Routing Specific Traffic over VTI
-
This post is deleted! -
This post is deleted! -
@stan-fergusonsmith said in Routing Specific Traffic over VTI:
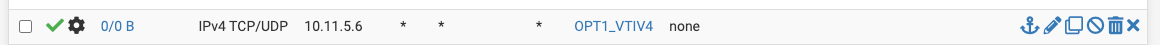
Remote Server WAN Rules:
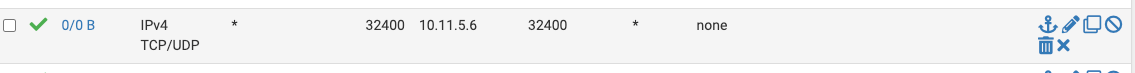
What's your intention? Routing this to a machine on the remote site?
Did you add a Port forwarding rule?
-
This post is deleted! -
@stan-fergusonsmith
A port forwarding rule is needed for this in any case.
In the port forwarding rule you can select an option to let pfSense create an associated firewall rule automatically or just select "pass" to allow the traffic without an explicit rule.
Anyway both are needed.But there is something else. Assuming it's not an issue for you to not see the real client IP at the destination device, you can go with masquerading as well.
So on the remote site you have to add an additional outbound NAT rule to the IPSec interface with source = any, destination = 10.11.5.0/24, translation = interface address.And an additional outbound NAT rule is needed on the local VPN endpoint. So you have also switch the outbound NAT into hybrid mode and add a rule:
interface: LAN
source: any
dest.: 10.11.5.0/24These NAT rules are needed, that the destination devices send reply packets back to the local pfSense and the local to the remote. Without this they would send replies to their default gateway.
-
This post is deleted! -
This post is deleted! -
@stan-fergusonsmith
Does your application really use a static source port?? That's very unusual.
Most application use a random source port. So you probably have to set the source port to 'any' in the port forwarding and firewall rule. -
This post is deleted!