IPSec problem with one-way traffic flow
-
Hi everyone,
I have set up a tunnel between two 2.7.2CE VM's:
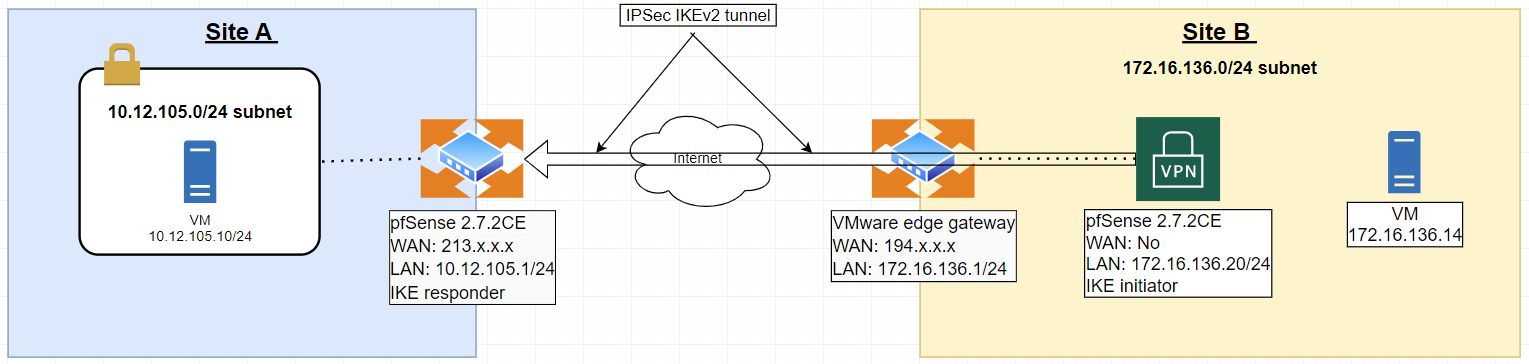
On SiteA pfSense is the primary gateway.
On SiteB pfSense is not the primary gateway.P1 and P2 comes up but I can only get traffic to flow from the 172.16.136.0/24 side to the 10.12.105.0/24 side.
I can ping:
172.16.136.20 to 10.12.105.10
172.16.136.14 to 10.12.105.10
10.12.105.10 to 172.16.136.20I cannot ping:
10.12.105.10 to 172.16.136.1
10.12.105.10 to 172.16.136.14My firewall rules right now are Allow Any on all interfaces.
It seems like I am missing something really basic.,.
Hopefully someone can point me in the right direction.Thanks!
-
@crosstheroad said in IPSec problem with one-way traffic flow:
On SiteA pfSense is the primary gateway.
On SiteB pfSense is not the primary gateway.P1 and P2 comes up but I can only get traffic to flow from the 172.16.136.0/24 side to the 10.12.105.0/24 side.
So I assume, you have added static routes for site A subnet at B.
How did you do this? -
@viragomann
Thanks for the reply.
I have not configured any static routes on the pfSense VM's.
I figured since traffic flowed without static routes from B to A that the opposite would be true as well.On the 172.16.136.14 VM I have added a static route in the OS for traffic destined for 10.12.105.0/24 to route through 172.16.136.20 (instead of the default gateway 172.16.136.1)
I have also added a static route on the 10.12.105.10 VM since it is connected to multiple networks, but can still only reach the site B pfSense LAN IP address and nothing else on that subnet.What routes should I configure in the pfSense machines?
-
@crosstheroad said in IPSec problem with one-way traffic flow:
On the 172.16.136.14 VM I have added a static route in the OS for traffic destined for 10.12.105.0/24 to route through 172.16.136.20 (instead of the default gateway 172.16.136.1)
I have also added a static route on the 10.12.105.10 VM since it is connected to multiple networks, but can still only reach the site B pfSense LAN IP address and nothing else on that subnet.You should at least be able to reach 172.16.136.14, which has the static route set.
If the machine doesn't respond though, it probably blocks access from outside of its local subnet by its own firewall. -
@viragomann
I double checked the static route configuration on the 172.16.136.14 VM and traffic between the two VM's now work!
Thanks for guiding me in the right direction.Ideally I would like for the static route magic to happen in the VMware edge gateway, so that individual configuration of VM's is not needed.
I added this in the Edge gateway configuration:

The blurred Interface is the 172.16.136.1 interface of the edge gateway.
Using another Windows VM, 172.16.136.107, without a static route configured, I cannot reach anything on the 10.12.105.0/24 network.
Fully aware that I am now asking questions about a completely different product than pfSense, but I am hoping that I have just misunderstood something about static routes in general.
-
@crosstheroad
Sadly it's not as simple. Your setup will lead into asymmetric routing.Additionally to the static route you need to source-nat the traffic destined to the remote site to the interface IP on the edge gateway.
Maybe you can do this on the NAT tab.Another, even better solution would be to move the pfSense into a separate virtual network. Then the LAN devices just send packets destined to A to the router, which forwards it to pfSense due to the static route. Traffic from A to B would arrive at pfSense and are forwarded to the router, because it's the upstream gateway, and there the packets are routed to the LAN devices.
-
@crosstheroad Static route on 172.16.136.1 is good. I would remove the static route on 172.16.136.14 so you can troubleshoot/get this working properly.
I think you're going to have an asymmetric routing issue with having everything from Site B 'flow' through 172.16.136.1, since traffic returning from Site A will hit 172.16.136.20 and then be routed directly to whatever host on the 172.16.136.0/24 subnet directly without first passing back through 172.16.136.1.
Both these articles may be useful:
Advanced IPsec Settings
NAT with IPsec Phase 2 NetworksYou should also be more specific when reporting what addresses/protocols/services you're testing connectivity with because @viragomann is right—your VM host OSes are likely to software-firewall block any incoming connections from any subnet they're not directly attached to.
-
@viragomann @tinfoilmatt
Based on your feedback I read up on asymmetric routing and ended up skipping pfSense for this setup altogether
I always try to standardize on products but here it just lead to a level of network knowledge I do not fully understand.I configured a basic IKEv1 tunnel in the edge gateway, added necessary firewall rules and everything worked as intended.
A sidenote is that IKEv2 did not work well in VMware NSX-V with the P2's being disconnected after 3600 seconds and not being able to reconnect without tearing down the P1 manually as well.
Thanks everyone for your input!