pfSense Instance as »third party router« within existing Network
-
We have an existing Network (A) which is Setup with Equipment from another Vendor. I am asked to install a Firewall for one of our clients within that Network, such that they can put all there Stuff into their resulting Subnet (B).
Additionally I am asked to setup a WiFi for the Client which I would like to broadcast over the existing Access Points within our Network (A). For that I need to create a network on our Router. Going down that route, I found that our Router offers the ability to create a Network that is provided by an »third party Router«.
So in order to use the pfSense Instance (Network B) as router I guess I need to open some Ports / Settings, such that Devices can connect to that Network.
=> Which settings / Ports would I need to open, such that Networking would work?
If the pfSense Instance works as the Router, it could broadcast itself as the default Gateway (which is kind of the default, isn't it). Would that require even more Ports to open on the pfSense instance - meaning: if someone from the wifi wants access a website, Ports 80 and 443 need to be open in order to establish the connection?
Here a tiny outline of the Setup:
ISP | Router A —> Access Points —> WiFi Client , client Network, Router B default Gateway | Router B (pfSense Instance, client Network Router) | LAN Client with clientNetwork BIs that Possible? What Security Implications would that create?
Thanks for Directions!
-
Hmm, well the biggest issue I'd be concerned about there is that any client in Network B would be able to access anything in the subnet behind router A unless you have some tunneling setup to prevent it. That could be a VLAN between router A and B with separate firewall rules in router A for example.
-
@stephenw10 The concern that users from the »nested« / »client Network« / »B« can access Stuff in the »outer« / »hosting« / »A« Network is not a Problem at all - at least I think it is. Within that Network all the community stuff is added.
The biggest Concern or reason why the pfSense layer is added, is because the other way around. People from the community (A) must not be able to access the NAS in Network B.
-
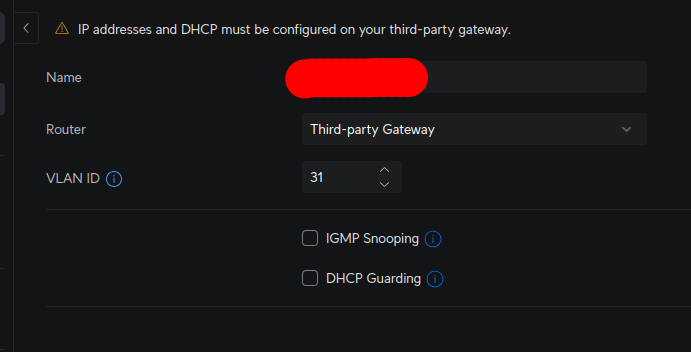
@signerror In the Unifi world, when you select Third-party Gateway for a VLAN, all it does is create that VLAN and distribute information about it, to all the relevant Unifi devices under it's control, like Switches and AP's.
That VLAN will have no internet access or even a subnet, until you set up a router to handle that (i.e. the Third-party Gateway). And that gateway needs to have it's LAN attached to a switch port with VLAN 31 in your case. In addition, the WAN port of that gateway needs to be connected to get internet access somehow. But that would mean that it's LAN is connected and under the control of the Unifi controller and whoever owns that.
So what it does is essentially what @stephenw10 is suggesting, to simply create a VLAN to handle things, but in a somewhat complicated way.
A better setup would be to create that VLAN 31 in the UDM/UDR, using the UDM/UDR as the gateway instead (not Third-party Gateway). Set up the IP range (Manual) to whatever you like (different from other subnets). Click Isolate Network, which creates rules to effectively isolate that VLAN and in effect pfsense from Router A's network.
In the port manager for the switch where you connect pfsense, you assign it's port as Native VLAN / Network 31 (Untagged). I suppose you don't see the VLAN ID, but rather the name which you obfuscated.
Now your pfsense will get a WAN IP from within the VLAN31 subnet and you can start using it for your Network B.And while you are at it, why not get rid of Router B, since pfsense will be handling things from now on. If you need it for wifi, just turn off DHCP and move the cable over from WAN to one of the LAN ports.
-
@Gblenn Thanks a lot for those insights! I guess I need to review what I am planning. But
-
But there is one thing that I still would really like to know: Does a Networks' default gateway need to have all Ports open that any user on the network would like to use? F.i.: If a User would like look at a website, does the gateways Ports 80,443 need to be open?
-
@signerror No, nothing needs to be opened for that type of use case. You need to open ports for traffic to get INTO the network, from the internet och in this case from Router A LAN.
If you host a web site, or a game server, even for ad hoc gaming, you need to open the required ports. And in the case of a web site it would typically be 443 for HTTPS.
This presents a bit of a problem in your case since you are double NATed. So in order for that to work, you first need to open port 443 on the Unifi machine, and forward it to the IP of your pfsense. And then on pfsense you need to do the same and point it to your webserver. Similarly for hosting a game... However, for gaming you might be able to make it work if you turn on UPnP in both machines.
-
It has to pass that traffic outbound obviously but no inbound ports need to be open. Replies from remote resources will be allowed by a stateful firewall like pfSense.