vti IPsec, gateway not adding static routes on 24.11
-
I have an IPSEC VPN with a customer (on my side a pfsense 24.11, customer is a Palo Alto).
We are trying to establish a VPN with a single shared IP on my side and multiple different ranges on the customer side. Since there are many address ranges and to avoid having several tunnels, we decided to try a single tunnel were I share a single IP on my side and the customer shares 0.0.0.0/0 on his side, and then route only the appropriate traffic through the tunnel with static routes (a routed tunnel connection)So I created the single P2 tunnel, vti mode, from my single address to the customers 0.0.0.0/0 range.
The customer configured the tunnel on his side as a routed tunnel on the Palo Alto, sharing 0.0.0.0/0 on both sides.The issue is that when bringing up the tunnel, it is created as 0.0.0.0/0 to 0.0.0.0/0. This is the appropriate part of the log:
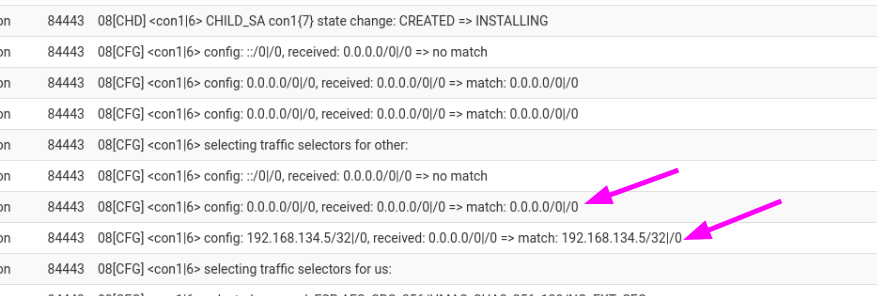
Since the tunnel is created from 0.0.0.0/0 local, then when I create the gateway it doesn't get an address, and so the static routes cannot be added.
This is somewhat related to https://forum.netgate.com/post/1172294, but isn't the same scenario.
Is there a setting for me to avoid proposing the 0.0.0.0/0 range locally?
-
@lmassera said in vti IPsec, gateway not adding static routes on 24.11:
We are trying to establish a VPN with a single shared IP on my side and multiple different ranges on the customer side
Just trying to understand, but are you saying you have e.g. one subnet on your side and the Palo Alto site has a whole range of subnets, all of which you want to reach from your side?
If so, doesn't one VTI tunnel and a static route via that tunnel for each of the Palo Alto subnets work?
But I'm thinking you can't anyway propose 0.0.0.0/0 for the pfsense side ? Perhaps you can keep that for the PA side but rather just set a /32 or /30 address on the pfsense side? -
@Gblenn Thanks for your answer. I am doing what you are proposing. On the pfsense side I propose a single /32 range.
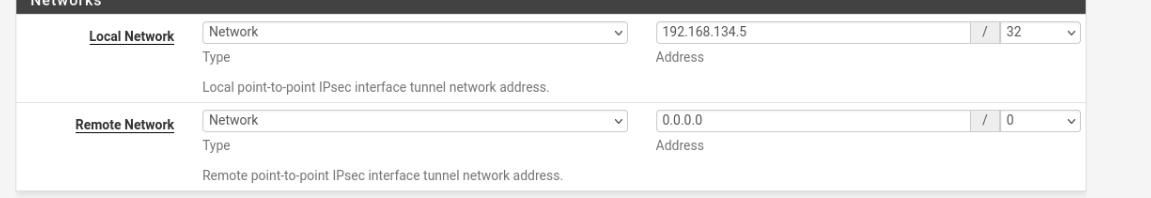
But the pfsense adds to the proposal automatically 0.0.0.0/0 and ::/0.
Since the Palo Alto is configured to use 0.0.0.0/0 on both sides (it seems they cannot do anything else if it is a routed tunnel), when negotiating the P2 the tunnel is established as 0.0.0.0/0 - 0.0.0.0/0.I suppose there is a reason for adding these networks by default to the proposal, but in my case it makes it impossible to set up a gateway on my side.
-
@lmassera Hmm, sounds a bit like Sophos XG I have at one end of one of my tunnels. But that is only half the truth, since on the Sophos with VTI setup I also have the xrfm interface which is automatically added when I select VTI. I then set it up with a /30 (or /24) subnet matching that of pfsense. I wonder if there is something amiss on their side then?
-
Finally managed to solve it.
The issue was that the gateway wasn´t getting an IP address automatically because the VPN interface was created from 0.0.0.0/0 on my side.
Had to manually assign an IP address to the interface using the console (you cannot do it from the GUI).
Once I assigned an IP address to the interface (an unused /30 range) I was able to create the gateway on that interface and assign it the routes.
Then the routes showed up on the routing table and everything worked. -
Hey, I'm the person who made the original thread that you referenced. I can confirm that setting the interface address manually via console is a working solution for 24.11. However, under "system -> routing" the gateway address changed from 0.0.0.0 to "dynamic", which is not correct. This still makes me think it's a bug.
I would like to stress again that routing via interface has been working flawlessly since at least CE 2.6.0 (from 2022), even though I understand it's not quite supported explicitly in strongswan. Setting a static address for an interface that is then ignored seems... unnecessary.
-
OK, this has been working correctly for a couple months, but a few days ago the interface "lost" the IP address.
The router hasn't restarted nor I can find anything in the logs. Had to reassing an IP address and it just continued to work.
I will try to dig deeper in the gateway address handling to see if I find the bug.