Removal of LAGG
-
Sort out get it, so this mean I have an issue in the outbound nat?
-
Cant see anything wrong in NAT
-
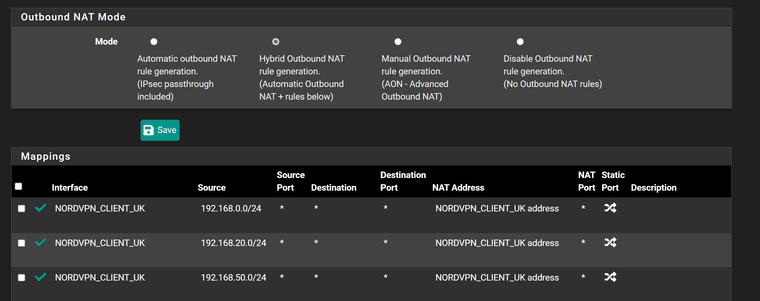
-
@stevencavanagh well its not going to work if you don't nat..
Here I just setup a policy route. To route traffic out a vpn client I have for testing.. You can see its natted to the vpn IP.
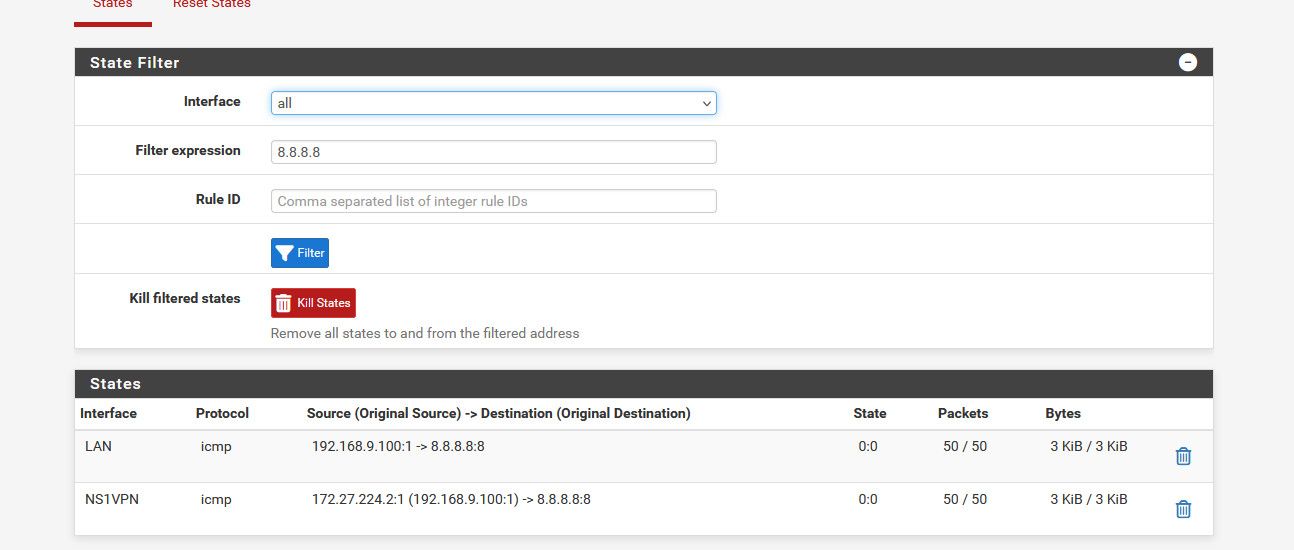
Without a full picture there is no way to know what you have missing.. What is the rest of the nat outbound rules.. What are the rules on the interface client is hitting.
But if your vpn client sends on the traffic with a source of 192.168.0.100 your vpn service isn't going to do anything with it.. So yeah no response.
-
What I cannot get my head around is that same NAT rules work fine on old interface but not on new. I cannot find anywhere in pfsense where the interface is used except LAGG and assignments.
