IPSec Site-to-Site SPD not matching Phase2 Policies
-
Hi,
I have a weird problem with IPSEC VPN:
pFsence version: 24.11 on Netgate 2100 MAX.
Remote device is a Mikrotik Router.LAN Subnet = 192.168.60.0/24
OPT1 Subnet = 10.1.0.0/24
OPT4OCIPE Subnet = 192.168.189.0/24What I try to achieve is to encrypt:
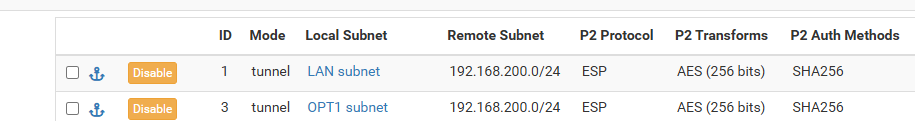
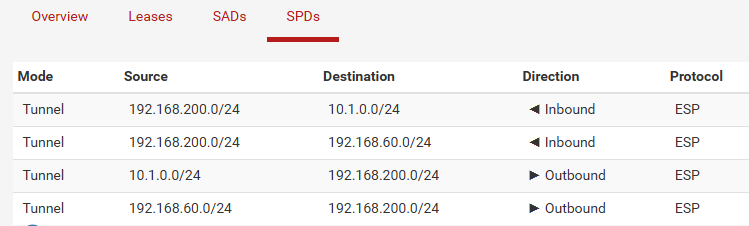
LAN Subnet (192.168.60.0/24) <-> 192.168.200.0/24
OPT1 Subnet (10.1.0.0/24) <-> 192.168.200.0/24
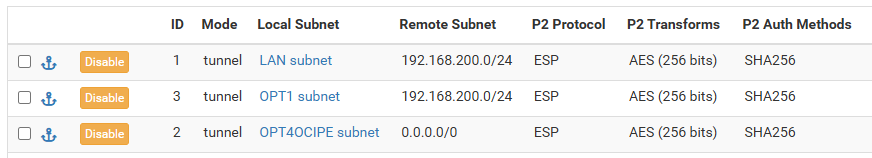
OPT4OCIPE Subnet (192.168.189.0/24) <-> 0.0.0.0/0Example working Correctly:
Phase 2 Policies:
SPDs:
Example causing Issues, when I add a 3rd P2 Policy to encrypt all traffic (0.0.0.0/0) from OPT4OCIPE (192.168.189.0/24)
Phase 2 Policies:
SPDs circled in RED should not be present. It is encrypting traffic which is not supposes to be encrypted.
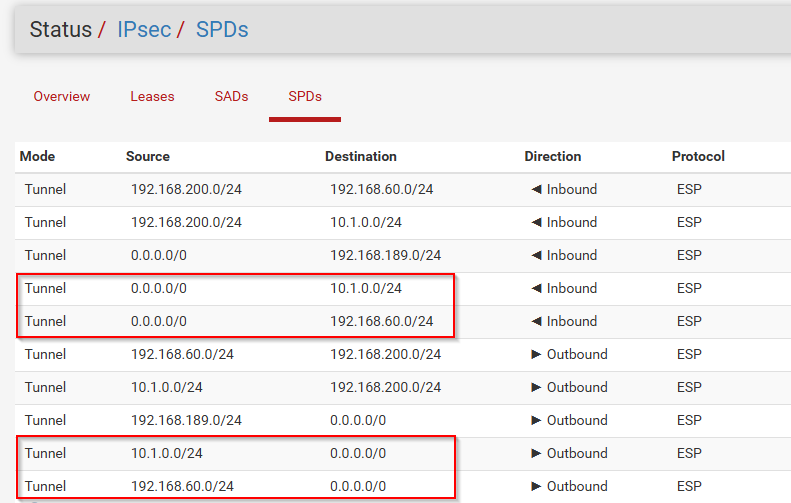
Let me know if any of you have idea of what I did incorectly. I can provide more info if required.
On the other side of the VPN tunnel, the Phase2 policies and SPDs are correct.
Thx.
PLP.
-
@plep Yeah, it can be a bit confusing. PfSense by default attempts to “combine” the subnets in P2s into one. That causes issues just like described where your other P2’s are “extended” from only the remote subnet to 0.0.0.0/0. To avoid this you need to tick the “Split Connections” box on your P1 for the tunnel then it will create several independant P2’s like the other end.