back to pfsense to be routed back to my other networks.
So when say my 192.168.9.100 pc wants to talk to 10.1.1.65 (camera) that outbound nat says hey anything coming from 192.168/16 leaving the camera interface to talk to a 10.1.1 address, nat it so it looks like the pfsense camera address which is 10.1.1.253
This really the same thing that pfsense does when your device talk to the internet out your wan.. They source nat the traffic to the wan address.
That other one I have overrides the normal wan outbound nat and says hey if your talking to 192.168.100.1 (my cable modem management IP) instead of natting to the wan address (public ip) nat it to the vip I created on pfsense wan of 192.168.100.2
BTW if your network 192.168.1 wants to talk to your other network 192.168.2 - there is no need for a port forward between local networks..
Only time you need a port forward is when traffic is coming in your wan, and there is a nat in place. You would use a source nat between your networks when the device on the other network has no gateway set, or different gateway than pfsense and you can not add or don't want add route on the device. Or that device has a firewall that only allows local networks.
-
@johnpoz Hi,
Thank you for the response.
I tried that NAT also, but no luck
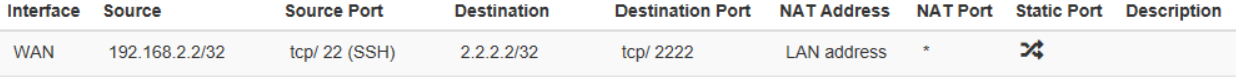
and
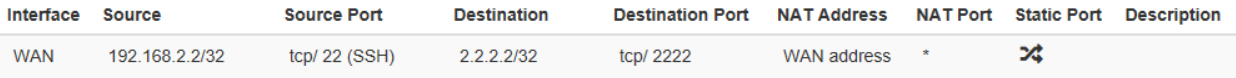
and
and
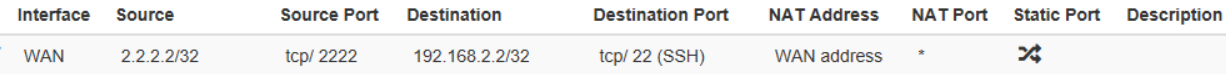
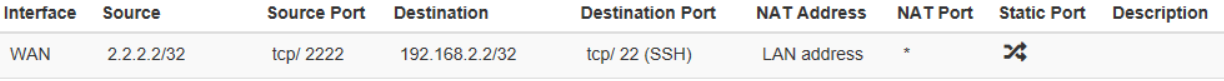
My PC is on the WAN side, and I'm trying to connect to 2.2.2.2:2222, I expect to be connected over the LAN port with the source IP of the LAN interface to 192.168.2.2:443
I can't understand what is wrong here.
-
@tramp_sergey if your device your wanting to talk to is on pfsense wan.. It would already be natted to your wan address.. All you would have to setup is a port forward to get the traffic to your device behind pfsense when the traffic hits your wan IP. If the device on your wan was going to start the conversation..
BTW - why would you be using 2.anything on your pfsense wan? that 2.2.anything is owned by oracle
org-name: Oracle America Inc.
Who is starting the conversation? The 2.2.2.2 or the 192.168.2.2 ?? Who is wanting to talk to who on port 22, is it your device on your wan wanting to talk to device on your lan, or is the lan device wanting to talk to the device on your wan. Who is starting the conversation to the other one?
-
All IPs here are just for example.
Who is starting the conversation? The 2.2.2.2 or the 192.168.2.2 ??
A client with src 1.1.1.1:<any port>
2.2.2.2 is WAN port IP address
192.168.2.2 is a server over the LAN portWho is wanting to talk to who on port 22, is it your device on your wan wanting to talk to device on your lan, or is the lan device wanting to talk to the device on your wan. Who is starting the conversation to the other one?
The client tries to connect to 2.2.2.2:2222.
The pfsense should NAT the connection with the source IP of the LAN interface to 192.168.2.2:443 -
@tramp_sergey so some public IP out on the internet hits your pfsense wan which your calling 2.2.2.2 on port 22, and you want to forward that to 192.168.2.2 on your pfsense lan
And you want this to look like this public IP on the internet is coming from your pfsense lan IP 192.168.2.x
Well none of those Nats you said you tried would work.. As you see in my example the interface is my cam interface.
So your outbound nat should be on pfsense lan, and the source would be any or whatever source IP out on the internet is going to want to talk to your ssh server that you are forwarding and the destination would be your 192.168.2.2 address, and the nat address would be your Lan Address on pfsense.