-
LAN interface rules
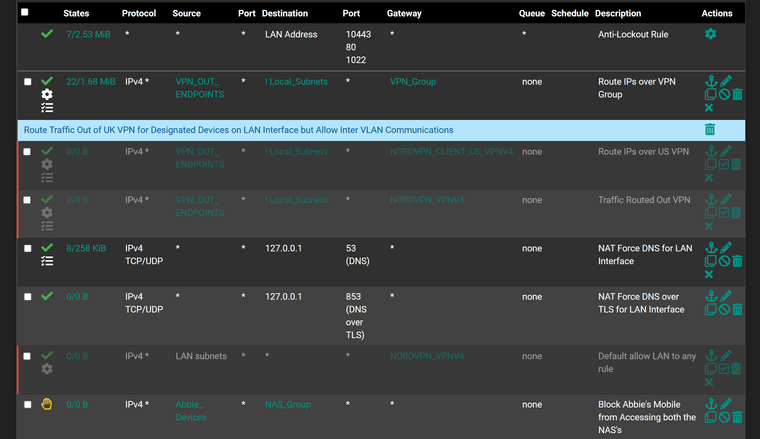
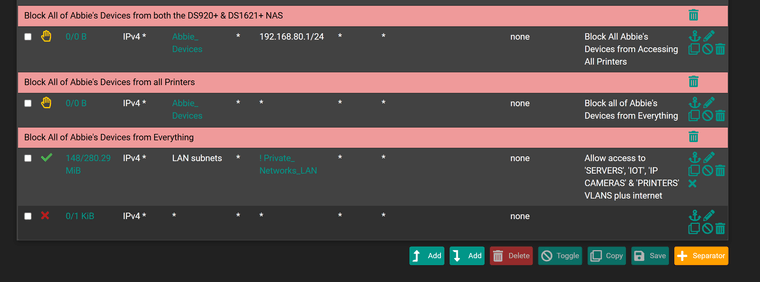
-
Outbound NAT
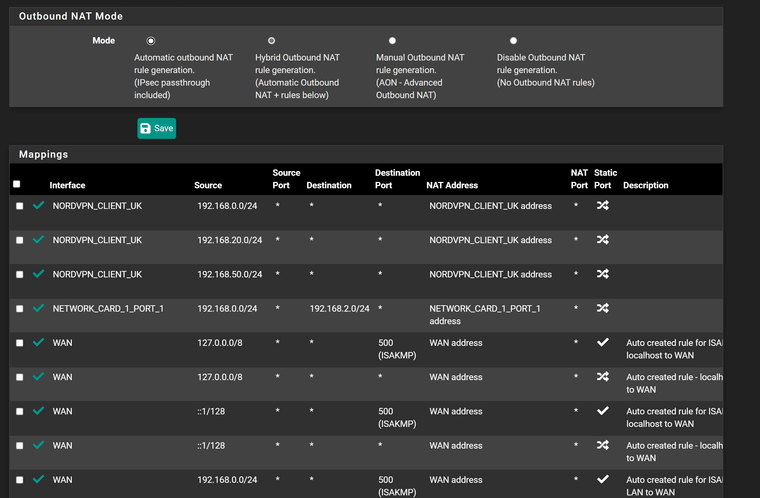
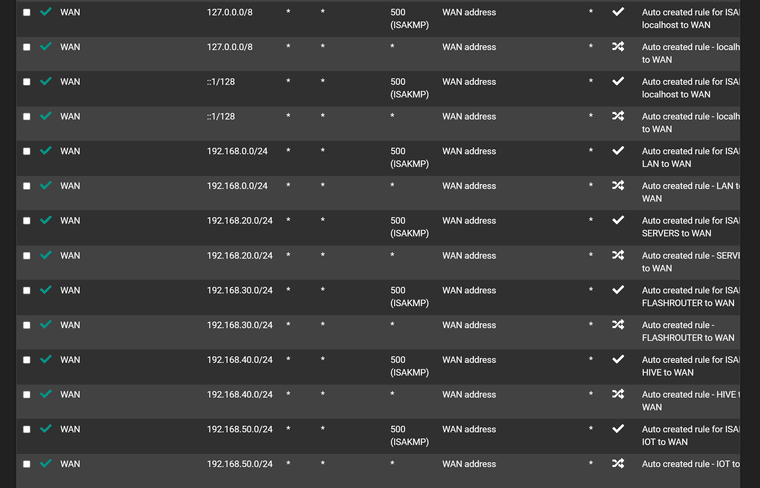
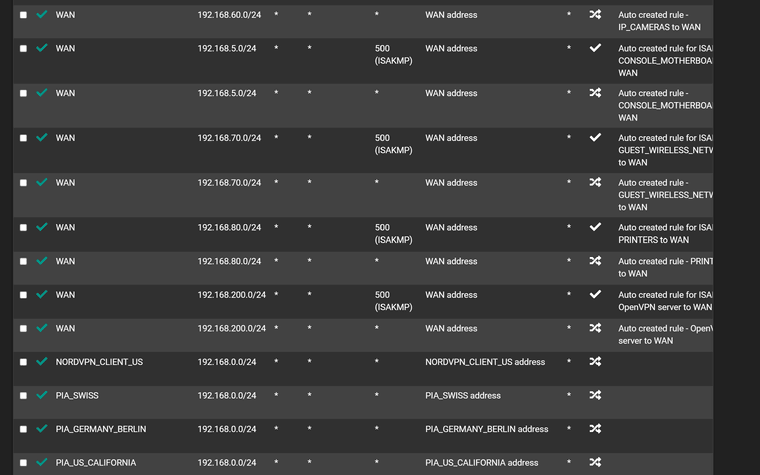
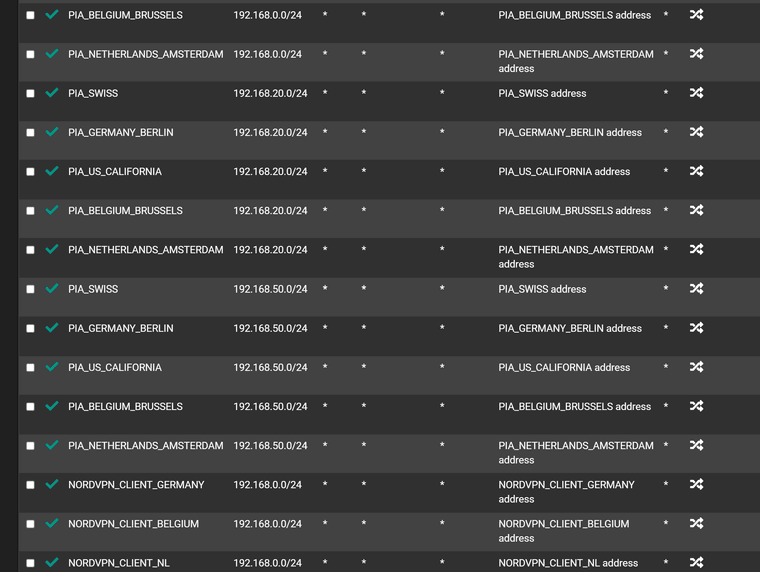
-
Not changed anything but...............
It now all works and only thing that seems to have changed is it is using PIA Belgium as VPN...........
