Can't get acme wildcard certs / ha proxy to work with any home lab servers on my vlans except pfsense
-
I'm posting some images in case it's obvious what I'm doing wrong. All I am trying to do is provide ssl certs for my many home lab servers for internal use only. pfsense is the only one that works as expected, I would doubt that it's because ha proxy is working. All servers have host overrides pointing to their respective vlans. cloudflare dynamic dns is working fine, as is acme let's encrypt certificates. I have had this all woking in the past, but with lots of changes, like which domain, etc, so i nuked ha proxy and started from scratch. I have watched several hours of YT videos (all of them) on the topic, and afaik, I am doing everything pretty much like I remember and like I see on the vids. I gotta be missing something stupid.

-
Where are you testing from?
How does it fail?
@Cloudless-Smart-Home said in Can't get acme wildcard certs / ha proxy to work with any home lab servers on my vlans except pfsense:
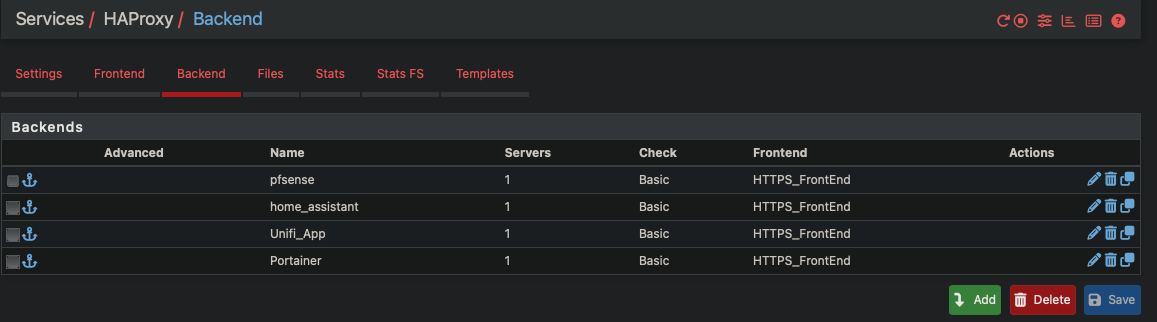
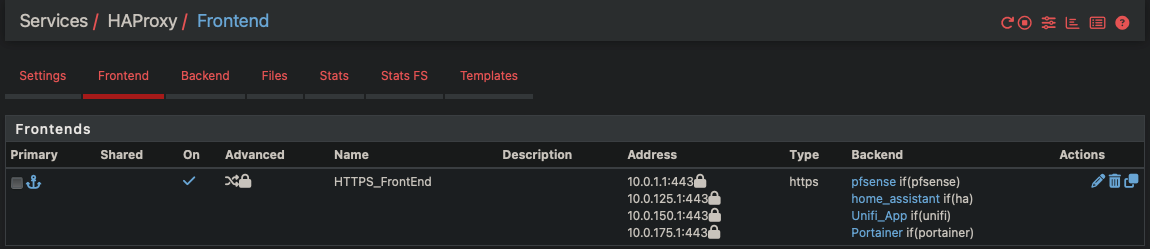
All servers have host overrides pointing to their respective vlans.
What exactly do you mean by that? HAProxy would usually listen on all available addresses and as long as anything resolved to one of them it should respond there.
-
@stephenw10 said in Can't get acme wildcard certs / ha proxy to work with any home lab servers on my vlans except pfsense:
Where are you testing from?
Hey Stephen! you have helped me in the past, so I'm thankful for your support! testing from inside my network on my 175 vlan
How does it fail?
page just doesn't load on any of them, including other browsers, private windows.
@Cloudless-Smart-Home said in Can't get acme wildcard certs / ha proxy to work with any home lab servers on my vlans except pfsense:
All servers have host overrides pointing to their respective vlans.
What exactly do you mean by that? HAProxy would usually listen on all available addresses and as long as anything resolved to one of them it should respond there.
dns host override entries, even though they resolve to what I think is the goal, all pointing back to pfsense. here is dig output...; <<>> DiG 9.10.6 <<>> portainer.casa.cloudlesssmarthome.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37713 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1432 ;; QUESTION SECTION: ;portainer.casa.cloudlesssmarthome.com. IN A ;; ANSWER SECTION: portainer.casa.cloudlesssmarthome.com. 3600 IN A 10.0.150.1 ;; Query time: 0 msec ;; SERVER: 10.0.175.1#53(10.0.175.1) ;; WHEN: Mon Apr 21 13:42:03 CDT 2025 ;; MSG SIZE rcvd: 82it's really weird. I have turned on debugging logs, and I'm not seeing anything interesting there. it's like ha proxy isn't doing anything. The logs are complaining about home assistant, but I will worry about that one after I can get the easier ones working. there's a lot of info out there about having to install certs on home assistant to get it working with proxy for ssl.
-
It seems more like it's not actually seeing the requests. I'd expect some sort of error in the browser if it was seeing a bad cert or failing to see the correct response.
Check the states when you try to connect. Check the firewall logs.
-
@stephenw10 I'm an idiot. a few troubleshooting commands with help from grok showed me that I'm not supposed to keep the old port numbers on when I go to the new web address. oh my gosh. it's been working all along. now to work on home assistant stubbornness.
-
@Cloudless-Smart-Home many, many threads regarding the home assistant not liking to be proxied, but I found the solution was to turn off the ssl checkbox that works in every other server, evidentially because they were already running https, unlike home assistant. also had to add a config.yaml entry to allow trusted proxies and uncheck forward for, but then it worked too, for the record, incase someone else stumbles into this conversation, they won't have to spend hours and hours to find a simple solution. sooo much to learn and such hard knocks when you do, lol.