Curious why do you think you need to do this? Does the 192.168.2.2 device not have a gateway set, or is using something other than pfsense as its gateway, or a firewall that won't allow this public IP to talk to it?
public IP -----> 2.2.2.2:22 (wan) pfsense (lan) 192.168.2.1 ----> 192.168.2.2:22
Your outbound nat interface is pfsense lan, the nat address is lan address. Now when publicIP hits pfsense wan and pfsense does it port forward to 192.168.2.2:22, the outbound nat in pfsense will change the source IP to 192.168.2.1 (pfsense address) so your 192.168.2.2 will think ssh is coming from 192.168.2.1, when he sends back the answer pfsense will know oh I need to send this back to PublicIP. And to the publicIP it will think the return traffic coming from pfsense 2.2.2.2 wan IP.
-
@johnpoz If I understand correctly, you mean this configuration
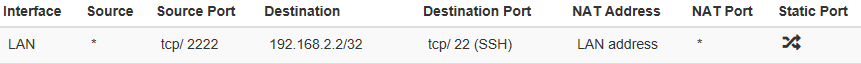
But it doesn't work also. I don't see any packets on the LAN, but logs show that the traffic is passed.The scheme is more correct:
public IP -----> 2.2.2.2:2222 (wan) pfsense (lan) 192.168.2.254 ----> 192.168.2.2:22The device has a different default gateway and it's easier to configure NAT than create a static route on the device and other devices in the location.
-
@tramp_sergey The source port on Internet connections is normally random so will basically never be "22"...change that to any/*.
-
@tramp_sergey said in Source NAT and port forwarding:
But it doesn't work also. I don't see any packets on the LAN, but logs show that the traffic is passed.
If your not seeing any traffic on your lan then your port forward isn't working.. As mentioned by @SteveITS that source port is wrong..
Per your updated drawing of mine, the destination hitting pfsense wan IP on 2.2.2.2 is 2222 but that has nothing to do with the source port the public IP sent from, which is almost always going to be some random port 1024 or above.. Can you show your port forward, because if you are calling out source port there, its not going to work..
-
@johnpoz I don't have rules for port forwarding.
Do you mean I should have two NAT rules in that case:
first for ports
second for IPs
? -
@tramp_sergey NAT rules are port forwards. Here's an example:
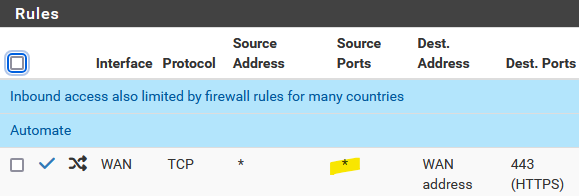
or one with a source defined:
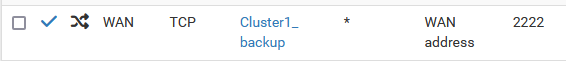
-
@tramp_sergey said in Source NAT and port forwarding:
I don't have rules for port forwarding.
Well then how do you think traffic from some public IP on the internet hitting your wan is going to get sent to this 192.168.2.2 address on a different port?
Here is a port forward I have for my plex server
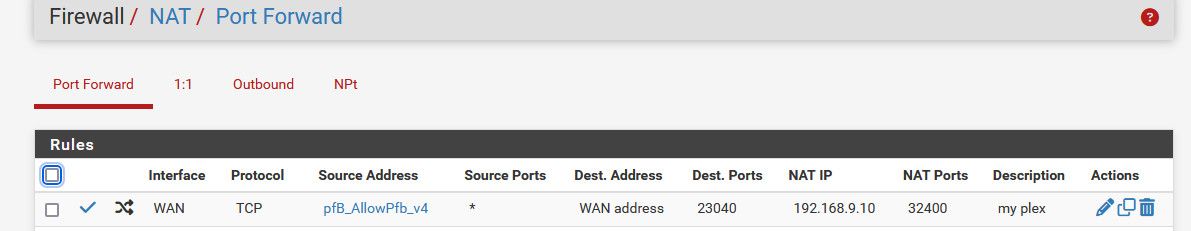
So some IP on the internet hits my pfsense wan PublicIP.. to port 23040, pfsense forwards that to my box running plex at 192.168.9.10 port 32400
But it will only do that if the source IP is in my alias pfb_allowed.. Which is really any IP in the US or belgium currently - and some other IPs that plex uses to validate plex is available, and other ips that check if my plex is up - and if not warns me that plex is down.
But some IP out on the internet hitting your wan IP isn't just going to magically get sent to your 192.168.2.2 IP on some other port.
-
-
@tramp_sergey you need both the port forward and the outbound nat to change it to the IP of pfsense interface on your lan.
-
@johnpoz I understand the logic now.
I've added the rule yet, and it works as expected now.
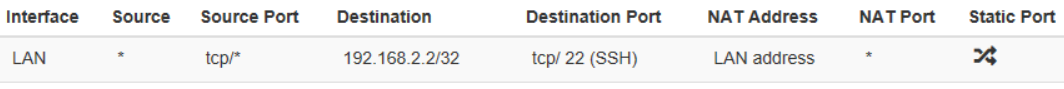
Thanks a lot for your help and patience!