-
What I cannot understand is why it wasn't working with NordVPN as nothing has changed at all
-
@stevencavanagh Maybe just needed to reset/re save the rules after your interface change?
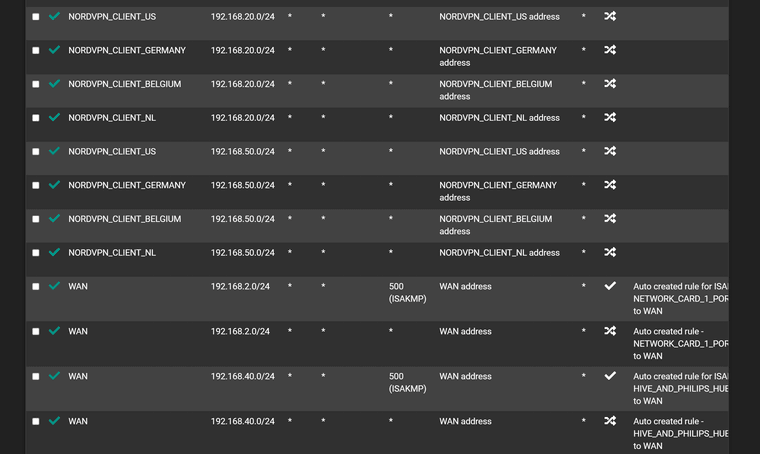
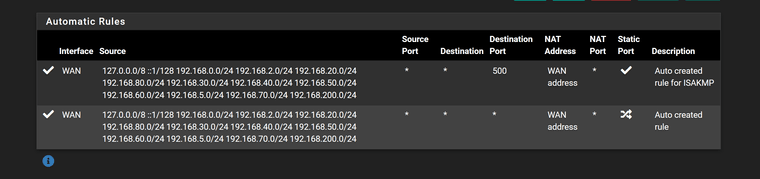
Maybe a policy route issue.. Not sure why you have wan rules along with your vpn interfaces in what look all broken apart but say auto created?
What you should see is a few hybrid rules and then those auto rules with all of your networks - but looks like you have rule for the vpn interface and wan in the hybrid mapping? Odd..
-
@johnpoz
Not sure why I ended up with so many rules either, just following guides how to set up VPNs.When you say some are broken, how are you determining which?
-
@stevencavanagh If it all works for a while I will swap the 4 port rj45 card (igb2-igb5) for the 2 port sfp+ and try and get a 10G link to the core switch, which is where I am trying to get to.
-
@stevencavanagh said in Removal of LAGG:
just following guides how to set up VPNs.
All of them are pure crap - the ones I have read at least, but yeah they have you go to manual rules for ZERO reason..
Did I say broken? I meant make no sense, if your in hybrid mode why would you have rules in mapping in your hybrid section for your normal wan interface? Maybe it was how you snipped up and posted the images?
Also hybrid are evaluated top down as well.. So then you have multiple in row with the same source network I see multiple with 192.168.20 and then 192.168.50..
How are you doing your policy routing.. Your going to have issues trying to switch between them - unless you kill all the existing states..
-
@johnpoz said in Removal of LAGG:
@stevencavanagh said in Removal of LAGG:
just following guides how to set up VPNs.
All of them are pure crap - the ones I have read at least, but yeah they have you go to manual rules for ZERO reason..
Did I say broken? I meant make no sense, if your in hybrid mode why would you have rules in mapping in your hybrid section for your normal wan interface? Maybe it was how you snipped up and posted the images?
Also hybrid are evaluated top down as well.. So then you have multiple in row with the same source network I see multiple with 192.168.20 and then 192.168.50..
How are you doing your policy routing.. Your going to have issues trying to switch between them - unless you kill all the existing states..
I snipped them up from top to bottom.
If I remember I had set them up so multiple VPN gateways were in a group (all Tier 1) and I could then use policy routing to send all traffic from certain IPs (all static) out via VPN and the rest via the default gateway. The outbound NAT for 192.168.20, 192.168.50 etc are all VLANs, hence why there are so many.
Also, floating rule exists (kill switch).
What I cannot remember is how Pfsense determines which of the Tier 1 VPNs to select as my IP address switches regularly from country to country, which is fine.
Fairly certain I'm not killing all the states, what problems will I have?
-
If they're actually set as the same tier it will just move to the next gateway in the group in the event of a failover.
-
Must be failing fairly regularly then!
-
Depends how you are using it. If they are in a group you're policy routing to (which I think they are) then pf will will load-balance between them so you will see connections change continually.
-
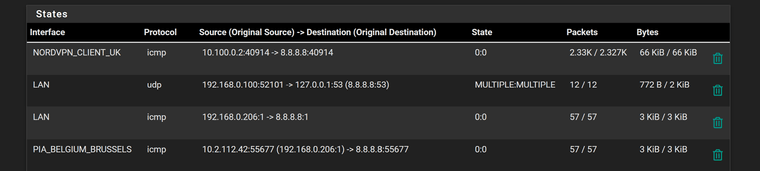
They are inna group and they do appear o load share but only seems to be 3 of them at any one time for some reason.
-
Are they all connected? Are they all at the same tier?
-
@stephenw10 Yes, they are all connected and all at tier 1